Back to Changelog
new release July 3, 2023
Security Context, Attack Path, Bulk Review, Remediation Your Way
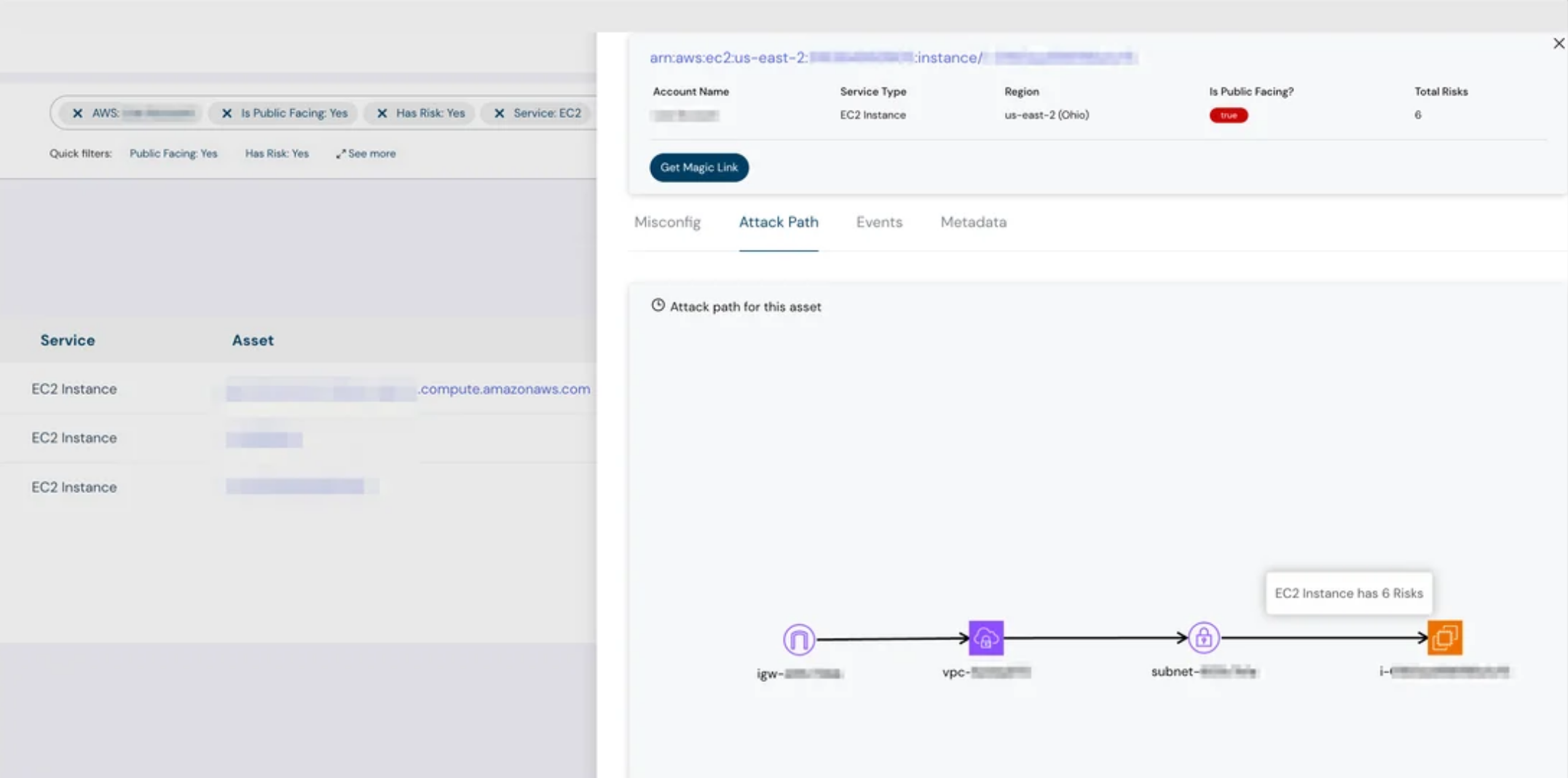
Attack Path for Compute & Database Resources
- Visually understand the relationships and risks affecting your compute and database resources.
- Correlates image vulnerabilities running in containers, helping you save productive time.
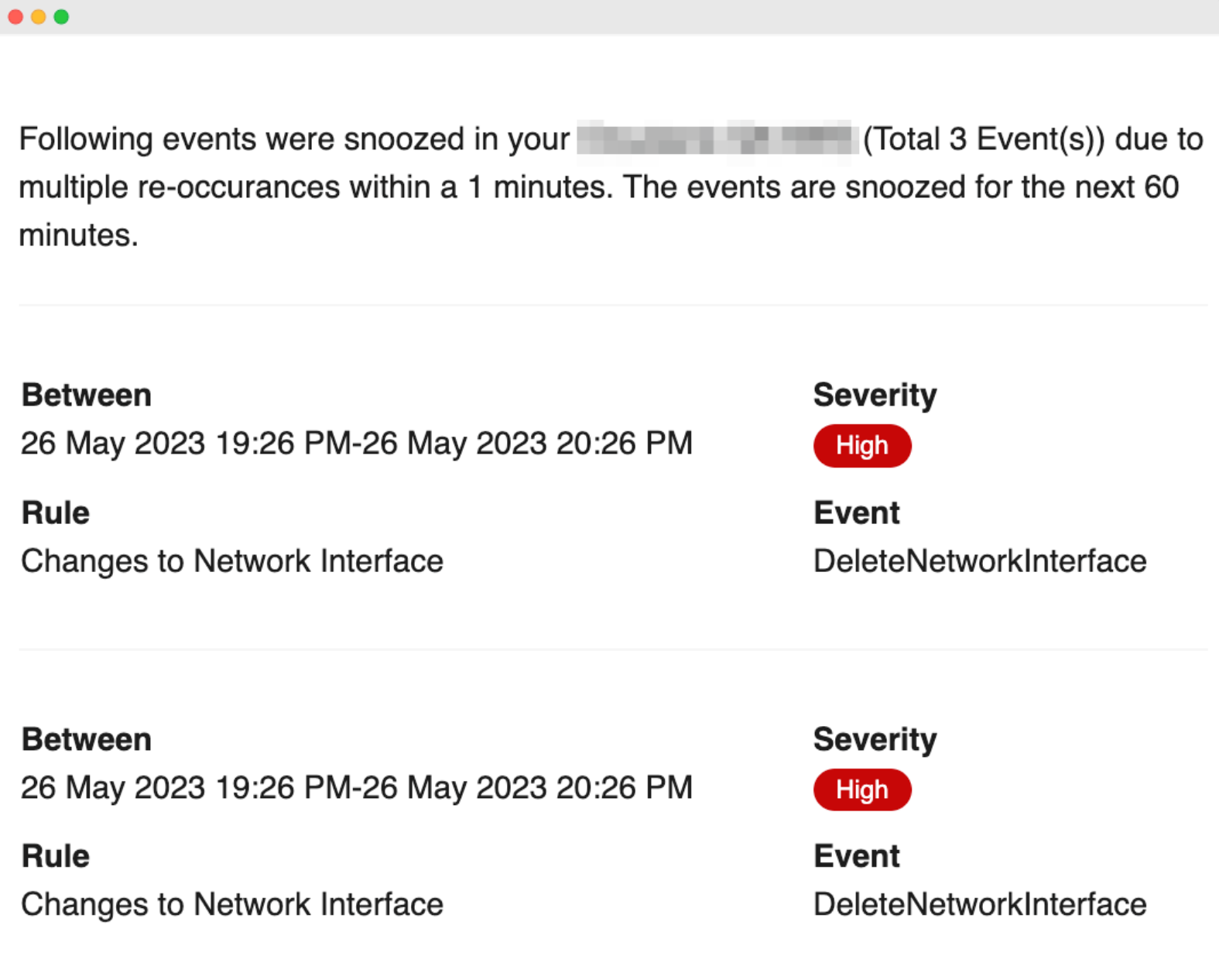
Event Auto-Snooze
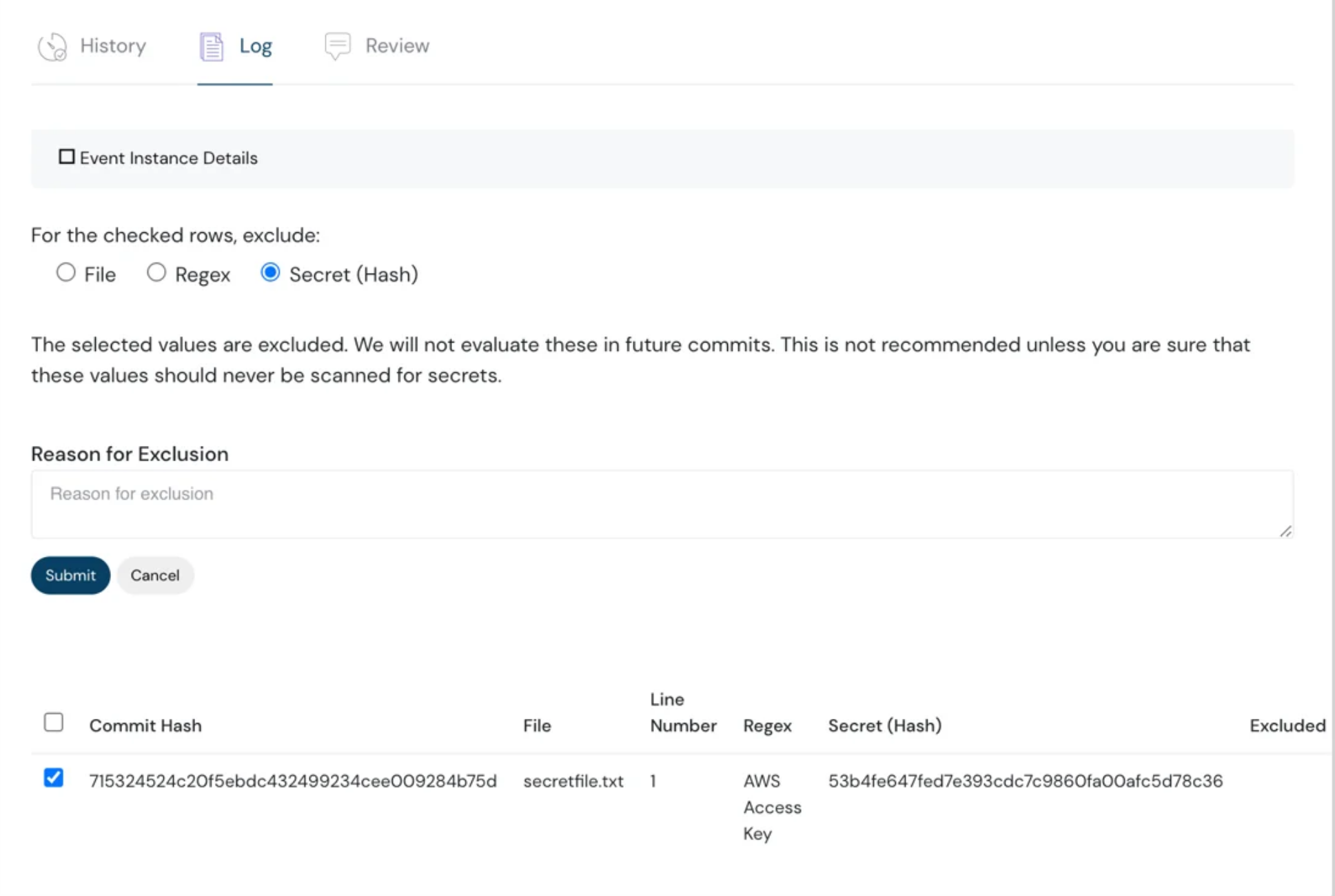
- Flexible identification and management of secrets within files or code repositories.
- Allows tailoring of the secret scanning process to match your organization’s needs.
Secret Scanning Capability
- Scan full repositories for secrets in both GitHub and Bitbucket.
- Detects and manages sensitive information before it can be exploited.
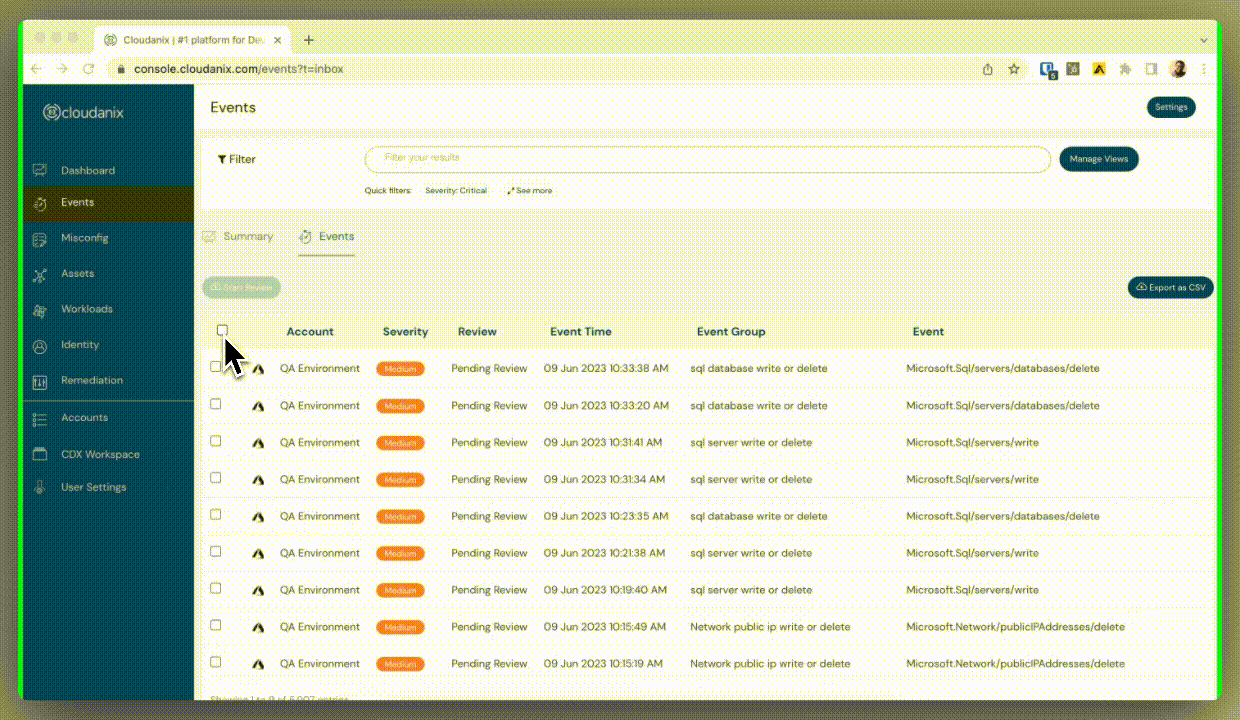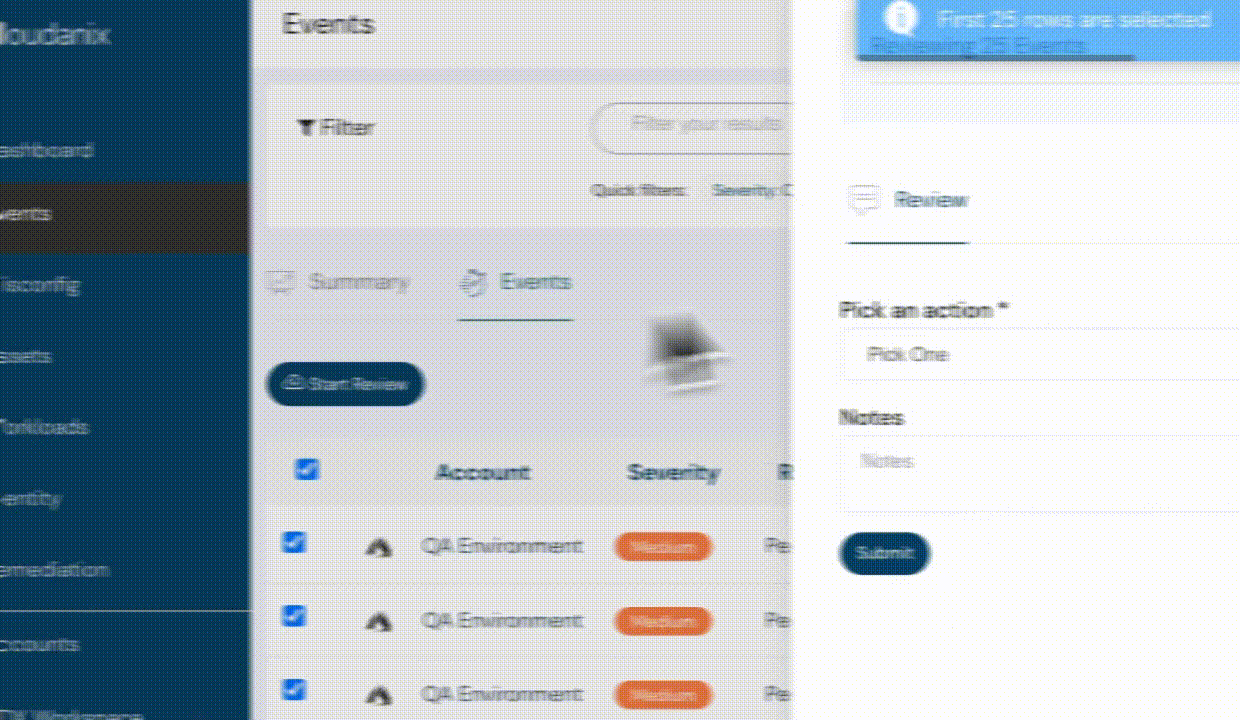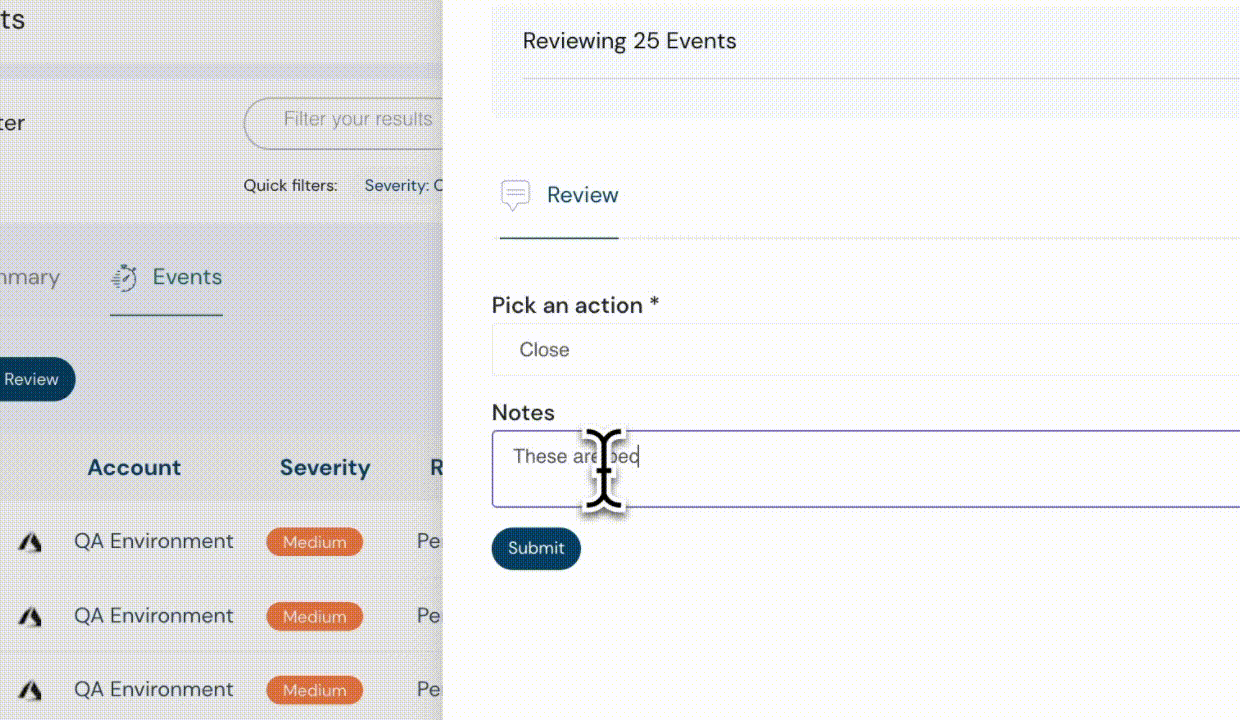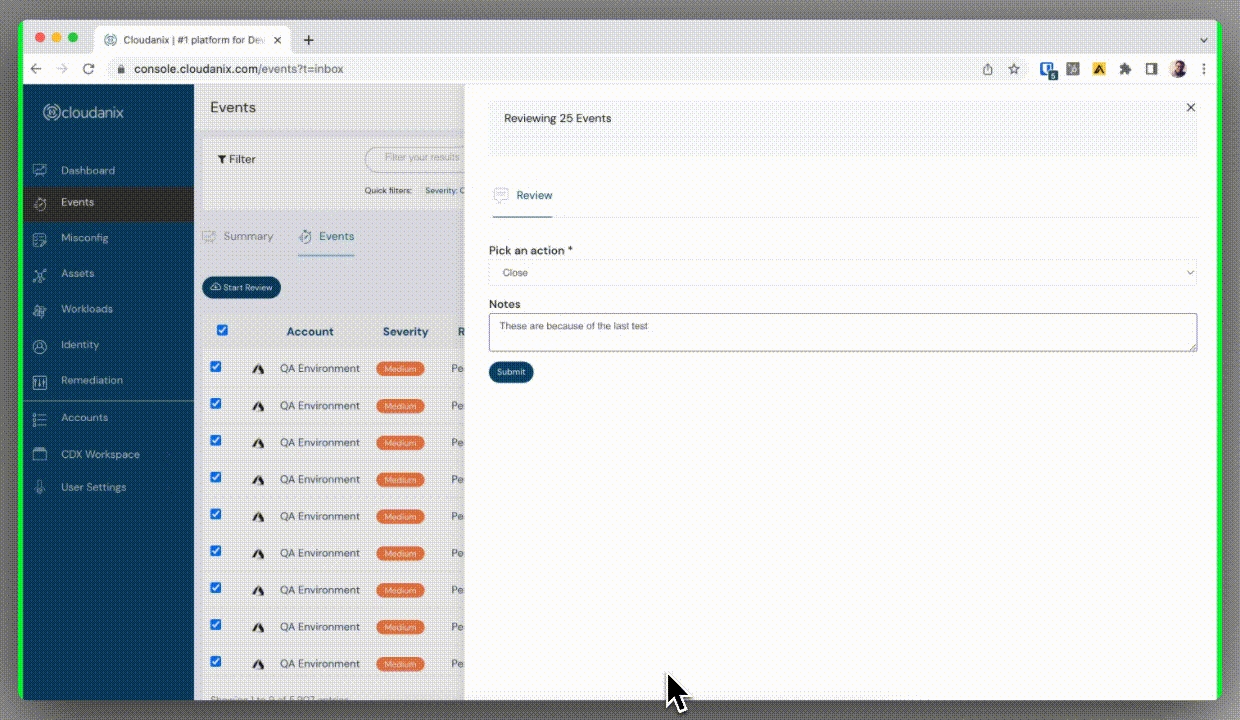
Bulk Event Review & Remediation
- Manage multiple events with a single action instead of updating each individually.
- Ideal for applying consistent changes across large numbers of events, reducing fatigue and saving time.
IAM Event Support for Azure
- Now includes additional event monitoring such as:
- Permissions updated for service accounts
- User MFA changes
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedBlog
Read More Posts
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Wednesday, Nov 05, 2025
From Static to Strategic: Modernizing Privileged Access for Cloud Infrastructure
The promise of the cloud – agility, scalability, and innovation – has revolutionized how enterprises operate. Cloud infr
Read MoreTuesday, Sep 30, 2025
Eliminate Standing Access: Introducing JIT Kubernetes for Azure AKS Security
The Security Mandate: Why Permanent Access Fails Mission-Critical AKS Kubernetes has become the operating system of
Read MoreFriday, Aug 08, 2025
User Access Review in Cloud Security: A Foundational Guide to Securing Your Cloud Environment
Introduction: The Unseen Gatekeepers of Cloud Security In the rapidly expanding landscape of cloud computing, organi
Read More