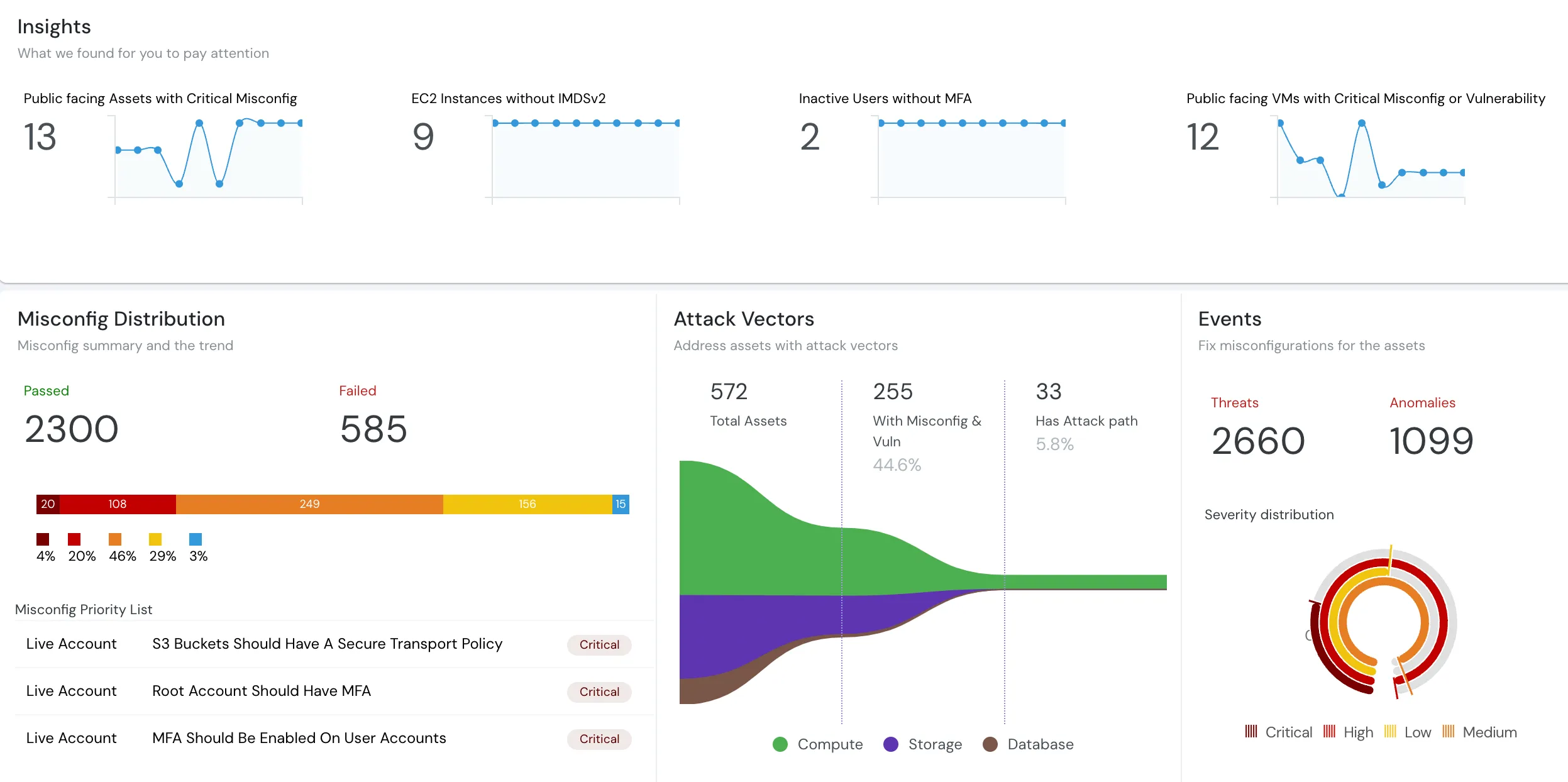
Cloud Asset Management - Explained
Cloud asset management is the process of identifying, tracking, and managing all of the assets that are associated with cloud computing. This includes physical assets, such as servers and storage, as well as virtual assets, such as container images and Kubernetes clusters. It also includes the management of software licenses, security posture, and compliance.
Cloud Asset Management is an essential part of any cloud computing strategy. By implementing Cloud Asset Management, organizations can optimize their cloud spending, improve their security posture, and ensure compliance.
What is the importance of Cloud Asset Management?
There are a number of reasons to have cloud asset management in place. We have discussed a few of them that go as follows:
Complex and dynamic cloud environments
Cloud users typically have a wide range of cloud assets, including physical infrastructure, virtual machines, container images, Kubernetes clusters, and software licenses. These assets are often distributed across multiple cloud providers and regions. This complexity can make it difficult to track and manage cloud assets manually.
Valuable and vulnerable cloud assets
Cloud assets contain sensitive data, such as customer information, financial data, and intellectual property. This makes them attractive prey for attackers. Cloud users need to have Cloud Asset Management in place to protect their assets from unauthorized access, theft, and loss.
Compliance requirements
Many industries are subject to regulations that require organizations to implement certain security measures. CAM can help organizations comply with these regulations by providing visibility into their cloud assets and helping them to identify and remediate security vulnerabilities.
Specific Benefits of Cloud Asset Management
Security improvement
Cloud asset management can help cloud users identify and remediate security vulnerabilities, which can reduce the risk of data breaches and other security incidents.
Compliance improvement
Cloud asset management can help cloud users comply with industry regulations and standards.
Improved visibility and control
Cloud asset management can provide cloud users with a centralized view of all of their cloud assets, which can help them improve their visibility into and control over their cloud environment.
Increased efficiency and productivity
Cloud asset management can automate many of the tasks involved in managing cloud assets, which can free up IT teams to focus on other important tasks.
Cost optimization
Cloud asset management can help cloud users identify and eliminate unused or underutilized resources, which can lead to significant cost savings.
What are the challenges of Cloud Asset Management?
There are various challenges of Cloud Asset Management that are faced by Cloud security teams. Below are a few:
Securing a dynamic and distributed cloud environment
Cloud environments are constantly changing, with new assets being provisioned and decommissioned on a regular basis. This can make it difficult to keep track of all assets and ensure that they are all properly secured.
Lack of integration between cloud security tools
Many security teams use a variety of cloud security tools, but these tools are often not integrated with each other. This can make it difficult to get a complete view of the security posture of the cloud environment and to respond to threats effectively.
Ensuring compliance with security regulations
Security teams need to ensure that their cloud environment is compliant with all applicable security regulations. This can be a complex and challenging task, as regulations can vary from country to country and industry to industry.
Detecting and responding to threats against cloud assets
Cloud assets are often targeted by attackers, who exploit vulnerabilities in software, configuration errors, and human error to gain access to systems and data. Security teams need to be able to detect and respond to these threats quickly and effectively.
Keeping up with the latest cloud security threats and vulnerabilities
Cloud security threats and vulnerabilities are constantly evolving, and security teams need to keep up with the latest developments in order to protect their cloud environments.
Managing the cost of cloud security
Cloud security can be expensive, especially for large organizations with complex cloud environments. Security teams need to find ways to manage the cost of cloud security without sacrificing security.
How can Cloud Asset Management tools help organizations mitigate their challenges?
Securing a dynamic and distributed cloud environment
CAM tools provide visibility into all cloud assets, regardless of where they are located. This helps security teams identify and remediate security vulnerabilities before they are exploited.
These tools can enforce security policies across all cloud assets—ensuring that all assets are updated with security patches and access is properly restricted.
Detecting and responding to threats
CAM tools monitor cloud activity for unusual or suspicious behavior (login attempts, network traffic, file access) and can automate responses such as blocking access or isolating infected assets.
Ensuring compliance
CAM tools help security teams by offering visibility into the security posture of the environment and generating compliance reports.
Integrating with existing security tools
They help consolidate various tools into one platform, improving threat response and giving a complete security view.
Staying updated on threats
CAM tools often include security intelligence feeds to keep teams updated on the latest vulnerabilities and threats.
Best Practices of Cloud Asset Management
Organizations can get started with their cloud asset management by following some basic hygiene in their cloud environment.
1. Create a comprehensive inventory of your cloud assets
Identify all infrastructure, VMs, containers, clusters, licenses, etc. Use spreadsheets, cloud consoles, or specialized tools like CIM or CIEM.
2. Develop policies and procedures
Define rules for provisioning, patching, configuration, decommissioning, and securing assets—tailored to your organization and updated regularly.
3. Regular reviews of asset inventory and posture
Helps identify unused assets or vulnerabilities. Always review before/after major environment changes.
4. Implement a response process for security incidents
Include steps for detecting, investigating, mitigating, and communicating security issues.
Additional Tips
- Use tags to organize and track assets.
- Use version control to track asset changes.
- Automate asset management wherever possible.
- Document all processes and policies.
- Train staff on CAM best practices.
People Also Read
- What is Cloud Compliance?
- A Big List Of Mistakes AWS Cloud Users Have Done And Spent Millions
- Top 12 Container Security Best Practices
- Use Case: Cloud Asset Visibility
Let me know if you’d like this saved in a .md file or structured differently for Astro or a CMS.
