How to setup Multi Factor Authentication (MFA) devices in AWS?

Multi-factor Authentication (MFA), Why do I need it?
The most common way used to secure any account (or application) is using a password and username or email. This method of login provides only a single layer of security. And the credentials can be compromised by using methods like brute force attacks. Brute Force Attacks can take a long time, but if your password is something that is of common knowledge then it can be cracked fairly easily. Also if someone has eavesdropped on you while you were entering your credentials then your account is also compromised. Hackers use phishing, social engineering, and doxing tactics to reveal some of your personal information and use that to crack your password. So in order to make accounts more secure MFA is the key.
What is Multi-factor Authentication?
Multi-factor authentication requires the user to provide more than one verification factor to gain access to an account. The first factor for authentication can be a username and password. The subsequent ones can be verified through a Virtual MFA device like Authenticator App (ex: Google Authenticator) or Hardware Tokens. These devices generate a six-digit OTP code for the account, the OTPs can also be received in your email or through SMS. Another secure way is using a hardware token generator or using a YUBI key which uses biometrics(fingerprint) for authentication.
Note: As a security best practice root account should not be used to manage access to your account.
FIDO security keys
The hardware security key is provided by some third party like Yubico. The security key is connected to the USB port and the authentication is done with the fingerprint of the user. The FIDO key supports multiple root accounts and IAM users using a single security key
Virtual authenticator app
The virtual authenticator app uses a time-based-one-time-password. When you log in with a username and password you are also prompted to provide an OTP which is rotated after a few seconds in the authenticator app.
TOTP hardware tokens
Hardware tokens also use the TOTP algorithm to generate one-time passwords as used in the virtual authenticator app.
Use cases for multiple MFA devices
- You can use multiple MFA devices for a single account. While authenticating you can use either of the MFA devices. If you lose one of the MFA devices you can use the other MFA device to login.
- If the user of the MFA device is unavailable you can use the other MFA device to maintain access.
- Additional MFA devices can be securely stored in a locker or safe for emergency uses.
Setup Multiple MFA devices in AWS
Register first MFA Device
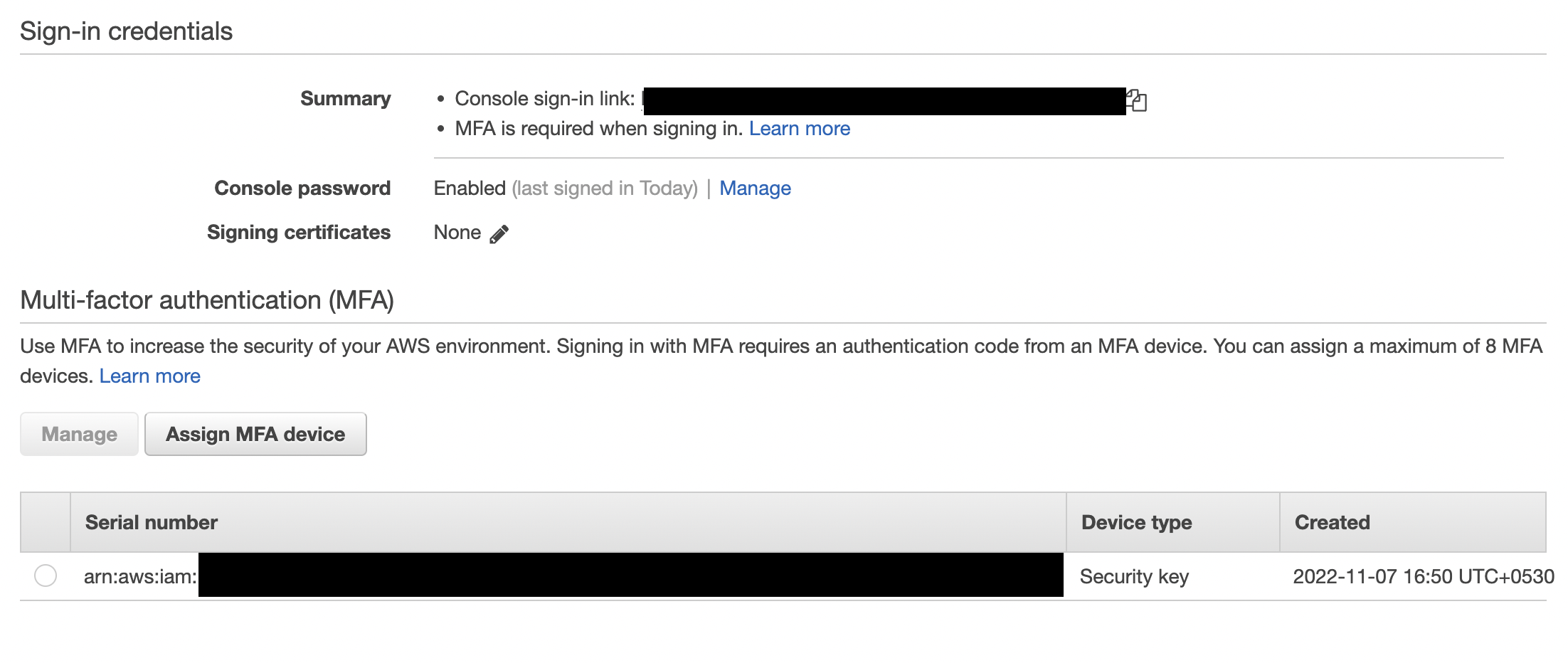
- For Multi-factor authentication (MFA), choose Assign MFA device.
- Select the type of MFA device that you want to use and then choose Continue.
- Give a name to the MFA Device

Register second MFA device
- Go to IAM Users click on Security Credentials
- Assign MFA device

- You Can select now a Security Key like YUBI key
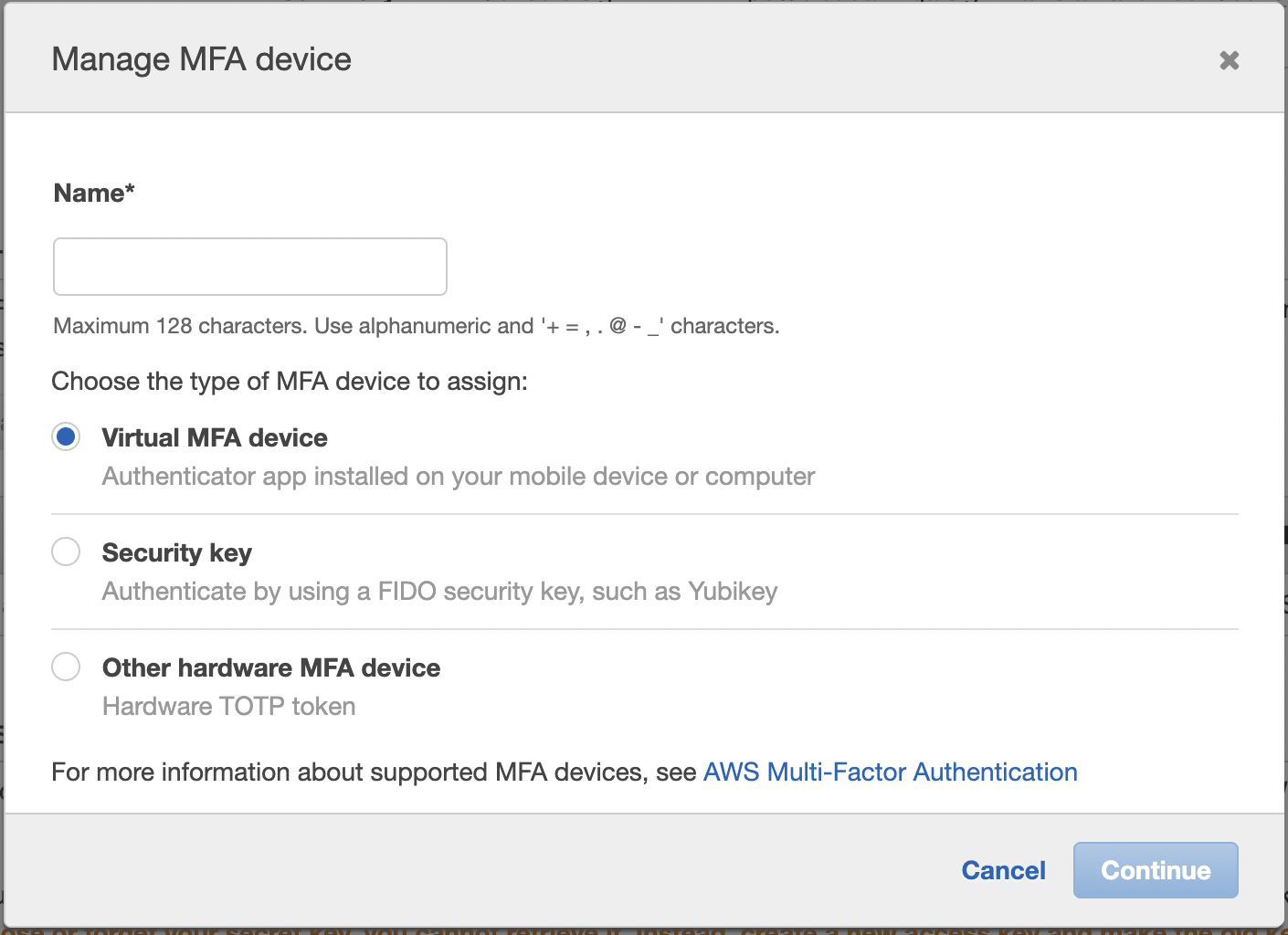
- Now you have two MFA devices registered for the User
Login with MFA
- Sign in to the AWS console.
- Enter your username and password.
- For Additional verification required select the type of MFA device that you want to use to continue. authenticating, and then choose the Next
- If you are using Multiple MFA devices you will get the following.

- If you are using FIDO key you will get the following

- Select the USB security key for the FIDO key or you can select Virtual MFA device if it is set up for the user.
Note: Multiple MFA is now available in AWS except for customers in AWS GovCloud US regions or in China regions. MFA service is available at no extra cost.
Conclusion
In this blog, we learned things
- What is MFA and why it is required.
- How we can set up multiple MFA devices for AWS root users or IAM users.
- Advantages of using multiple MFA devices.