Cloudanix
AWS EC2 Audit
Your EC2 instance snapshots should not be publicly accessible. This is to avoid exposing your private data.
EC2 Instance Snapshots Should Not Be Public
Your EC2 instance snapshots should not be publicly accessible. This is to avoid exposing your private data.
Long Running Instances Should Be Re-launched
EC2 instance running indefinitely in your AWS your account could increase the risk of potential issues.
EC2 AMIs Should Not Be Public
AWS AMIs should not be shared publicly with the other AWS accounts to prevent exposing sensitive data.
EC2 AMIs Should Be Encrypted
Amazon Machine Images (AMIs) should be encrypted to fulfill compliance requirements for data-at-rest encryption.
EC2 Instances Should Not Reach vCPU Limit
Monitoring vCPU-based limits for on-demand EC2 instances avoids resource starvation. Service Quotas is an AWS service that enables you to view and manage your quotas from a central location. Quotas, also referred to as limits, are the maximum value for your resources, actions, and items in your AWS account.
Blacklisted AMIs Should Not Be Used
Blacklist all those AMI to prevent certain security issues to attack your application. Your EC2 Instances should not use any of the blacklisted AMIs.
Default VPC Should Not Be In Use
It is recommended not to using the default VPC.
Security Groups Should Have Descriptions
Your security groups should have descriptions associated with them to help you run your operations smoothly. It serves as a documentation and guidance in future.
AMI Age Should Not Exceed the Configured Age
Your AMI age should be more than configured number of days. This ensures that your EC2 instances deployed are secure and reliable.
EC2 Instance Should Be of Desired Type
EC2 instance launched should be from an approved list of instance types.
Detailed Monitoring for EC2 Instances Should Be Enabled
Detailed monitoring should be enabled on EC2 instances.
EC2 Classic Should Not Be Used
VPC should be used for EC2 instances instead of using EC2 Classic. VPCs are the latest and more secure method of launching AWS resources.
Scheduled Events for EC2 Instances
There are EC2 instances scheduled for retirement and/or maintenance. Kindly take the necessary steps (reboot, restart or re-launch).
EC2 Instances With Multiple Security Groups
Checks if EC2 instances have several Security Groups attached. Ideally there should be just 1 security group attach to an EC2 instance.
Termination Protection Should Be Enabled
Ensuring Termination Protection feature is enabled for EC2 instances that are not part of ASGs.
Unrestricted Netbios Access Should Not Be Allowed
No AWS EC2 security group should allow unrestricted inbound access to TCP port 139 and UDP ports 137 and 138 (NetBIOS).
Unrestricted Outbound Access Should Not Be Allowed
EC2 security groups should not allow unrestricted outbound/egress access.
EC2 IAM Roles Should Be Used
IAM Roles/Instance profiles should be used instead of IAM Access Keys to appropriately grant access permissions to any application that perform AWS API requests running on your EC2 instances.
Restrict data-tier subnet connectivity to VPC NAT Gateway
Ensuring that the Amazon VPC route table associated with the data-tier subnets has no default route configured to allow access to an AWS NAT Gateway in order to restrict Internet connectivity for the EC2 instances available within the data tier.
Unrestricted CIFS Access Should Not Be Allowed
No AWS EC2 security group should allow unrestricted inbound access to TCP port 445 and (CIFS).
Unrestricted ICMP Access Should Not Be Allowed
No security group should allow unrestricted inbound access using Internet Control Message Protocol (ICMP).
Unrestricted Inbound Access on All Uncommon Ports Should Not Be Allowed
No EC2 security group should allow unrestricted inbound access to any uncommon ports.
Unrestricted MongoDB Access Should Not Be Allowed
No security group should allow unrestricted ingress access to MongoDB port 27017.
Unrestricted MsSQL Access Should Not Be Allowed
No security group should allow unrestricted inbound access to TCP port 1433 (MSSQL)
Unrestricted MySQL Access Should Not Be Allowed
No security group should allow unrestricted inbound access to TCP port 3306 (MySQL).
Unrestricted Oracle Access Should Not Be Allowed
No security group should allow unrestricted inbound access to TCP port 1521 (Oracle Database).
Security Group Port Range
Security groups should not have range of ports opened for inbound traffic in order to protect your EC2 instances against denial-of-service (DoS) attacks or brute-force attacks.
Unrestricted PostgreSQL Access Should Not Be Allowed
No security group should allow unrestricted inbound access to TCP port 5432 (PostgreSQL Database).
Unrestricted RDP Access Should Not Be Allowed
No AWS EC2 security group should allow unrestricted inbound access to TCP port 3389 (RDP).
Unrestricted RPC Access Should Not Be Allowed
No security group should allow unrestricted inbound access to TCP port 135 (RPC).
Unrestricted SMTP Access Should Not Be Allowed
No security group should allow unrestricted inbound access to TCP port 25 (SMTP).
Default Security Group Should Not Allow Unrestricted Public Traffic
Default security groups should restrict all public traffic to follow AWS security best practices.
Unrestricted Telnet Access Should Not Be Allowed
No security group should allow unrestricted inbound access to TCP port 23 (Telnet).
Unrestricted SSH Access Should Not Be Allowed
No security group should allow unrestricted inbound access to TCP port 22 (SSH).
Unrestricted Elasticsearch Access Should Not Be Allowed
No security group should allow unrestricted inbound access to TCP port 9200 (Elasticsearch).
Unrestricted FTP Access Should Not Be Allowed
No security group should allow unrestricted inbound access to TCP ports 20 and 21 (FTP).
EC2 Reserved Instances Should Not Have Payment Failed
To ensure that none of your AWS EC2 Reserved Instance purchases have failed.
EC2 Reserved Instances Should Not Have Payment Pending
To ensure that none of your AWS EC2 Reserved Instance purchases are pending.
EC2 Reserved Instances Recent Purchases Should Be Reviewed
For regularly reviewing your EC2 Reserved Instance purchases for cost optimization (informational).
EC2-Classic Elastic IP Address Limit Should Not Be Reached
Your account should not reach the limit set by AWS for the number of allocated Elastic IPs.
EC2-VPC Elastic IP Address Limit Should Not Be Reached
Your account should not reach the limit set by AWS for the number of Elastic IPs.
AWS EC2 Hibernation Should Be Enabled
The Hibernation feature should be enabled for EBS-backed EC2 instances to retain memory state across instance stop/start cycles.
Instance Should Be Launched In Auto Scaling Group
Every EC2 instance should be launched inside an Auto Scaling Group (ASG) in order to follow the best AWS reliability and security practices.
Reserved Instance Lease Expiration In The Next 30 Days
Lists all EC2 reserved instances expiring in the next 30 days.
Reserved Instance Lease Expiration In The Next 7 Days
Lists all EC2 reserved instances expiring in the next 7 days.
Security Group Excessive Counts
Your AWS account should not have excessive number of security groups per region.
Security Group Name Prefixed With launch-wizard Should Not Be Used
EC2 security groups prefixed with launch-wizard should not be in use in order to follow AWS security best practices.
EC2 Instance Count Should Not Exceed the Limit
Your AWS account should not reached the limit set for the number of EC2 instances.
EC2 Instances Should Use Latest Generation
Your AWS servers should be using the latest generation of EC2 instances for price-performance improvements.
Security Group Rules Counts
EC2 security groups should not have an excessive number of rules defined.
Security Groups Should Not Allow Inbound Traffic From RFC 1918
No EC2 security group should allow inbound traffic from RFC-1918 CIDRs in order to follow AWS security best practices.
Unassociated Elastic IP Addresses Should Be Removed
Identify and remove any unassociated Elastic IP (EIP) addresses for cost optimization.
EC2 Instance Should Not Be In Public Subnet
No backend EC2 instances should be running in public subnets.
Unrestricted DNS Access Should Not Be Allowed
No security group should allow unrestricted inbound access to TCP and UDP port 53 (DNS).
Unrestricted HTTP Access Should Not Be Allowed
No security group should allow unrestricted inbound access to TCP port 80 (HTTP).
Unrestricted HTTPS Access Should Not Be Allowed
No security group should allow unrestricted inbound access to TCP port 443 (HTTPS).
EC2 Instances Should Not Have Blacklisted Instance Types
Your AWS account should not have any EC2 instance with the instance type blacklisted.
Unused Elastic Network Interfaces Should Be Removed
Unused AWS Elastic Network Interfaces (ENIs) should be removed to follow best practices.
Unused AMIs Should Be Removed
Unused AMIs should be removed to follow best practices.
Unused AWS EC2 Key Pairs Should Be Removed
Unused AWS EC2 key pairs should be decommissioned to follow best practices.
Reserved Instances Should Not Be Unused
AWS EC2 Reserved Instances should be fully utilized.
EC2 Instances Should Not Be Overutilized
Overutilized EC2 instances should be upgraded to optimize application response time.
EC2 Instances Should Not Be Idle
Idle AWS EC2 instances should be stopped or terminated in order to optimize AWS costs.
EC2 Instances Should Not Be Underutilized
Underutilized EC2 instances should be downsized in order to optimize your AWS costs.
EC2 Instance Tenancy
EC2 instances should have the required tenancy for security and regulatory compliance requirements.
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedCLOUDANIX
Insights from Cloudanix
Explore guides, checklists, and blogs that simplify cloud security and help you secure your infrastructure.
Case Studies
Real-world success stories where Cloudanix helped organizations secure their cloud infrastructure. Watch how we made a d...
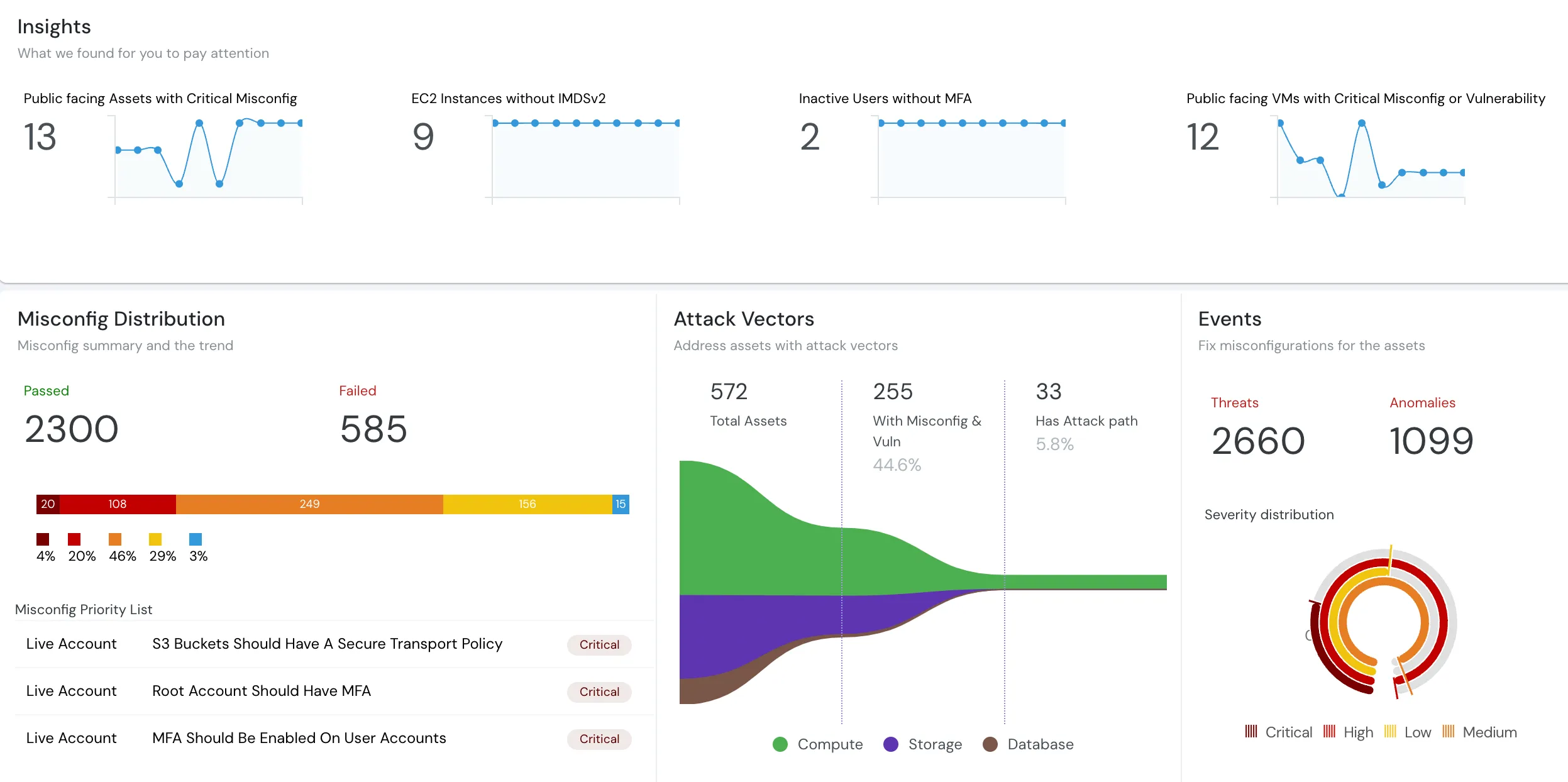
What is CSPM?
Understand what Cloud Security Posture Management (CSPM) is and how it automates security and compliance across cloud en...
CASB, CSPM, SIEM: Cloud Security Essentials
Understand how CASB, CSPM, and SIEM work together to enhance your cloud security posture and ensure better governance.
What is Cloud Audit?
In-depth assessment of cloud environment for security, compliance, and optimization. Identify vulnerabilities, ensure da...
Top 10 Challenges of CSPM
Cloud environments are getting more complex and dynamic day by day, making it difficult to gain complete visibility into...
Cloudanix docs
Cloudanix offers you a single dashboard to secure your workloads. Learn how to set up Cloudanix for your cloud platform ...
Changelog
A complete history of changes, improvements, and fixes for Cloudanix. Subscribe to get notified about the latest updates...
