Security context, Events anomaly and Bulk reviews
Real-time Events Anomaly Support for GCP & AZURE and Signals in Notifications
This has been an awaited feature by many. We’re glad to announce it’s finally here. With real-time events anomaly alerts for GCP and Azure your cloud infrastructure is safer than ever. Suspicious behavior that you may miss seeing is automatically reported to you for correction. This feature is sure to bring you a good night’s sleep and lay your worries to rest.
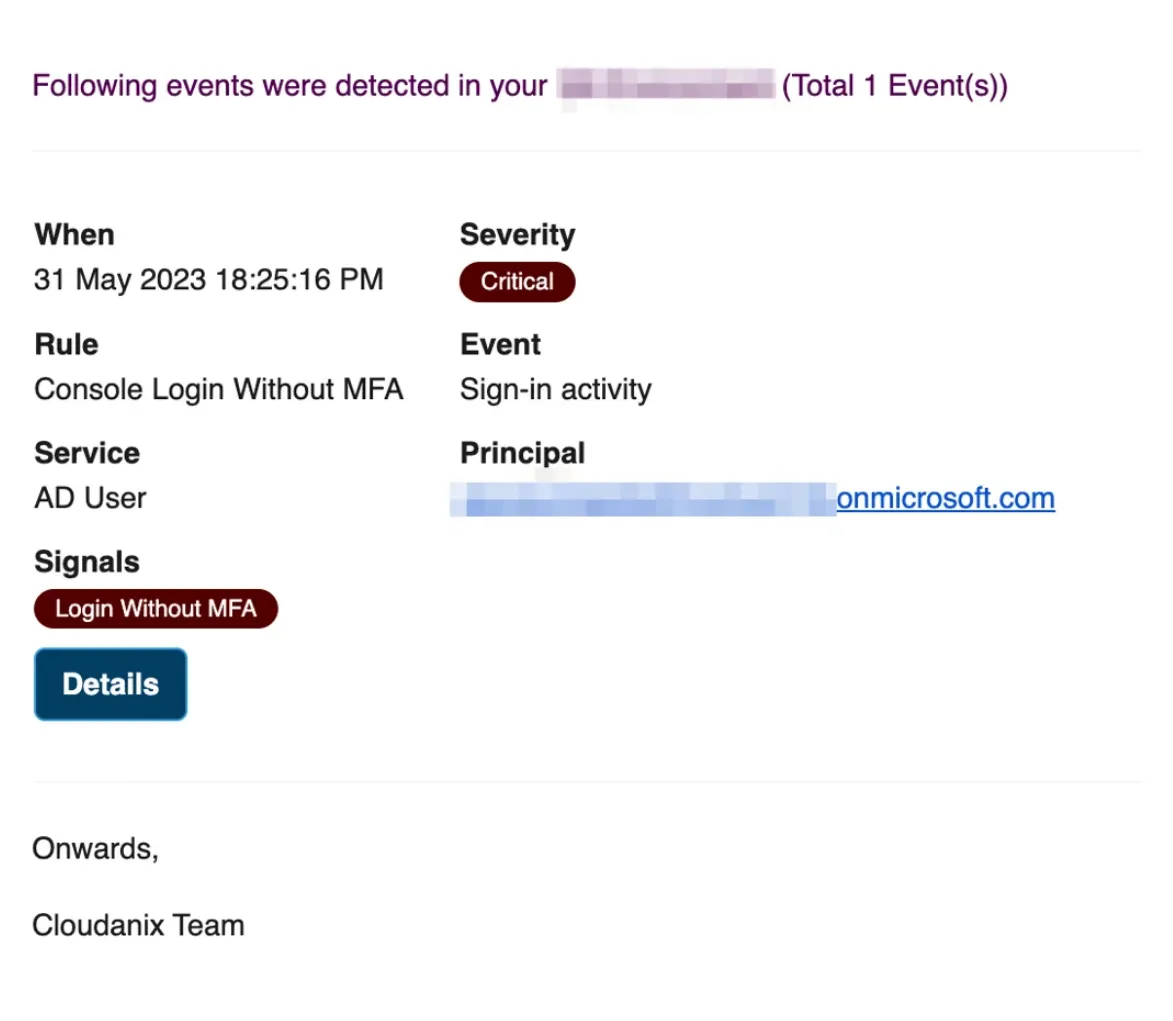
Events signal control dashboard
Auto Snooze to Avoid Alerts Fatigue
Don’t we all snooze our alarms every once in a while? Imagine your clock could snooze the days you want it to automatically and ring the other days when you need it to. Crazy right? This is enabled for you and visible in the email.
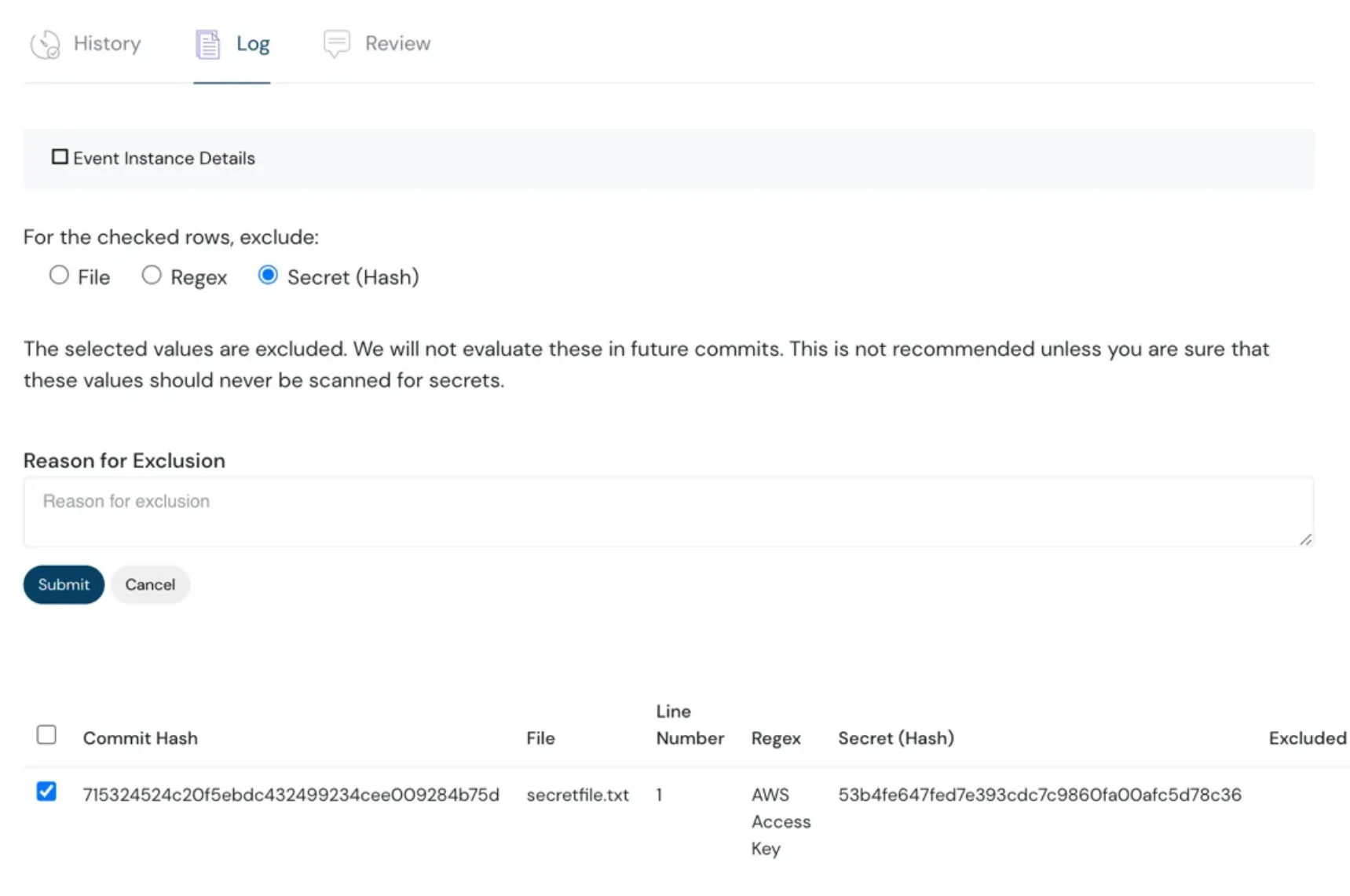
Event auto snooze feature - dashboard
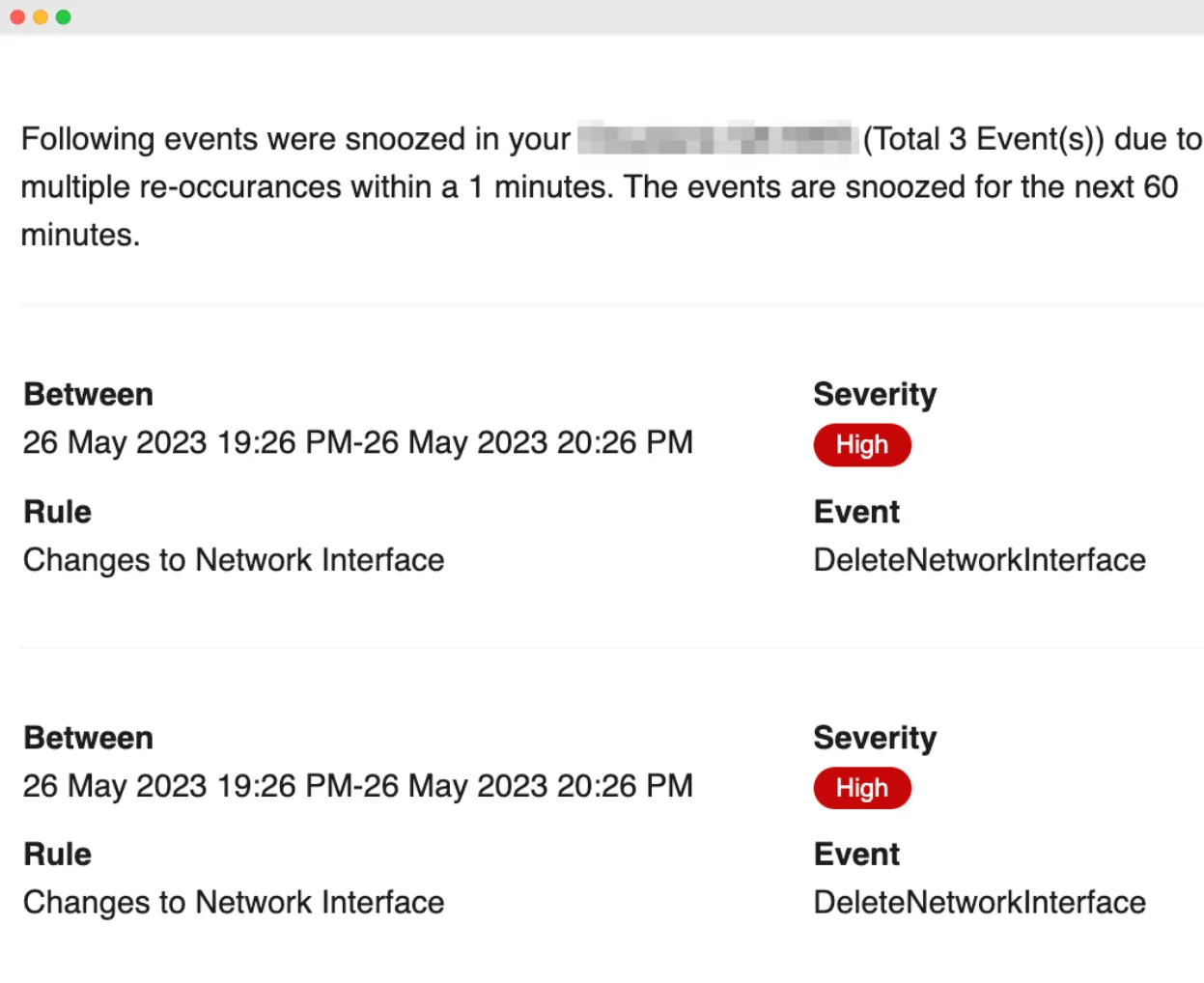
In Secret Scanning Capability – Support for Custom Patterns and Exclusions
Support for custom patterns and exclusions for existing patterns, files, or secrets.
This allows for more flexibility in identifying and managing secrets within files or code repositories. This feature enables organizations to tailor the secret scanning process to their specific needs and requirements.
Bulk Update of Events
This feature allows you to manage multiple events in a click rather than making individual updates to each event separately, saving you time and fatigue. This capability is particularly useful in scenarios where you need to apply a consistent change or modification across a large number of events simultaneously.
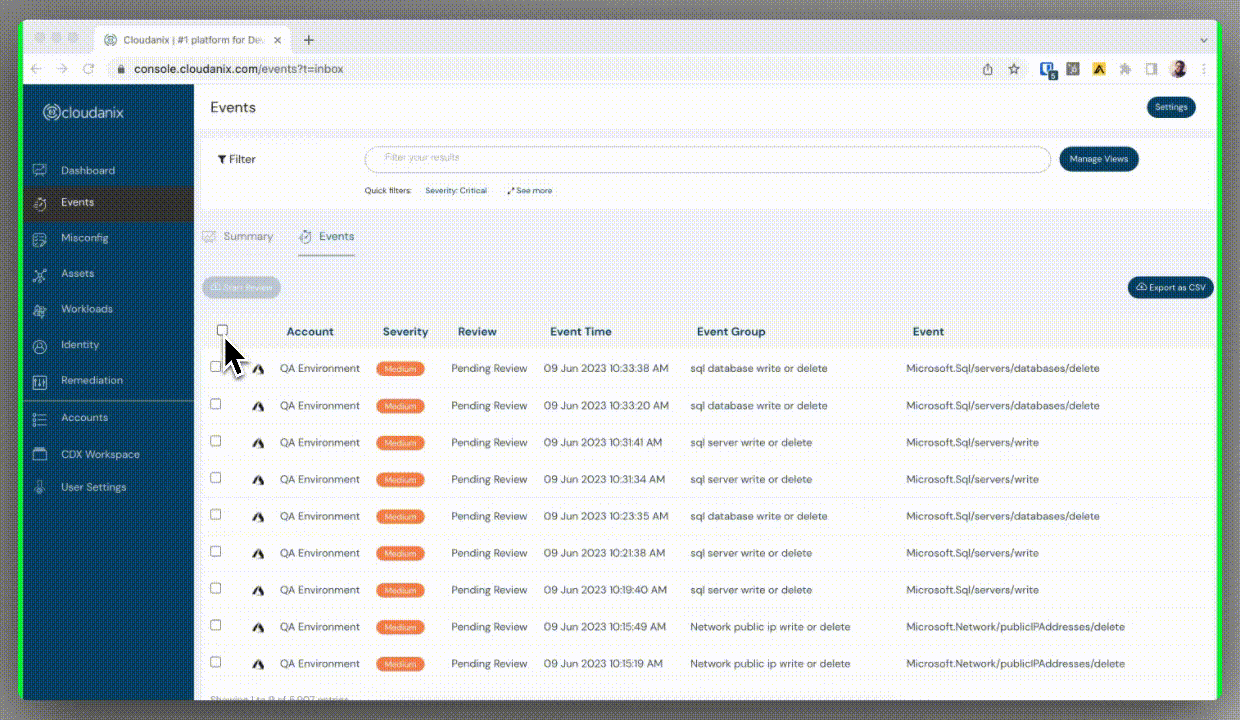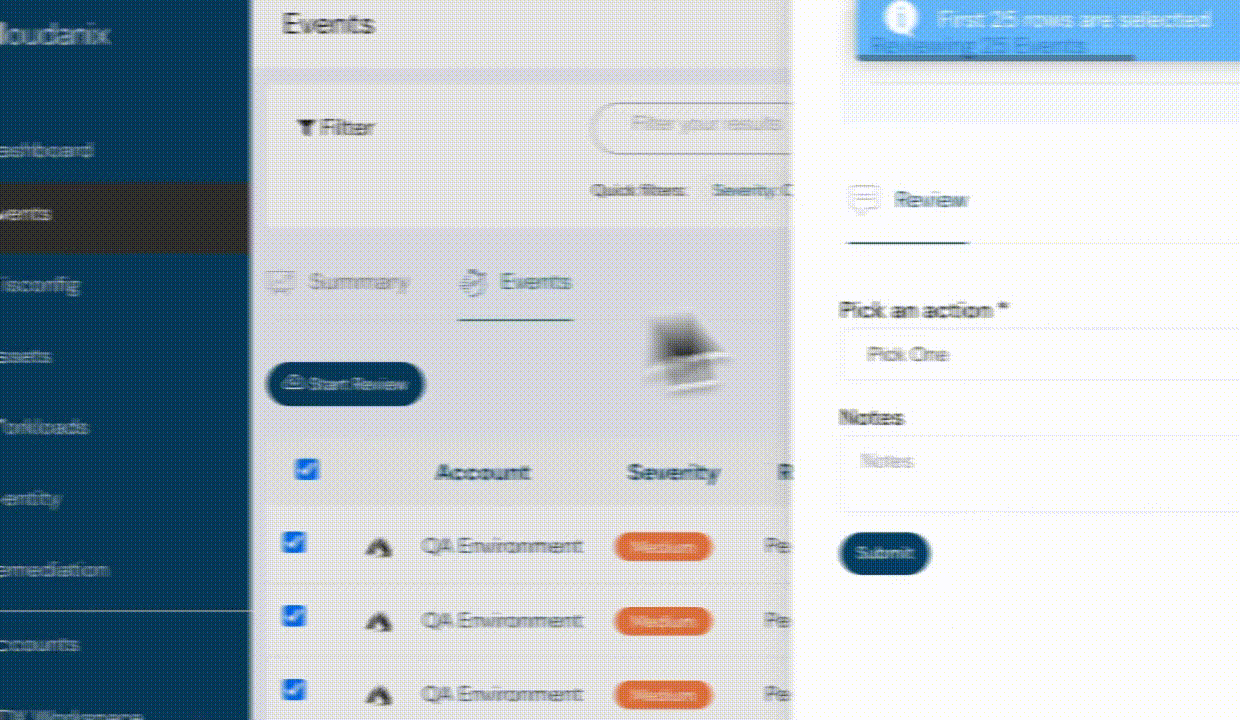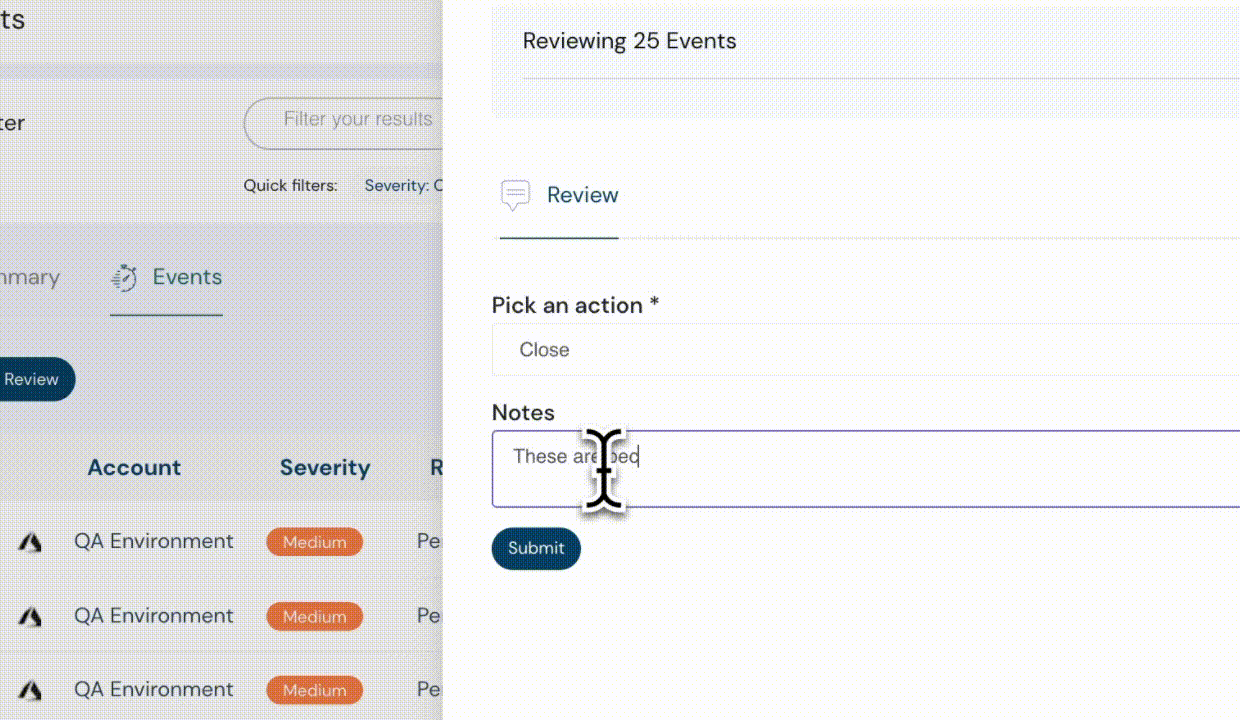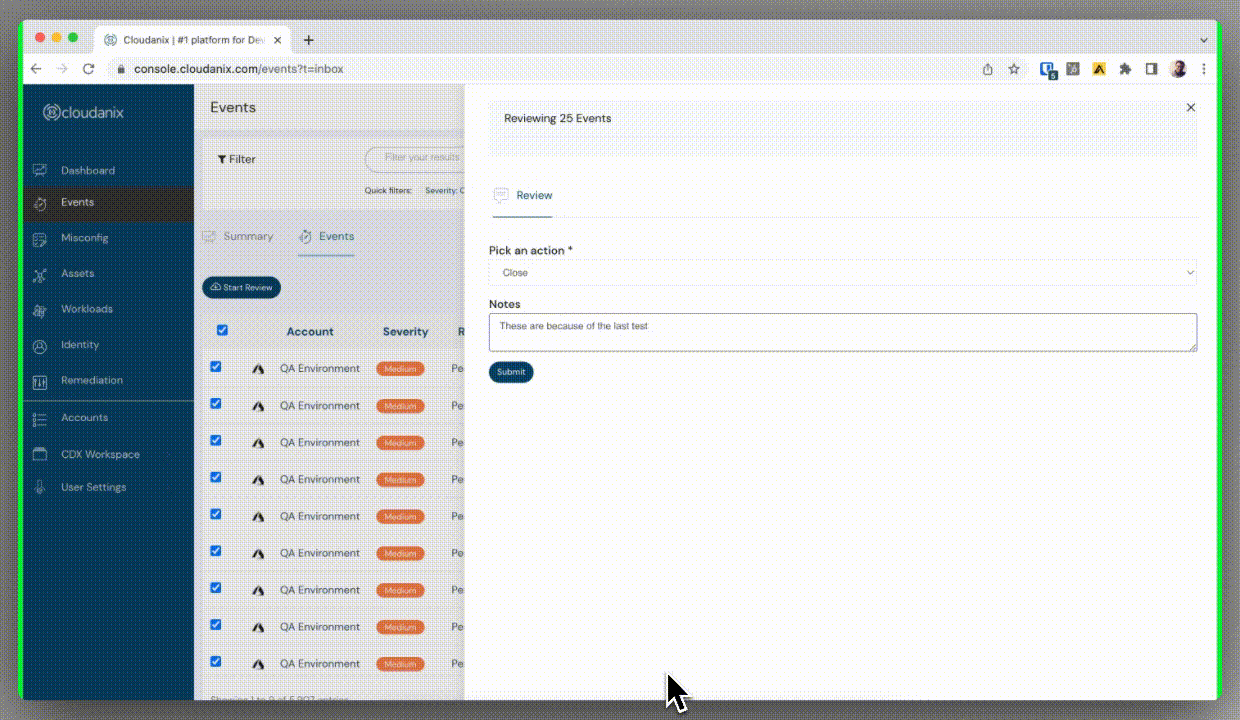
Bulk events feature - Cloudanix dashboard
Additional Updates
- Scan full repository for secrets in both Github and Bitbucket.
- Additional Events support for IAM in Azure (e.g., permissions updated for Service Account, User MFA changes, etc.)
Coming Soon
- Attack Path
- VM Security
TODO:// is not an option for Cloud Security**
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedBlog
Read More Posts
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Tuesday, Feb 10, 2026
The 2026 CNAPP Compliance Framework: Turning Audit from Crisis to Continuity
Introduction: The Death of the Point-in-Time Audit In the high-velocity cloud landscape of 2026, the traditional app
Read MoreThursday, Feb 05, 2026
CSPM vs. CNAPP: Navigating Cloud Security Evolution for Modern Enterprises
The shift to cloud-native architectures represents a fundamental change in how applications are designed, built, and dep
Read MoreThursday, Jan 22, 2026
Top 10 Identity and Access Management Solutions
Identity and Access Management (IAM) has traditionally been considered one of the boring parts of security. But with the
Read More