CLOUDANIX
Cloud Security Posture Management (CSPM)
CSPM tool to improve your Cloud Security Posture. The vast majority of [cloud] mistakes are self-inflicted wounds—mistakes that the customer makes. Cloud security posture management (CSPM) tools create automated guardrails to ensure consistent security controls across workloads.
CSPM Helps You Avoid Common Cloud Mistakes
The vast majority of [cloud] mistakes are self-inflicted wounds—mistakes that the customer makes. Cloud security posture management (CSPM) tools create automated guardrails to ensure consistent security controls across workloads. —Gartner
What Do You Get With a CSPM?
A good CSPM tool should provide continuous visibility of your multiple clouds and monitor and identify misconfiguration vulnerabilities.
You should get to remediate these vulnerabilities either automatically or via self-serve before they become potential threats.
You should get to leverage the best practices and compliance such as SOC 2, GDPR, PCI, NIST 800-53, HIPAA, CIS, etc.
A good CSPM tool should have the capability to provide real-time alerts for misaligned events happening in the cloud infrastructure.
Cloud Security Posture Management (CSPM)
Achieve Cloud Hygiene With Built-In Remediation
CSPM mitigates the risk of misconfigurations as most of the successful attacks and threats on cloud services are due to the big M [Misconfigurations]. Cloudanix detects these misconfigurations and minimizes the risk of compromise. Misconfigurations are unintended actions from within the company setup. A CSPM continuously assesses, detects, and governs these threats in your cloud environments and helps remediate them.

Trusted by over 100+ customers worldwide
CLOUDANIX
Our Approach To Cloud Security Posture Management
Our approach to securing your public cloud infrastructure is a multi-pronged one. Organizations need complete visibility into their cloud assets, continuous monitoring for misconfigurations and the risks they carry, real-time reporting of these to not compromise their cloud infrastructure, and remediation to mitigate the threats. With Cloudanix, these are now possible. Our platform categorizes these features into 3 broad categories: Events, Misconfigurations and Assets.

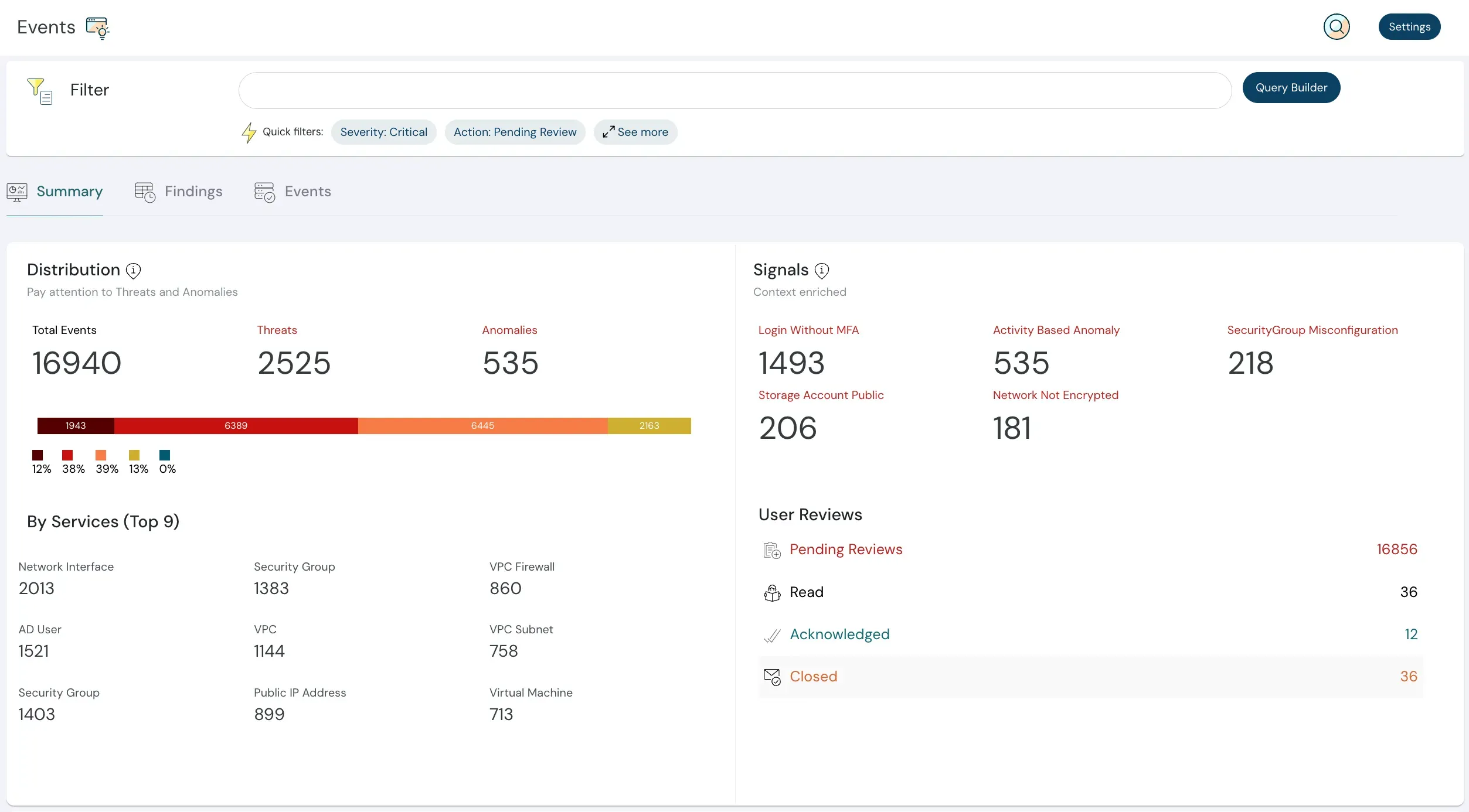
Events
With events, you get real-time reporting of changes happening in your cloud infrastructure. To control the signal from noise, you can subscribe to specific events which you deem essential. A detailed log is available to see exactly what happened, when and by whom. Any bad actors (external or internal) can be checked and almost immediately corrected.
Event Subscriptions
Subscribe to specific cloud events you deem important.
Detailed Audit Logs
Logs show what happened, when, and by whom to detect suspicious activity.

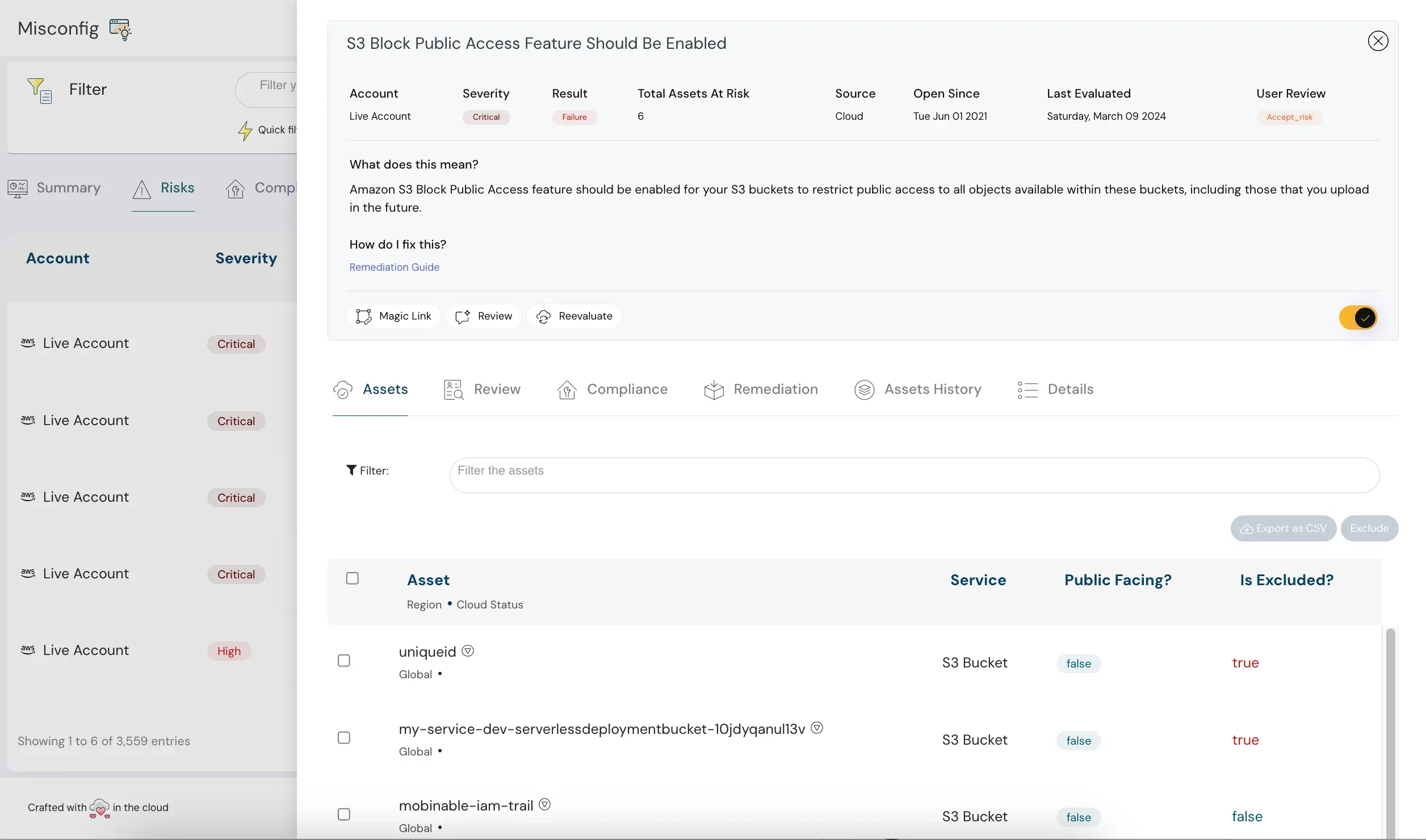
Misconfiguration
Misconfigurations help keep track of the risks you are exposed to. Timely detection can prevent any mishaps. While this is good to hear, there are times when you cannot worry about these misconfigurations occurring. Especially in highly productive environments where your development team is deploying code fast, the organization sometimes has limitations in using legacy systems. For these situations and more, Cloudanix has a novel feature where you can pause, acknowledge or accept the risk for a set amount of time or permanently.

Assets
Having complete visibility into all the assets of your cloud infrastructure can be a game changer. Cloudanix shows your assets across all the different regions with the metadata from a single dashboard. Here you can see the total assets, public-facing and otherwise. All this while calculating the drift and misconfigurations across the entire cloud infrastructure.
Your CSPM is here
Cloudanix CSPM Capabilities
From audit readiness to real-time alerting and remediation, Cloudanix offers a comprehensive suite of features for ensuring cloud security posture management. Here’s what you get with Cloudanix CSPM.
Audit and Compliance
For any enterprise, audit and compliance is essential for stakeholder and customer trust. Meeting legal requirements is no longer optional, and adhering to best practices is equally important. Cloudanix helps you meet standards like HIPAA, SOC 2, GDPR, and ISO 27001.
Asset Visibility
You can't secure what you can't see. Cloudanix provides complete asset visibility across your cloud environment. Enable transparency so teams can understand relationships between critical and non-critical assets.
Drift, Misconfiguration and Baseline
Internal oversights are a leading cause of security issues. With Cloudanix, detect drifts and misconfigurations in real-time to prevent potential breaches and protect sensitive data.
Real-Time Alerting
In a fast-paced DevOps world, real-time alerts are crucial. Cloudanix notifies you the moment vulnerabilities are introduced—helping you patch issues before they’re exploited.
Cloud Misconfiguration Remediation
Cloudanix helps you set automated, policy-driven remediation actions. With custom playbooks and built-in rules, reduce human error and enforce a secure, productive cloud environment.
Continuous Monitoring
Detect threats, anomalies, and unauthorized behaviors continuously. Cloudanix prioritizes risks so you can act before damage occurs—making it a core part of any robust CSPM solution.
It's Never Too Early to Secure Your Cloud
When Do You Need a CSPM Tool?
If you're operating in the cloud and care about security, a CSPM tool should already be on your radar. Cloud misconfigurations are one of the most common causes of data breaches — and they’re almost always avoidable. If you answer *yes* to most of the questions below, it's time to explore how CSPM can help.
You're Ready for CSPM If...
These are common signs that your organization will benefit from Cloud Security Posture Management:
- Is your data residing on the cloud?
- Despite having a backup, you do not feel safe?
- Are you serious about security?
- Does the reputation of your organization matter to you?
- Is your cloud environment growing/going to grow?
- Do you feel the need for continuous monitoring for threats?
- Do you want to map and identify unused assets and resources consumed and save precious time and money?
- Do you want to verify the integrity of recent deployments?
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedYour questions answered.
Frequently Asked Questions
Everything you need to know about Cloud Security Posture Management (CSPM) — its role, value, and why modern cloud-native environments can't live without it.
Solutions For Roles
How Cloudanix Helps Different Teams
Whether you're leading security strategy or maintaining day-to-day cloud health, Cloudanix equips every role with the tools needed to ensure security, compliance, and visibility.
CISOs
As a CISO, your job is to continuously secure the environment and find ways to advance your organization’s security. Cloudanix gives you a unified view and actionable insights to make strategic decisions.
DevSecOps
With new code being continuously pushed, you're responsible for maintaining and improving cloud security. Cloudanix integrates into your CI/CD pipeline to prevent issues before they ship.
Cloud Security Professionals
Cloudanix cuts the complexity of maintaining the highest standards of compliance and reduces the attack surface of your cloud infrastructure—giving you more control, with less manual work.
GRC Teams
Maintain the highest governance and compliance standards. With Cloudanix, gain high visibility, seamless integrations, and powerful prevention and remediation tools to keep your cloud secure.
CLOUDANIX
Insights from Cloudanix
Explore guides, checklists, and blogs that simplify cloud security and help you secure your infrastructure.
Case Studies
Real-world success stories where Cloudanix helped organizations secure their cloud infrastructure. Watch how we made a d...

What is CSPM?
Understand what Cloud Security Posture Management (CSPM) is and how it automates security and compliance across cloud en...
CASB, CSPM, SIEM: Cloud Security Essentials
Understand how CASB, CSPM, and SIEM work together to enhance your cloud security posture and ensure better governance.
What is Cloud Audit?
In-depth assessment of cloud environment for security, compliance, and optimization. Identify vulnerabilities, ensure da...
Top 10 Challenges of CSPM
Cloud environments are getting more complex and dynamic day by day, making it difficult to gain complete visibility into...
Cloudanix docs
Cloudanix offers you a single dashboard to secure your workloads. Learn how to set up Cloudanix for your cloud platform ...
Changelog
A complete history of changes, improvements, and fixes for Cloudanix. Subscribe to get notified about the latest updates...
