IAM JIT, PagerDuty Integration, Image scanning with Jenkins and Bitbucket
The most in demand security feature across the globe has now been shipped. Take a guess, it gives you super powers…still not sure then read along to see what I’m talking about.
Cloudanix joins AWS ISV Accelerate program, read about it here.
Just In Time Access
Instead of Just In Case Access, now your team can request elevated privileges for Just In Time Access. With in-built workflows, you have the super power to follow Principles of Least Privilege without any effort. Cloudanix takes care of Providing Access, Revoking Access and Auditing the Access.
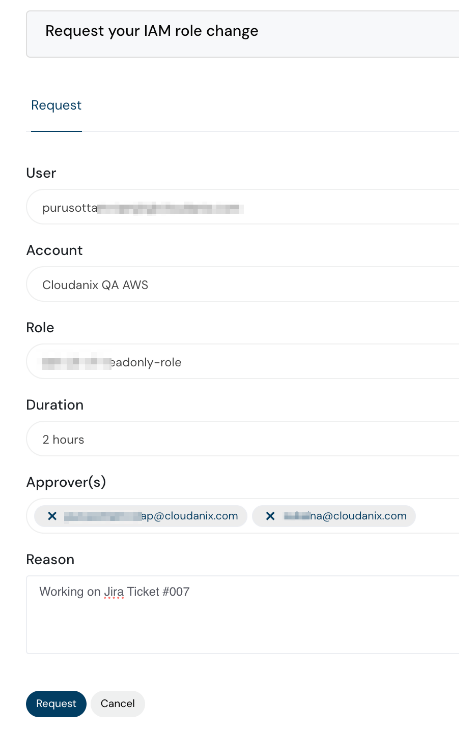
IAM JIT Access dashboard
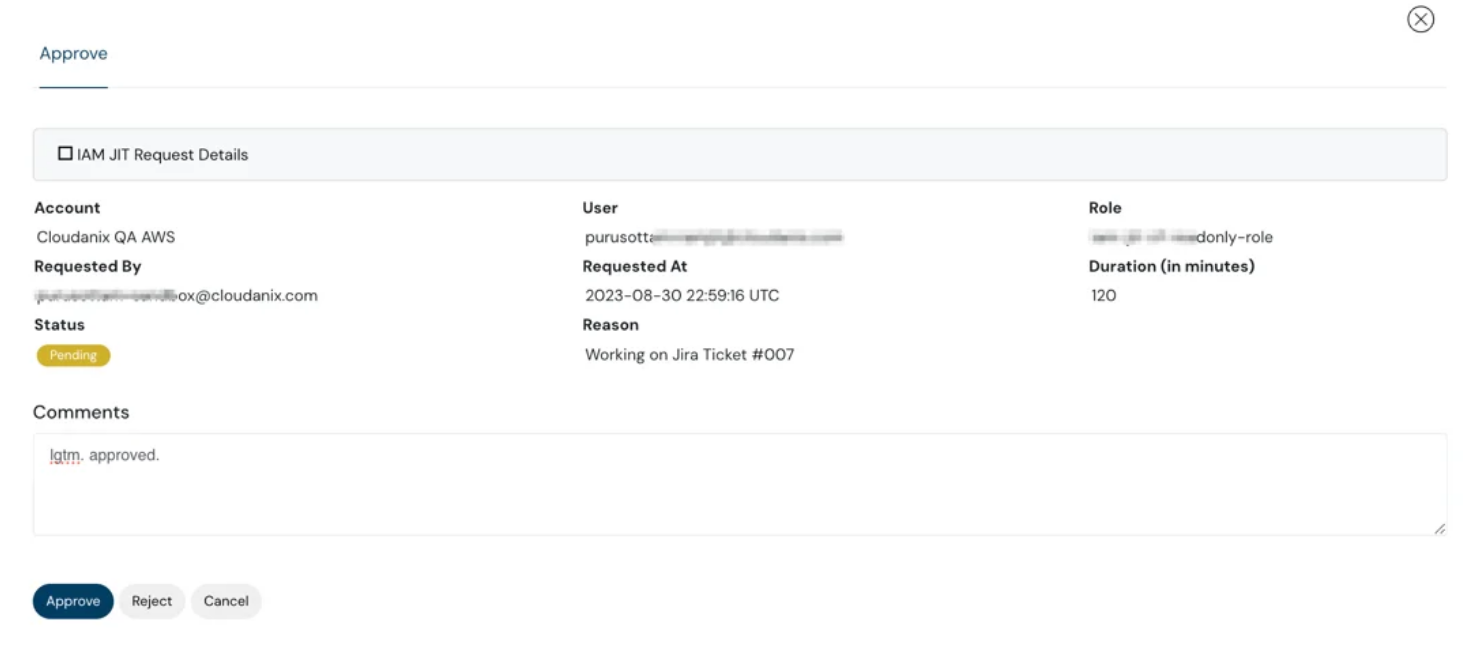
IAM JIT Access request dashboard
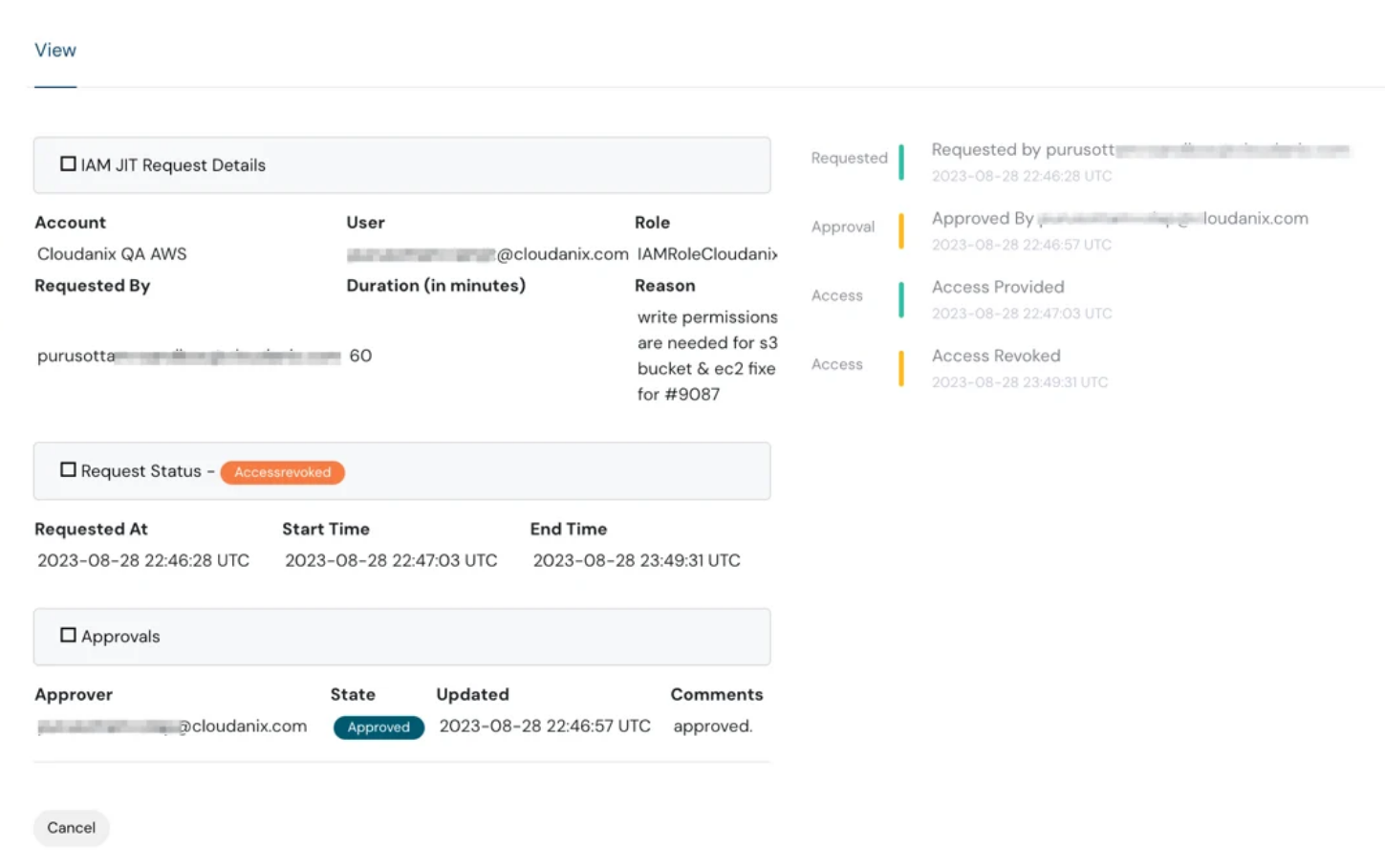 IAM JIT view dashboard
IAM JIT view dashboard
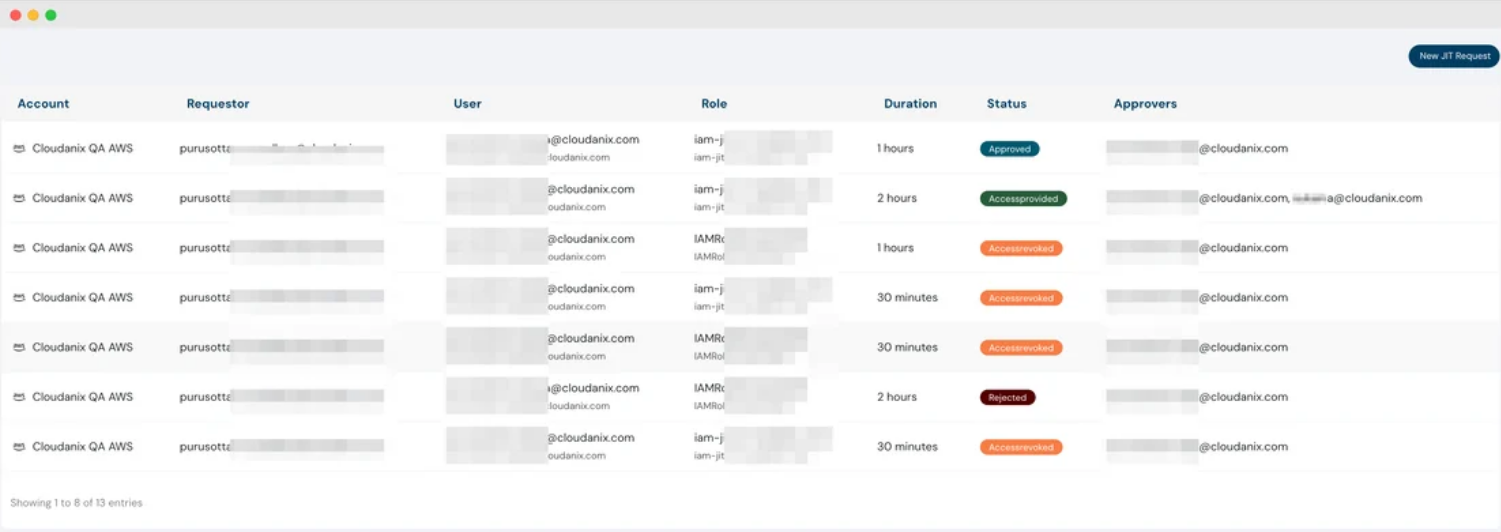 IAM JIT overview dashboard
IAM JIT overview dashboard
PagerDuty Integration
Arm your on-call team with additional context from Cloudanix. Integrate Cloudanix with PagerDuty to push Security Alerts to PagerDuty Services.
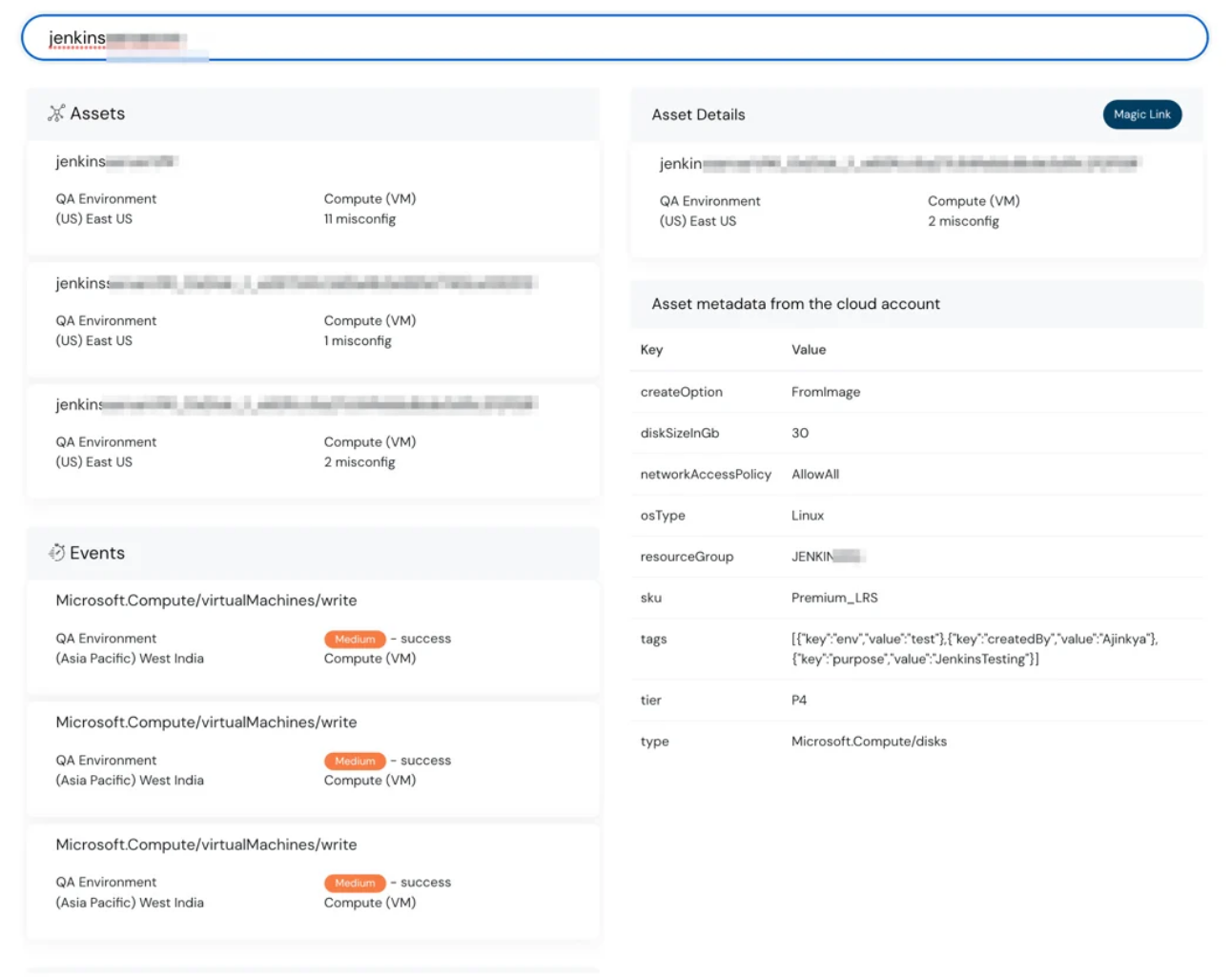 Global search feature in dashboard
Global search feature in dashboard
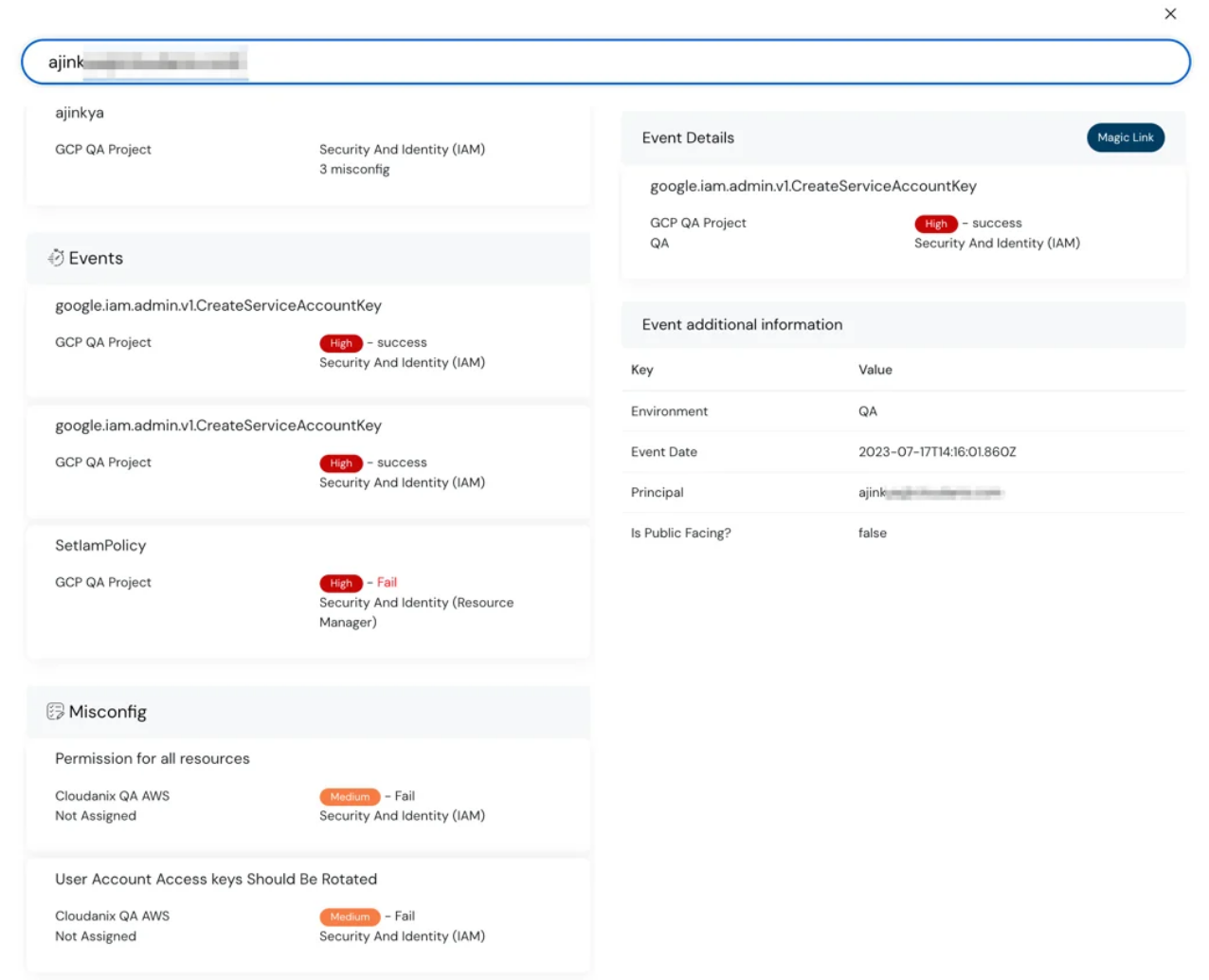 Global search feature detailed view in dashboard
Global search feature detailed view in dashboard
Graph View of Attack Path and Connected Assets
It’s not enough to see an asset information without its related assets and also, if there’s an attack path that can be exploited. With the connected assets view, you can do both. You can expand this further by clicking on any node and see its connected assets as well.
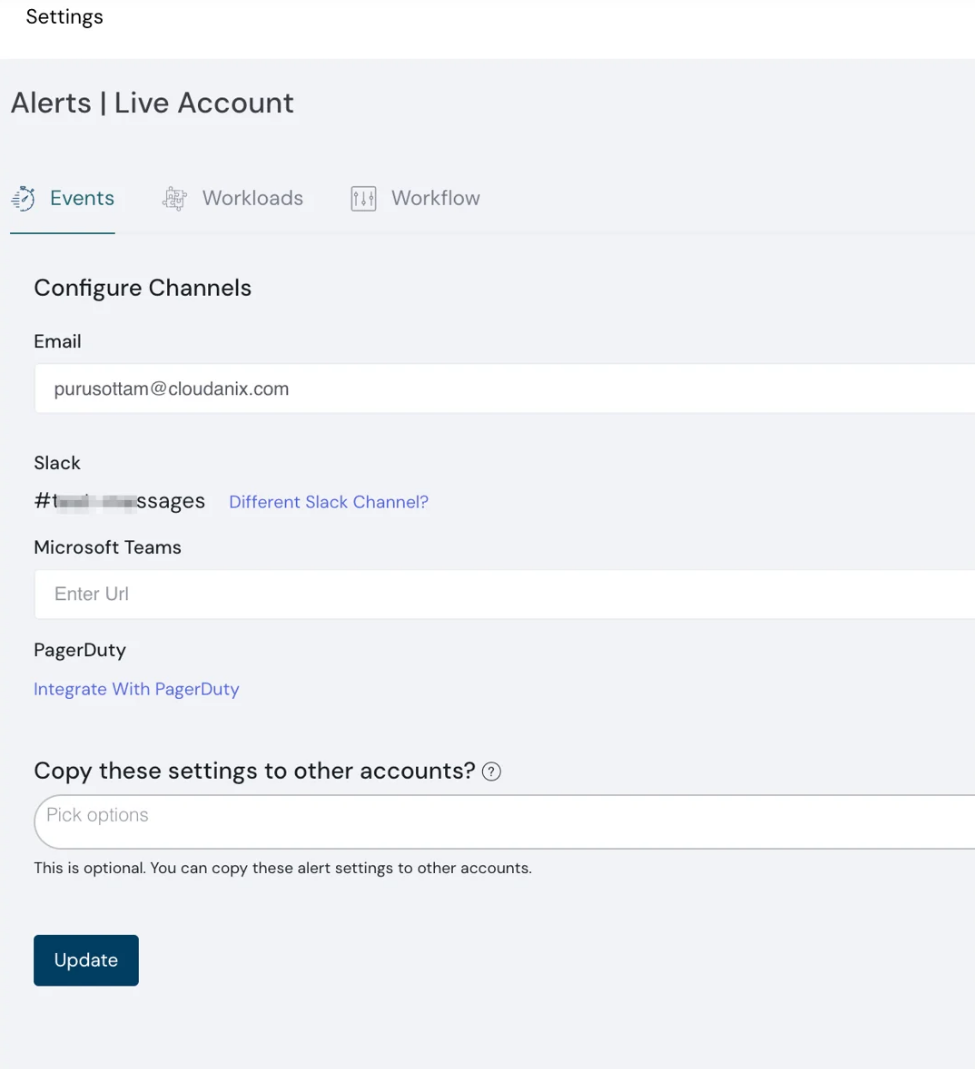 PagerDuty settings - dashboard
PagerDuty settings - dashboard
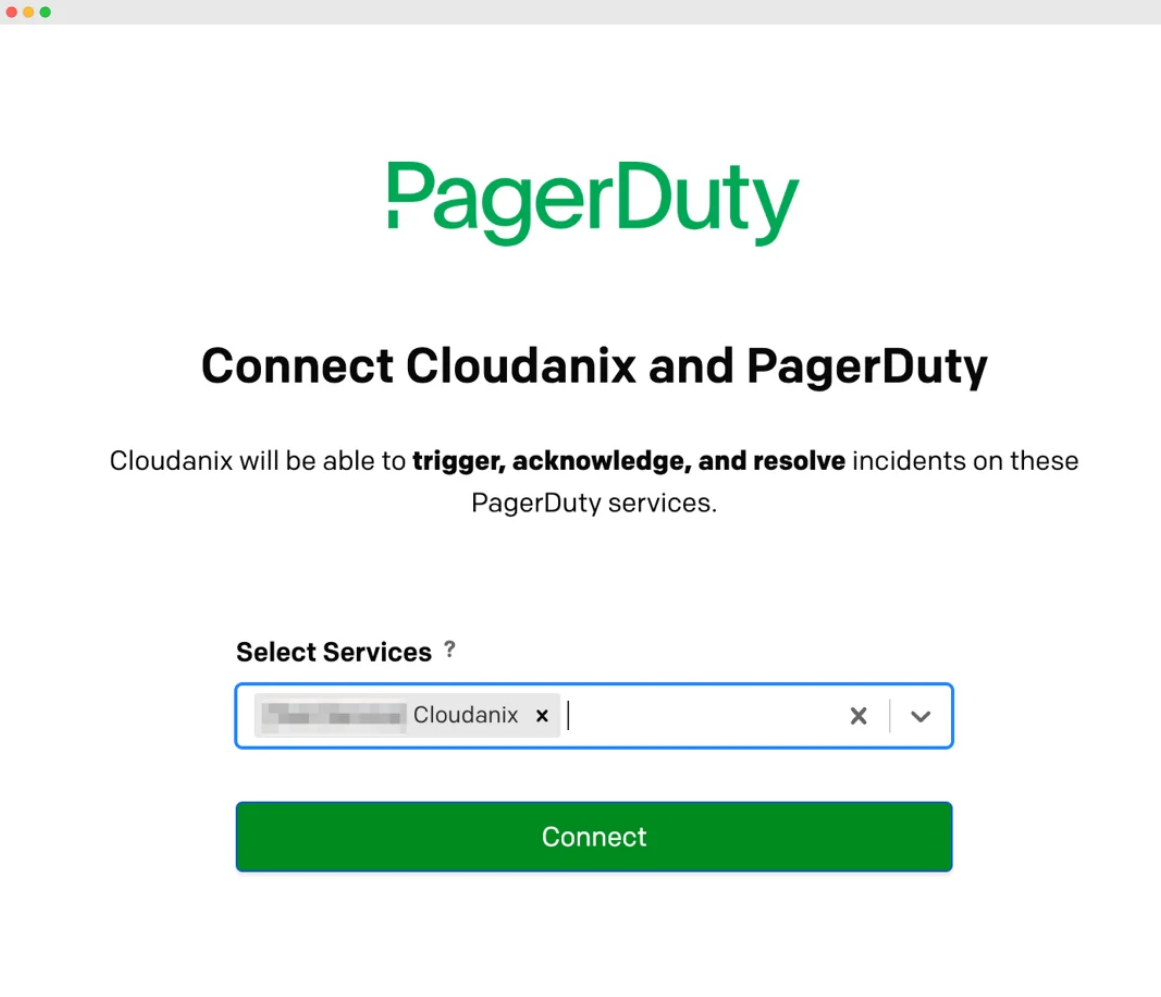 Cloudanix and PagerDuty integration
Cloudanix and PagerDuty integration
 Cloudanix and PagerDuty integration
Cloudanix and PagerDuty integration
Image Scanning at Build Time with Jenkins and Bitbucket
We have extended Image Scanning capability to Jenkins and Bitbucket as well. With a few clicks, integrate Image Scanning in your pipelines. With our Plugins, findings are presented at both the Pipeline and in the Cloudanix Console.
Threat Detection for GitHub & Bitbucket
Similar to our Threat Detection for Clouds (AWS, GCP & Azure), we have added Threat Detection capabilities to GitHub and Bitbucket. We cover over 30 threats ranging from License Changes to Repository Status changes and many more.
AWS Startup Security Baseline Compliance Pack
AWS Startup Security Baseline (SSB) is a set of controls that create a minimum foundation for businesses to build securely on AWS without decreasing their agility. We have built a Compliance Pack for Startups to visualize the Security Posture of the foundation.
Kubernetes Support for Pod Security Standards instead of Pod Security Policies
Pod Security Policies (PSP) were officially deprecated and replaced with Pod Security Admission (PSA) in Kubernetes version 1.21. It implements Pod Security Standards (PSS), policies to cover a broad security spectrum. In 1.25, PSP was completely removed. So, we have updated our charts to support PSAs.
Here’s a migration guide: https://kubernetes.io/docs/tasks/configure-pod-container/migrate-from-psp/
Additional Resources
- Importance of Kubernetes Security
- How to go about building a SAST plan for your company?
- What is Vulnerability Management?
- What is Threat Modeling?
Industry News
- Build Docker Images Smaller and Secure
- Kubernetes 1.28 (Planternetes) is out
- Understand LLMs and the threats they pose
TODO:// is not an option for Cloud Security
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedBlog
Read More Posts
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Wednesday, Nov 05, 2025
From Static to Strategic: Modernizing Privileged Access for Cloud Infrastructure
The promise of the cloud – agility, scalability, and innovation – has revolutionized how enterprises operate. Cloud infr
Read MoreTuesday, Sep 30, 2025
Eliminate Standing Access: Introducing JIT Kubernetes for Azure AKS Security
The Security Mandate: Why Permanent Access Fails Mission-Critical AKS Kubernetes has become the operating system of
Read MoreFriday, Aug 08, 2025
User Access Review in Cloud Security: A Foundational Guide to Securing Your Cloud Environment
Introduction: The Unseen Gatekeepers of Cloud Security In the rapidly expanding landscape of cloud computing, organi
Read More