“Enabling small businesses to harness the power of the internet to sell. Showcasing their wares to even the remotest parts of India sitting at home. That is the power Meesho brings to India.”
— Digvijay Singh, Staff Security Engineer, Meesho
Best quality shopping at the lowest prices
Meesho is India’s fastest-growing internet commerce company. They want to make eCommerce accessible to all with a vision to enable 100 million small businesses in India, including individual entrepreneurs, to succeed online. Their mission is to democratize internet commerce by bringing a range of products & new customers online and shaping the future of online shopping in India. They have created a single ecosystem connecting sellers to consumers and entrepreneurs. They have delivered orders from over 100K registered suppliers to over 27,000 pin codes in over 5,000 cities and towns. They’ve generated over 500+ crores in income for individual entrepreneurs and customers in more than 4,500 Tier 2+ cities — truly bringing e-commerce to ‘Bharat’.
Compliance and Security for customers
Meesho is a consumer-first company. The safety and security of their sellers and consumers are their top priorities. They wanted a partner who could help them secure their assets on the cloud, inform them of the misconfigurations in their cloud infrastructure and help them stay abreast of the latest compliance standards.
Choosing the right tool to support their multi-accounts and multi-runtime DevSecOps pipelines and misconfigurations was vital. With the multi-dimensions in play, they required a solution that would be easy to adopt by their security team and assist the team with a unified dashboard to provide visibility across all their accounts. That’s the reason Meesho implemented Cloudanix.
Cloudanix’s capabilities fulfilled their criteria and more. Cloudanix helped their security team adopt the tooling easily by providing an intuitive dashboard with a clean interface. This helped Meesho get clear visibility into the happenings of their cloud infrastructure. Cloudanix helped Meesho’s security team stay on top while mitigating threats.
“Cloudanix delivered value within 5 minutes of onboarding. Continuous monitoring, timely detection, and excellent documentation helped us attain a great cloud security posture.”
— Divyanshu Shukla, Senior DevSecOps at Meesho
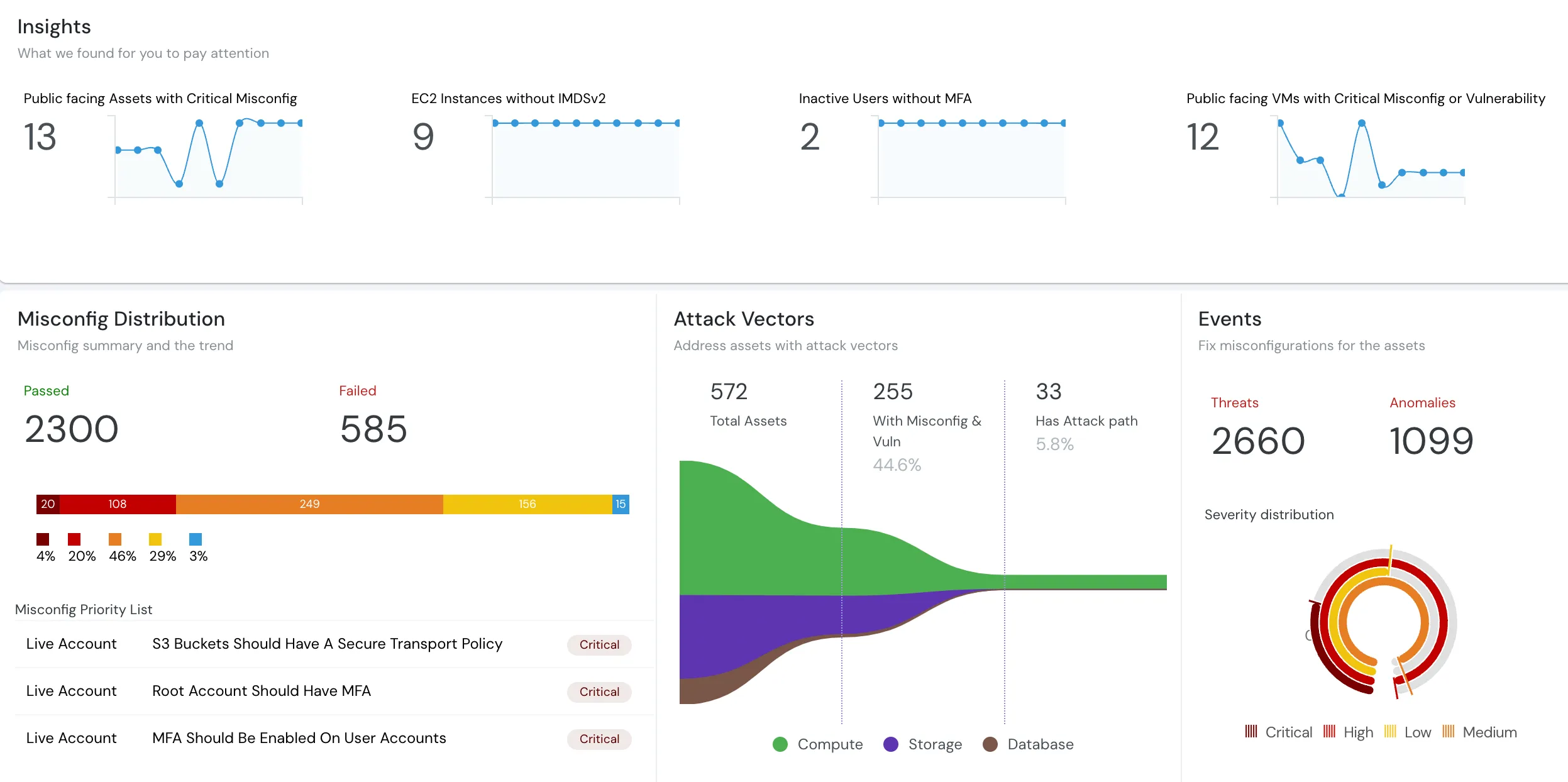
Cloud Compliance at glance
Note: For illustration purpose only.
“The real-time notifications that Cloudanix provides are a real lifesaver. Their adaptive notifications ensure that my team stays productive and doesn’t get interrupted all the time.”
— Digvijay Singh, Staff Security Engineer, Meesho
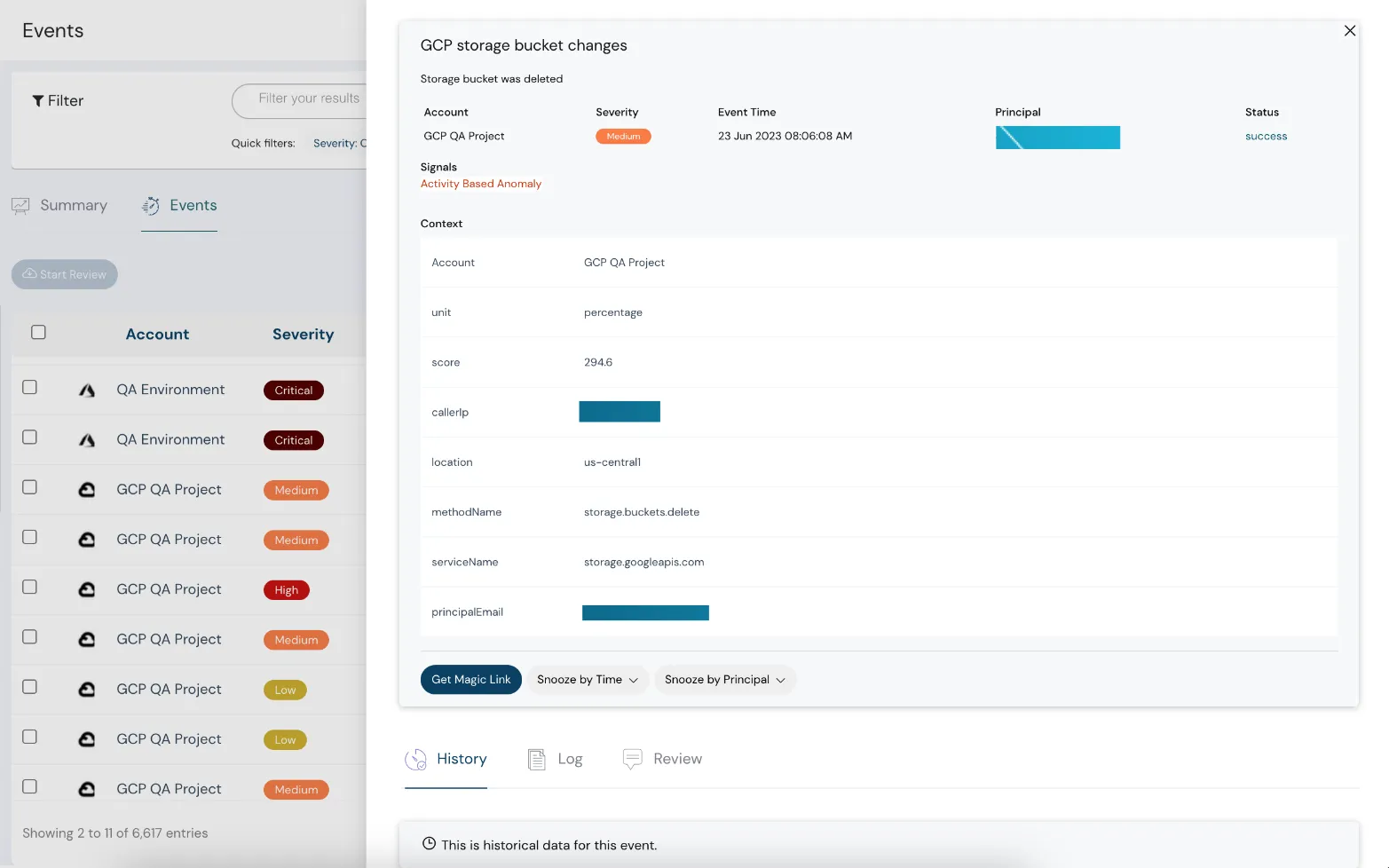
Real-time alerting, WOW!
Meesho takes security seriously. The scale of operations is enormous, with multiple teams deploying to the cloud and may cause misconfigurations and drifts to occur. This can significantly drop cloud security posture, leaving a wide attack surface and making the cloud infrastructure vulnerable to attacks. A robust system is vital to alert of drifts and misconfigurations occurring.
Cloudanix provides continuous monitoring and automated real-time alerts for their CI/CD pipelines. Not just that, the violations are also graded into severity, enriched with threat information with anomalies highlighted to filter the noise from the signal. This enables the security teams to prioritize the alerts and attend to the ones that may leave them vulnerable to threats. To avoid the alerts being missed, Cloudanix offers integrations with multiple channels such as Slack, Jira, Email, and Webhooks, to name a few.
Note: For illustration purpose only.
The Law of Compounding
The “Law of Compounding” applies for security too. The more cloud, accounts, runtimes you have, the more complex security becomes.
Meesho has multiple AWS accounts and several GCP projects with assets spread across these cloud accounts. Discovery and high visibility of the inventory are essential. Cloudanix provides a visual attack path helping the Meesho team learn how the infrastructure can get compromised.
Cloudanix continuously monitors the entire cloud infrastructure for changes in the assets, among other things. A single dashboard provides high visibility into the entire inventory for multiple accounts and multiple clouds.
Any misconfigurations and drifts are reported methodically. Auditing the assets regularly reduces the attack surface and helps mitigate any threats.
“You can’t fix what you can’t see. Cloudanix helped provide true visibility into our entire cloud infrastructure.”
— Divyanshu Shukla, Senior DevSecOps, Meesho
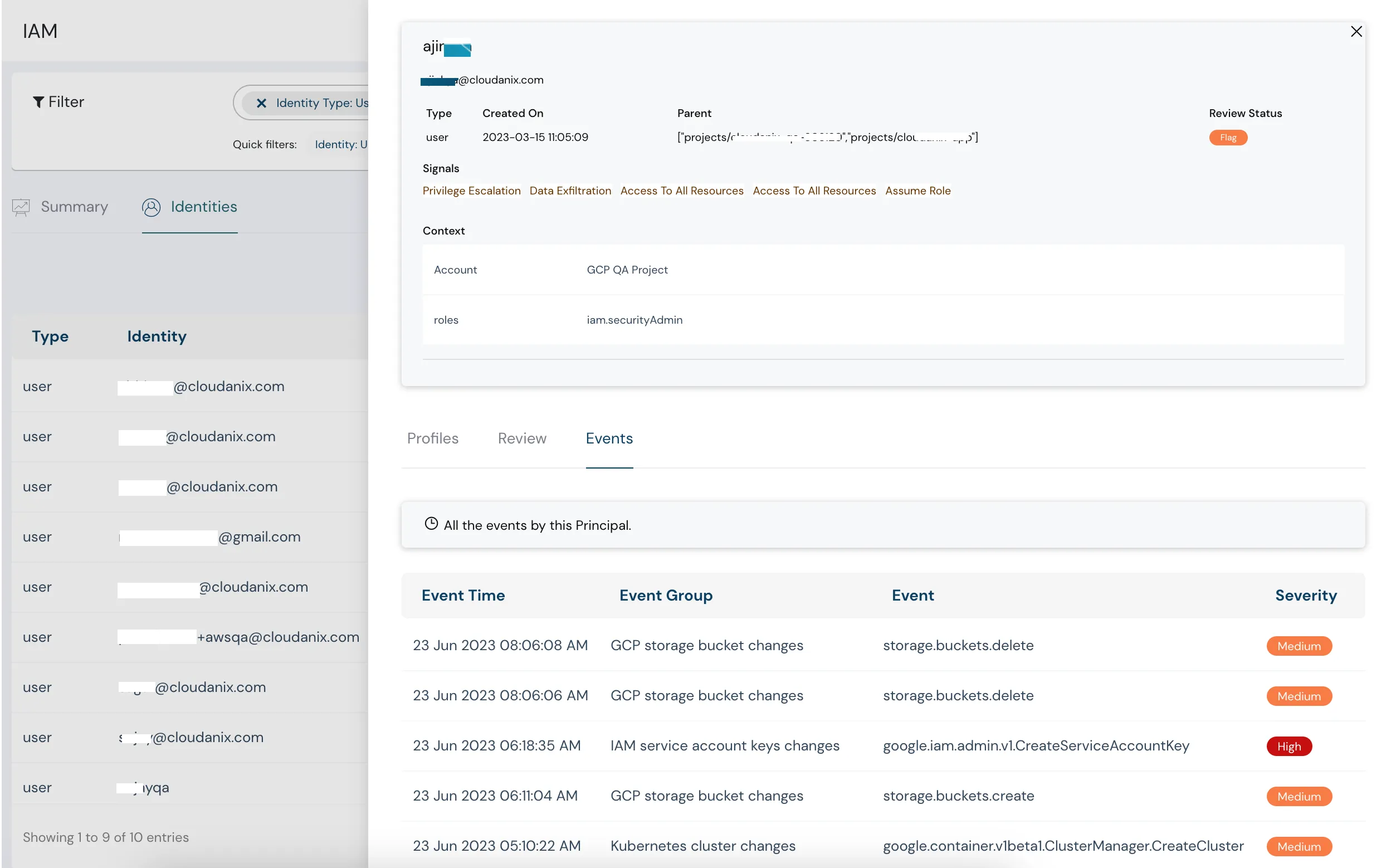
IAM Ready. Let’s go.
Meesho requires a robust CIEM tool to ensure the roles and permissions are correctly allocated. Having a big team poses a challenge of over-permissions and entitlements. High visibility is required into who has what permissions and whether they are in excess or just right. Meesho acknowledges that IAM is usually a weak link and the cause of most breaches. They wanted to convert IAM into their strength rather than a weakness.
Cloudanix provides a IAM tool that helps identify all the roles across Meesho’s multi-cloud and multi-account infrastructure. Any excessive permissions or any anomalies around incorrect permissions are detected and alerted. Using AI & ML, our algorithms are trained to detect these. A single window view helps organize roles & permissions for multi-cloud for the same user in a better and more consumable way.
Note: For illustration purpose only.
Red-team, InfoSec, DevOps and the Leadership
Meesho has multiple clouds, accounts, runtime, tools which is expected for its size and scale. It doesn’t end here.
Meesho’s commitment to security also demands Red Team, InfoSec, DevOps, Security Engineers and Leadership to be on the same page. Finding a solution which can cater to demands of different stakeholders is not an easy task.
Cloudanix is built not just for multi-clouds, accounts, runtimes, tools but also for multiple personas in an organization. That makes Cloudanix a true “Multi*” security solution.
A long-term vision for partnership
Meesho is devoted to security and was looking for a partner that would share their vision. With many stakeholders involved, this task may seem daunting. Cloudanix provides exceptional support to overcome this. Being in the security industry Cloudanix understands “Support delayed is support denied.” This brings confidence to Meesho teams for high-velocity deployments. Cloudanix team became an extended arm of Meesho’s devops and security teams via a Slack channel and ensured that the security solutions are co-created which meets Meesho’s requirements.
“Meesho is devoted to security, and Cloudanix shares this vision. Cloudanix has the stuff long-term partnerships are made of,” adds Digvijay.
Customer Brief
Customer: Meesho
Industry: E-commerce
Country: India
Cloud Accounts Secured: AWS, GCP
Impact: Helped securely deploy at scale
Deliverability: Software as a service (SAAS) Platform
