Security Context, Bitbucket Security and Container Security Upgrades
Filter Events and Identities with Signals
We released “Signals” a few months back to give additional context on what’s going on in your cloud infrastructure. Our users gave additional feedback, and now we are rolling out pre-built Signals as part of the Filter control.
What’s better than just seeing all the signals? The capability to filter them.
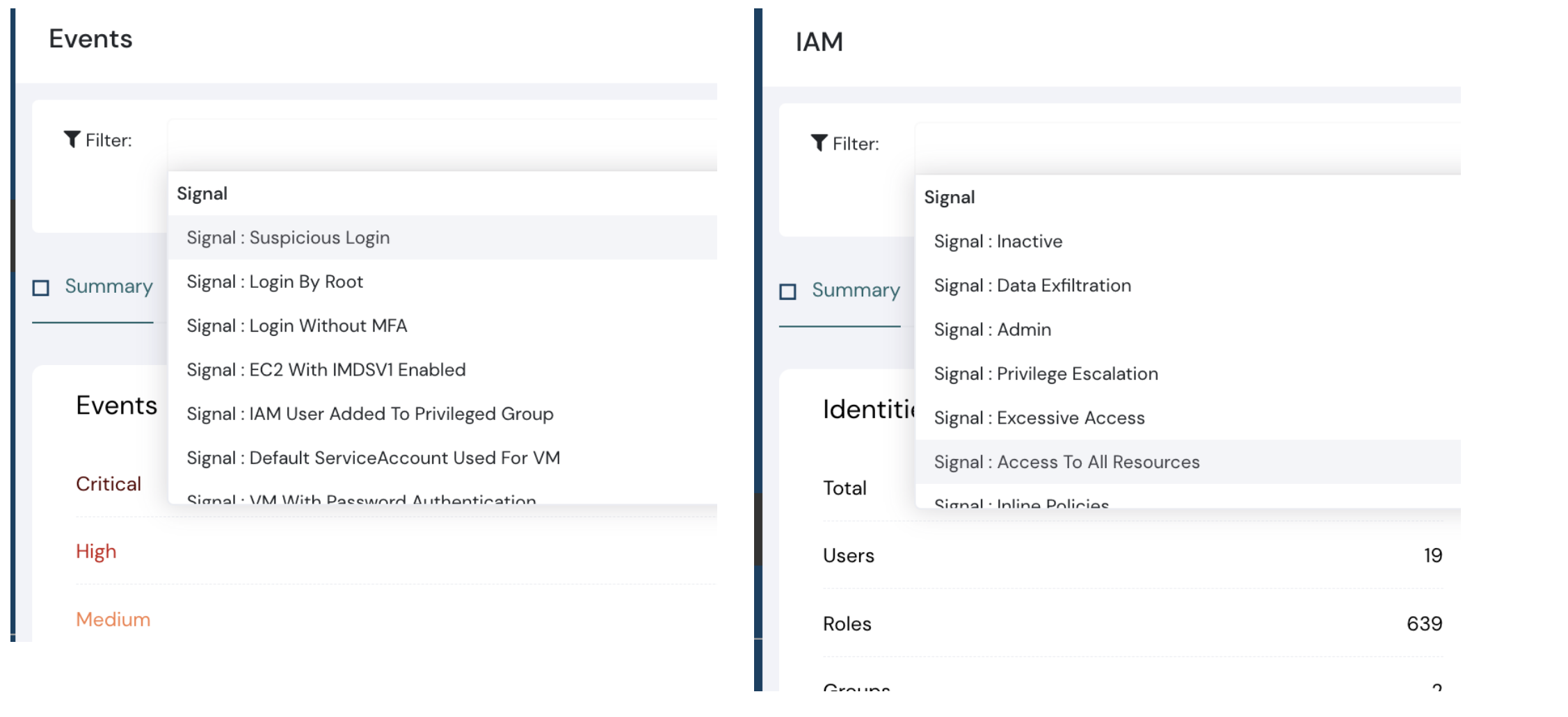
- Events signal control dashboard and Identities signal control dashboard
Bitbucket Security
If GitHub is secured, can Bitbucket be far behind?
Last month we announced GitHub security, where we covered three areas:
- Misconfig: e.g., Outside collaborator is an Admin
- Events and Threats: e.g., Your private repository became public
- Secret Detection: e.g., Developer checked in a secret in this Repo, in this file online number x
Now we have rolled out these capabilities to Bitbucket too. Here’s a peek:
- Bitbucket Events Monitoring
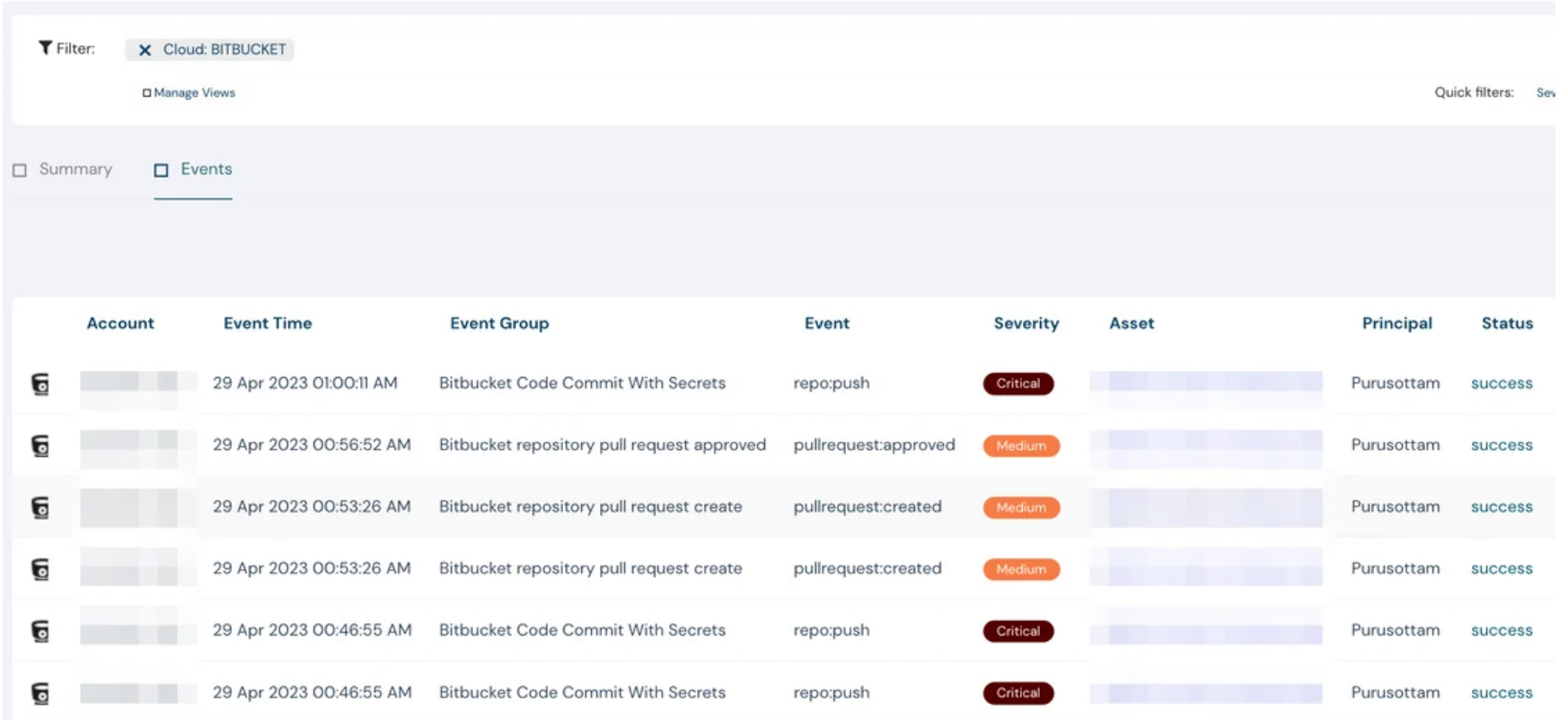
- Bitbucket Secret Scanning
Checking secrets into your source code is not ideal — but detecting them instantly is. Cloudanix can alert you in real time if secrets get checked in. Give Bitbucket security a spin and discover more.
Other platforms are coming soon.
Container Security Upgrade
Container Security upgrade to support latest EKS Linux AMIs (AmazonLinux2 & Bottlerocket)
Release: Amazon EKS AMI v20230411
Coming Soon
- Realtime Events Anomaly support for GCP & Azure
- Additional Events support for IAM in Azure (e.g., permissions updated for Service Account, User MFA changes)
- In Secret Scanning Capability – Support for Custom Patterns and Exclusions for existing Patterns, Files or Secrets
- VM Scanning
- Attack Path
Scale to Zero Podcast
The more we speak to experts, the more we learn. We have been lucky to find these amazing experts who gave us their time and wisdom to make sense of the queries we had. Take a look:
- Brett Johnson: Get to know the world of the dark web and cybercrime better.
- Walter Haydock: Deep dive into Vulnerability Management.
- Jeevan Singh: Understanding Threat Modeling.
- Ashwin Patil: Get to know security frameworks and security tools better.
Find more conversations at ScaleToZero website.
TODO:// is not an option for Cloud Security
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedBlog
Read More Posts
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Wednesday, Nov 05, 2025
From Static to Strategic: Modernizing Privileged Access for Cloud Infrastructure
The promise of the cloud – agility, scalability, and innovation – has revolutionized how enterprises operate. Cloud infr
Read MoreTuesday, Sep 30, 2025
Eliminate Standing Access: Introducing JIT Kubernetes for Azure AKS Security
The Security Mandate: Why Permanent Access Fails Mission-Critical AKS Kubernetes has become the operating system of
Read MoreFriday, Aug 08, 2025
User Access Review in Cloud Security: A Foundational Guide to Securing Your Cloud Environment
Introduction: The Unseen Gatekeepers of Cloud Security In the rapidly expanding landscape of cloud computing, organi
Read More