Best Cloud Security Platform For IAM Teams
IAM Professional
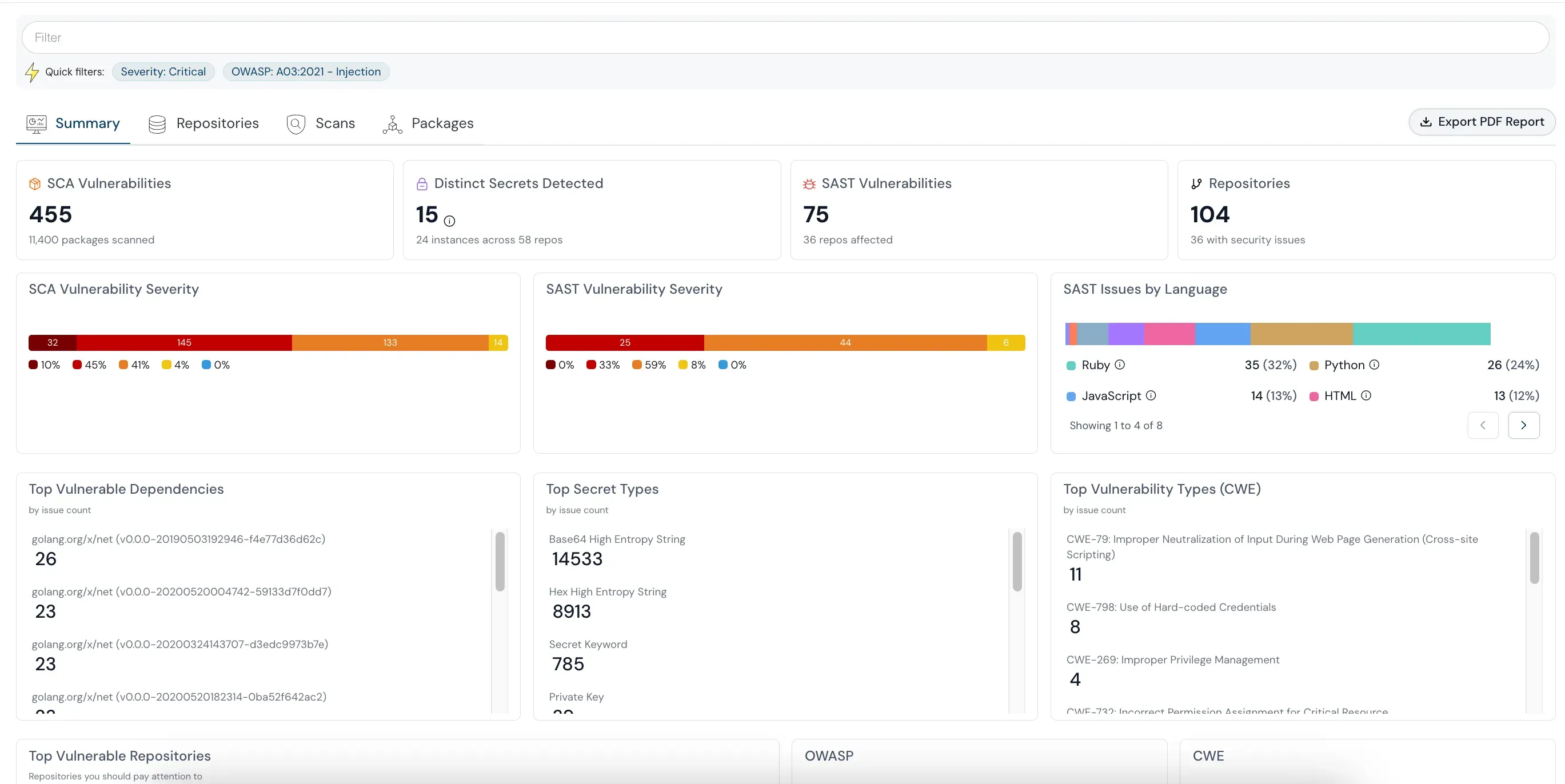
Why is the IAM team so important? Today innovation and migration to the cloud is happening at lightning speed. Moving operations to the cloud does streamline processes but brings with it a host of risks. Especially for an IAM team as identity and privileged access for hundreds and thousands of human and machine processes. The IAM team is tasked with the gargantuan task of securing access entitlements and cloud security posture of these thousands of identities in a multi cloud environment.
Built for Cloud Security Teams Navigating Complexity
How Cloudanix Helps Cloud Security Professionals
It’s never too early to think about security. If your answer is yes to most of these questions below, then you are ready for a CSPM tool. Cloudanix empowers Cloud Security professionals with real-time visibility, control, and automation across multi-cloud environments — all from one unified platform.
Core IAM Team Capabilities
Comprehensive IAM management across AWS, Azure, and GCP with continuous monitoring and enforcement.
- A single dashboard for all your three clouds - AWS, Azure, and GCP - showing IAM exposure across team members and service accounts.
- Implementation of the path of Least Privilege.
- Identification and analysis of excess permissions.
- Continuous discovery of all entities, policies, and configurations.
- Secure multi-cloud visibility to manage and investigate identities and permissions.
- Detecting anomalies and configuration changes.
- Define and automate guardrails, enforce policies, and Shift Left security.
- Mitigate risky privileges and misconfigurations.
- Ensure compliance with highest standards like CIS, HIPAA, SOC 2.
IAM Just In Time (JIT)
Grant permissions only when needed, with full audit and approval workflow.
How Cloudanix Stands Out For IAM Governance

Give permissions when needed - Just In Time!
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedCLOUDANIX
Insights from Cloudanix
Explore guides, checklists, and blogs that simplify cloud security and help you secure your infrastructure.

AI Code Remediation
Learn how AI code remediation automates the process of finding and fixing software vulnerabilities. Discover various tec...

What is Code Security?
Learn about code security fundamentals, OWASP Top 10, security tools like SAST/DAST, and best practices for embedding se...
Cloudanix docs
Cloudanix offers you a single dashboard to secure your workloads. Learn how to set up Cloudanix for your cloud platform ...
Write Vulnerability-Free Code
A comprehensive guide to secure coding practices, covering vulnerabilities, prevention techniques, and industry standard...
Changelog
A complete history of changes, improvements, and fixes for Cloudanix. Subscribe to get notified about the latest updates...
Privacy by Design
A framework for embedding privacy into the entire product development lifecycle, ensuring it is a proactive consideratio...
