CLOUDANIX
Multi-Cloud Compliance
Improve your Cloud Security Posture with minimal efforts
Cloud Compliance Made Easy!
Today every company, irrespective of its size, runs workloads in the Cloud. To safeguard your business and consumer data, a robust security posture should be achieved too. Cloudanix makes it easy for our customers to ensure that end user's data is safe by ensuring that all the Compliance controls are adhered.
What is Cloud Compliance?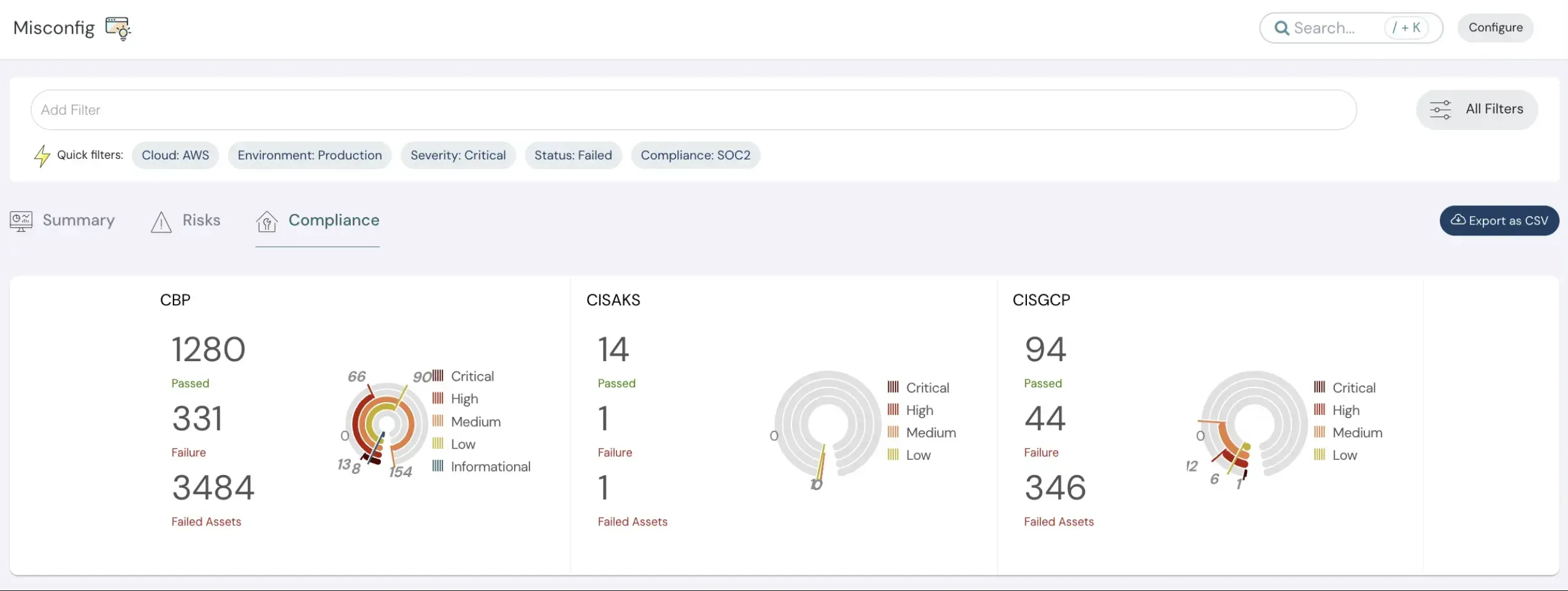
Monitoring & Compliance
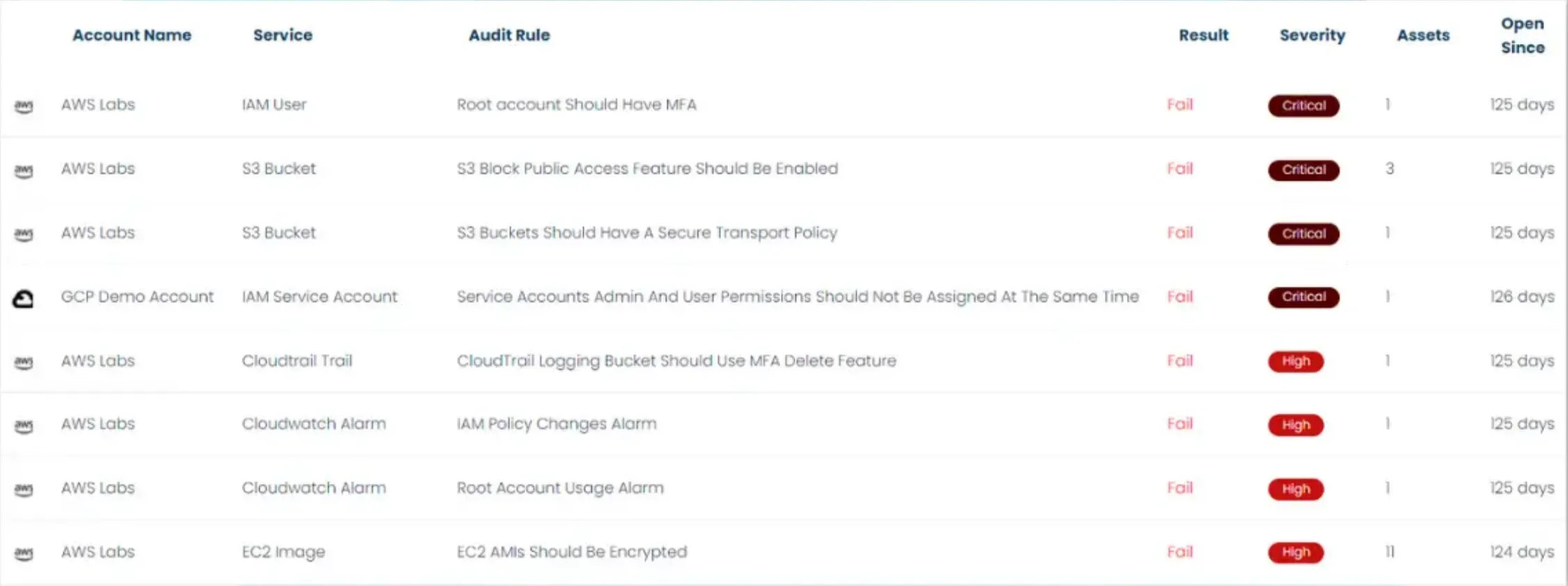
There's always a critical need to meet compliance requirements while improving your security posture. Cloudanix provides continuous compliance capabilities as part of its CSPM tooling, helping your team stay audit-ready and compliant at all times.
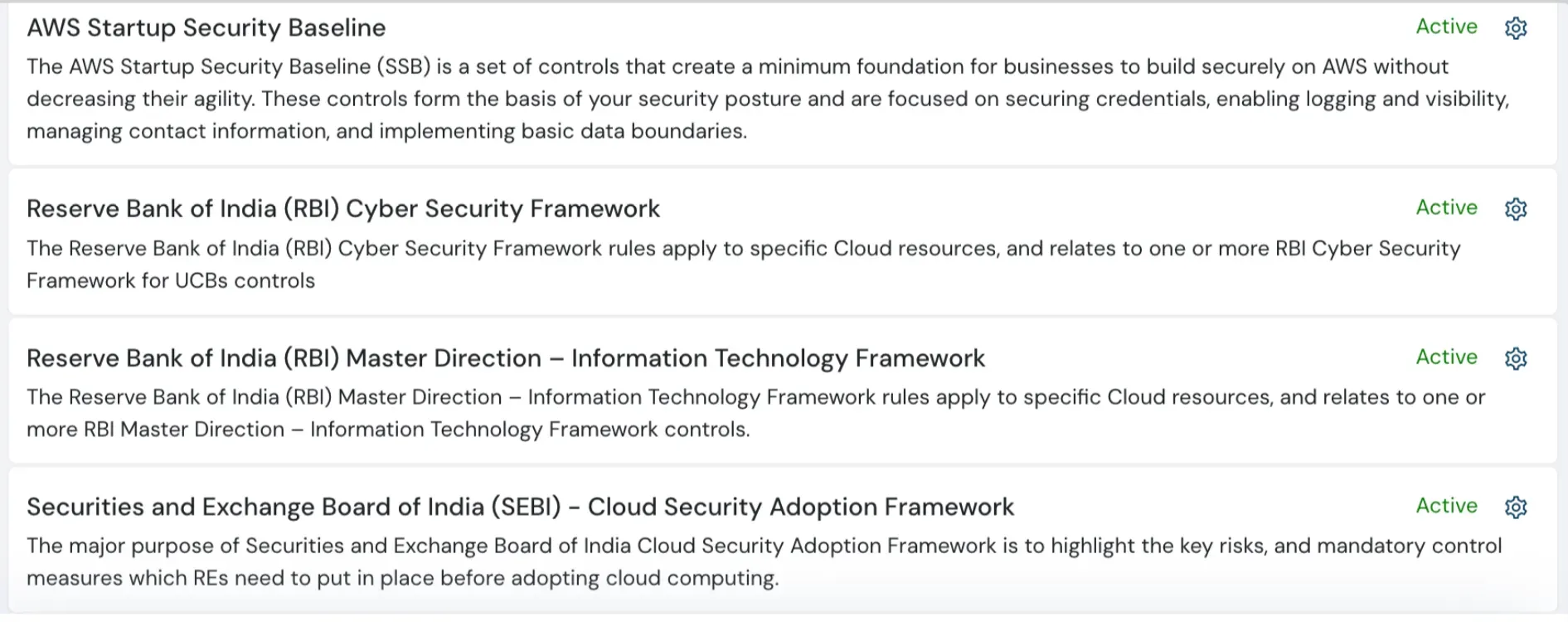
RBI & SEBI Compliance Packs
RBI and SEBI have introduced new compliance requirements for our Indian customers. In response, we've launched Compliance Packs. These not only allow customers to monitor compliance but also enhance security posture in accordance with RBI & SEBI guidelines.
Trusted by over 100+ customers worldwide
Your Compliance Hub
All Compliance Standards Under One Umbrella
Cloudanix supports all major compliance frameworks—simplifying audit readiness and helping you stay secure across industries like finance, healthcare, and cloud-native SaaS.
APRA
APRA oversees banking, insurance, and superannuation institutions to promote Australia's financial stability.
Read MoreCIS
CIS Controls are 20 prioritized actions developed by SANS to help secure organizational assets and data from known attack vectors.
Read MoreGDPR
GDPR enforces data privacy and protection laws in the EU and EEA. It governs how organizations handle personal data.
Read MoreHIPAA
HIPAA ensures the privacy and security of Protected Health Information (PHI) in the U.S. healthcare and insurance sectors.
Read MoreISO 27001
ISO 27001 is the global standard for information security, published by ISO and IEC, focused on risk management and controls.
Read MoreMAS
MAS TRM Guidelines help financial firms in Singapore manage tech risk, secure systems, and protect sensitive data.
Read MoreNIST
NIST provides technology, measurement standards, and frameworks used widely across U.S. federal and enterprise systems.
Read MorePCI DSS
PCI DSS outlines technical and operational standards to protect cardholder data for organizations handling payment information.
Read MoreSOC 2
SOC 2 reports assess how well your systems safeguard customer data based on 5 trust principles: security, privacy, availability, confidentiality, and processing integrity.
Read MoreSOC 1
SOC 1 audits evaluate internal controls related to financial reporting, used by auditors and regulators.
Read MoreHITRUST
HITRUST provides a comprehensive and certifiable framework for managing risk and compliance across healthcare, finance, and tech industries.
Read MoreFedRAMP
FedRAMP provides standardized security assessment and authorization for cloud services used by U.S. federal agencies.
Read MoreISO 27017
ISO 27017 provides cloud-specific security controls and guidelines supplementing ISO 27001 for cloud service providers and customers.
Read MoreNIS2 Directive
NIS2 Directive is the EU's updated cybersecurity legislation establishing comprehensive security requirements for essential and important entities.
Read MoreNIST CSF
NIST Cybersecurity Framework provides a risk-based approach to managing cybersecurity organized around Govern, Identify, Protect, Detect, Respond, and Recover functions.
Read MoreEssential 8
Essential Eight is Australia's baseline cybersecurity mitigation strategies developed by the Australian Cyber Security Centre (ACSC).
Read MoreKSA PDPL
Saudi Arabia PDPL is a comprehensive personal data protection law applying to all organizations processing personal data in the Kingdom of Saudi Arabia.
Read MoreCloudanix Best Practices
The Cloudanix Best Practices Framework complements CIS Benchmarks and provides extra guidance to prevent misconfigurations.
Read MoreCloud Security | Audit and Compliance | Cloudanix
Cloud + Compliance + Complexity
There is a general belief that Cloud Compliance is very complex. We do agree that innovation demands your team to move fast. Sometimes, this could result in missing out on "Best Practices" — compromising security and becoming non-compliant. At Cloudanix, we understand this and have built our Compliance recipe to help you and your business stay compliant.
A Happy Cloudanix User
AWS Cloud Multiple Accounts Uses CSPM and CIEM "Cloudanix has helped us address misconfiguration and workload vulnerabilities in AWS, which otherwise would have gone unnoticed. Integration of multi-accounts and having a reliable risk score associated with each account keeps us informed about the security stature of all our cloud accounts in a single view and helps maintain it." — Bhargav Garimella, MoveInSync
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedCLOUDANIX
Insights from Cloudanix
Explore guides, checklists, and blogs that simplify cloud security and help you secure your infrastructure.
Case Studies
Real-world success stories where Cloudanix helped organizations secure their cloud infrastructure. Watch how we made a d...
What is Cloud Compliance?
Master Cloud Compliance! Our in-depth guide explains what it is, its importance, governance differences, & top 5 complia...
Establishing an Auditable Emergency Access Process for Critical Resources
Establish a secure, auditable break glass procedure for emergency access to critical systems.
Cloudanix docs
Cloudanix offers you a single dashboard to secure your workloads. Learn how to set up Cloudanix for your cloud platform ...
What is Cloud Audit?
In-depth assessment of cloud environment for security, compliance, and optimization. Identify vulnerabilities, ensure da...
Changelog
A complete history of changes, improvements, and fixes for Cloudanix. Subscribe to get notified about the latest updates...

Safeguard Identity Across Multi-Cloud Environments
IAM tools weren’t built for today’s multi-cloud environments. Learn how to adapt your identity and entitlement managemen...
Podcast
Tune in to the Cloudanix podcast for expert discussions on cloud security, compliance, and the latest industry trends. L...
