CLOUDANIX
Cloud Workload Protection Platform (CWPP)
Secure your Container and VM Workloads in few clicks
What is Cloud Workload Protection Platform (CWPP)?
Workload is a host of processes and resources that are used to run applications. It includes all the network resources needed to connect several components of the application and in turn connect users to the application. These applications are usually public-facing and have multiple compute options and are difficult to monitor and secure. Cloudanix CWPP offers a low-friction and scalable solution to secure your diverse workloads.
Learn More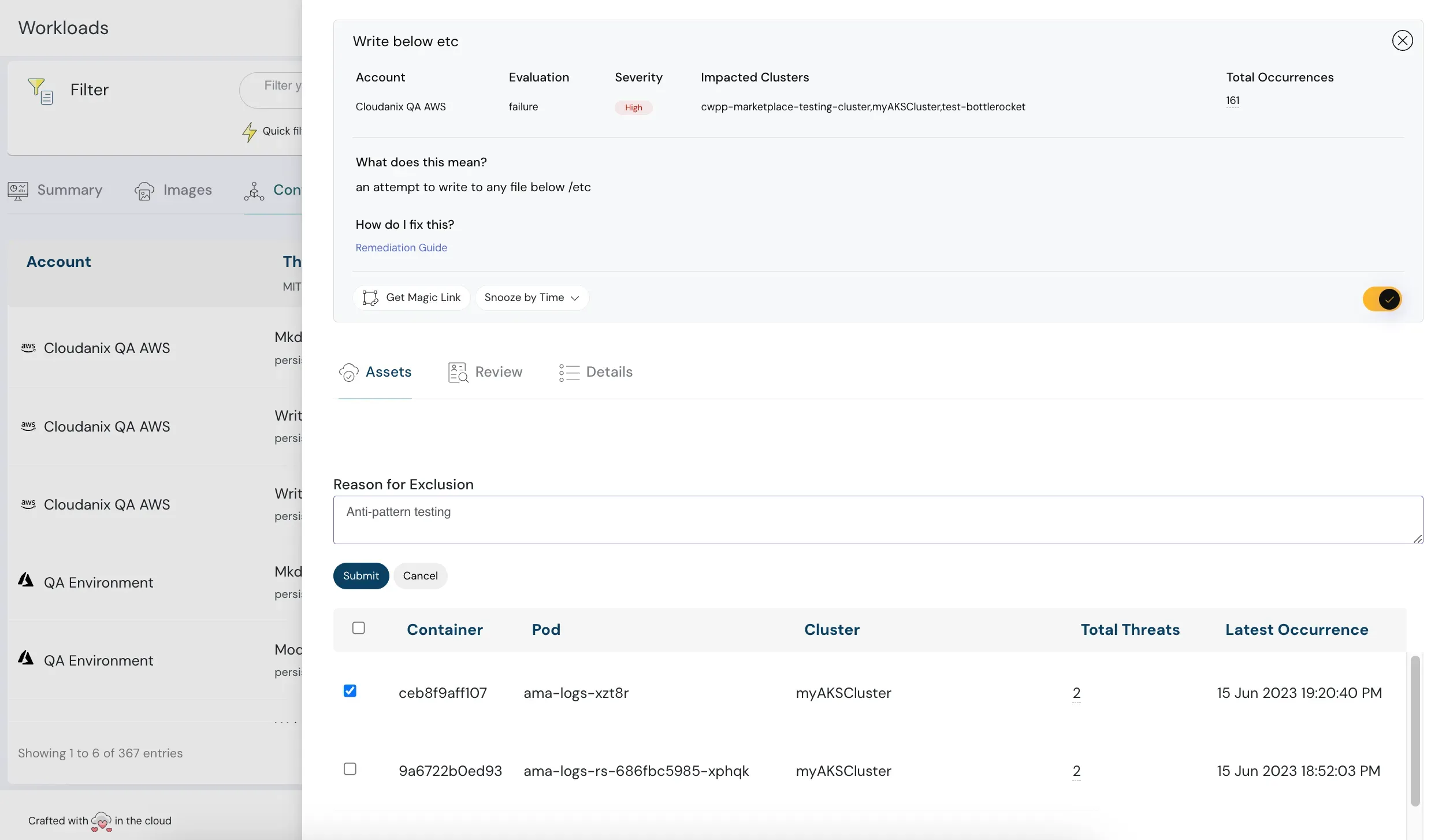
How Cloudanix Aces CWPP
Most companies use hybrid or multi-cloud infrastructure—making it harder to maintain consistent visibility. Traditional network-based protection falls short in cloud environments. Cloudanix offers visibility and protection starting from deployment. We scan for vulnerabilities, detect misconfigurations, and provide architectural clarity across workloads of all types and sizes.
Built for Hybrid & Multi-Cloud
Visibility and protection no matter where your workloads live.
Start Security at Deployment
Scan containers and serverless workloads right at deployment time.
Secure Your Workloads
Cloudanix CWPP Core Capabilities
Whether your workloads are in the cloud or on-premises, Cloudanix delivers uncompromised protection, deep visibility, and continuous security across the DevOps lifecycle. Here's what Cloudanix CWPP offers.
Workload Discovery & Protection
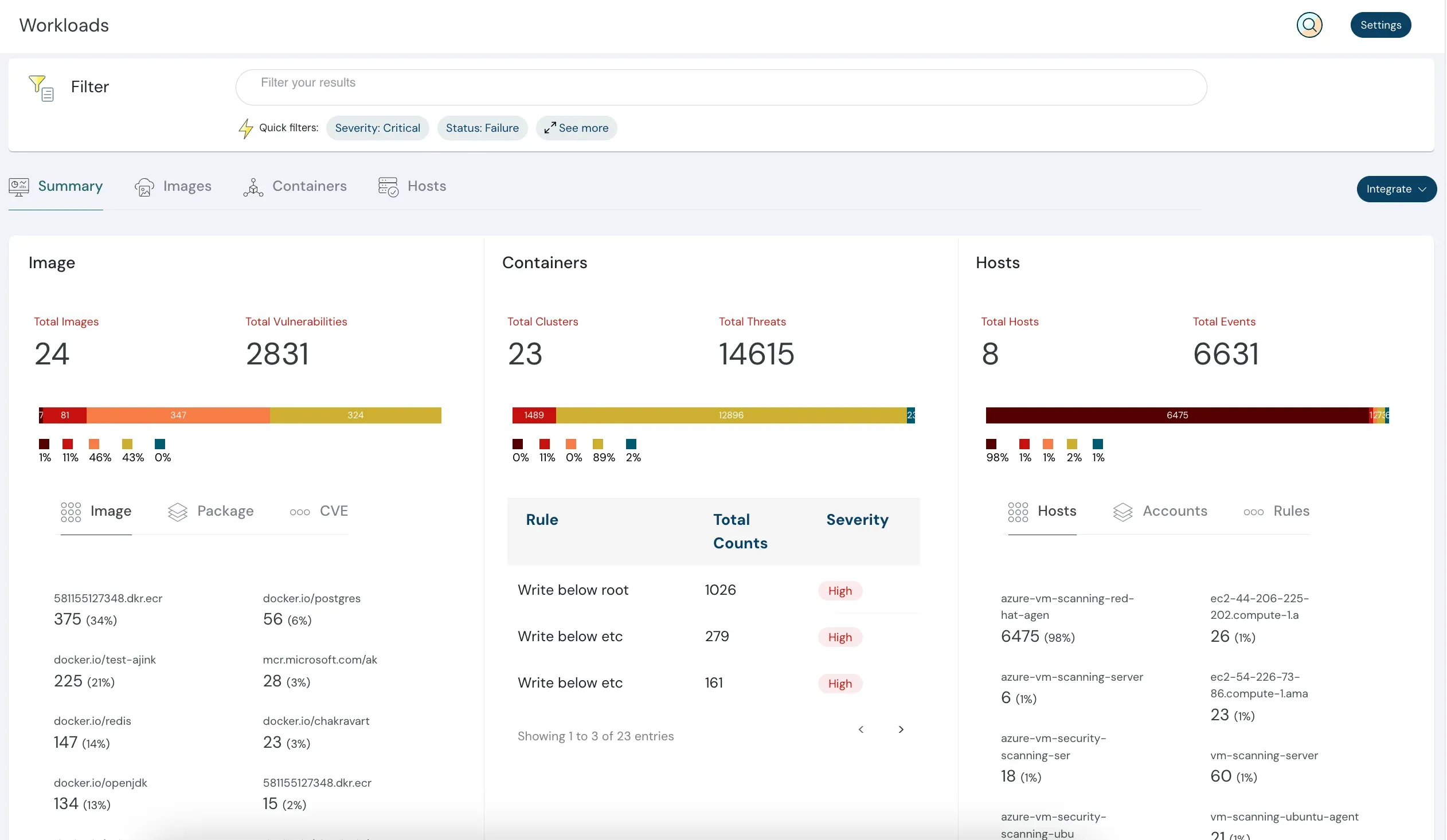
Discover all cloud and on-prem workloads and ensure they are protected with no compromises. Cloudanix secures your compute, containers, and functions from threats across environments. (Know more)
Vulnerability Assessment
Automatically audit your workloads to identify misconfigurations, software vulnerabilities, and potential threats—keeping your infrastructure secure and compliant. (Know more)
Exploit Risk Detection
Identify security issues that could potentially be exploited by attackers. Cloudanix continuously scans for risks tied to your workloads and prioritizes actions to fix them. (Know more)
CI/CD Integration
Cloudanix integrates seamlessly into your DevOps pipelines to ensure that security is built into every stage of development—without slowing down your team. (Know more)
Secure by Default
Automatically configures workload security settings based on best practices, helping developers deliver secure applications without manual effort.
Developer-Friendly Security
Allow developers to integrate security without added overhead. Cloudanix ensures that protecting workloads doesn’t come at the cost of agility or productivity.
Scalable Protection
Security that scales with your workloads—whether you're scaling up for growth or scaling down. Cloudanix adapts in real-time without manual intervention.
Tailored Visibility & Controls
Gain detailed visibility into different types of workloads and apply tailored controls for each. Make better decisions with workload-specific insights. (Know more)
Compliance & Remediation
Automate compliance checks, detect violations, and remediate threats fast. Cloudanix ensures data remains protected and audit-ready at all times. (Know more)
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedSolutions For Roles
How Cloudanix Helps Different Teams
Whether you're leading security strategy or maintaining day-to-day cloud health, Cloudanix equips every role with the tools needed to ensure security, compliance, and visibility.
CISOs
As a CISO, your job is to continuously secure the environment and find ways to advance your organization’s security. Cloudanix gives you a unified view and actionable insights to make strategic decisions.
DevSecOps
With new code being continuously pushed, you're responsible for maintaining and improving cloud security. Cloudanix integrates into your CI/CD pipeline to prevent issues before they ship.
Cloud Security Professionals
Cloudanix cuts the complexity of maintaining the highest standards of compliance and reduces the attack surface of your cloud infrastructure—giving you more control, with less manual work.
CLOUDANIX
Insights from Cloudanix
Explore guides, checklists, and blogs that simplify cloud security and help you secure your infrastructure.
Case Studies
Real-world success stories where Cloudanix helped organizations secure their cloud infrastructure. Watch how we made a d...
What is CWPP?
Understand what is Cloud Workload Protection Platform (CWPP) and how it helps organization to automate security and comp...
Container Runtime Security
Learn about container runtime security, the four core phases, and why its essential for protecting cloud-native applicat...
Cloudanix docs
Cloudanix offers you a single dashboard to secure your workloads. Learn how to set up Cloudanix for your cloud platform ...
JIT Kubernetes for Azure AKS Security
The traditional approach of granting permanent, or “standing,” access to Azure Kubernetes Service (AKS) clusters creates...
Guide to Cloud Workload Protection
Organizations are shifting their workloads to the cloud. But the question is - Are your workloads safe?
Changelog
A complete history of changes, improvements, and fixes for Cloudanix. Subscribe to get notified about the latest updates...
Podcast
Tune in to the Cloudanix podcast for expert discussions on cloud security, compliance, and the latest industry trends. L...
