Data Security Platform
Unified Data Security Across Your Cloud Environment
In today's cloud-native world, your data flows everywhere—from code repositories to databases, storage buckets to runtime workloads. Traditional point solutions can't keep up. Cloudanix delivers comprehensive data security by unifying CSPM, DAM, JIT access, and CNAPP capabilities into a single platform that protects your most valuable asset: your data.
Trusted by over 100+ customers worldwide
Cloudanix
Complete Data Security Through Unified Platform Capabilities
Data security isn't just about one tool or one layer of defense. Cloudanix brings together multiple security capabilities to ensure your data remains protected throughout its entire lifecycle—from development to production, from storage to access.
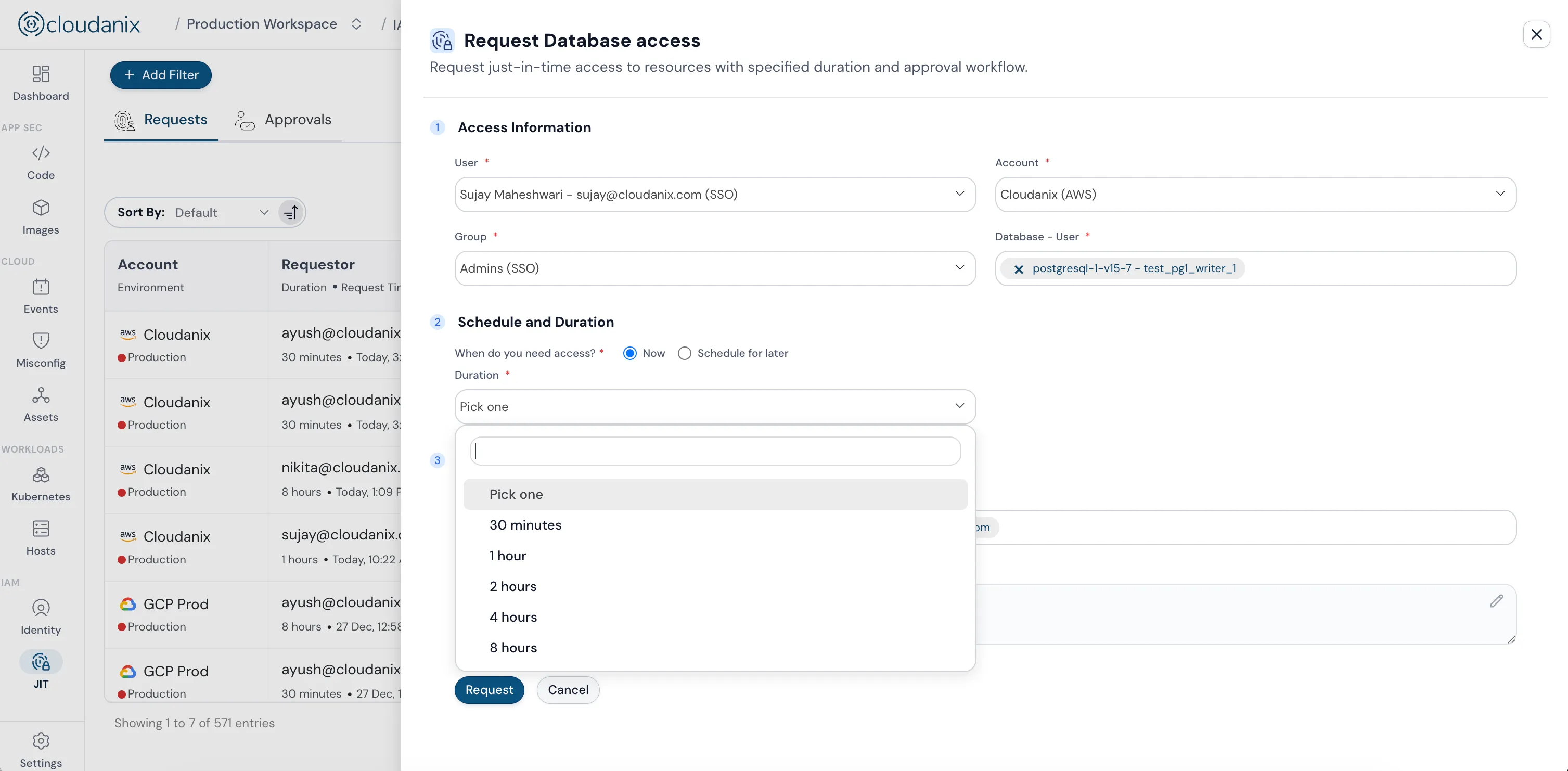
Database Activity Monitoring (DAM) with JIT Access
Your databases contain your most sensitive data. Cloudanix DAM continuously monitors database access patterns, queries, and administrative activities to detect suspicious behavior in real-time. Combined with Just-In-Time (JIT) access controls, you can ensure that database access is granted only when needed and automatically revoked when sessions expire. This eliminates standing privileges that create persistent security risks. Monitor privileged user activities, detect SQL injection attempts, track data exfiltration, and maintain comprehensive audit trails for compliance requirements like SOC 2, HIPAA, and GDPR.
Explore JIT Database Access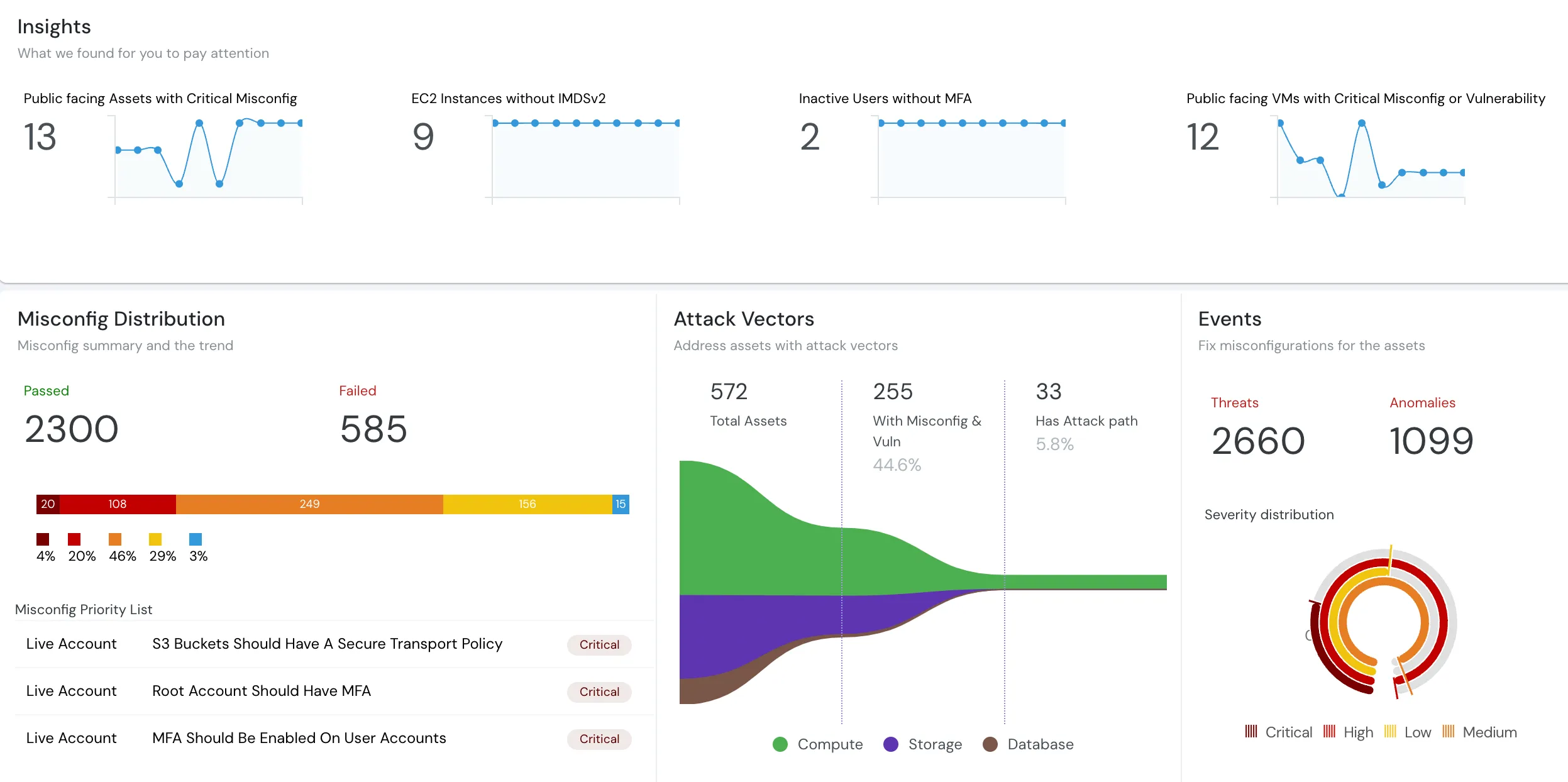
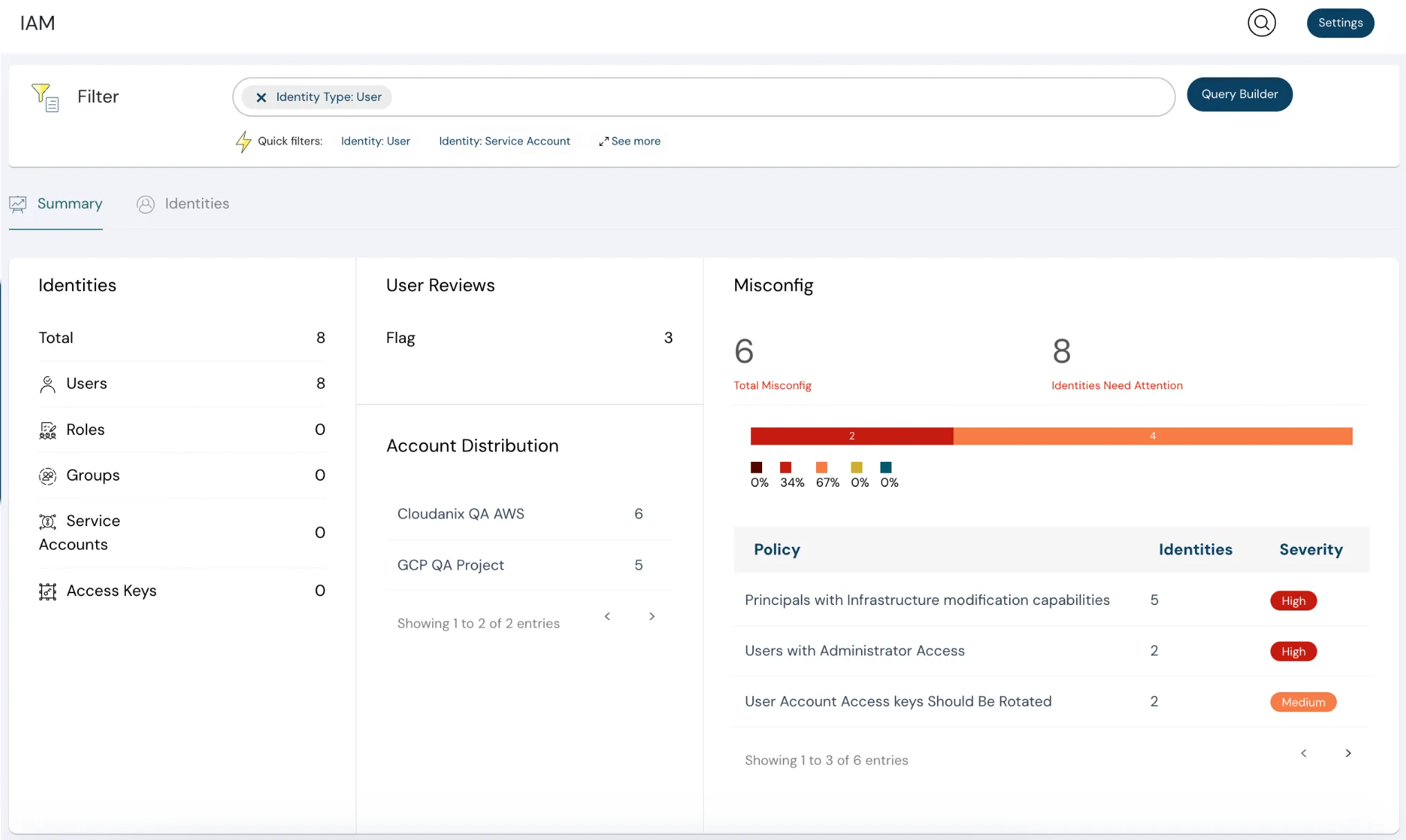
Cloud Security Posture Management (CSPM) for Data Protection
Misconfigurations are the leading cause of data breaches in cloud environments. Cloudanix CSPM continuously scans your cloud infrastructure to identify risky configurations that could expose your data. Detect publicly accessible S3 buckets, misconfigured database instances, unencrypted storage volumes, and overly permissive access policies before they become incidents. Automated remediation helps you fix issues in one click, reducing risk exposure time from days to seconds. Maintain compliance with data protection regulations through continuous monitoring of encryption standards, access controls, and data residency requirements.
Discover CSPM Capabilities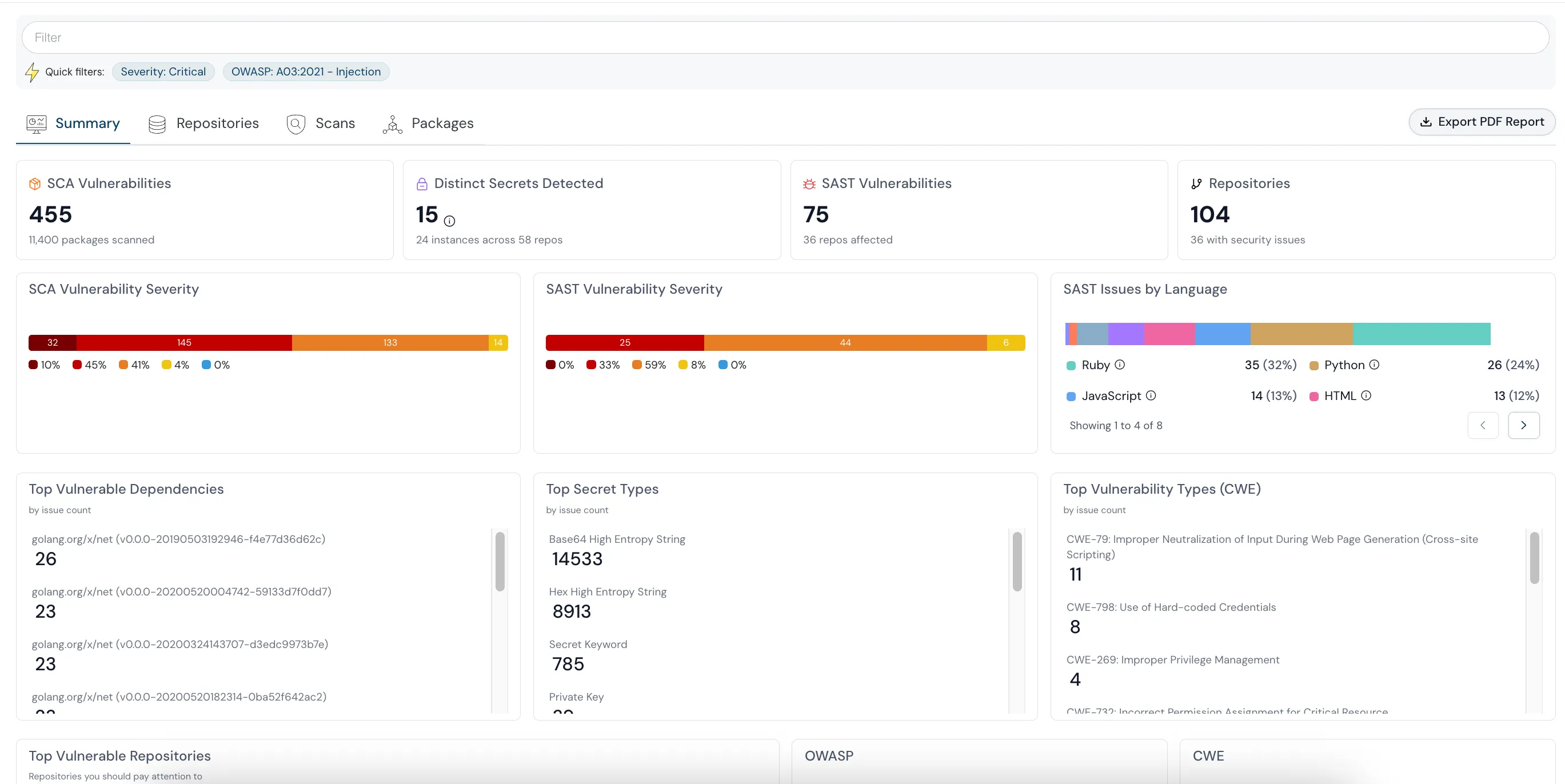
Cloud-Native Application Protection Platform (CNAPP)
Data security starts in your code. Cloudanix CNAPP correlates security findings from pull request to runtime, ensuring sensitive data is protected throughout the application lifecycle. Scan for hardcoded secrets, credentials, API keys, and PII in source code before they reach production. Detect sensitive data exposure vulnerabilities through SAST scanning integrated into your CI/CD pipeline. Connect code-level findings with runtime behavior to understand the actual risk—a vulnerability in code that handles sensitive customer data requires immediate attention, while one in unused code paths can wait.
Explore Code SecurityEverything You Need to Protect Your Data
Data Security Platform Capabilities
Cloudanix brings together the essential capabilities required for comprehensive data security in cloud-native environments.
Database Security & Monitoring
Protect your most critical data stores with continuous monitoring, activity logging, and anomaly detection for all your databases—RDS, DynamoDB, Cloud SQL, Cosmos DB, and more.
Data Discovery & Classification
Automatically discover sensitive data across your entire cloud environment. Classify data based on sensitivity levels and apply appropriate security controls automatically.
Access Governance
Manage who has access to sensitive data with least-privilege principles. JIT access ensures temporary, audited access to production data stores with automatic expiration.
Encryption Management
Ensure data is encrypted everywhere—at rest, in transit, and during processing. Monitor encryption key usage and enforce encryption policies across all data stores.
Data Loss Prevention
Prevent sensitive data from leaving your environment through unauthorized channels. Monitor data transfers, detect bulk downloads, and block suspicious exfiltration attempts.
Compliance Reporting
Generate compliance reports for GDPR, HIPAA, PCI DSS, SOC 2, and other regulations. Demonstrate data protection controls to auditors with comprehensive audit trails.
Secrets Management
Scan code repositories, configuration files, and container images for exposed secrets. Prevent credentials and API keys from being committed to version control.
Data Residency & Sovereignty
Ensure data stays in the required geographic regions to meet regulatory requirements. Monitor data replication and enforce data residency policies automatically.
Audit & Forensics
Maintain detailed audit logs of all data access and modifications. Investigate security incidents with complete forensic trails showing who accessed what data and when.
Comprehensive Protection
How Cloudanix Secures Your Data
Data security requires visibility, control, and continuous monitoring across every layer of your cloud environment. Here's how Cloudanix delivers complete data protection.
Real-Time Database Monitoring
Monitor all database activities including queries, schema changes, and access patterns. Detect anomalous behavior, privilege escalation, and potential data exfiltration attempts. Maintain detailed audit logs for compliance and forensic analysis.
Data Classification & Discovery
Automatically discover and classify sensitive data across your cloud environment—databases, storage buckets, file shares, and more. Identify PII, PHI, payment card data, and other regulated information to ensure proper protection controls are in place.
Encryption & Key Management
Verify encryption at rest and in transit across all data stores. Monitor encryption key usage, rotation policies, and access to key management services. Detect unencrypted data stores and enforce encryption standards automatically.
Just-In-Time Access Control
Eliminate standing privileges to sensitive data. Grant temporary, time-bound access to databases and data stores only when needed. Automatically revoke access when sessions expire. Maintain complete audit trails of who accessed what data and when.
Data Access Visibility
Gain complete visibility into who has access to sensitive data, how they're using it, and whether access patterns are normal. Detect unauthorized access attempts, unusual query patterns, and bulk data downloads that could indicate a breach.
Data Compliance Automation
Continuously validate compliance with data protection regulations including GDPR, HIPAA, PCI DSS, SOC 2, and more. Automated checks ensure encryption, access controls, data residency, and retention policies meet regulatory requirements.
Sensitive Data Exposure Detection
Scan code repositories, container images, and configuration files for exposed secrets, credentials, and API keys. Prevent sensitive data from being committed to version control. Alert on public exposure of private data stores.
Automated Data Security Remediation
Don't just detect data security issues—fix them automatically. One-click remediation for common data security misconfigurations. Automated playbooks enforce encryption, revoke excessive permissions, and secure publicly exposed data stores.
The Cloudanix Advantage
Why Organizations Choose Cloudanix for Data Security
Data breaches are expensive and damaging. Don't let fragmented security tools leave gaps in your data protection strategy.
Unified Platform for Complete Data Security
Stop managing multiple point solutions. Cloudanix brings together CSPM, DAM, CNAPP, and identity security in one unified platform. Correlate findings across security layers to understand the complete risk picture.
From Code to Cloud Data Protection
Secure sensitive data throughout its entire lifecycle—from code commit to production database. Detect hardcoded secrets in pull requests, monitor database access in real-time, and verify encryption policies across all storage.
Automated Compliance for Data Regulations
Meet GDPR, HIPAA, PCI DSS, SOC 2, and other data protection requirements without the manual overhead. Automated compliance checks run continuously, providing evidence for auditors and reducing compliance preparation time by 80%.
Zero Standing Privileges to Sensitive Data
Eliminate the risk of compromised credentials granting persistent access to your databases. JIT access ensures database permissions are granted only when needed and automatically expire, reducing your attack surface.
Fast Time to Value
Get comprehensive data security visibility within minutes. Cloudanix deploys in under 5 minutes with agentless scanning. Start protecting your data immediately without complex integrations or infrastructure changes.
Built for Cloud-Native Environments
Traditional data security tools weren't designed for cloud-native architectures. Cloudanix was built from the ground up for AWS, Azure, GCP, and Kubernetes—providing native integration with cloud-native data stores.
Actionable Intelligence, Not Just Alerts
Every security team is overwhelmed with alerts. Cloudanix prioritizes data security findings based on actual risk—considering data sensitivity, exposure level, and exploitability. Focus on what matters most.
Developer-Friendly Security
Security shouldn't slow down development. Cloudanix integrates seamlessly into developer workflows—GitHub, GitLab, Bitbucket, CI/CD pipelines—providing actionable feedback without friction.
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedYour questions answered.
Frequently Asked Questions
Everything you need to know about Cloud Security Posture Management (CSPM) — its role, value, and why modern cloud-native environments can't live without it.
CLOUDANIX
Insights from Cloudanix
Explore comprehensive resources to understand CNAPP and cloud-native security best practices.
Case Studies
Discover how organizations leverage Cloudanix CNAPP to secure their cloud-native applications and achieve compliance acr...
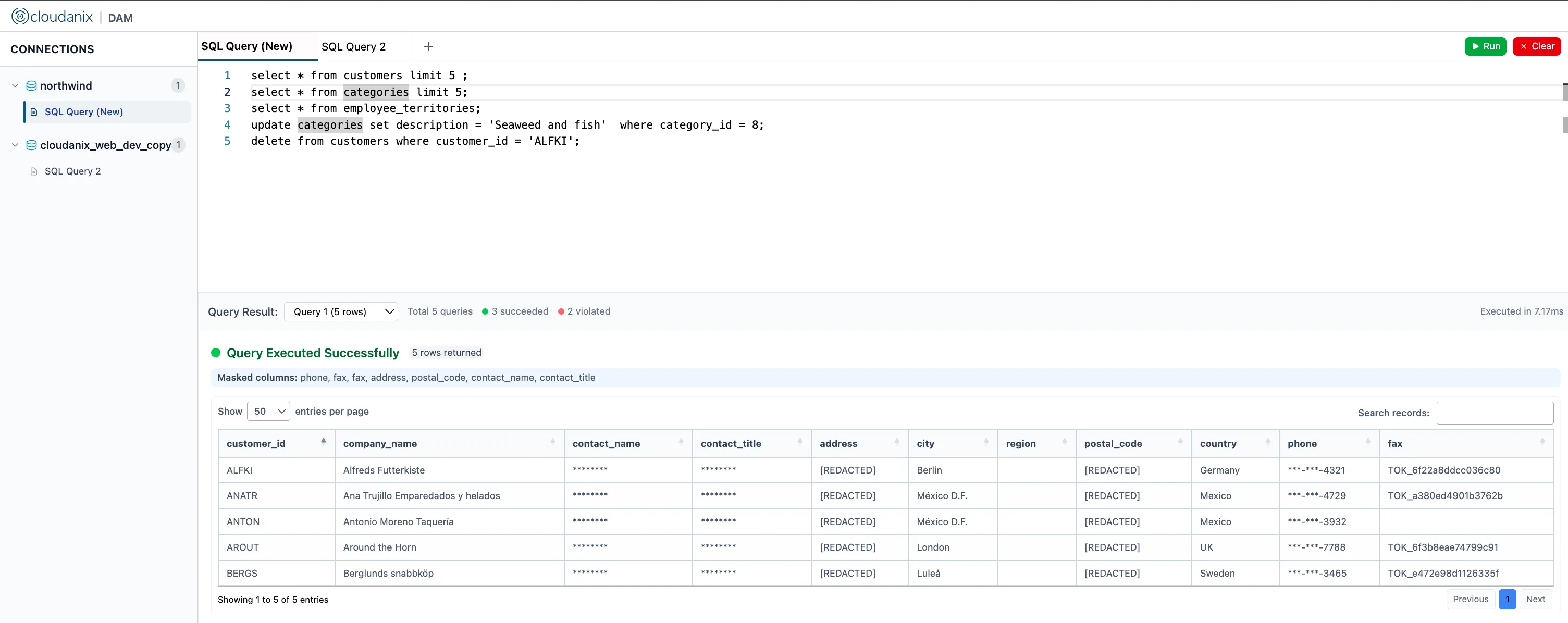
What is Database Activity Monitoring?
Learn how Database Activity Monitoring provides real-time visibility, detects insider threats, and creates an immutable ...
Understanding Code-to-Cloud Security
Explore how modern security practices span the entire application lifecycle, from source code through runtime, and why a...
Cloudanix Documentation
Get started with Cloudanix CNAPP. Learn how to connect your cloud accounts, configure policies, and leverage the platfor...
Product Changelog
Stay updated with the latest features, improvements, and capabilities added to the Cloudanix CNAPP platform.
