Attack Vector Enhancement, Image Security with Prioritization, Code Blocks and Workflows
January was a busy month for both the business and technical teams. At Cloudanix, we know that user experience is critical, especially for small teams aiming to achieve more with less. This update, shaped by customer feedback, focuses on efficiency and usability.
Guided Tours
We’ve introduced interactive Guided Tours across the platform, helping you navigate with ease and focus on the most critical insights. Designed to enhance learning and onboarding for new users.
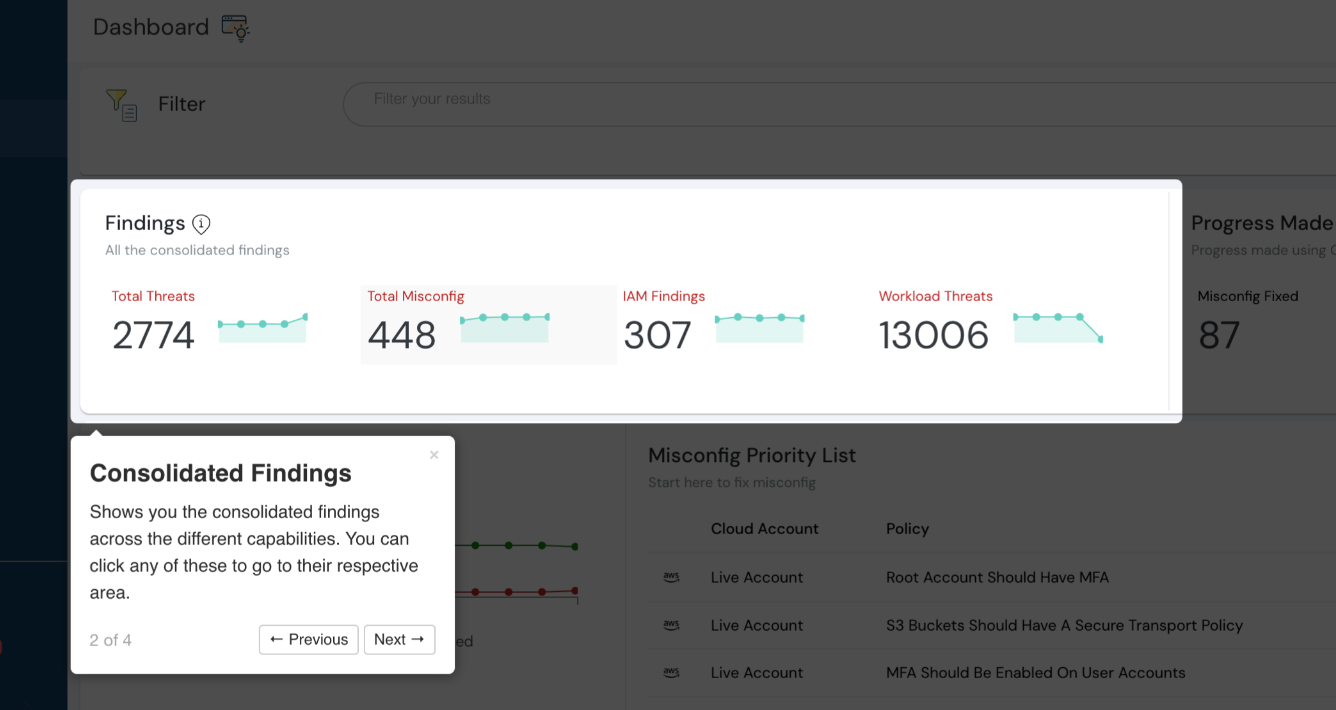
Consolidated findings at glance
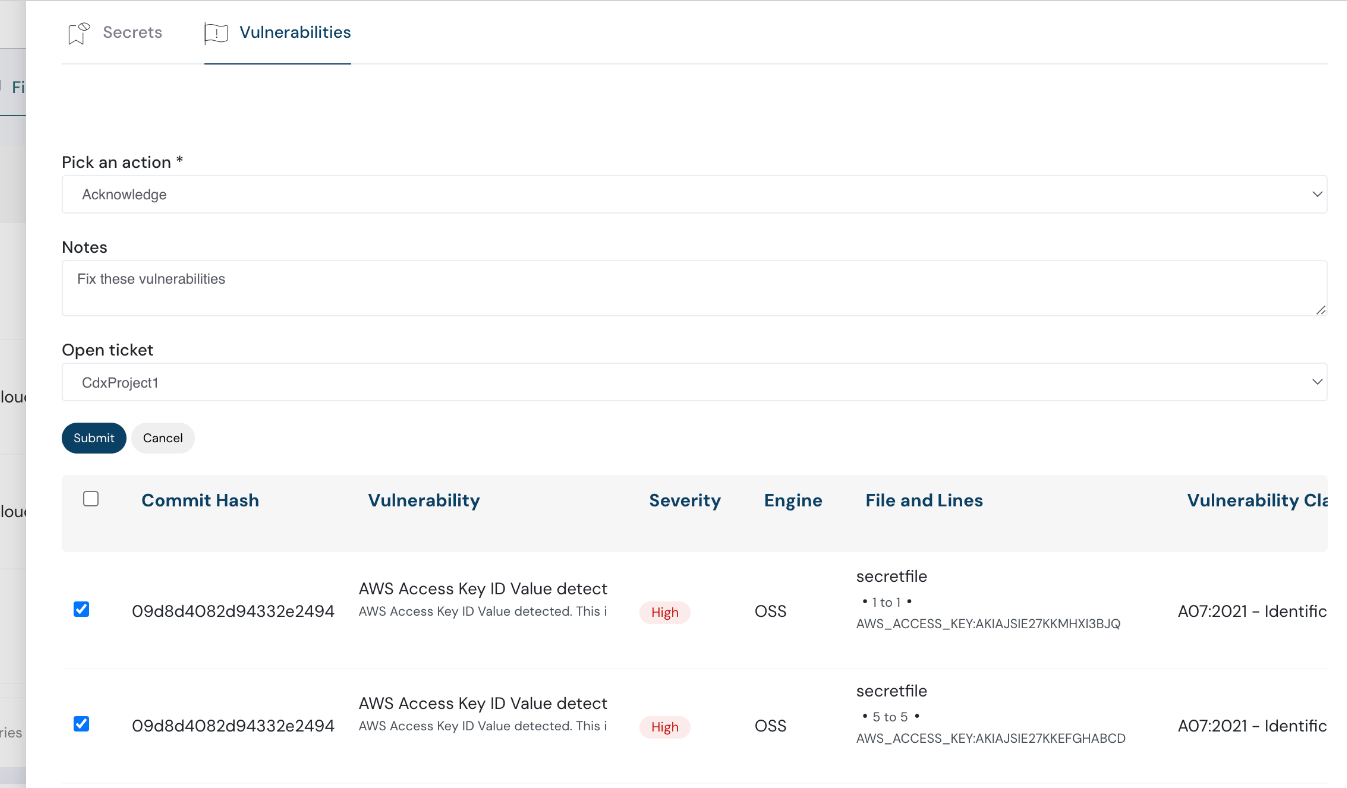
Code Blocks and Workflows
Code Security now displays code blocks affected by vulnerabilities and enables triaging via the new Review Capability, which includes:
- Pause
- Acknowledge
- Accept Risk
This allows security teams to manage findings more efficiently.
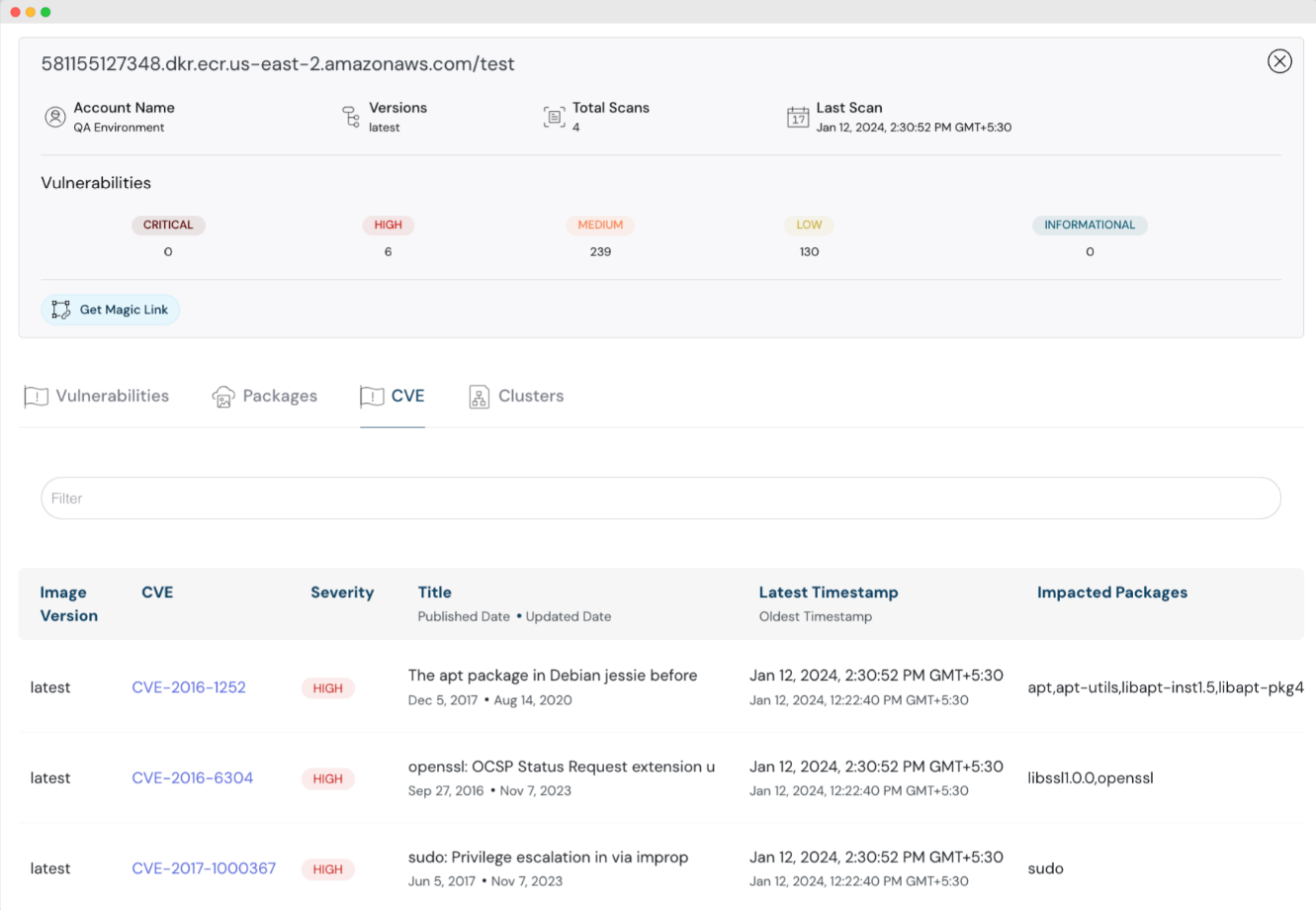 Code security showcasing affected vulnerabilities
Code security showcasing affected vulnerabilities
 Code security feature open ticket option
Code security feature open ticket option
Time-Based Filters for Events
Events, Threats & Anomalies now support a Time-based “Events Since” filter, allowing you to quickly view and analyze recent activity for faster response.
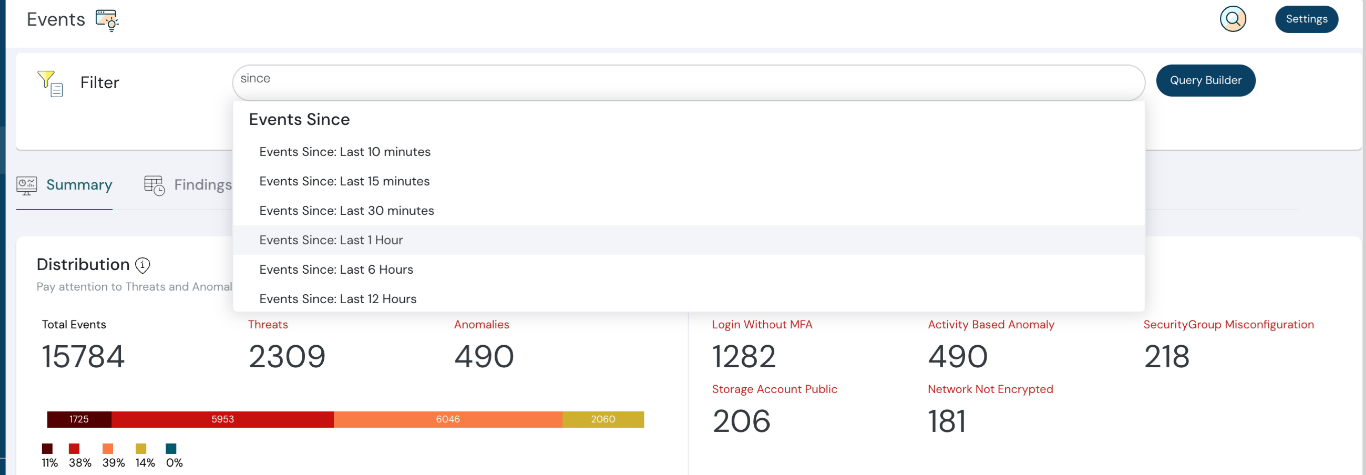 Events based filters now available
Events based filters now available
Attack Vectors Include Subdomain Findings
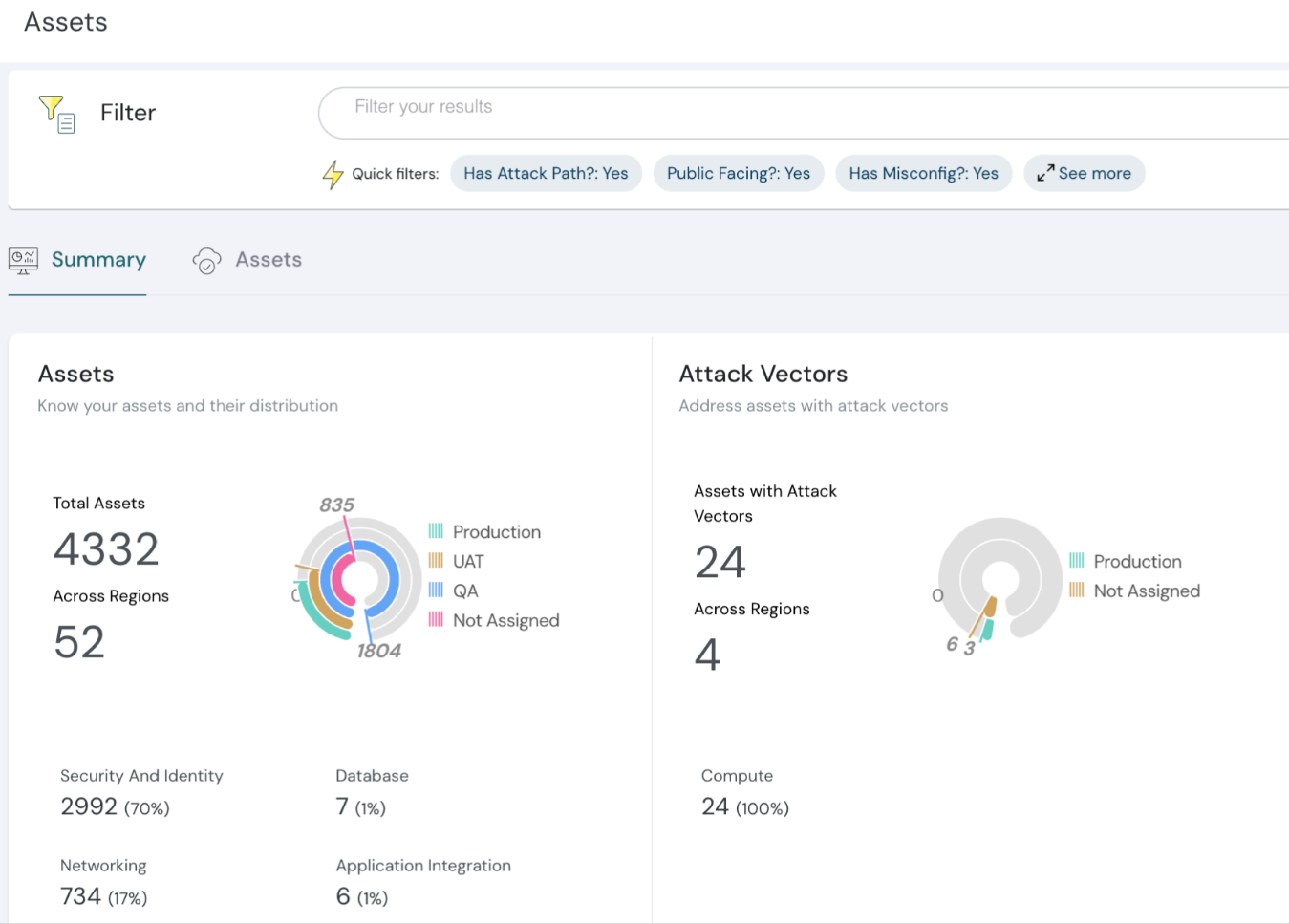
Attack Vectors are now extended to include findings from vulnerable subdomains, broadening visibility into potential attack surfaces.
 Assets with attack vectors
Assets with attack vectors
Image Security Prioritization
Image Security now supports grouping findings by vulnerabilities, packages, and CVEs, along with active cluster usage data, enabling prioritization of remediation.
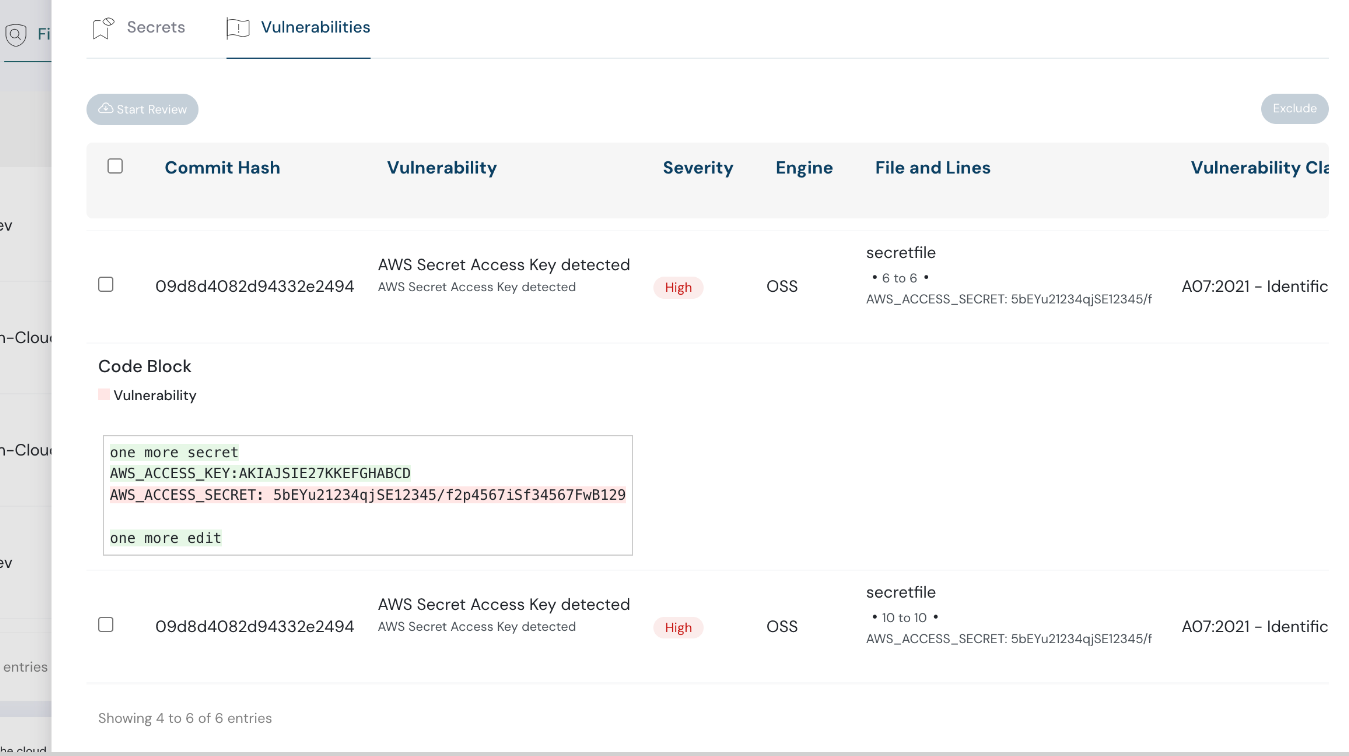 Image security is more enhanced
Image security is more enhanced
Multiple and Area-Specific Jira Projects
Cloudanix now integrates with multiple Jira projects, allowing you to assign specific projects to specific capabilities (e.g., code security vs. misconfiguration). This improves task organization and streamlines workflows.
Cloudanix Blogs
- AWS & Cloudanix: Real-Time Threat and Anomaly Detection for Workloads on AWS
- AWS & Cloudanix: How Cloudanix Secures Containerized Applications Running on Amazon EKS
- Launching Cloud Console Link Open Source Project
Additional Resources
Industry News
- AWS to Charge for Public IPv4 from Feb 01
- Azure Attack Paths
- AWS re:Invent Security Recap
- Securing Google Cloud Admins
- Dependency Confusion Supply Chain Attack
TODO:// is not an option for Cloud Security
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedBlog
Read More Posts
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Thursday, Feb 05, 2026
CSPM vs. CNAPP: Navigating Cloud Security Evolution for Modern Enterprises
The shift to cloud-native architectures represents a fundamental change in how applications are designed, built, and dep
Read MoreThursday, Jan 22, 2026
Top 10 Identity and Access Management Solutions
Identity and Access Management (IAM) has traditionally been considered one of the boring parts of security. But with the
Read MoreThursday, Jan 22, 2026
Unauthorized Privilege Escalation & Secure Elevation: A Blueprint for Cloud Security Leadership
In the expansive and hyper-dynamic realm of enterprise cloud, a silent and insidious threat often overshadows more overt
Read More