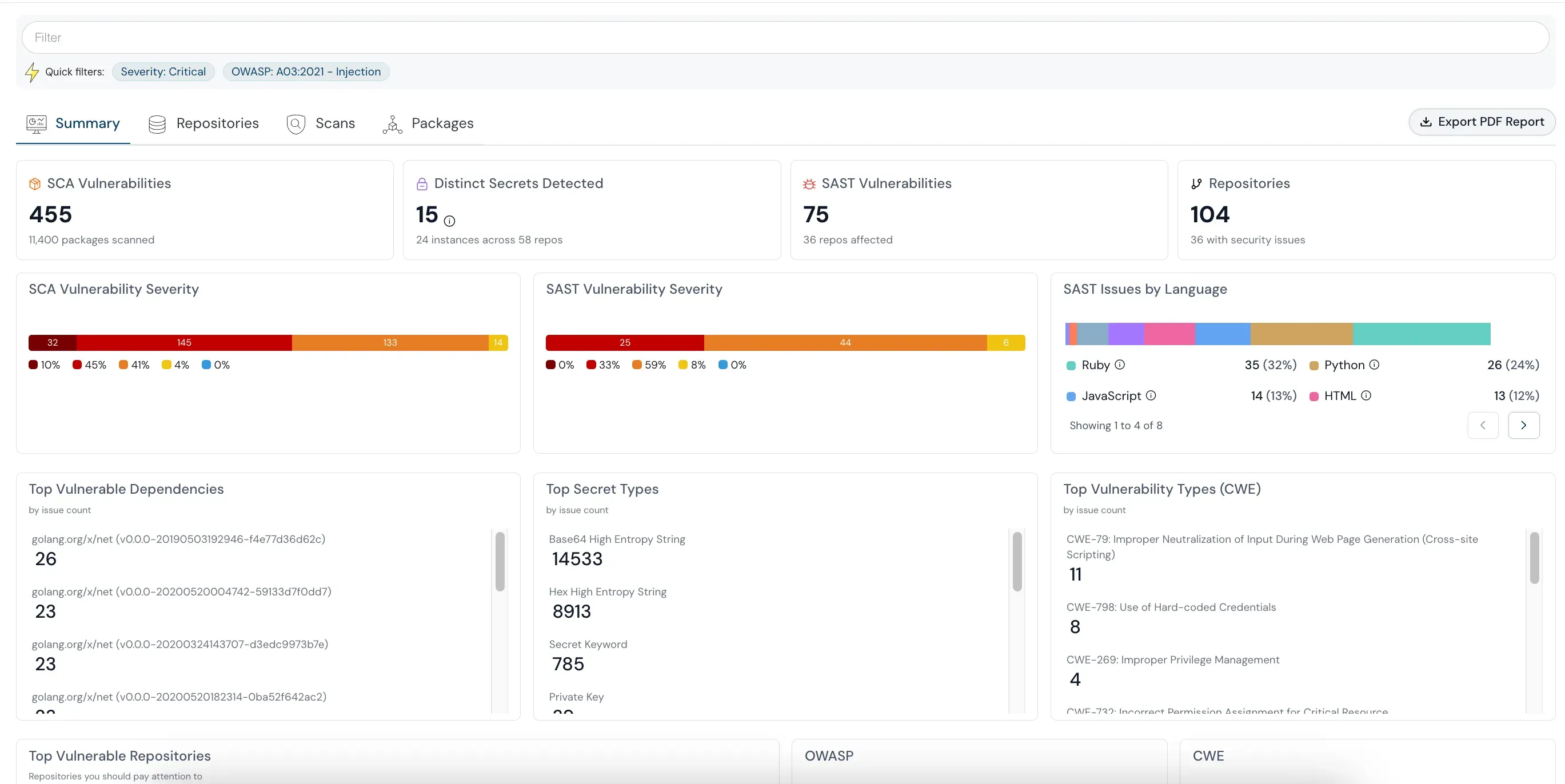
Understanding NIS2 Directive Requirements
NIS2 Directive establishes comprehensive cybersecurity requirements for essential and important entities across 18 sectors including energy, transport, banking, health, digital infrastructure, and public administration. The directive mandates risk-based cybersecurity measures, incident notification within 24 hours, and supply chain security management.
Organizations using cloud infrastructure from AWS, Azure, GCP, or OCI must implement appropriate technical and organizational measures to manage cybersecurity risks. NIS2 emphasizes the security of network and information systems, with potential fines up to €10 million or 2% of global annual turnover for non-compliance.
Just-In-Time Access for NIS2 Access Control Requirements
NIS2 Article 21 requires entities to implement access control policies and procedures to manage access to network and information systems. Cloudanix's Just-In-Time (JIT) access provides time-bound, temporary privileged access across AWS, Azure, GCP, and OCI environments.
JIT access supports NIS2's requirements for limiting access rights, managing privileged accounts, implementing authentication policies, and maintaining audit trails of access activities. Zero-standing-privileges approach minimizes the risk of unauthorized access and insider threats, both critical concerns under NIS2's risk management framework.
Database Activity Monitoring (DAM) for NIS2 Incident Detection
NIS2 requires organizations to detect, prevent, and respond to cyber threats and incidents. Article 21 mandates implementation of policies for monitoring, auditing, and logging to detect cybersecurity incidents affecting network and information systems.
Cloudanix's DAM solution provides real-time monitoring of database access across AWS RDS, Azure SQL, Google Cloud SQL, and Oracle Cloud databases. DAM detects anomalous database activities, identifies potential security incidents, maintains comprehensive audit logs, and provides alerts that support NIS2's 24-hour incident notification requirement.
Comprehensive Identity Management for NIS2 Compliance
NIS2 requires robust identity and access management controls covering both human users and automated systems. Modern cloud environments include thousands of identities including administrators, developers, service accounts, API keys, workload identities, and third-party integrations across AWS, Azure, GCP, and OCI.
Cloudanix provides identity governance that monitors all identity types, detects excessive permissions, enforces least-privilege access, manages cloud service accounts and API keys, and tracks access patterns. This comprehensive approach helps organizations meet NIS2's requirements for access control, authentication, and accountability.
Cloud Security Configuration and Risk Management
NIS2 Article 21 requires entities to implement security measures based on a risk assessment approach, including policies for securing network and information systems. Cloud misconfigurations represent significant cybersecurity risks that can lead to data breaches and service disruptions.
Cloudanix continuously scans AWS, Azure, GCP, and OCI environments for security misconfigurations, implements security baseline monitoring, detects deviations from approved configurations, and provides automated or semi-automated remediation. This helps organizations maintain the secure configuration posture required by NIS2's risk-based approach.
Workload Security and Business Continuity
NIS2 requires organizations to implement security measures ensuring availability and continuity of network and information systems. Cloud workloads including containers, Kubernetes clusters, serverless functions, and virtual machines must be protected against cyber threats.
Cloudanix secures cloud workloads across AWS, Azure, GCP, and OCI through vulnerability management, runtime protection, configuration compliance, and network security monitoring. These capabilities support NIS2's requirements for system security, vulnerability handling, and business continuity planning.
Supply Chain Security and SBOM for NIS2
NIS2 Article 21 specifically addresses supply chain security, requiring organizations to assess cybersecurity risks related to suppliers and service providers. The directive emphasizes understanding and managing risks from third-party software components and dependencies.
Cloudanix generates comprehensive Software Bill of Materials (SBOMs) for cloud workloads and containerized applications. SBOM capabilities provide visibility into software components and dependencies, identify vulnerabilities in third-party code, enable risk assessment of the software supply chain, and support NIS2's requirements for managing supply chain cybersecurity risks across cloud environments.