Strategic Access: Minimizing Risk and Maximizing Efficiency with Just-in-Time IAM
Excessive user and service privileges create a significant attack surface, risking costly data breaches and compliance failures. This over-permissioning, often unintentional, leads to a broad window of vulnerability, impacting financial stability and reputational integrity.
Just-in-Time (JIT) IAM strategically minimizes these risks by granting temporary, precise access only when required. This approach enhances operational efficiency by streamlining access workflows, reducing administrative burdens, and ensuring that access is always aligned with immediate business needs.
Implementing JIT is not merely tactical; it's foundational to a resilient security posture. By enforcing the principle of least privilege dynamically, JIT limits the potential damage from both internal and external threats, ensuring that security is proactive, not reactive, and fundamentally sound.
What are the business risks associated with over-provisioned access?
The repercussions of over-privileged access extend far beyond mere technical vulnerabilities, directly impacting an organization's financial stability and reputational integrity. Data breaches stemming from excessive privileges trigger a cascade of financial penalties and erode the trust that forms the bedrock of customer and partner relationships. Understanding these impacts is crucial for executives to grasp the urgency of implementing robust access controls.
Financial impacts of data breaches due to excessive privileges
- Direct breach costs: Excessive privileges allow attackers to access and exfiltrate large volumes of sensitive data, leading to substantial direct costs, including forensic investigations, legal fees, and regulatory fines. Immediate and significant financial drain, directly impacting the bottom line.
- Business disruption and downtime: Breaches caused by over-privileged access can disrupt critical business operations, leading to extended downtime, lost productivity, and revenue loss. Revenue loss and increased operational expenses due to service interruptions.
- Increased cybersecurity insurance premiums: Following a data breach attributed to excessive privileges, insurance providers often increase premiums or deny coverage due to heightened risk. Long-term increase in operational costs related to insurance.
- Legal settlements and regulatory fines: Breaches resulting from inadequate access controls can lead to costly legal settlements and regulatory fines, especially under stringent regulations like GDPR and HIPAA. Significant financial penalties and legal expenses can severely impact profitability.
Reputational impacts of data breaches due to excessive privileges
- Loss of customer trust: Customers lose trust when their sensitive data is compromised due to inadequate access controls, leading to customer attrition and decreased loyalty. Long-term damage to customer relationships and brand loyalty.
- Damage to brand reputation: Data breaches attributed to excessive privileges can severely damage a company's brand reputation, impacting its ability to attract and retain customers and partners. Negative publicity and erosion of brand value can affect market position.
- Regulatory scrutiny and public criticism: Breaches caused by over-privileged access often attract intense regulatory scrutiny and public criticism, leading to investigations and potential penalties. Increased regulatory oversight and negative public perception are impacting investor confidence.
- Loss of competitive advantage: Companies that suffer data breaches due to excessive privileges may lose competitive advantage as customers and partners opt for more secure alternatives. Erosion of market share and loss of strategic partnerships.
By implementing Just-in-Time IAM, organizations can proactively mitigate these severe financial and reputational risks. The strategic shift towards granular, temporary access not only minimizes the potential for breaches but also reinforces a commitment to data security. This approach safeguards the bottom line and preserves the organization's reputation, demonstrating a proactive stance in protecting vital assets and stakeholder trust.
How does over-provisioning hinder compliance with regulatory requirements?
Over-provisioning directly conflicts with stringent regulatory mandates like GDPR, HIPAA, and PCI DSS, which demand "least privilege" access. Excessive permissions grant unauthorized users potential access to sensitive data, violating data protection principles. Audit trails become muddled, hindering compliance demonstrations. Regulators penalize uncontrolled data access, viewing it as negligence. JIT addresses this by enforcing temporary, role-based access, creating clear audit logs. This minimizes the risk of non-compliance, demonstrating proactive data security measures and simplifying regulatory reporting, thereby avoiding hefty penalties and maintaining stakeholder trust.
How JIT addresses these risks by limiting the window of opportunity for malicious activity?
JIT minimizes the window of opportunity by granting precise, time-limited privileges only when needed. This eliminates persistent, excessive access that attackers exploit. If a malicious actor gains access, their potential impact is severely limited by the temporary nature of the granted permissions. Automatic revocation ensures privileges vanish after the task, preventing prolonged access and lateral movement. This proactive approach significantly reduces the timeframe for exploitation, effectively neutralizing the risk of long-term damage from compromised accounts.
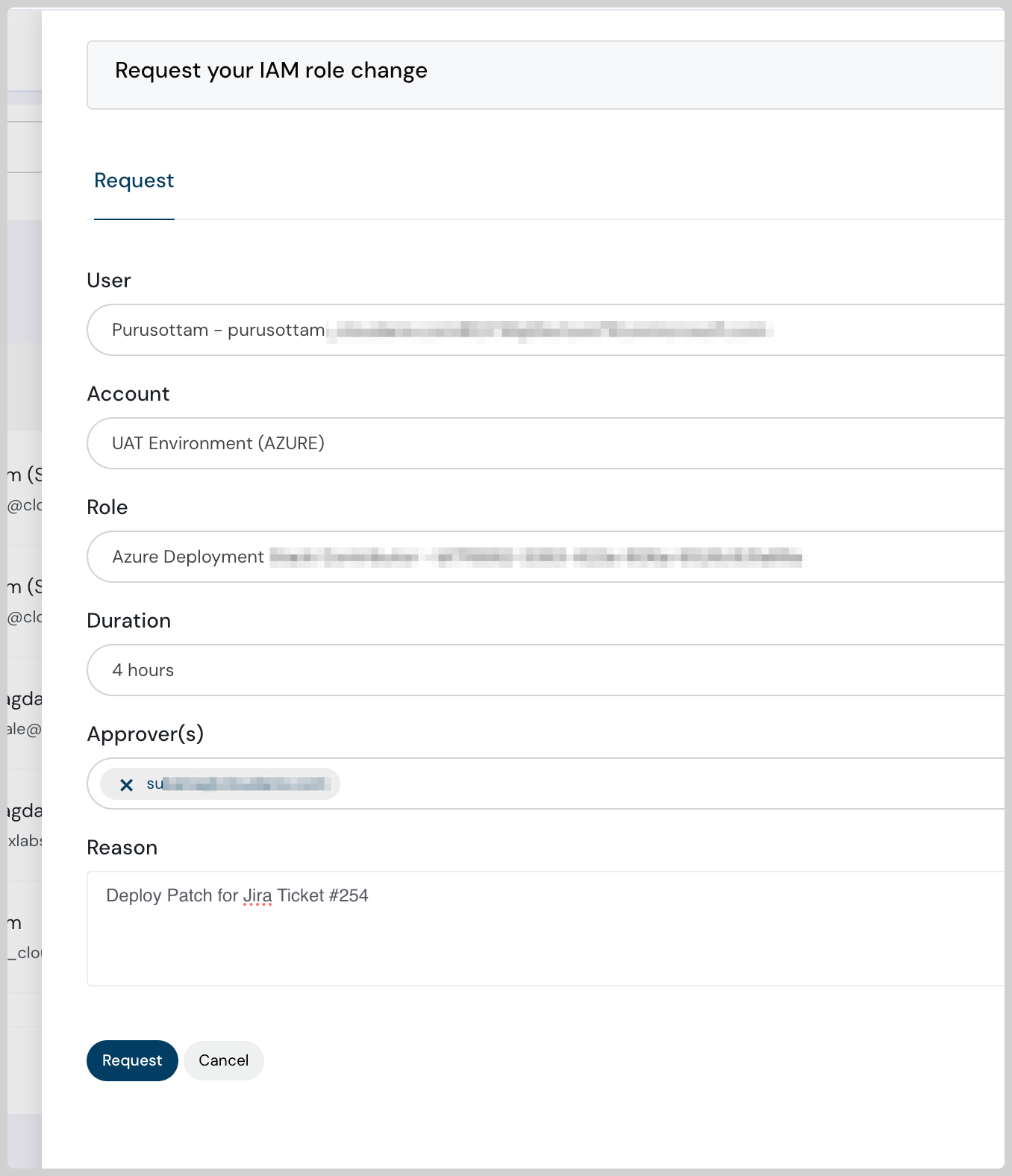
How can JIT grant temporary, scoped privileges only when needed?
JIT operates on the principle of "least privilege, just in time." Instead of granting users or services persistent, broad access, it provides them with the minimum necessary privileges for a specific task and a limited duration. This is achieved through a workflow that typically involves the following steps:
- Request Initiation: A user or service requiring elevated privileges initiates a request. This request specifies the resources they need to access and the actions they intend to perform. This request often needs to be approved by a designated approver.
- Policy evaluation and approval: The JIT system evaluates the request against predefined policies and rules. These policies dictate who can request what privileges, under what circumstances, and for how long. Depending on the sensitivity of the request and the organization's policies, it may require manual approval from an authorized individual or automated approval based on predefined criteria.
- Temporary privilege granting: Upon approval, the JIT system grants the requested privileges for a specific, pre-determined timeframe. This could be minutes, hours, or even days, depending on the task's requirements. The system creates temporary credentials or modifies access control lists (ACLs) to provide the necessary access.
- Scoped access: The granted privileges are "scoped," meaning they are limited to the specific resources and actions required for the task. This ensures that users or services cannot perform unauthorized actions or access unrelated data. For example, a developer might be granted temporary access to a specific database table for a particular query, but not to the entire database.
- Automatic privilege revocation: Once the specified timeframe expires, the JIT system automatically revokes the granted privileges. This ensures that access is not inadvertently left open, minimizing the window of opportunity for malicious activity. The system may also revoke privileges upon completion of the task, if explicitly requested.
- Audit logging: The JIT system logs all access requests, approvals, and privilege grants and revocations. This provides a comprehensive audit trail, which is essential for compliance and security investigations. This logging provides proof of access and allows for the security team to investigate any anomalous behavior.
By implementing this workflow, JIT ensures that users and services only have the necessary privileges for the duration of their task, significantly reducing the risk of unauthorized access and data breaches.
What is the role of automation in streamlining the access requests and revocations?
Automation is pivotal in JIT IAM, streamlining access requests and revocations. Automated workflows eliminate manual intervention, reducing human error and accelerating response time. Users initiate requests through self-service portals or APIs, triggering automated policy evaluations and approvals. System-driven privilege grants and revocations ensure timely access and automatic expiration. This automation extends to audit logging, providing real-time visibility and simplifying compliance. By automating these processes, JIT enhances operational efficiency and strengthens security posture, ensuring access is both agile and secure.
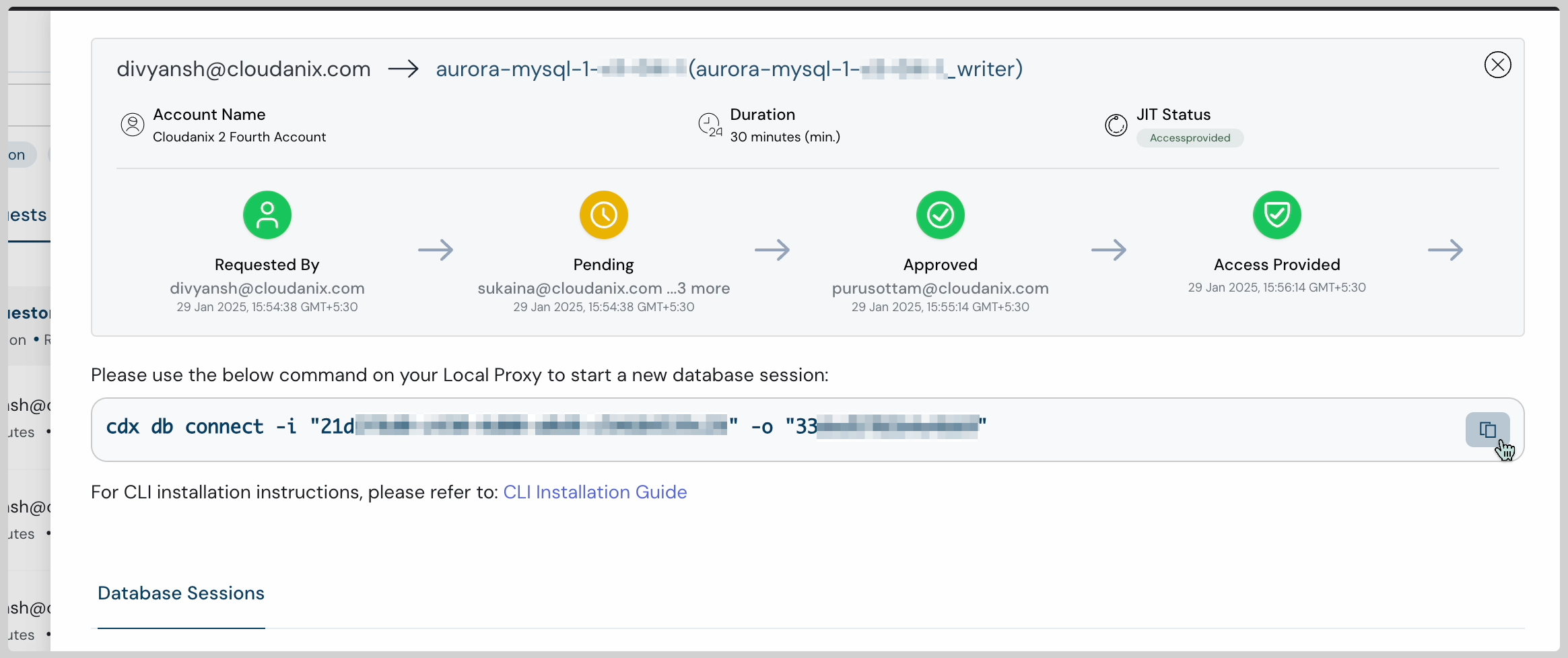
What are the key benefits for the executive suite?
For the executive suite, the adoption of Just-in-Time (JIT) IAM transcends mere technical implementation, delivering strategic advantages that directly impact the organization's bottom line and long-term viability. From quantifiable risk mitigation to enhanced compliance and operational agility, JIT offers a compelling value proposition that aligns with core business objectives.
- Quantifiable risk mitigation: JIT significantly reduces the attack surface by limiting persistent privileges, thereby minimizing the potential impact of data breaches. Executives can see a direct correlation between JIT implementation and a reduction in security incidents, leading to lower financial losses and reputational damage. Teams benefit from demonstrable reduction in exposure and vulnerability, translating to tangible financial protection.
- Enhanced compliance and reduced regulatory burden: JIT's granular access controls and comprehensive audit trails simplify compliance with stringent regulations like GDPR, HIPAA, and PCI DSS. This reduces the risk of costly fines and legal battles, freeing up resources for core business activities. Teams benefit from streamlined compliance reporting and reduced regulatory risk, improving overall governance.
- Temporary privilege granting: Upon approval, the JIT system grants the requested privileges for a specific, pre-determined timeframe. This could be minutes, hours, or even days, depending on the task's requirements. The system creates temporary credentials or modifies access control lists (ACLs) to provide the necessary access.
- Increased operational efficiency and agility: Automated access workflows and self-service portals empower employees to quickly obtain necessary privileges, minimizing downtime and delays. This agility enables faster response to business needs and supports rapid innovation. Faster operational workflows, reduced administrative overhead, and improved business responsiveness.
- Cost savings through prevention: By proactively preventing data breaches and compliance failures, JIT avoids substantial financial losses associated with incident response, legal settlements, and regulatory penalties. This translates to significant cost savings and improved financial stability.
By embracing JIT IAM, executives can drive a paradigm shift in access management, transforming it from a reactive necessity to a proactive strategic asset. The measurable benefits, including reduced financial exposure, streamlined compliance, and enhanced operational efficiency, position JIT as a critical investment in the organization's security and resilience. Ultimately, JIT empowers executives to build a culture of security that fosters trust, drives innovation, and safeguards the organization's future.
Case studies: Real-world impact
To illustrate the tangible benefits of Just-in-Time (JIT) IAM, these anonymized case studies showcase real-world scenarios where organizations have achieved significant improvements in security and compliance. By focusing on quantifiable results, these examples demonstrate the strategic advantage of proactive access management.
Case Study 1: Global Financial Institution
Challenge: The institution faced frequent regulatory audits due to excessive privileged access, leading to high compliance costs and potential fines. They also experienced several minor security incidents due to compromised service accounts with long-lived credentials.
JIT Implementation: Implemented JIT for privileged access to sensitive financial databases and critical applications. Automated temporary privilege grants for administrators and service accounts, with strict audit logging.
The following were the results after implementation of IAM JIT
- Reduced compliance audit findings by 70% within the first year.
- Decreased security incident response time by 50% due to clear audit trails.
- Eliminated 80% of long-lived service account credentials.
Case Study 2: Large E-commerce Company
Challenge: A company's Data Science team members had broad, persistent access to production environments, leading to concerns about potential data breaches. Like most of the data teams needs access to data, this company's data team also wanted access.
JIT Implementation: Integrated JIT to grant temporary, scoped access for databases.
The following were the quantifiable results after implementation of JIT
- Data science and support teams now get time-bound access to databases
- All their query activity is logged for audit and compliance
- Data leakages threat is minimized
Case study 3: Healthcare Provider Network
Challenge: The network struggled to maintain compliance with HIPAA regulations due to uncontrolled access to patient data. They also faced challenges in managing emergency access during critical incidents.
JIT Implementation: Implemented JIT for access to patient records, with strict role-based access controls. Established a JIT-based emergency access workflow, allowing authorized personnel to request and receive temporary, highly privileged access with full audit logging.
The following were the quantifiable results after implementation of JIT
- Improved HIPAA compliance scores by 85%
- Reduced emergency access response time by 60%
- Reduced unauthorized patient data access incidents by 95%
These case studies underscore the transformative impact of JIT IAM. By adopting a strategic approach to access management, organizations can achieve measurable improvements in risk mitigation, compliance, and operational efficiency. The quantifiable results highlight the value of JIT as a critical component of a robust security strategy, enabling organizations to protect their valuable assets and maintain stakeholder trust.
The future of IAM: Embracing JIT as a core principle
The evolving threat landscape, characterized by sophisticated cyberattacks and insider threats, necessitates a paradigm shift in IAM practices. Persistent, broad access privileges are increasingly untenable.
Just-in-Time (JIT) IAM emerges as a critical defense, minimizing the window of vulnerability by granting temporary, scoped access. As threats become more dynamic, continuous improvement and adaptation of IAM strategies are essential. Organizations must embrace automation and real-time monitoring to stay ahead of evolving attack vectors. Implementing JIT is not merely a tactical adjustment but a strategic investment in long-term security and resilience.
By proactively limiting access and enforcing least privilege, organizations can significantly reduce the impact of potential breaches. This approach enhances compliance, builds stakeholder trust, and ensures that security practices remain agile and effective in the face of ever-changing threats.
Conclusion
Just-in-Time (JIT) IAM offers a strategic solution to mitigate risks associated with over-provisioned access. By granting temporary, precise privileges, JIT minimizes the attack surface, enhances compliance, and improves operational efficiency. Embracing JIT is a proactive investment in long-term security, enabling organizations to safeguard assets and build stakeholder trust in an evolving threat landscape.
Know more about
- Integrate Just In Time (JIT) Access with AWS Identity Center
- Elevate your Security with IAM Just-In-Time (JIT) Access
- What is IAM JIT?