CIEM | Cloud Infrastructure Security | Cloudanix
Cloud Infrastructure Entitlement Management - CIEM Security
Simplified Cloud IAM To Secure Your Multi Cloud Environments

What is Cloud Infrastructure Entitlements Management (CIEM)?
CIEM is Cloud Infrastructure Entitlements Management. The primary function of this solution is IAM (Identity and Access Management) governance. CIEM mitigates the risk associated with compromised credentials and privileged identities and provides a detailed log of who and when anyone has accessed any cloud resources. It helps define permissions, which essentially means who has access to what and thus avoids vulnerabilities in the system, keeping your cloud assets safe. Identities overview Identities at glance
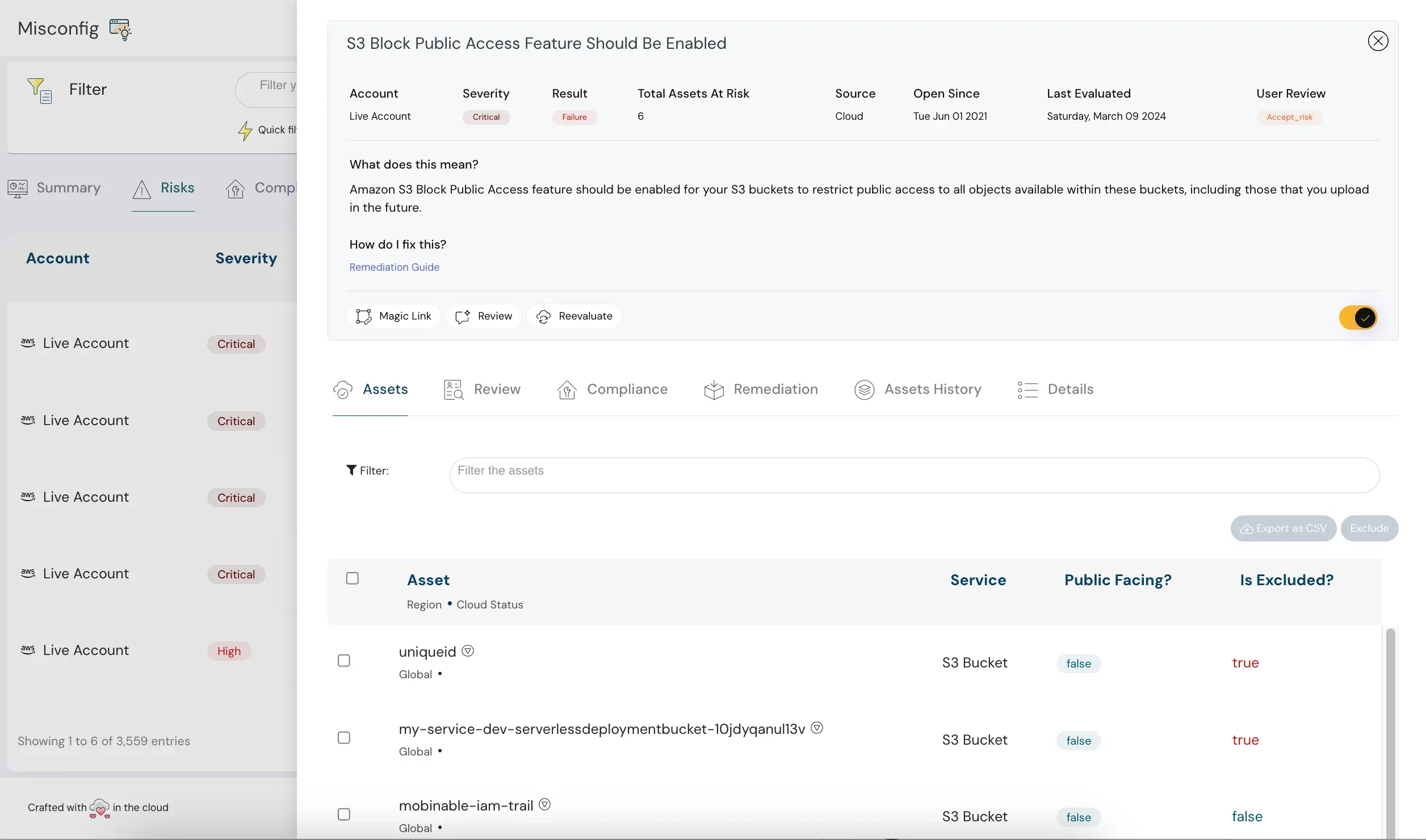
Need for a CIEM Security Solution
Cloud Providers offer a host of tools for monitoring and reducing risk. These tools, though native, are limited in the scope and depth they can offer. This is not to say that native tools are not recommended. You have to see the cost and scale parameters of your organization before arriving upon this decision.
Multi-cloud Limitations
Native tools struggle with centralized visibility across cloud providers.
Tool Fatigue
Switching screens is inefficient — Cloudanix brings it all to one dashboard.
Cloud Infrastructure Entitlement Management (CIEM)
What do you get with CIEM?
A good CIEM security tool should provide access governance capabilities while maintaining strict compliance and regulatory standards. You should get capabilities to identify and continuously monitor unusual behavior that may be indicative of a breach or misuse. CIEM helps track users' activities and can generate reports which will help track any unusual access, thus eliminating loopholes within the system. As we all preach, “Prevention is better than cure” this applies here more than anywhere else. It can help track access changes or any other sensitive changes by providing a timeline view, thus preventing the compromise of your cloud infrastructure. CIEM provides deep visibility of entitlements, detects identities or resources with excessive permissions to access patterns, and provides a comprehensive view of access key usage to help monitor them. It also provides an audit and report of user permissions of IAM, Audit roles, and service accounts.
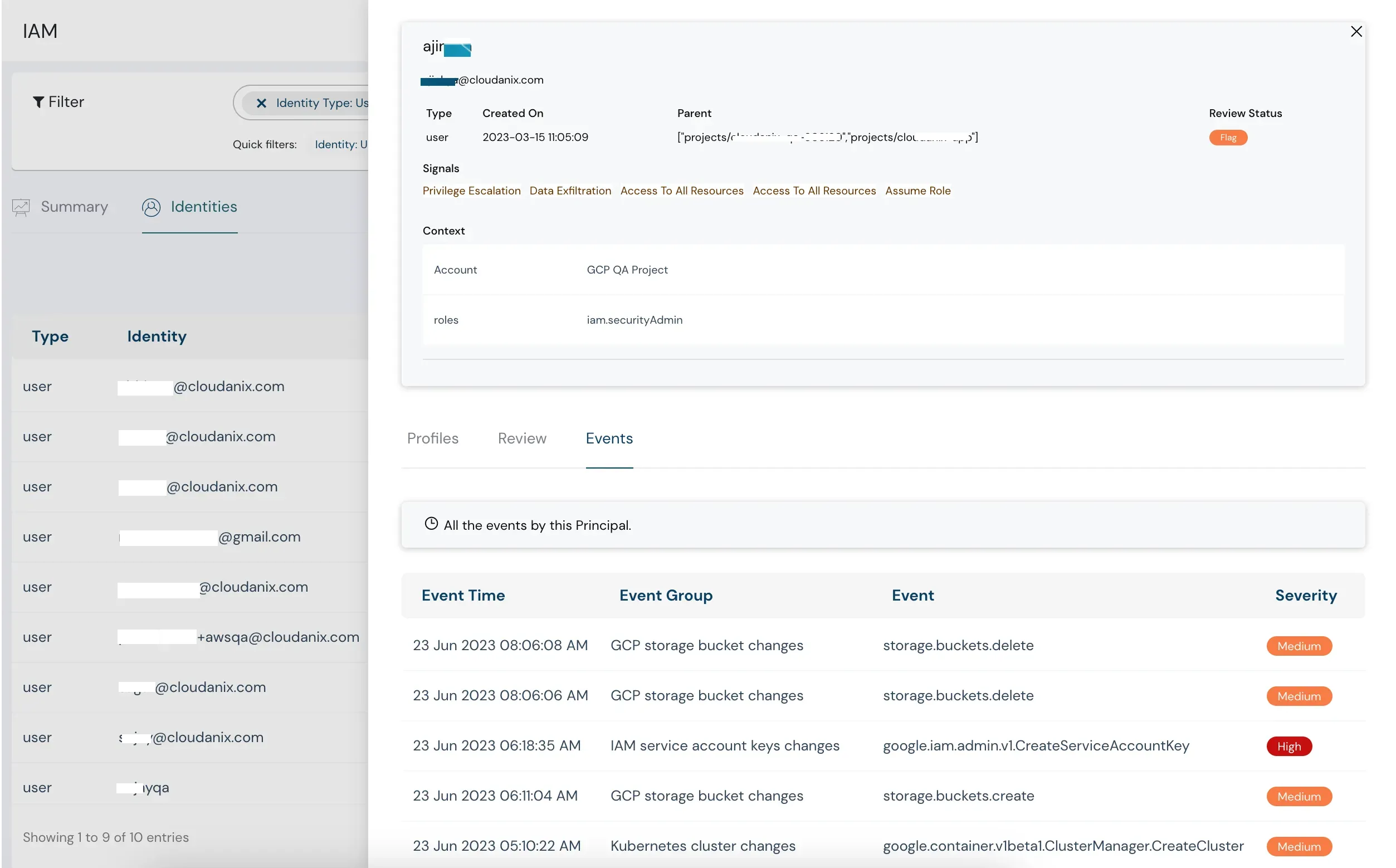
Advanced Cloud Infrastructure Entitlement Management
Cloudanix CIEM Security for You
Protect your organization's cloud infrastructure with automated analysis of access risks and real-time threat detection across all cloud platforms.
Complete Identity Inventory
Comprehensive inventory of human and machine identities across multiple cloud platforms with unified visibility.
- Multi-cloud identity mapping
- Human and machine identity tracking
- Real-time identity discovery
- Cross-platform correlation
Excessive Permissions Detection
Detects resources and identities with excessive permissions and entitlements that violate least privilege principles.
IAM Compliance Scoring
Overall IAM compliance scores by cloud account or account groups with detailed breakdown and improvement recommendations.
- Cloud account scoring
- Account group analysis
- Compliance trending
- Improvement tracking
Compliance & Audit Ready
Generate reports for compliance, audit, entitlements and executive summaries. Supports CIS, SOC2, HIPAA and more.
Automated Risk Analysis
Advanced automated analysis of access risks for all permissions granted and their severity across all clouds.
Real-Time Threat Detection
Identifies toxic permission combinations and alerts in real-time before unintended entitlements can cause damage.

Policy Governance
Governs right-size roles and enforces custom IAM policies with integrated workflow suggestions for remediation.
Access Pattern Monitoring
Comprehensive visibility and monitoring of access key usage and access patterns across your infrastructure.
- Access key usage tracking
- Pattern analysis
- Anomaly detection
- Usage reporting
Cloud Infrastructure Entitlement Management (CIEM)
Our approach to Cloud Infrastructure Entitlement Management
A robust Cloud Infrastructure Entitlements Management (CIEM) tool, can mitigate the risk of unintended entitlements as most successful attacks and threats on cloud services are due to internal oversights or bad actors. Cloudanix not only detects excessive permissions but also prevents this risk by alerting the team in real-time to take action and mitigate any possible threats. Various compliances like CIS, SOC2, HIPAA, etc., require that organizations have cloud security capabilities to govern access policies and enforce the least privilege. Cloudanix provides these capabilities and access controls that allow continuous auditing and automated reporting. This helps stakeholders answer the golden question, “Who can access what?”
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedCloudanix CIEM Capabilities
Why should you try Cloudanix for CIEM?
From fast onboarding to deep visibility, Cloudanix delivers the critical capabilities needed to manage cloud entitlements, identities, and access risks. Here’s what you get with Cloudanix CIEM.
Audit and Compliance
For any enterprise, audit and compliance is a must for stakeholder and customer trust. Meeting legal requirements is not optional anymore. Following best practices is an equally important part of compliance management. Formal regulations, laws or even internal governance controls have to be in place and follow compliance standards set by HIPAA, SOC 2, GDPR, ISO 27001, etc.
Identity and Access Management
You can't secure what you can't see. You have multiple team members. And then you got Code, Workloads, Files, Databases, Networks and so much more. IAM ensures the right people have the right controls and access to the tools they need to complete their job.
Drift, Misconfiguration and Baseline
Unintentional internal oversights are the biggest cause for these mishaps. Untimely detection can open doorways into the organization's precious cloud environment, compromising their precious data. These exploits are the easiest to gain access to and require continuous and real-time monitoring.
Continuous Monitoring
One of the most important features of a good CSPM and CIEM tool. The ability to identify and continuously monitor unusual behavior that may be indicative of a breach or misuse is crucial. If left unchecked, it can open doorways to intentional or unintentional threats.
Real-time Alerts
Important changes in roles and access need to be notified in real-time. Detection and alerts for excessive permissions can be the difference between a secure and an insecure environment. Immediate action is possible to mitigate threats with real-time alerting.
Dynamic View Builder
For regular tracking of important roles, identities, access, and permissions, it is important to have the option to save a particular view to avoid the fatigue of selecting the same options over and over again.
Risk Assessment and Review
Without the option to assess and review the risks associated with certain roles or excessive permissions is like shooting in the dark. You will never know the impact these have on the overall security of your cloud infrastructure.
Visibility of Assets Access
Complete visibility into the assets a certain role has access to is important. A log of changes to the asset or role must be available for review.
What to look for while choosing a CIEM solution?
● Ease of adoption: The tool should have a clean and easy-to-use interface for easy adoption. The amount of time spent to find what you are looking for should be minimum to avoid fatigue in the user.
● Multi-Cloud support: To match with the scale of your business, the tool should have multi-cloud support. This will save you from switching to different windows for multiple clouds, that you may have in the future, while saving you the cost of a new tool.
● Great visibility: Having a tool with high visibility can be a game changer. The tool should have the capability to discover and display the complete inventory of human or machine identities across multiple clouds.
● Comprehensive compliance with regulatory and statutory bodies: It is mandatory to comply with certain compliance, regulatory and statutory bodies. The tools should have mapped multiple frameworks and provide an overall IAM compliance score by cloud accounts or account groups.
● Accurate discovery and detection: The tool capability must include detecting resources and identities with excessive permissions and entitlements.
● High visibility into your cloud infrastructure: The tool must possess the capability to provide visibility and monitoring of access key usage and access patterns while governing the right-size roles and capability to enforce custom IAM policies.
● Audits and Reports: The tool should have the capability to audit and track changes to sensitive data on your dynamic cloud infrastructure, generate reports for compliance, audit, entitlements, and executive summaries.
Cloudanix Cloud Identity Entitlements Management has these capabilities and more, ensuring a smooth functioning threat-free environment.

Give permissions when needed - Just In Time!
Your questions answered.
Frequently Asked Questions
Get clarity on Cloud Infrastructure Entitlement Management (CIEM)—what it is, who needs it, and how it supports secure identity and access practices in the cloud.
Built for Every Security Persona
Solutions for Roles
Cloudanix adapts to different security roles—whether you're a CISO setting vision, an IAM expert managing identity risks, or a cloud security engineer reducing the attack surface. Explore how Cloudanix helps you.
CISOs
As a CISO, your job is to continuously secure the environment and advance your organization’s security posture. Cloudanix gives you full visibility, continuous monitoring, and audit readiness—so you can focus on strategic outcomes.
IAM Professionals
Identity and Access Management becomes easy with Cloudanix. Across multiple cloud providers, we reduce your IAM risk and save your time managing permissions, entitlements, and privilege boundaries.
Cloud Security Professionals
Discover how Cloudanix cuts the complexity of maintaining the highest compliance standards while reducing your cloud infrastructure's attack surface. Automate detection and remediation across environments.
CLOUDANIX
Insights from Cloudanix
Explore guides, checklists, and blogs that simplify cloud security and help you secure your infrastructure.
Case Studies
Real-world success stories where Cloudanix helped organizations secure their cloud infrastructure. Watch how we made a d...
CASB, CSPM, SIEM: Cloud Security Essentials
Understand how CASB, CSPM, and SIEM work together to enhance your cloud security posture and ensure better governance.
Cloudanix docs
Cloudanix offers you a single dashboard to secure your workloads. Learn how to set up Cloudanix for your cloud platform ...
Why do we need continuous audits for public cloud?
Incorporating regular audits into your organization’s security program can help eliminate problems arising from infracti...

What is CIEM?
CIEM manages access to cloud resources by identifying and analyzing user entitlements to mitigate risks like data breach...
Changelog
A complete history of changes, improvements, and fixes for Cloudanix. Subscribe to get notified about the latest updates...
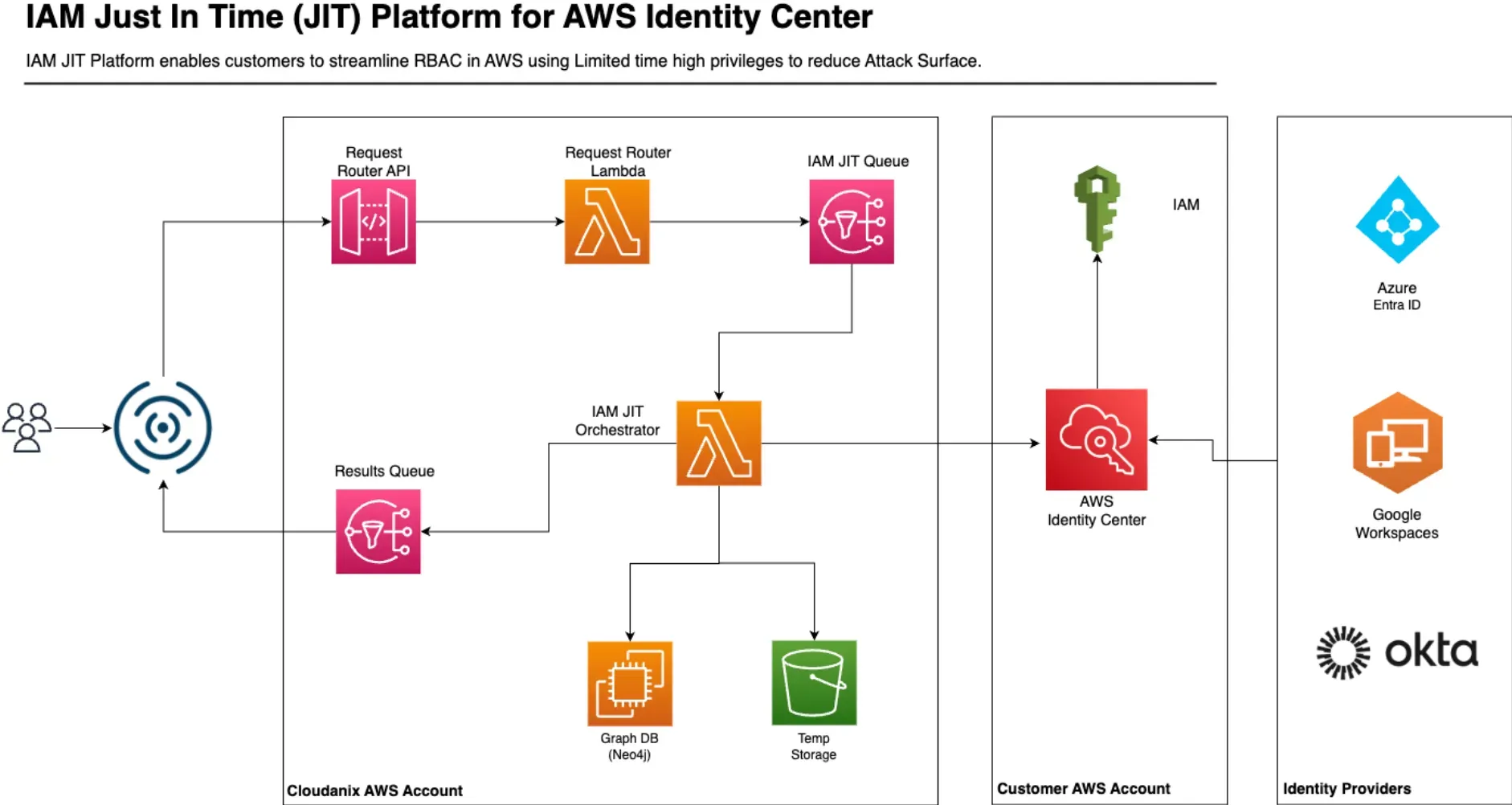
Integrate Just-In-Time IAM Access with AWS
Dive deep into how IAM JIT and AWS Identity Center can strengthen your IAM security posture and streamline identity work...

Safeguard Identity Across Multi-Cloud Environments
IAM tools weren’t built for today’s multi-cloud environments. Learn how to adapt your identity and entitlement managemen...
Podcast
Tune in to the Cloudanix podcast for expert discussions on cloud security, compliance, and the latest industry trends. L...
