Real-time scan, Attack path graph view and Global search
Cloudanix is now an AWS ISV Accelerate partner.
This means that AWS recognizes the work Cloudanix is doing in the security space, and you, our customers are to thank for that. So Cheers to you.
Realtime Vulnerability Scanning for Virtual Machines
Similar to real-time threat detection for Kubernetes clusters, we have extended that to Virtual Machines. Detect malwares and vulnerabilities in your Hosts real-time, instead of waiting for the end of the week or the end of the month assessments.
We maintain an up to date list of all applications installed on the endpoints, use that to identify vulnerable applications using database of CVEs (Common Vulnerabilities and Exposures)
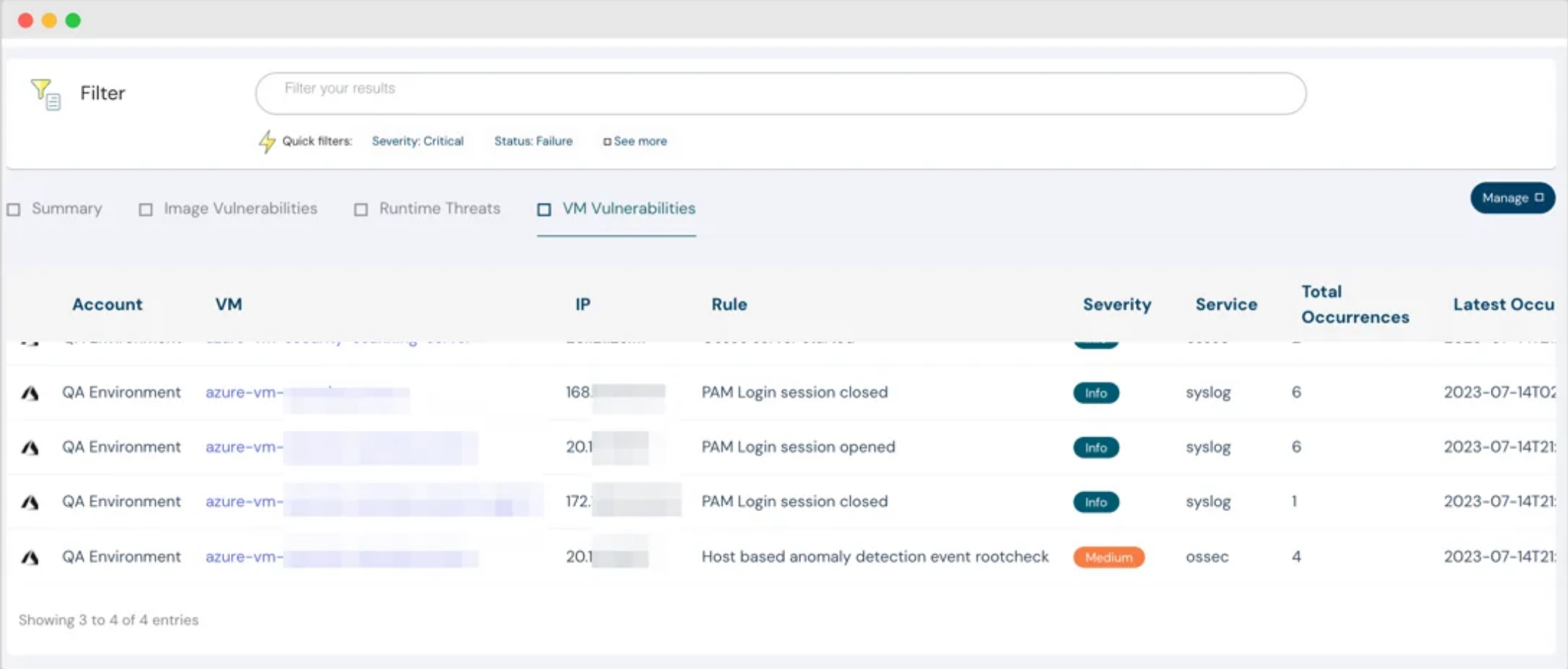

VM vulnerability scanning
PAM login session details
Global Search
Search for any asset, principal, ip, events, etc. and you can find out misconfigurations, events, and asset Information, all in one place.
Global search feature in dashboard
Global search feature detailed view in dashboard
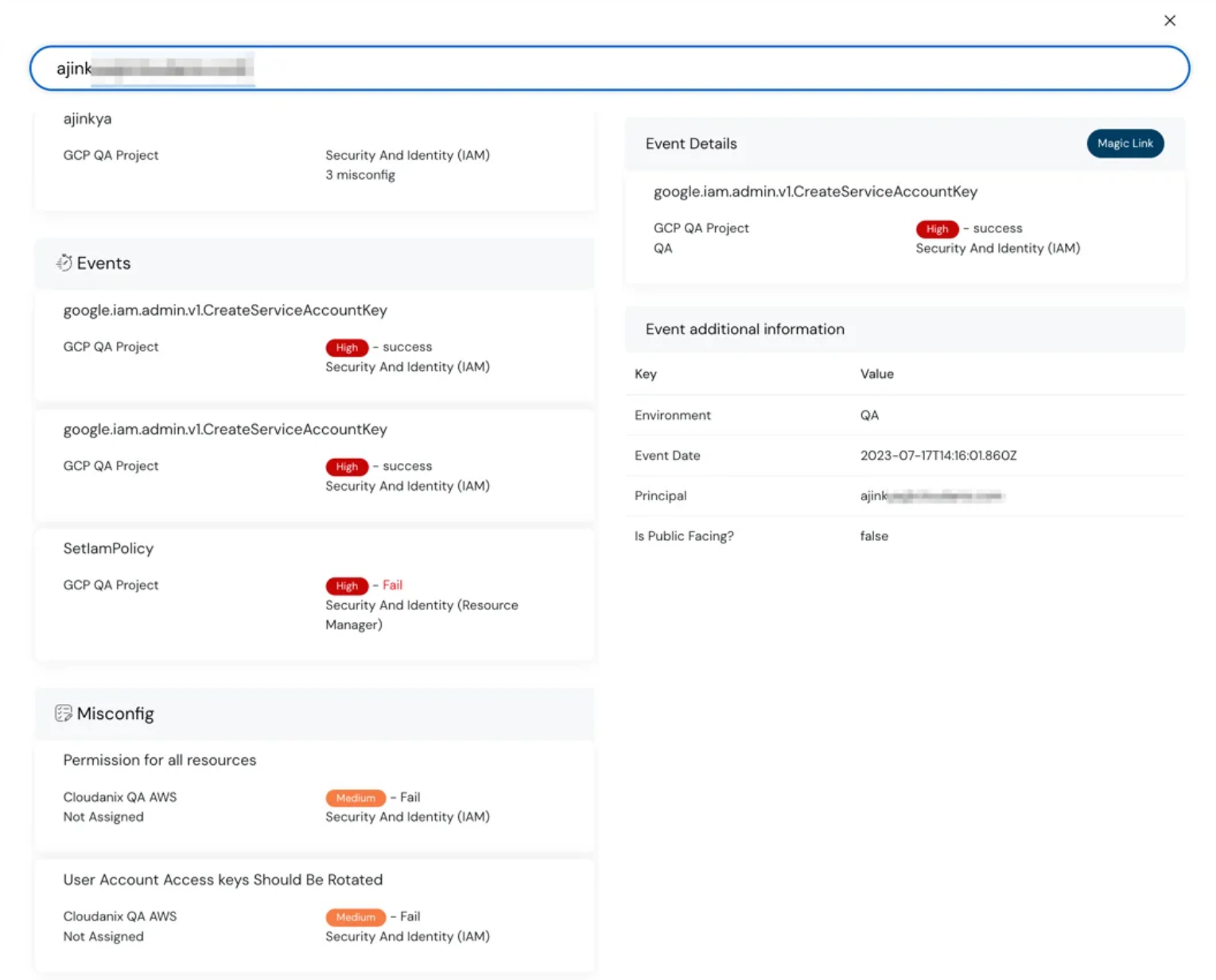
Graph View of Attack Path and Connected Assets
It’s not enough to see an asset information without its related assets and also, if there’s an attack path that can be exploited. With the connected assets view, you can do both. You can expand this further by clicking on any node and see its connected assets as well.
secret scanning capability - dashboard
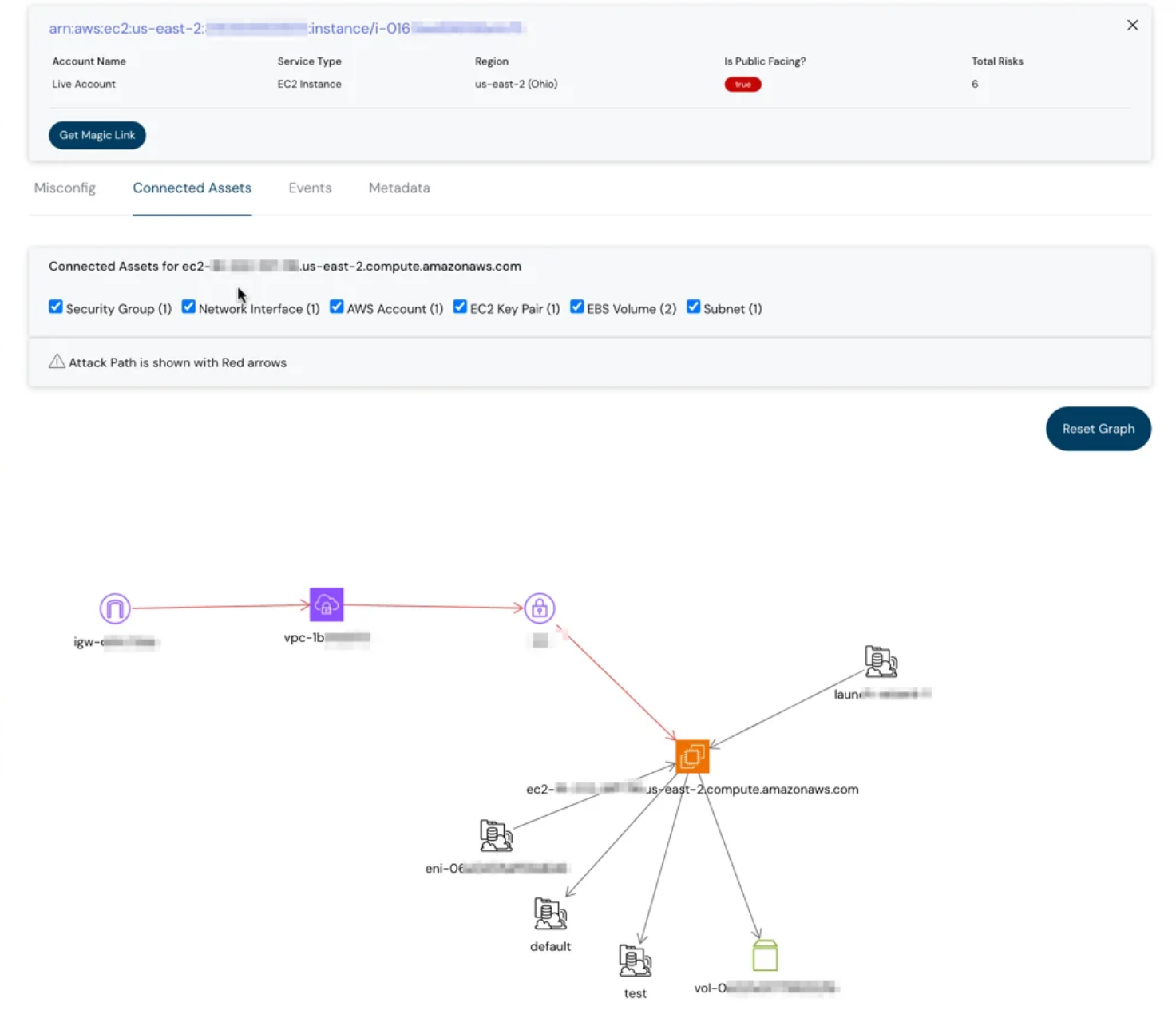
Shortcuts in misconfigurations
We are introducing shortcuts for rule activation/deactivation, review initiation, docs, and magic link.
Shortcuts in misconfig - Cloudanix dashboard
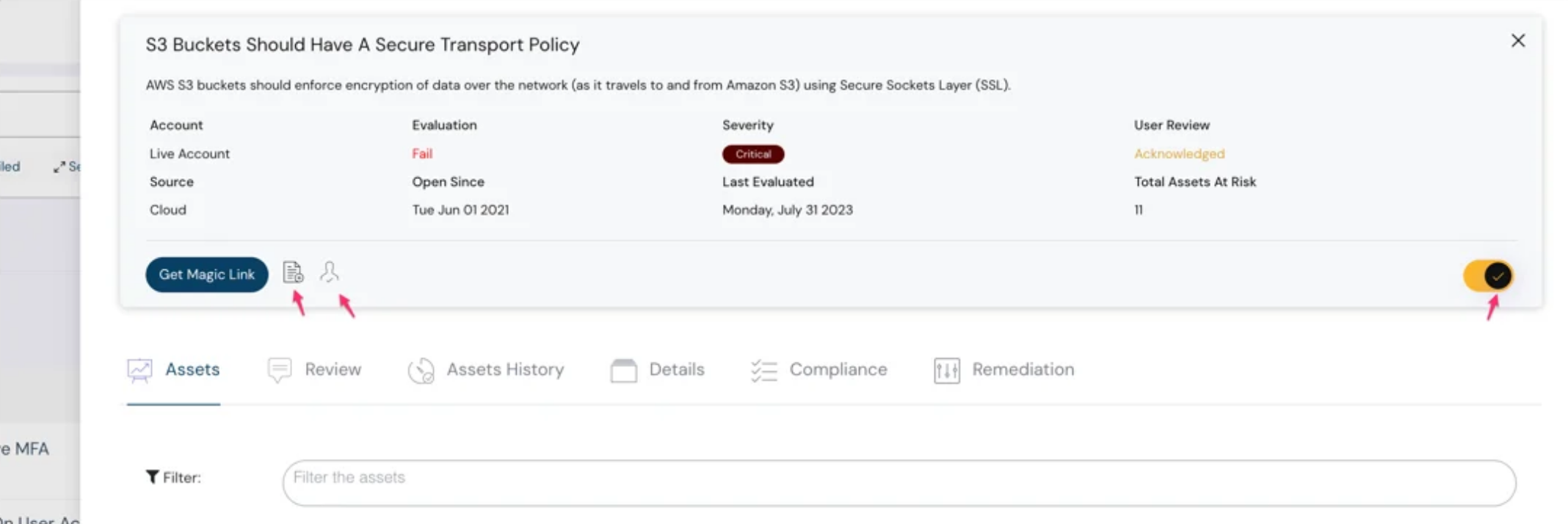
Re-designed Dashboard, Events & Misconfigurations
We have re-designed the dashboard, events, and misconfigurations to bring forward the most useful information for your day-to-day work. Do share if you have any feedback. We would love to hear and improve.
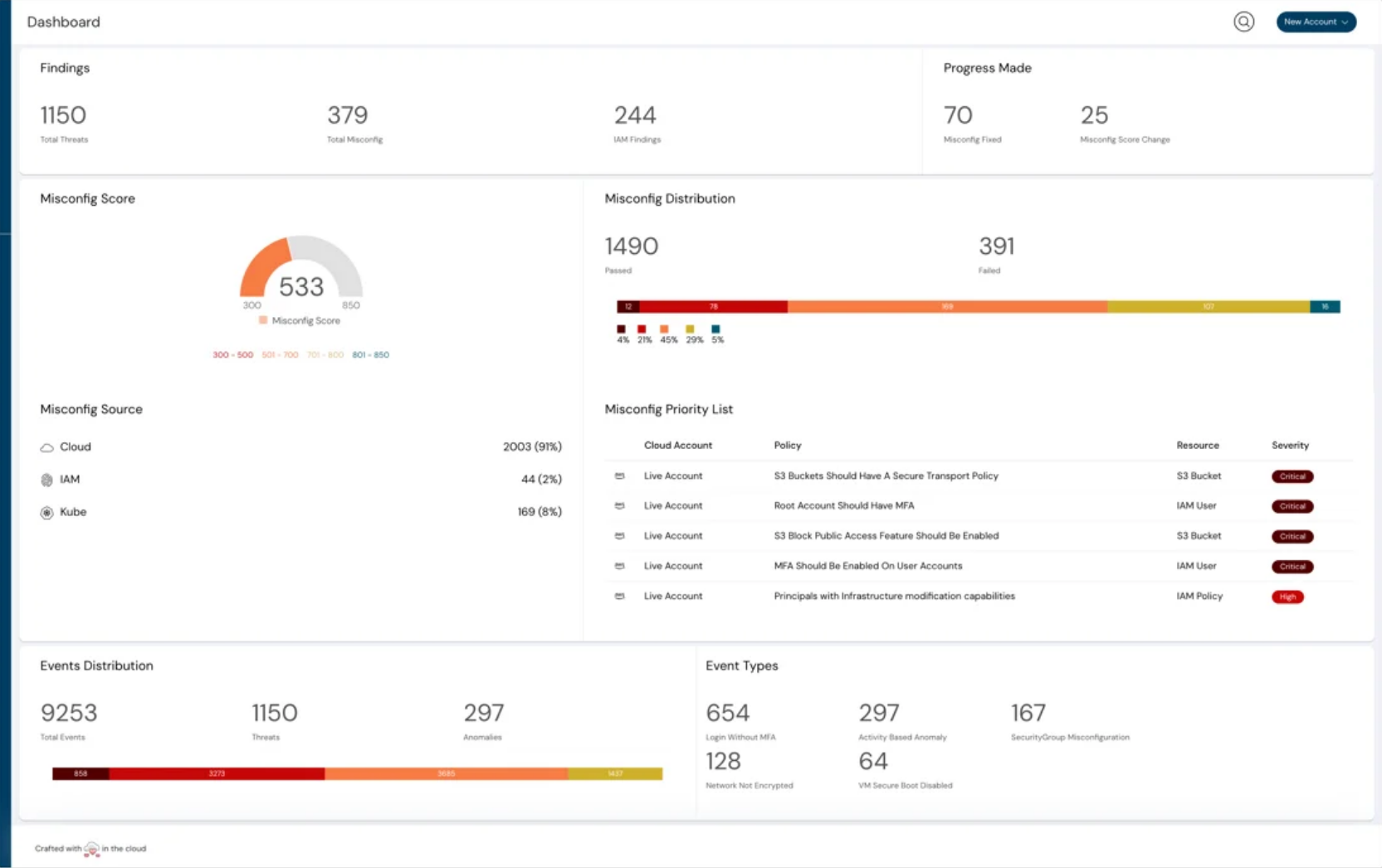
The new redesigned dashboard
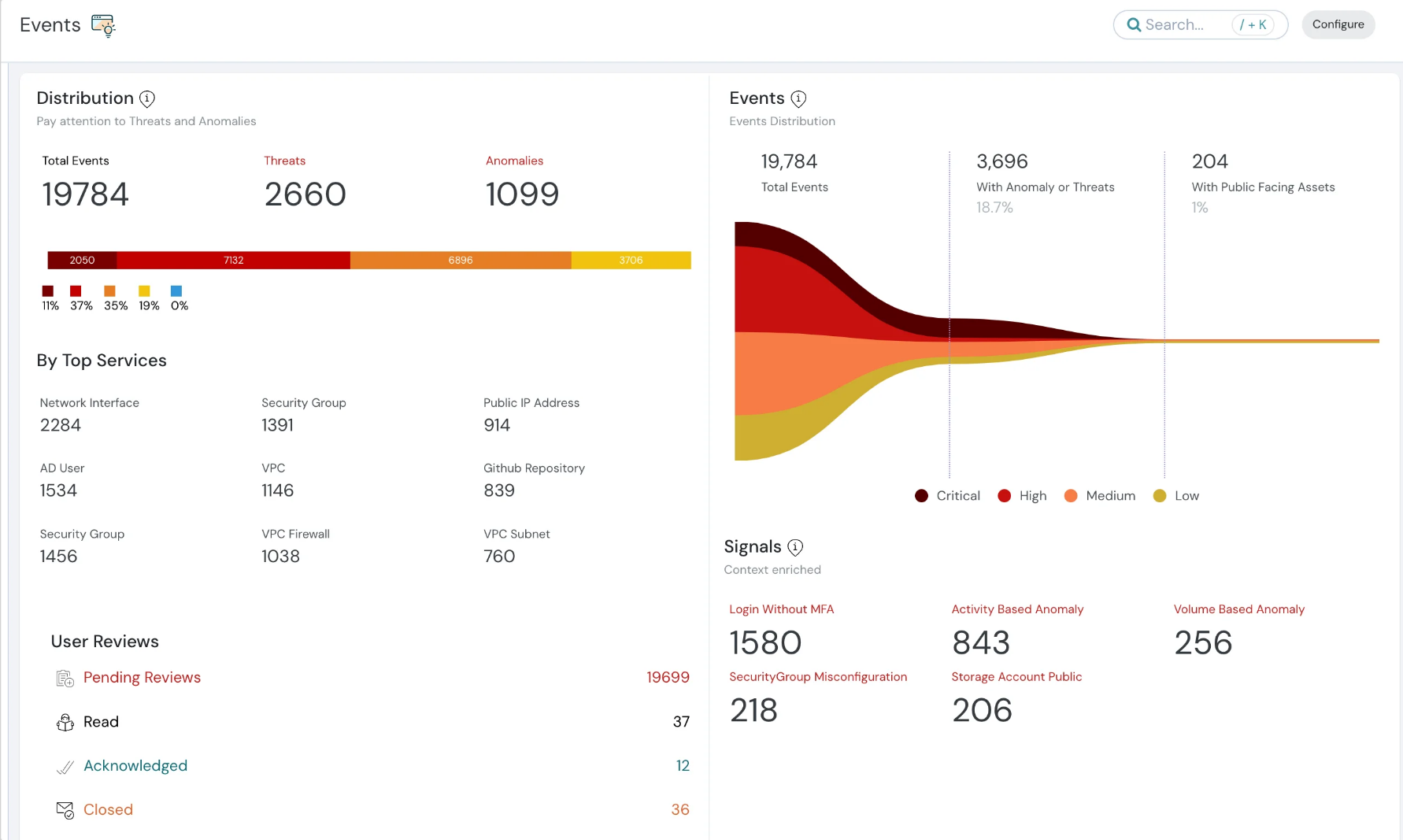
The new redesigned events dashboard
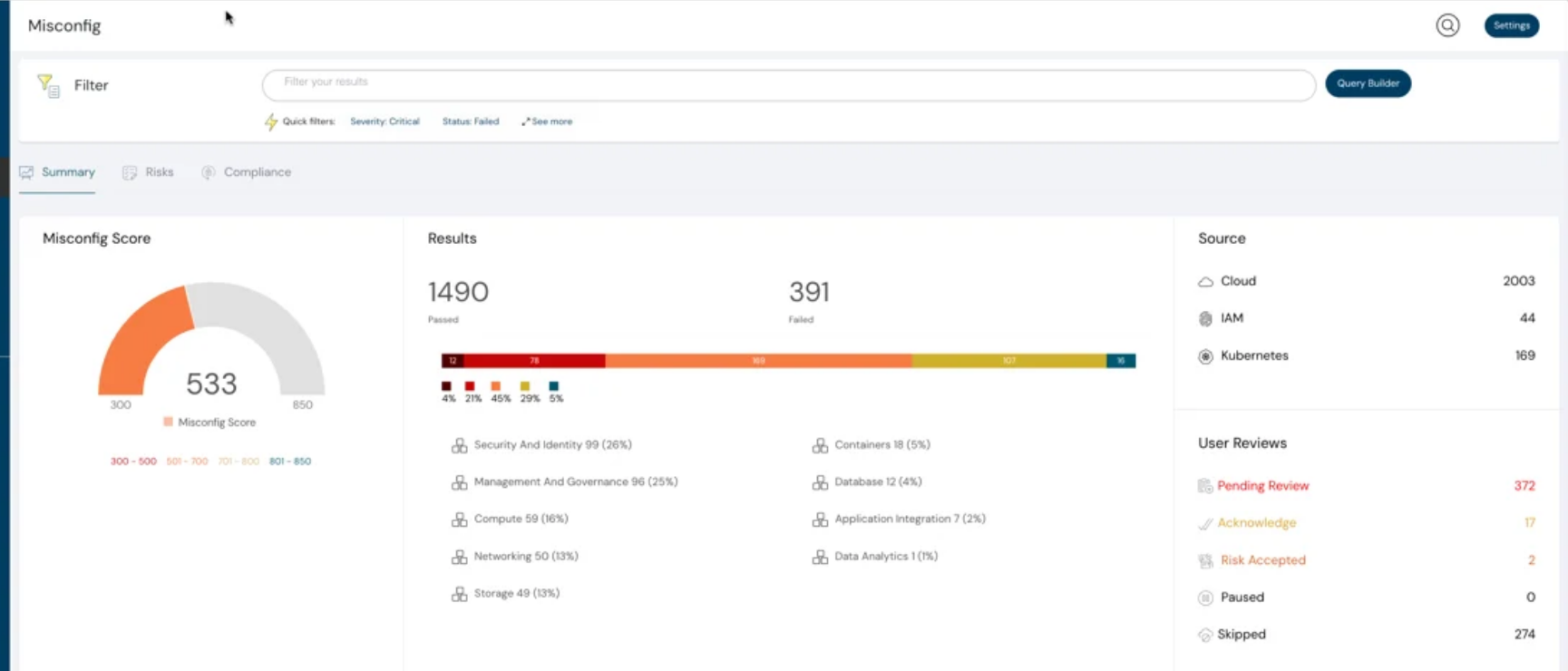
The new redesigned misconfig dashboard
Here are some more goodies for you
Image Scanning at Build Time with GitHub Actions - Auto-scan your images before deploying to avoid pushing vulnerable containers to production.
With our GitHub Action, you can scan and view findings in GitHub Workflows and in Cloudanix Console.
Industry News
- Starting Feb 1, 2024 - AWS would charge for IPv4 addresses
- Short-Term Service Account Keys in GCP
- Advantages of EPSS 3.0
TODO:// is not an option for Cloud Security
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedBlog
Read More Posts
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Wednesday, Nov 05, 2025
From Static to Strategic: Modernizing Privileged Access for Cloud Infrastructure
The promise of the cloud – agility, scalability, and innovation – has revolutionized how enterprises operate. Cloud infr
Read MoreTuesday, Sep 30, 2025
Eliminate Standing Access: Introducing JIT Kubernetes for Azure AKS Security
The Security Mandate: Why Permanent Access Fails Mission-Critical AKS Kubernetes has become the operating system of
Read MoreFriday, Aug 08, 2025
User Access Review in Cloud Security: A Foundational Guide to Securing Your Cloud Environment
Introduction: The Unseen Gatekeepers of Cloud Security In the rapidly expanding landscape of cloud computing, organi
Read More
