Introducing the New Cloudanix Dashboard
We hope this year is off to a great start for you. Cloudanix is going through a lot of work to be as user-friendly as possible so that getting the security right doesn’t take all your time!
The month has just passed, and we have a brand NEW DASHBOARD!
What’s new this month?
We have had quite a change in the look and feel of our product. Here is what you should check out that has changed this month:
- Our Logo! Cloudanix has released its new and updated Logo!
- Our UX is better now. You can navigate through the dashboard much more easily.
- Last month we had released Container Security capability. In addition to k8s, we can also protect your k3s based workloads. Why should Edge workloads be left without security monitoring?
Take a quick look at how our Dashboard changed
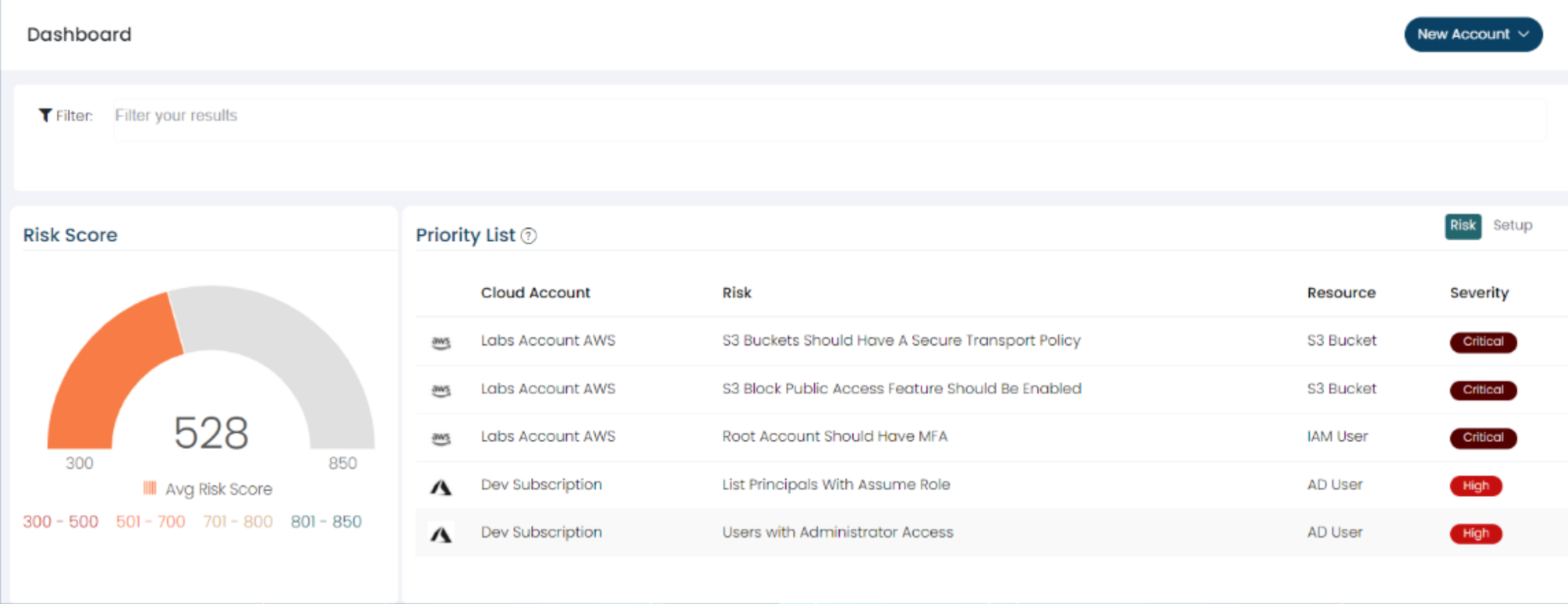
Cloud security Software | Cloudanix
And also,
We would like to remind you that our Container Workload Protection (CWPP) is Live if you missed it last month!
TODO:// is not an option for Cloud Security
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedBlog
Read More Posts
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Wednesday, Nov 05, 2025
From Static to Strategic: Modernizing Privileged Access for Cloud Infrastructure
The promise of the cloud – agility, scalability, and innovation – has revolutionized how enterprises operate. Cloud infr
Read MoreTuesday, Sep 30, 2025
Eliminate Standing Access: Introducing JIT Kubernetes for Azure AKS Security
The Security Mandate: Why Permanent Access Fails Mission-Critical AKS Kubernetes has become the operating system of
Read MoreFriday, Aug 08, 2025
User Access Review in Cloud Security: A Foundational Guide to Securing Your Cloud Environment
Introduction: The Unseen Gatekeepers of Cloud Security In the rapidly expanding landscape of cloud computing, organi
Read More