CLOUDANIX
Identity and Access Management (IAM) Security Platform
Know who has direct or indirect access to what—Cloudanix IAM simplifies permissions, highlights misconfigurations, and enforces least privilege with insights and automation.
Identity and Access Management (IAM) Simplified
You have multiple team members. And then you got Code, Workloads, Files, Databases, Networks and so much more. These are spread across multiple accounts, multiple clouds—so how do you as a Security team know and approve: "Who should have access to what?"
IAM Risk Management
We've built a unified identity across accounts and highlight IAM misconfiguration risks like Data Exfiltration, Privilege Escalation, and wildcard (*) permissions. These risks are presented to you in a clear and actionable way so you can resolve them before it’s too late.
Just-In-Time (JIT) Access Control
Cloudanix IAM JIT lets your team request permissions for a limited time in just a few clicks. Permissions are revoked automatically after the task is done. The built-in approval workflow adds oversight and simplifies audit trails.
Explore IAM JIT Details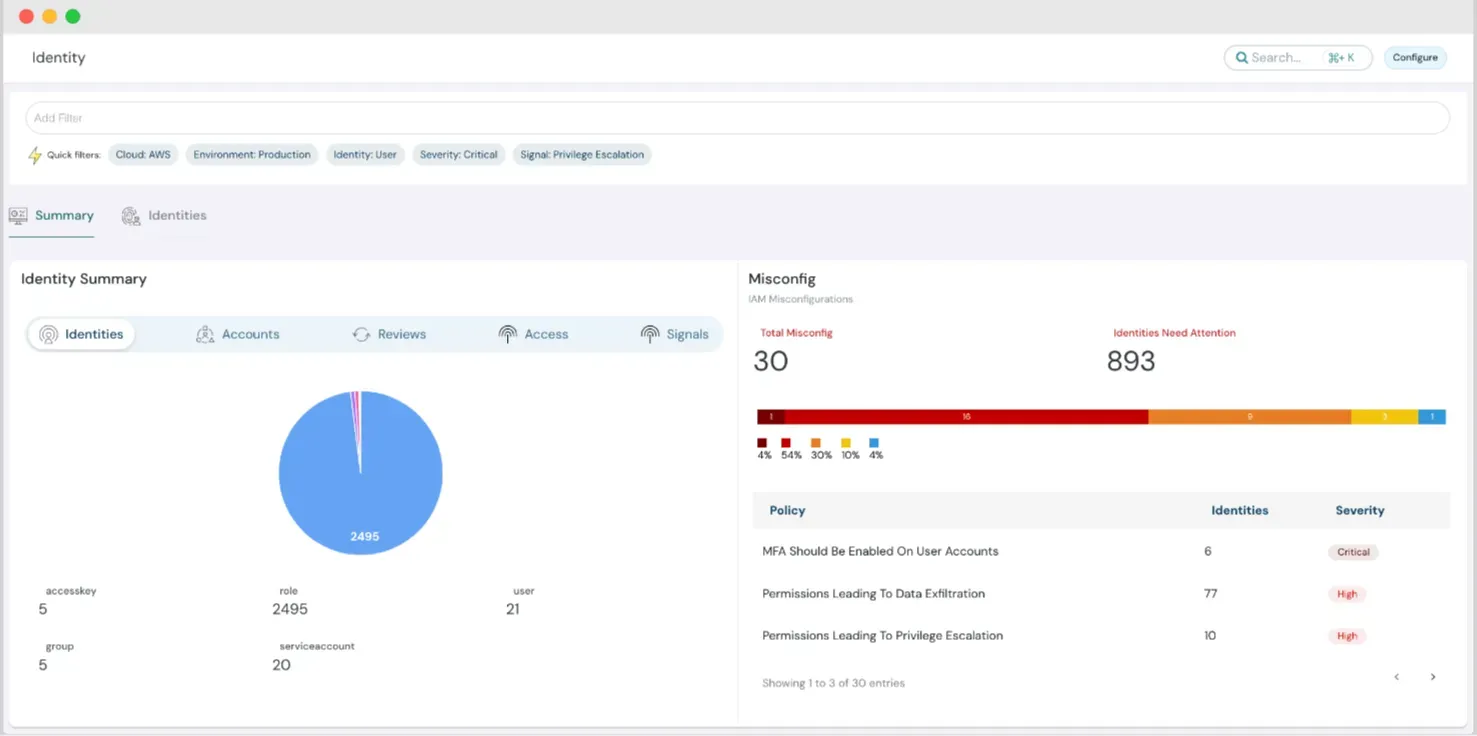
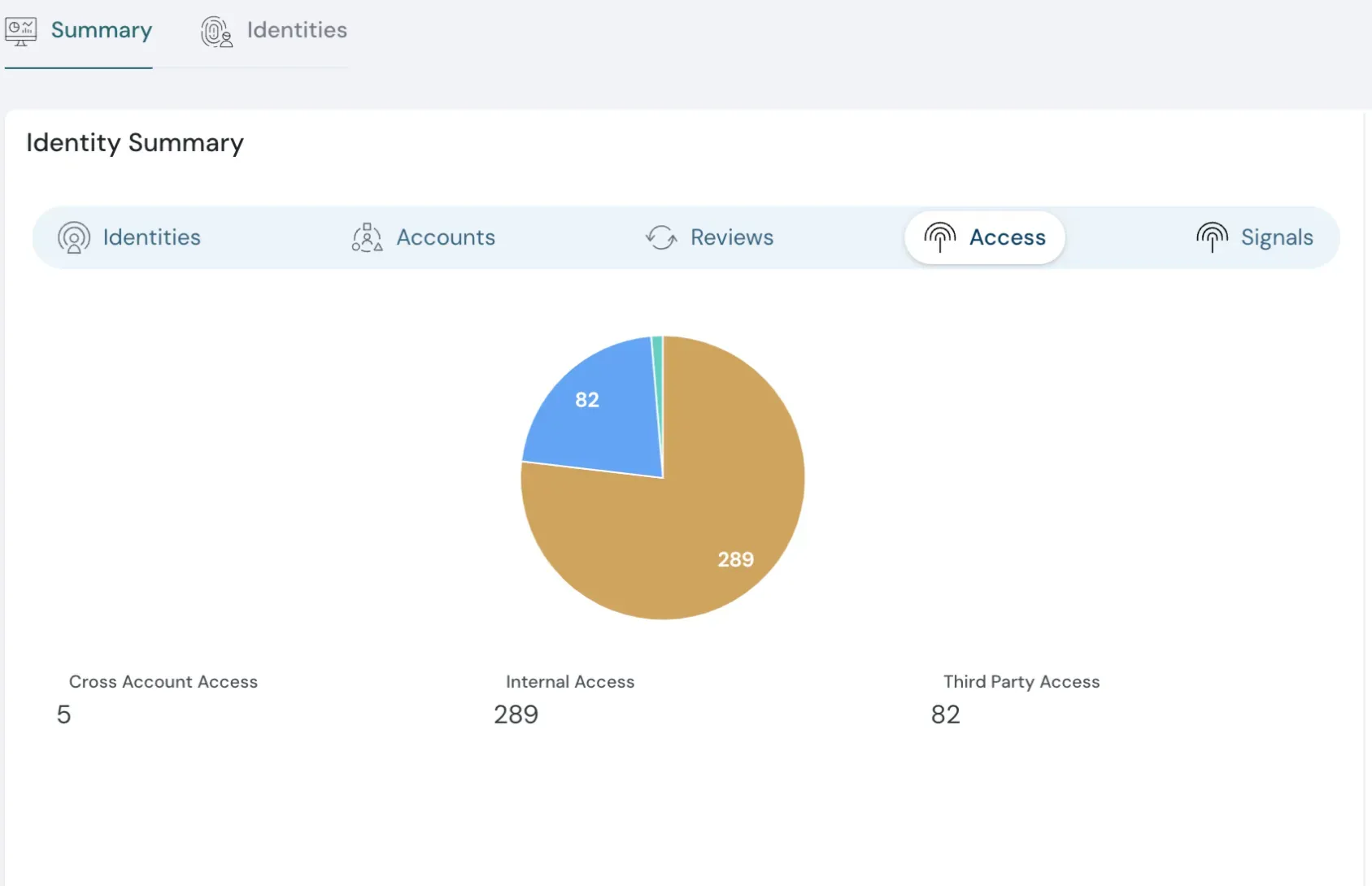
Track Non-Human Identities in Detail
Monitor Non-Human and Human identities, including third-party, cross-account, and internal access. Gain visibility into every access point, making it easier to secure your cloud and stay compliant.
Principle of Least Privilege with IAM Insights
Use advanced IAM insights and right-sizing capabilities to detect unused or excessive permissions. Enforce least privilege access and strengthen your security posture.
IAM Right-Sizing Recommendations
Cloudanix provides right-sizing suggestions based on actual user activity. Whether it’s defining a new policy or removing unused permissions, you get tailored recommendations to enforce granular access control.
Trusted by over 100+ customers worldwide
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedReading Resources
Why IAM Is Foundational to Modern Cloud Security
Identity and Access Management (IAM) is the first layer of defense in cloud security. Understanding IAM principles is critical for protecting access, enforcing least privilege, and ensuring accountability in your cloud infrastructure. Explore the key reasons why IAM must be a focus for security and compliance teams, especially in complex multi-cloud environments.
Why IAM Deserves Your Attention
If you're asking any of the questions below, you're already thinking like a cloud security architect:
CLOUDANIX
Insights from Cloudanix
Explore guides, checklists, and blogs that simplify cloud security and help you secure your infrastructure.
Case Studies
Real-world success stories where Cloudanix helped organizations secure their cloud infrastructure. Watch how we made a d...
What is Identity and Access Management?
Explore the various key areas of IAM that are evolving with the rise of AI and how all these changes are breaking the bo...
What is Just-In-Time (JIT) Access?
Discover the importance of Just-in-Time access in cybersecurity, its benefits, implementation, types, and challenges.
Role of AI in Identity and Access Management
Explore the various key areas of IAM that are evolving with the rise of AI and how all these changes are breaking the bo...
Cloudanix docs
Cloudanix offers you a single dashboard to secure your workloads. Learn how to set up Cloudanix for your cloud platform ...
Why IAM in the Cloud needs attention?
IAM is not a one-time fix; it requires ongoing attention and continuous improvement.
Changelog
A complete history of changes, improvements, and fixes for Cloudanix. Subscribe to get notified about the latest updates...
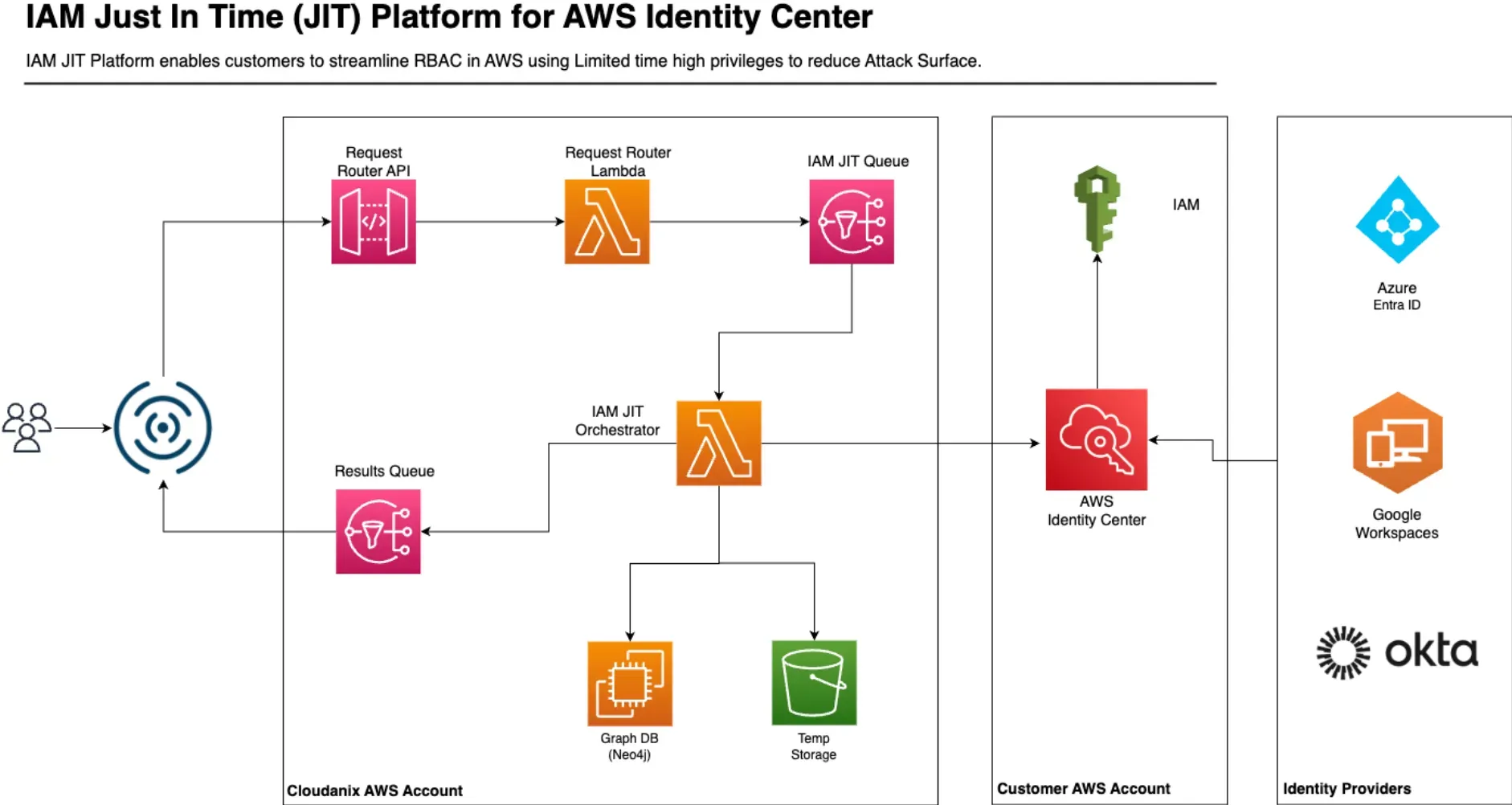
Integrate Just-In-Time IAM Access with AWS
Dive deep into how IAM JIT and AWS Identity Center can strengthen your IAM security posture and streamline identity work...

Safeguard Identity Across Multi-Cloud Environments
IAM tools weren’t built for today’s multi-cloud environments. Learn how to adapt your identity and entitlement managemen...
Demystifying Identity Access Management
Discover key considerations for setting up IAM, common vulnerabilities, and best practices for securing remote access an...
