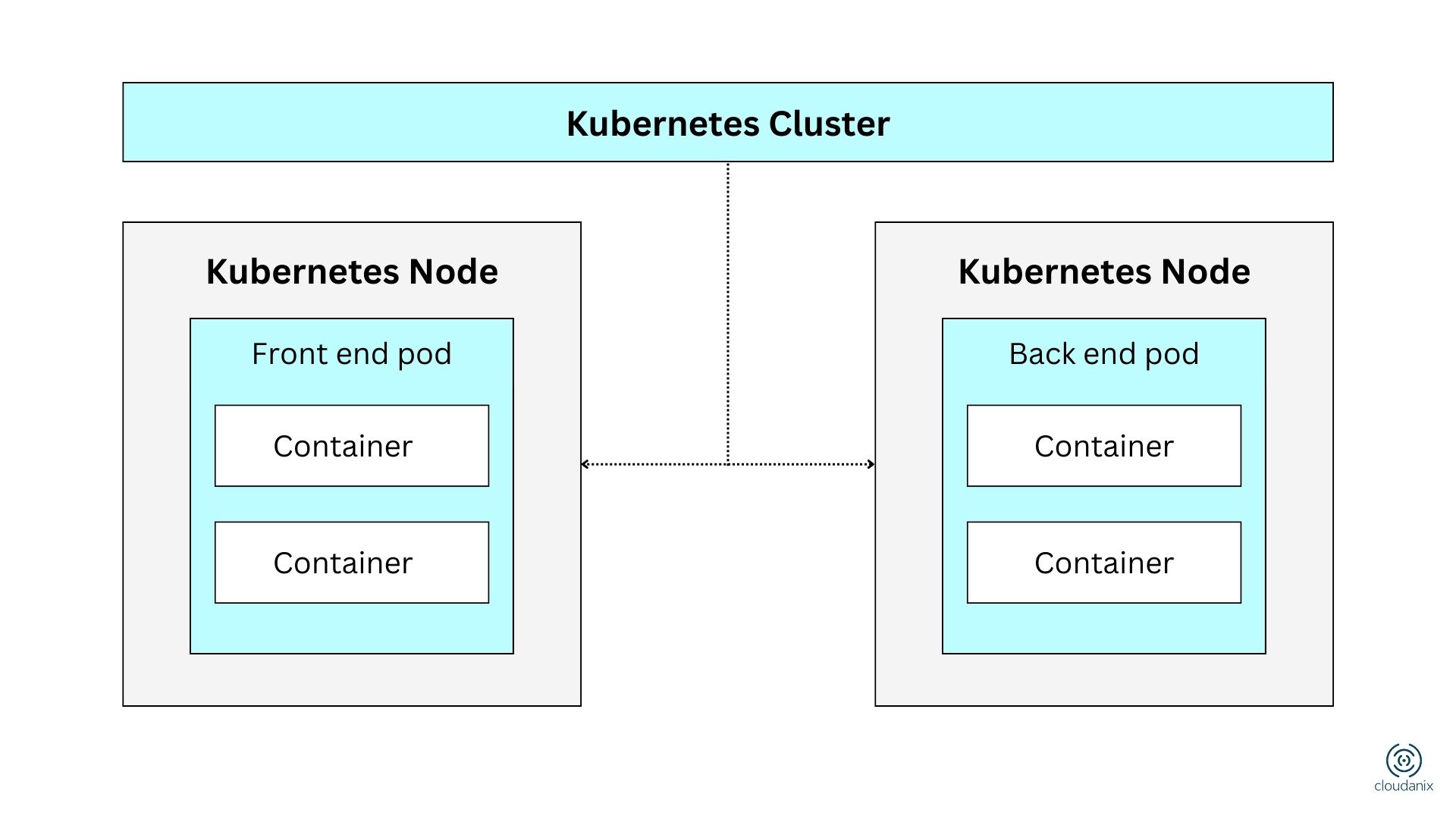
What is Azure Kubernetes Service?
Azure Kubernetes Service (AKS) is a managed Kubernetes offering by Microsoft Azure that enables businesses to deploy, manage, and scale containerized applications with minimal overhead. It removes much of the complexity found in managing vanilla Kubernetes clusters, allowing teams to focus on delivering better applications faster.
You can access AKS in three ways:
- Through the AKS Management Portal
- Using the AKS CLI (cross-platform command line)
- Via infrastructure-as-code templates
Benefits of Using Azure AKS
If you’re looking to simplify Kubernetes orchestration and reduce costs while maintaining security and compliance, Azure AKS is a solid choice.
Top 5 Benefits:
- Security & Compliance: Role-based access control, network isolation, vulnerability scanning. AKS complies with standards like HIPAA, ISO 27001, and SOC2.
- Cost-effective: Pay only for what you use, with flexible pricing tiers.
- Azure Integrations: Seamless integration with Azure Storage, Azure Compute, and Azure Networking.
- High Availability: Auto-scaling, rolling updates, and built-in load balancing ensure maximum uptime.
- Simplified Orchestration: AKS handles tasks like node provisioning and scheduling so devs can focus on code.
Azure AKS Architecture
When you create an AKS cluster, Azure automatically provisions a control plane (which remains managed by Azure and isn’t user-accessible). This control plane manages cluster configuration and operational tasks.
Key Components:
- Control Plane: Manages configuration, scheduling, and overall orchestration.
- Nodes: The worker machines (with defined CPU & memory) that run your workloads.
- Secure Communication: AKS configures communication between nodes and control plane automatically.
- Resource Groups:
- Kubernetes Resource Group – for cluster metadata.
- Node Resource Group – for infrastructure resources like VMs, networking, etc.
- Managed Identity: Used to securely interact with other Azure services.
Azure AKS Use Cases
Here are common scenarios where organizations use AKS effectively:
- Migrate Legacy Applications: Move apps into containers and manage with Kubernetes on Azure. Easily integrate Azure AD for access control.
- DevOps & Kubernetes: Combine AKS with DevOps pipelines to enhance CI/CD workflows and policy controls.
- Real-Time Data Streaming: Use AKS to process real-time sensor or telemetry data efficiently.
- Build Complex Microservices: Design and deploy scalable, modular apps with improved fault tolerance and performance.
What is Kubernetes?
Kubernetes is an open-source system for automated deployment, scaling, and management of containerized applications. It works across cloud and on-prem environments, offering:
- Declarative configuration
- Auto-scaling
- Health checks
- Rollouts & rollbacks
Kubernetes provides a portable and powerful platform for managing microservices architectures and cloud-native workloads.
Azure Misconfigurations
Cloudanix helps identify and prevent misconfigurations in your Azure AKS setup.
- Curated AKS audit checks
- Best practice enforcement
- Multi-cloud support (AWS, Azure, GCP)
Know Your Azure Misconfigurations
- Misconfigured RBAC policies
- Publicly exposed clusters
- Outdated Kubernetes versions
- Insecure API server endpoints
Secure Your AKS Workloads with Cloudanix
