What is Cloud Security Posture Management?
Cloud Security Posture Management - A detailed explanation
What is Cloud Security Posture Management?
Cloud Security Posture Management (CSPM) are solutions used for securing public clouds like AWS, Azure, GCP, DigitalOcean and others.
A CSPM tool automates cloud security across multiple clouds and diverse infrastructures. This makes possible continuous monitoring of cloud environments and has an option of remediating the security issues automatically. CSPM covers but is not limited to GRC, Misconfiguration, Drift, and Real-time visibility into what’s going on inside your cloud. With a CSPM tool, you can map and identify unused assets and resources, giving you complete visibility of all the assets in your cloud.
What is the scope of CSPM?
Tools, practices, and methodologies make a good CSPM that enables organizations to proactively identify, assess, and manage potential security risks and vulnerabilities in their cloud environments. At the core, it must continuously monitor the cloud environments for adherence to security policies and compliance requirements.
Why is CSPM important?
Organizations today perform their business operations at a global level and want to stay compliant without interrupting their business operations. To beat the competition, organizations also need to be innovative and thus adapt cloud, multi-cloud, and several other cloud-related technologies given their operational strengths and qualities.
While these innovations and experiments are proven to be beneficial to organizations, they are also accepting the fact that their assets (in general) are at risk due to misconfigurations. As all of us are aware, cloud misconfigurations can bring various operational business challenges not just limited to data breaches but also compliance violations, increased operational costs and complexities, and similar.
A good CSPM helps cloud users tackle most of these challenges by detecting and remediating misconfigurations into a single console, reducing complexities for security teams. Let us understand - Apart from improved security posture, what are some proven reasons why CSPM is important for cloud users?
Rapid Cloud Adoption and Complexity
As mentioned above, Organizations are rapidly migrating to the cloud, often adopting multiple cloud providers and services. This increased complexity makes it incredibly difficult for security teams to maintain visibility and control across their entire cloud environment. CSPM tools provide a centralized view, simplifying management and reducing blind spots.
Constant Change & Configuration Drift
Cloud environments are highly dynamic. Frequent infrastructure changes, updates, and misconfigurations can introduce vulnerabilities and security gaps. CSPM solutions continuously monitor for these changes, detect deviations from security best practices, and alert security teams in real-time.
Rise of Cloud-Native Threats
New threats specifically targeting cloud environments are constantly emerging. These include attacks on cloud APIs, serverless functions, and containerized applications. CSPM tools can identify these emerging threats and provide the necessary visibility and controls to mitigate them effectively.
Compliance & Regulations
Many industries have strict compliance regulations (e.g., GDPR, HIPAA, PCI DSS) that require organizations to maintain a secure cloud environment. CSPM tools help organizations demonstrate compliance by automating security checks, generating audit trails, and providing evidence of security controls.
Limited Security Expertise
Many organizations lack the in-house expertise for various reasons such as lack of awareness, expertise, insufficient funds, etc to effectively secure their complex cloud environments. CSPM tools provide automated solutions and actionable insights, empowering security teams with the knowledge and tools to address critical security issues.
Proactive Threat Hunting & Prevention
Many organizations think of CSPM as a basic vulnerability scanning tool. In reality, CSPM solutions today, go beyond basic vulnerability scanning. They employ advanced threat-hunting techniques to proactively identify and investigate suspicious activity, enabling organizations to prevent attacks before they can cause significant damage.
Cost Optimization
Misconfigurations and security vulnerabilities can lead to wasted resources and increased costs. CSPM tools help identify and remediate these issues, optimizing resource utilization and reducing cloud spending.
These are just a few of the key reasons why CSPM is more important than ever in the cloud security domain. As cloud environments continue to evolve and become more complex, the role of CSPM will only become more important.
Additionally, leveraging a CSPM is just a starting point, and we recommend organizations to further evaluate their security landscape and keep adding more layers of security as and when required.
What are the advantages of using Cloud Security Posture Management?
CSPM is very important for cloud security. Misconfigurations in cloud environments are a common cause of security breaches.
According to Gartner, “The vast majority of [cloud] mistakes are self-inflicted wounds—mistakes that the customer makes. Cloud security posture management (CSPM) tools create automated guide rails to ensure consistent security controls across workloads.”
Cloud infrastructure security is both the cloud provider’s and the user’s responsibility.
The shared responsibility principle includes the following:
- Things like the correct configuration of the cloud.
- Right-sizing IAM permissions.
- Identifying the crown jewels.
- Protecting the data.
CSPM solutions are pivotal in continuously checking for misconfigurations that can lead to data breaches and leaks. CSPM provides automated detection and monitoring capabilities and enables organizations to make necessary changes continuously, reducing the risk of unnoticed misconfigurations.
Misconfigurations often occur unintentionally. Due to the programmable nature of public clouds, the risk of these misconfigurations is very high and easy, putting the users of these cloud platforms at significant risk. These misconfigurations often arise due to the mismanagement of interconnected resources where the practitioners might be looking at a single resource and sometimes need help understanding the entire picture. For example, lacking visibility and a deep understanding of resource interactions can lead to applying for overly permissive permissions across resources, neglecting the principle of least privilege.
Enterprise environments have become increasingly complex, with the tech stack getting more options. This makes tracking and maintaining large numbers of resources and accounts challenging. Developers may inadvertently set liberal permissions or lose track of critical assets as business wants to operate at the speed of light. Also, lack of upskilling means that not all cloud operators know what it takes to stay secure 24x7.
CSPM solutions address the above challenges as follows
- Provide visibility into public cloud infrastructure.
- Allow organizations to gain insights into the number of cloud resources running and configurations.
- Detect and address misconfigurations so that they do not go undetected for extended periods compromising the security of the data and workloads.
- CSPM tools which do not provide automation are not scalable for organizations and will rather waste a lot more team time and effort.
The key areas below are necessary for any modern and effective CSPM platform
- 24x7 assessment of compliance policies: 1-time assessment is a thing of the past. Your CSPM should ensure a continuous assessment and upgrade and map new services to compliance controls.
- Realtime threat detection: Any change in the infrastructure should be assessed for threats, anomalies, and potential attacks and reported to the user using preferred notification channels.
- Incident response management: A central dashboard that integrates with project management tools like Jira, Asana to review the detection, quarantine, and remediation of threats originating within the cloud environment and detected by the CSPM platform.
- Risk identification: Identify and classify risks to maintain robust cloud security and drive prioritization.
CSPM solutions are essential for securing cloud configurations and safeguarding sensitive data. Organizations across all verticals, including Financial institutions and healthcare providers, rely on CSPM tools to protect their valuable information.
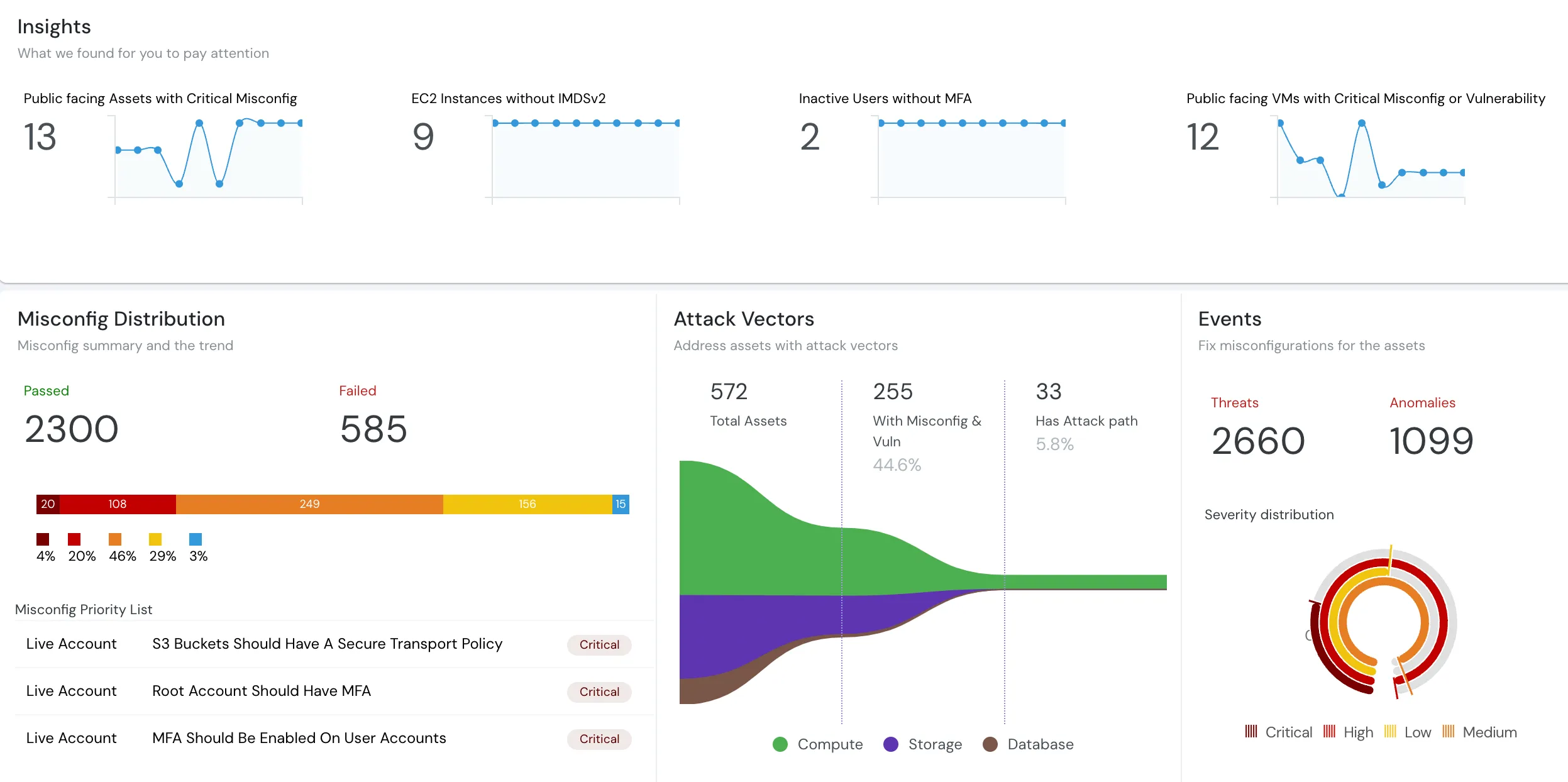
In addition to its core security functions, CSPM offers additional advantages. It can identify unused assets, map security team workflows, verify the integrity of recently deployed systems, and provide insights into the most utilized technologies. These capabilities enable organizations to optimize resource allocation, reduce costs, identify training opportunities, and leverage CSPM as a comprehensive solution for their cloud environment.
How Does CSPM Work?
Understanding how CSPM plays a role in improving and enhancing security infrastructure is important. In this section, we will understand the working of CSPM in 5-6 easy steps.
1. Cloud Environment Discovery
A CSPM tool starts by discovering and mapping the entire cloud infrastructure. This generally includes identifying all your cloud resources (e.g. servers, storage, databases, etc.) across different providers like AWS, Azure, and GCP.
2. Configuration Analysis
The tools continuously analyze the configurations of these resources. This involves checking for things like:
- Misconfigurations: Incorrectly configured firewalls, open ports, weak passwords, improper access controls, etc.
- Policy Violations: Deviations from your organization’s security policies and industry best practices (e.g., CIS Benchmarks, NIST).
- Compliance Gaps: Non-compliance with relevant regulations (e.g., GDPR, HIPAA).
3. Risk Assessment
Based on the analysis mentioned above, CSPM tools assess the level of risk associated with each identified problem. This helps prioritize remediation efforts and focus on the most critical vulnerabilities.
4. Continuous Monitoring
CSPM solutions can continuously monitor for the changes and new threats taking place in your cloud environment. This allows the tool to detect and alert you about all the emerging risks in real-time.
5. Remediation Guidance & Automation
Many CSPM tools guide how to remediate identified issues. Some tools like Cloudanix even offer automated remediation capabilities, such as automatically fixing misconfigurations or adjusting security settings saving you a ton of time.
6. Reporting & Dashboards
CSPM tools generate comprehensive reports and dashboards that provide visibility into your overall cloud security posture. This alone helps you to track progress, identify trends, and make informed decisions about your cloud security strategy.
Difference Between CSPM, CWPP, CASB, Cloud Security, CNAPP, SIEM, and DSPM
During our research, we witnessed a lot of people find it challenging to understand what exactly a CSPM is when compared with other cloud security concepts. Thus, we thought to break down the difference between CSPM and other key cloud security concepts like CSPM, CWPP, CNAPP, and similar. Let us get through them.
CSPM vs CASB (Cloud Access Security Broker)
CSPM focuses on security posture management within your cloud environment. This includes monitoring configurations, identifying vulnerabilities, and enforcing security policies across your cloud infrastructure.
Whereas, CASB is primarily concerned with controlling access to cloud services, especially SaaS applications. They act as a gateway, monitoring and enforcing policies for data traveling to and from cloud services.
CSPM vs Cloud Security
Cloud Security is a broad term encompassing all aspects of securing cloud environments. It includes various security measures like encryption, access control, threat detection, incident response, etc.
CSPM specifically is a subset of cloud security. It focuses on continuous monitoring, assessment, and improvement of your overall cloud security posture.
CSPM vs CNAPP (Cloud Native Application Protection Platform)
CNAPP is a broader platform that goes beyond traditional CSPM. It includes powerful capabilities like code security, runtime protection, container security, serverless security, identity and access management to mention a few, in addition to the core CSPM functions.
Whereas, CSPM is a core component of CNAPP. It provides a strong foundation for managing the security posture of your cloud infrastructure, which is essential for the overall security of cloud-native applications.
CSPM vs CWPP (Cloud Workload Protection Platform)
CWPP focuses on protecting workloads running in the cloud, such as virtual machines, containers, and serverless functions. This includes capabilities like runtime protection, vulnerability scanning, and threat detection specifically for these workloads.
In relation to CWPP, CSPM’s scope extends beyond workloads to encompass the entire cloud infrastructure.
CSPM vs SIEM
SIEM primarily collects and analyzes security logs from various sources, including cloud environments. It helps detect and respond to security threats by identifying suspicious activity and generating alerts.
CSPM helps users understand the security implications of the events detected by SIEM correlate them with their overall cloud security posture and identify potential vulnerabilities.
CSPM vs DSPM (Data Security Posture Management)
DSPM focuses specifically on protecting sensitive data in the cloud. DSPM capabilities generally include data discovery, classification, and encryption.
While data security is an important aspect, CSPM also addresses other critical areas like infrastructure security, access control, and threat detection.
We hope the above explanation gives our readers a broader outlook on understanding CSPM and other cloud security concepts.
Cloudanix and Cloud Security Posture Management
Our approach to securing your public cloud infrastructure is a multi-pronged one. Organizations need complete visibility into their cloud assets, continuous monitoring for misconfigurations and the risks they carry, real-time reporting of these to not compromise their cloud infrastructure, and remediation to mitigate the threats. With Cloudanix, these are now possible. Our platform categorizes these features into 3 broad categories: Events, Misconfigurations and Assets.
