GCP marketplace, secrets verification, SIEM integration and more
We’re excited to announce we are now listed on the GCP Marketplace too. We’re moving fast to not just provide better capabilities and workflows but to also make Cloudanix available at your favorite marketplaces like AWS, Azure and now GCP.
Read along to see what we have brewed for you last month.
Re-evaluate misconfiguration policies
Now, you can re-evaluate misconfiguration policies as soon as you address the gaps. No need to wait for end-of-the-day policy checks. And, you will get notified as soon as the evaluation is completed. Bonus: We also evaluate related policies.
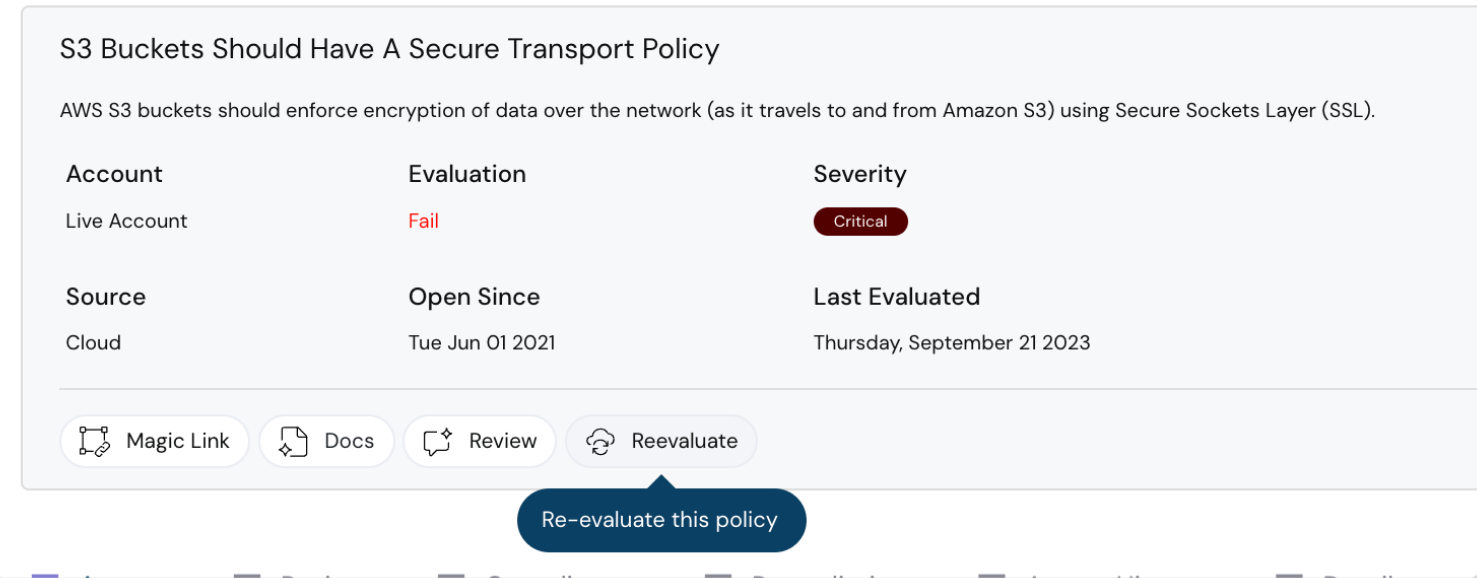 Cloudanix re-evaluation notification
Cloudanix re-evaluation notification
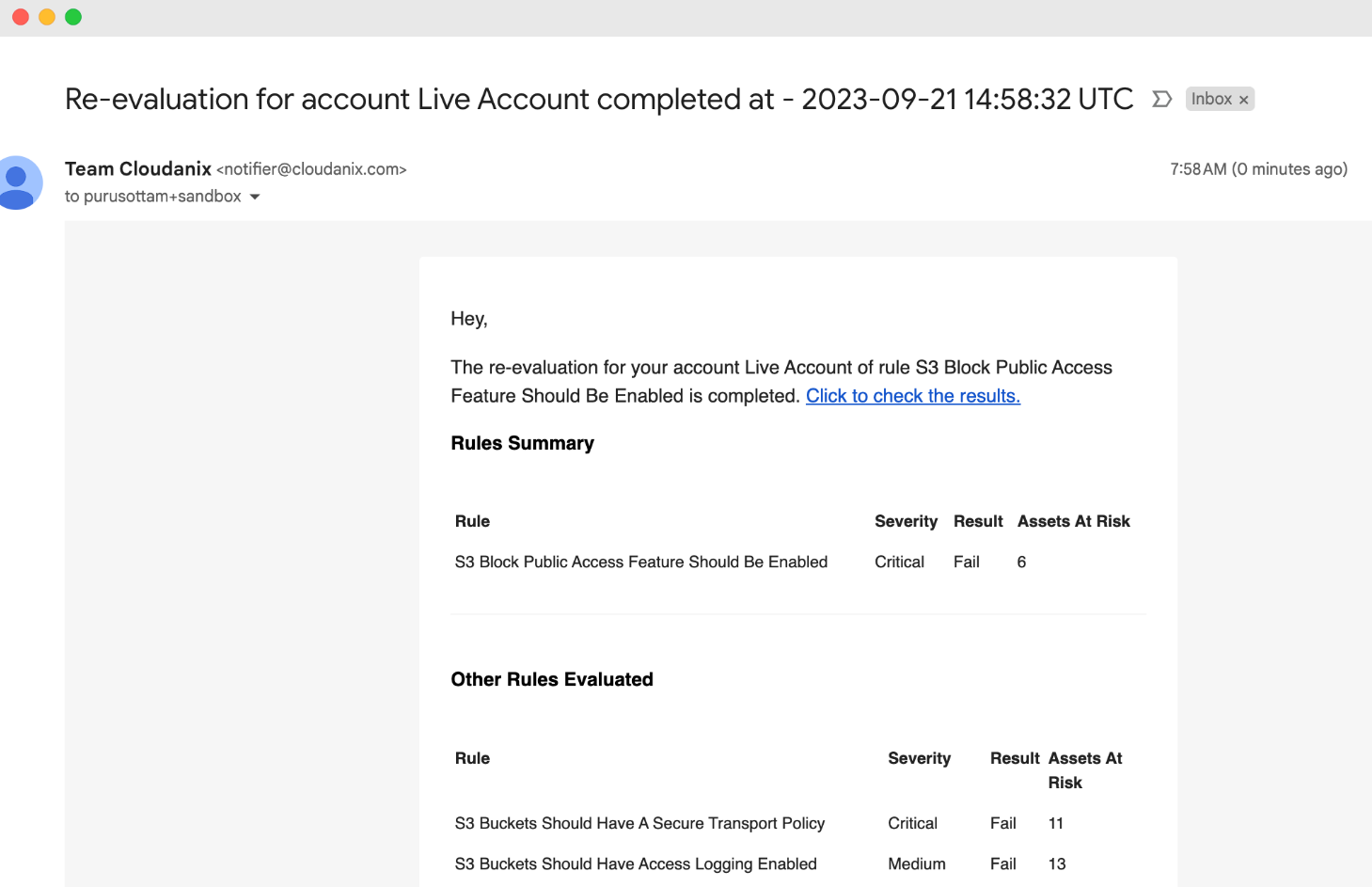 Confirmation mail of the changes from Cloudanix dashboard
Confirmation mail of the changes from Cloudanix dashboard
Secrets verification
As part of secret detection in your SCM tool, Cloudanix can verify and check the validity of secrets checked-in in your code. Even by mistake!!
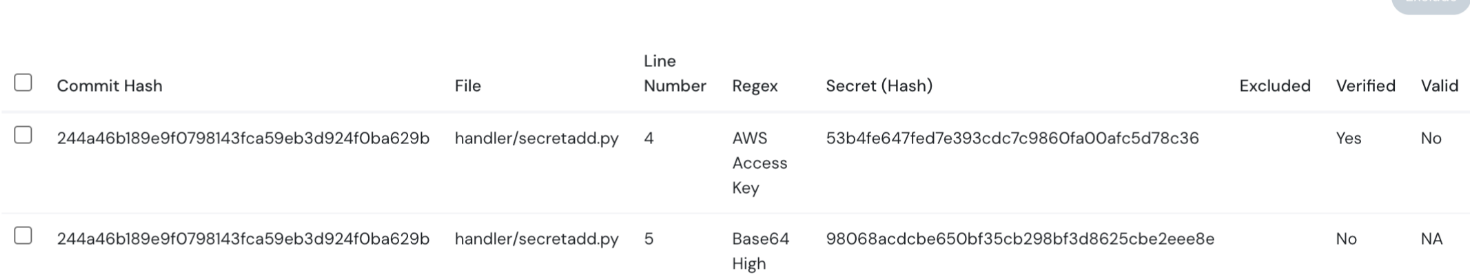 Log of secrets checked in your code
Log of secrets checked in your code
SIEM integrations
Integrate security findings (Threats, Anomalies, Events, and Misconfigurations) with your favorite SIEM tool via webhooks.
Organization events
In AWS, Cloudanix can monitor organization level events and alert you when something suspicious occurs.
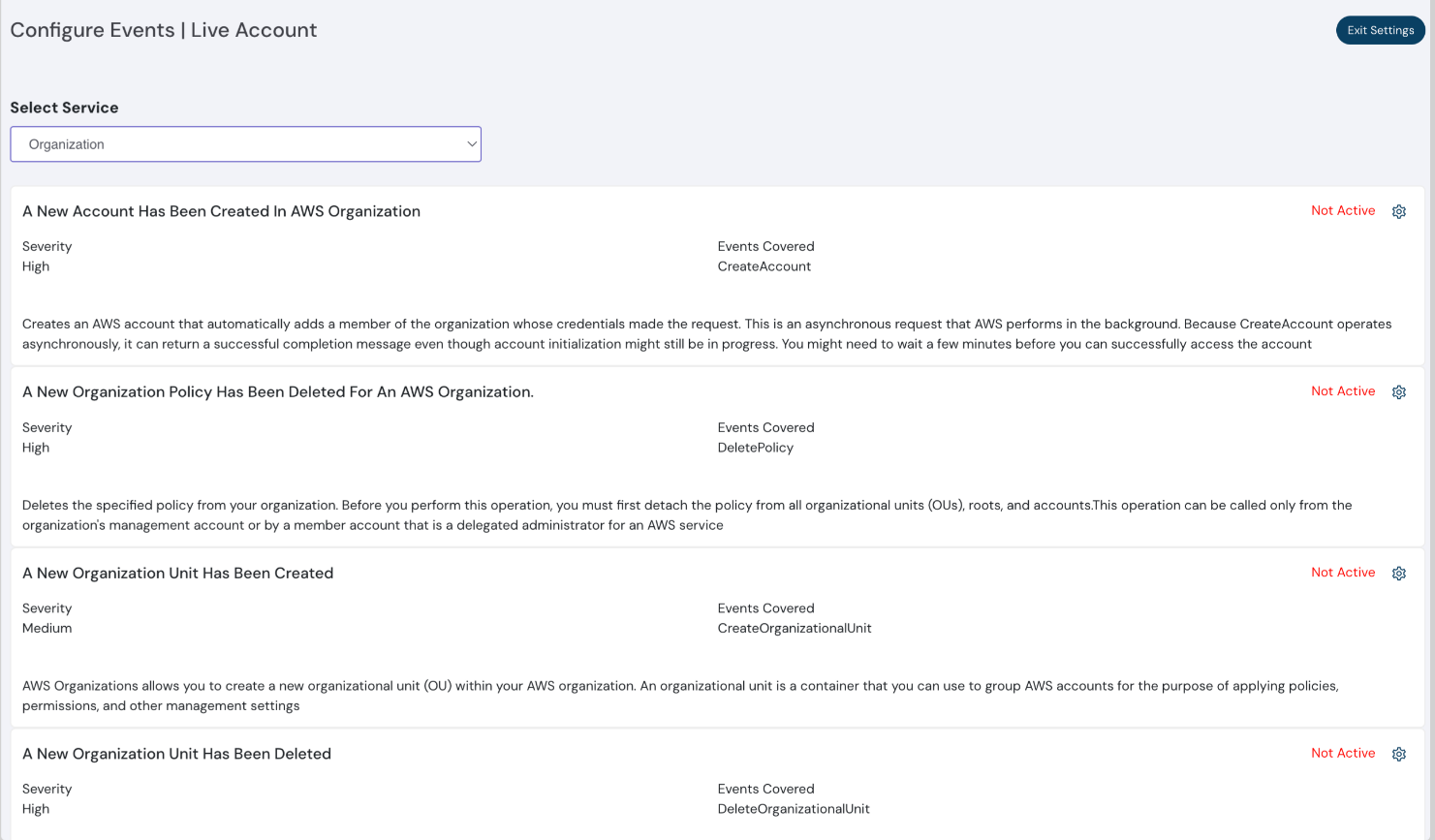
Log of secrets checked in your code
CIS 2.0.0 for GCP
We have added support for CIS 2.0.0 in GCP. All the controls are mapped to misconfiguration policies for your regulatory requirements.
Brace yourself for what’s coming up next:
- IAM Right sizing for GCP & AWS
- ISO 27002 compliance support
- DigitalOcean CSPM & 1-Click Kubernetes integration
Industry News
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedBlog
Read More Posts
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Wednesday, Nov 05, 2025
From Static to Strategic: Modernizing Privileged Access for Cloud Infrastructure
The promise of the cloud – agility, scalability, and innovation – has revolutionized how enterprises operate. Cloud infr
Read MoreTuesday, Sep 30, 2025
Eliminate Standing Access: Introducing JIT Kubernetes for Azure AKS Security
The Security Mandate: Why Permanent Access Fails Mission-Critical AKS Kubernetes has become the operating system of
Read MoreFriday, Aug 08, 2025
User Access Review in Cloud Security: A Foundational Guide to Securing Your Cloud Environment
Introduction: The Unseen Gatekeepers of Cloud Security In the rapidly expanding landscape of cloud computing, organi
Read More