Cloud Workload Protection
Removing threats from containers
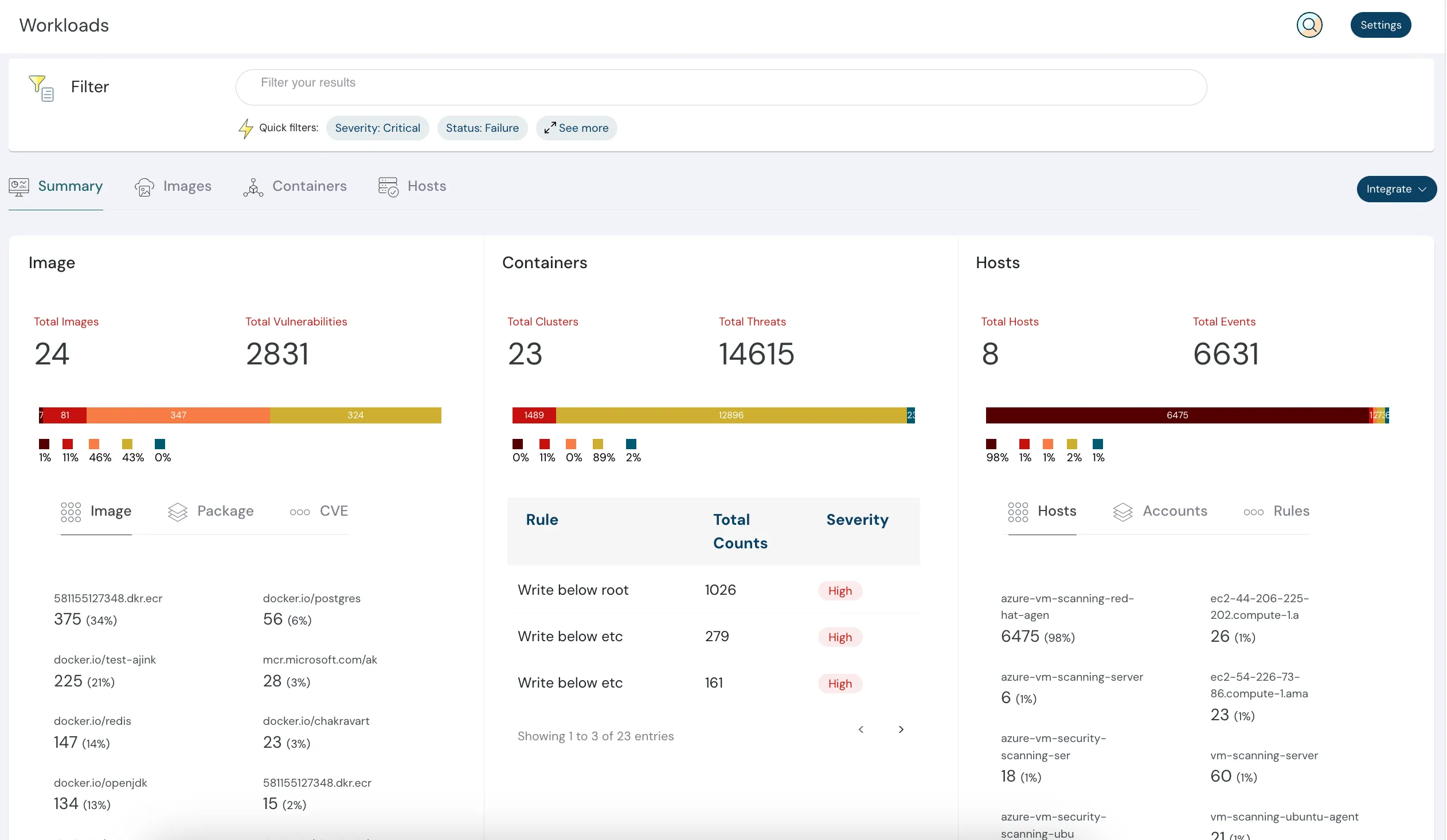
What is Cloud Workload Protection?
The process to secure the workloads that are hosted in any organization’s cloud environment is called cloud workload protection. This includes the protection of assets such as virtual machines (VMs), Containers, and Serverless functions. A combination of techniques is used by CWP to protect workloads. A cloud workload protection platform offers unified protection to workloads of any type and in any location across multi-cloud providers.
Techniques to protect workloads
Below we have listed in short, a basic combination of techniques used by CWP to protect workloads.
- Vulnerability scanning: Includes scanning of vulnerabilities for any known threats.
- Intrusion prevention: Blocks malicious traffic and monitors workloads for suspicious activities.
- Application control: Controls what applications to run on the workloads.
- Preventing data loss: Prevents workloads from exfiltrating sensitive data.
- CSPM: Access and recommends the required improvements in workloads.
Importance of Cloud Workload Protection
Cloud workload protection is crucial to safeguard cloud workloads i.e. organizational assets from cyber threats. No data is 100% secured, but organizations can ensure data confidentiality, integrity, and availability. Businesses can maintain workflow continuity and build trust in cloud operations by securing applications and assets available in their cloud environments.
Common threats that CWP mitigates
CWP helps organizations to protect from some of the common threats such as;
- Ransomware: One of the most common practices performed by attackers. Where an attacker encrypts the victim’s data and demands a ransom amount to decrypt it. CWP mitigates this threat by blocking malicious traffic to workloads.
- Data breaches: Data breach occurs when any sensitive data can be stolen from an organization.
- DDoS attacks: A type of attack that overwhelms a victim’s network with traffic. CWP blocks malicious traffic to workloads and keeps user assets protected.
In addition to these, Cloud Workload Protection can play a sound role in improving the performance and efficiency of workloads.
Benefits of Cloud Workload Protection
Organizations should consider practicing CWP, In order to protect cloud assets from different types of threats available.
Below are some of the benefits of using cloud workload protection.
- Improved workload visibility and management capabilities across multiple cloud platforms; CWP is the building block of CWPP, which provides a unified view of all available workloads regardless of the location they are hosted. This helps users better manage and protect workloads.
- The risk of data breaches and other security incidents is reduced; Unauthorized access to workloads and data is blocked, which helps to detect incidents more rigorously.
- Improved compliance; CWPPs help organizations to get in compliance with security standards like HIPAA, GDPR, and PCI DSS.
- Improved operational efficiency; Using CWPP, security tasks like vulnerability scanning or patch management can be automated. This allows IT teams to focus their efforts on more serious tasks.
Read our recent blog - The Ultimate Guide to Cloud Workload Protection
Challenges of Cloud Workload Protection
Both, the cloud security provider and the cloud user are committed to ensuring security at their best. To understand it in a more simplistic way; The security provider is committed to the security of the cloud, whereas the user (organization) is committed to the security in the cloud.
Below are some of the most common cloud workload protection challenges:
- Multi-cloud environment: Leveraging constant security across multi-cloud platforms can be complex.
- Evolving threats: Evolution demands upgrades, and adapting to new and evolved cyber threats needs continuous updates.
- Visibility: Comprehensive visibility into cloud workloads can be challenging and can lead to potential blind spots.
- Compliance: Staying compliant with regulatory standards when using dynamic cloud environments can be challenging.
Recommended best practices to secure your workloads
- AWS Cloud: Audit checks available for AWS cloud
- Azure Cloud: Audit checks available for Azure cloud
- GCP Cloud: Your data needs highest level of protection
What is Cloud Workload Protection Platform?
CWPP or Cloud Workload Protection Platform helps organization protects their workloads running in the cloud. Using CWPP solutions, organizations have constant visibility and control over their workloads to reduce data breaches and improve compliance.
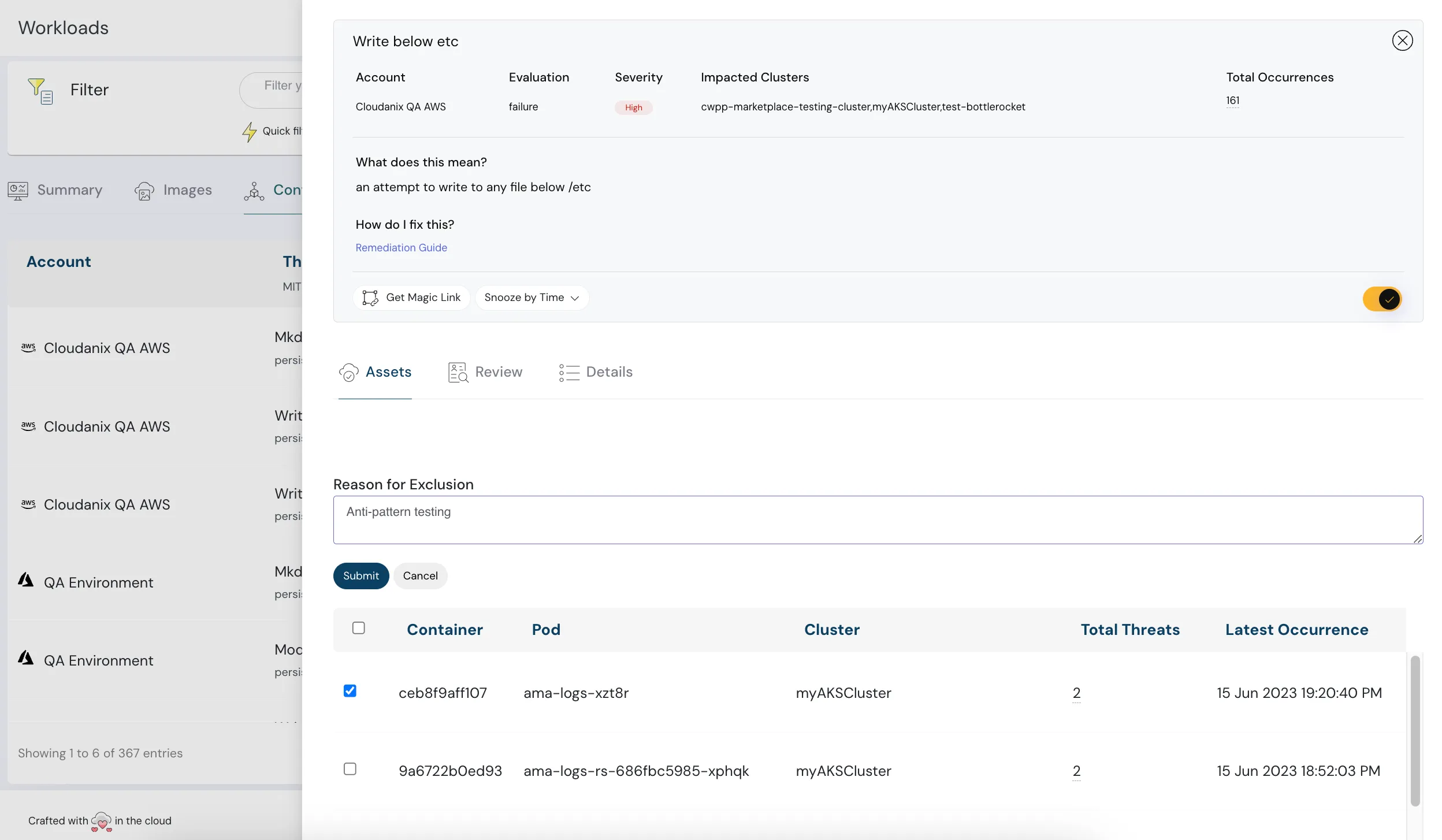
Cloudanix’s CWPP
Cloudanix is at the top of all this and provides a robust architecture for consistent visibility and control over all workloads; regardless of location, size, or architecture. With Cloudanix CWPP, you can: Identify and remediate misconfigurations that could be exploited by attackers, Protect your workloads from known and unknown threats with real-time threat detection and response, and Automate security workflows to improve efficiency and productivity.
Secure your cloud workloads with Cloudanix CWPP, a scalable and low-friction solution.
