How to use CSPM to detect and remediate cloud misconfigurations
Introduction
Cloud misconfigurations are errors or gaps in the configuration of cloud resources that can expose systems and data to security risks. These misconfigurations can be caused by human error, a lack of understanding of cloud security best practices, or changes to the cloud environment that were not properly implemented.
Cloud misconfigurations can have serious consequences, including data breaches, malware infections, and ransomware attacks, sometimes leading to compliance violations and financial losses as well.
Some common examples of cloud misconfigurations include:
- Insecurely configured storage
- Unrestricted access to cloud resources
- Outdated software
- Weak passwords and default credentials
- Lack of logging and monitoring
What is CSPM?
CSPM is Cloud Security Posture Management. When an organization starts to use a public cloud solution, they also have a shared responsibility of owning the security of their cloud account which is running their cloud workloads. To ensure that their cloud accounts have a robust security posture, CSPM should be adopted.
Understanding Cloudanix’s CSPM
Cloudanix provides an intuitive and easy-to-use dashboard that enables detection and mitigation of misconfigurations with ease. In the console the misconfig, assets, identity, and events tabs help with CSPM. This can be seen on the menu to the left of the console.

Events
Real-time happenings of your cloud infrastructure are displayed here. A highly configurable feature that alerts you within a minute of any untoward activity. Cloudanix allows you to customize the alerts you receive by severity across multiple channels like Slack, PagerDuty, MS Teams, Email, and Webhooks.
Misconfig
This tab as the name explains displays the miscongfigurations in your cloud and maps them to the relevant compliance families. Here it also shows you how the misconfigurations are distributed between your cloud, identities, and workloads.
Assets
Here you can see your entire asset inventory comprising databases, storage buckets, containers, etc, and the regions they are spread across. Cloudanix also displays the attack path which means you get to visualize how an attacker can get into your system.
Identity
One of the most important yet ignored aspects of attaining a great CSPM. A complete breakdown of users, roles, groups, service accounts, and access keys. This means you can see over-privileges and rightsize them.
Cloudanix step-by-step guide for achieving a great security posture
With just a few simple steps, you can find your remediation for any particular misconfiguration in place.
- Log in to your Cloudanix dashboard and click on “Misconfig” tab.(marked as 1 in the image below)
- Inside Misconfig, you will see three tabs Summary, Risks, and Compliance.
- Summary: Displays the misconfiguration score at a high level as shown in the image above.
- Risks: The risks tab (marked as 2 in the image) shows the list view of all misconfigurations that are affecting your organization’s cloud.
- Compliance: Here you can see the compliance families to which the misconfigurations are mapped. (marked as 3 in the image)
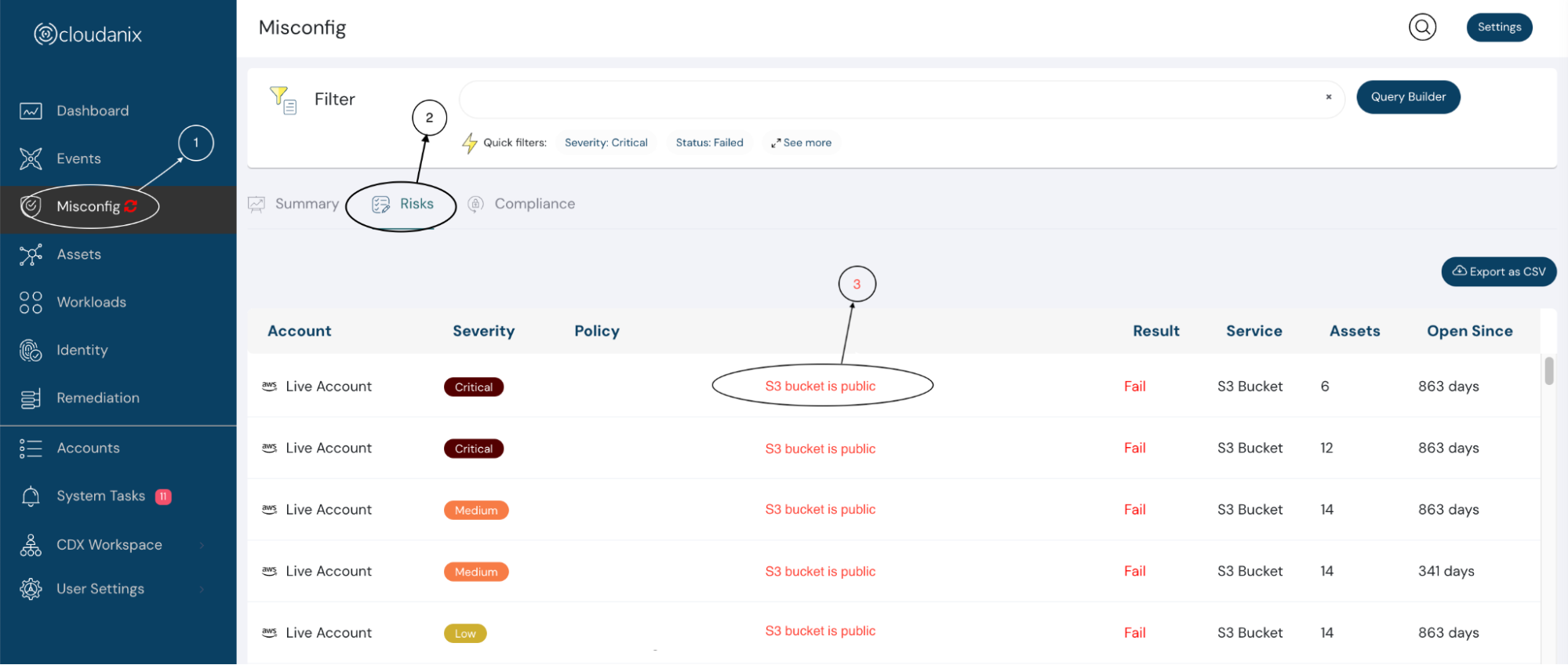
- Now, select the policy that you want to resolve / remediate (marked as 3 in the below image). It will open a slideout for you showing all the required details.
- Once the slideout opens, click on the Remediation tab (Marked as 4 in the image shown below). You are now ready to remediate your risks in an automated or manual manner. P.S.: Auto remediation cannot be available in all cases to prevent breaking your workloads, however, every misconfiguration has a manual remediation documentation. Cloudanix makes remediation available in 2 clicks. You now have multiple remediation recipes that you can resolve by going to the AWS console, CLI, or using Python.
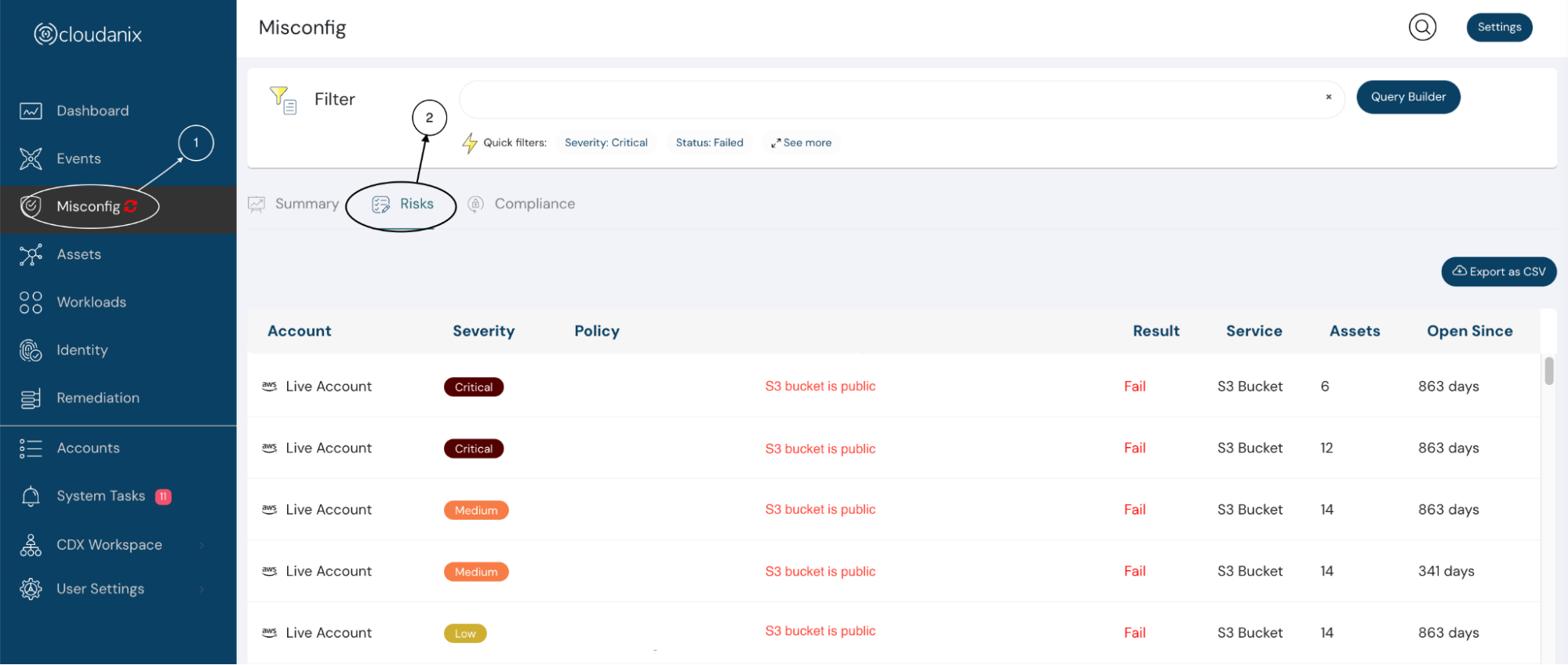
**Data reflecting in the image is for understanding purpose only**

"Simplicity is one step towards tool adoption. Cloudanix focuses on how easily it can help in achieving a great security posture."
- Purusottam Mupunu, Co-founder & CTO, Cloudanix