CLOUDANIX DAM
Database Activity Monitoring with Zero-Trust Data Access
Transform your database security posture with a revolutionary approach to Database Activity Monitoring that keeps your sensitive data within your infrastructure while delivering enterprise-grade protection, compliance, and governance. Our DAM solution combines preventive security controls, real-time monitoring, and intelligent access management in a unique architecture that ensures your data never leaves your cloud environment—giving you complete sovereignty while maintaining comprehensive visibility and control.
Privacy-First Architecture with Complete Data Sovereignty
Traditional DAM solutions force an impossible choice: comprehensive monitoring that requires data exposure to third-party infrastructure, or maintaining data sovereignty with limited visibility. Cloudanix DAM eliminates this trade-off with a browser-based secure IDE that runs entirely within your infrastructure. Your sensitive data never leaves your cloud environment, ensuring 100% data sovereignty while maintaining enterprise-grade monitoring and control. With built-in Just-In-Time access and optional integration with our CNAPP solution, you get complete visibility from code to cloud in a single dashboard.
See How It Works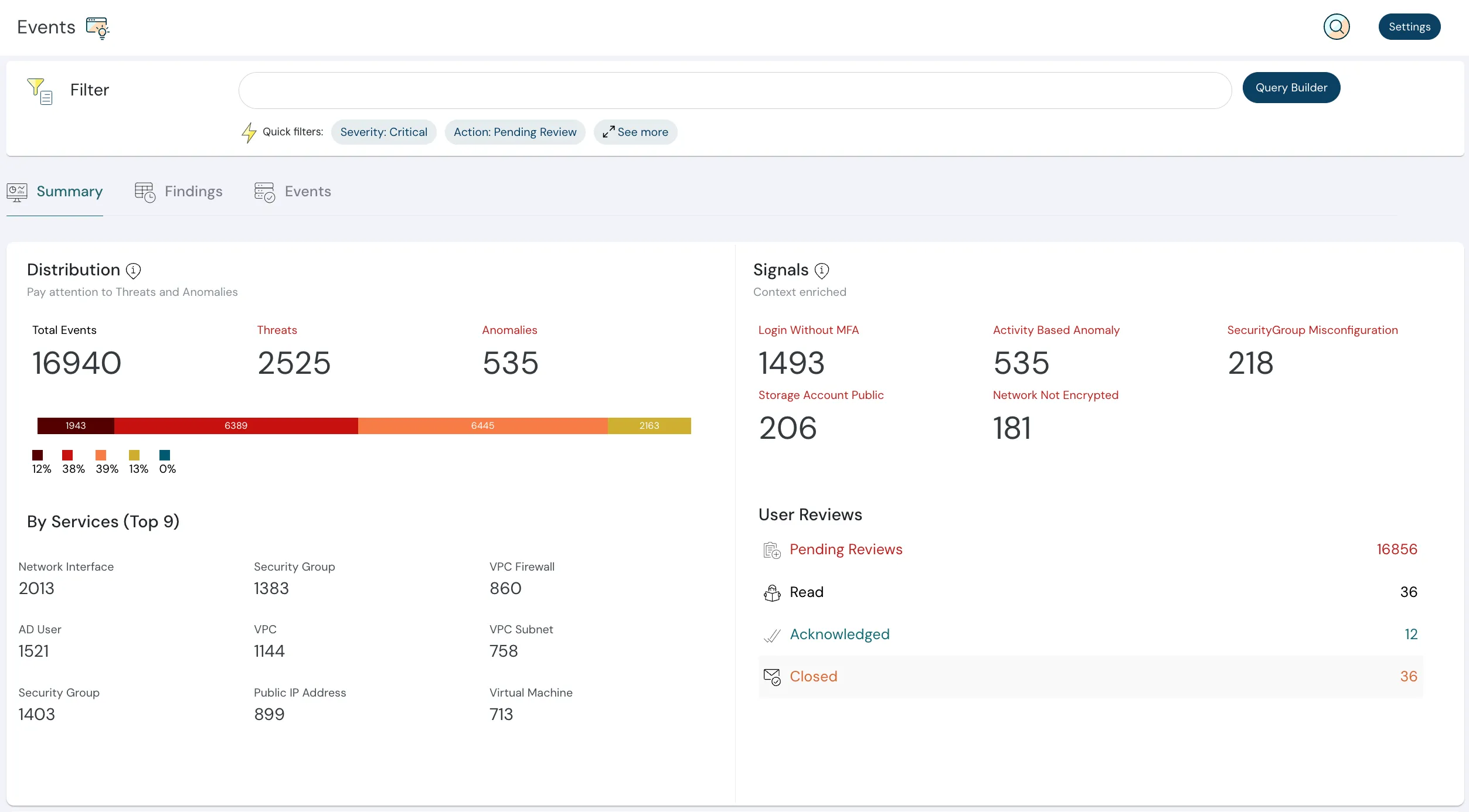
Universal Database Support Across All Platforms
One solution for all your databases. Cloudanix DAM provides seamless support for MySQL, PostgreSQL, Oracle, SQL Server, MongoDB, Cassandra, Snowflake, Redshift, and more. Whether you're running databases on customer-hosted VMs, managed services like RDS and Aurora, or modern cloud-native solutions, Cloudanix DAM integrates effortlessly with your existing infrastructure. Deploy once and secure all your database assets with unified policy-based query prevention, dynamic data masking, and comprehensive audit logging.
Learn About JIT AccessDatabase Activity Monitoring (DAM)
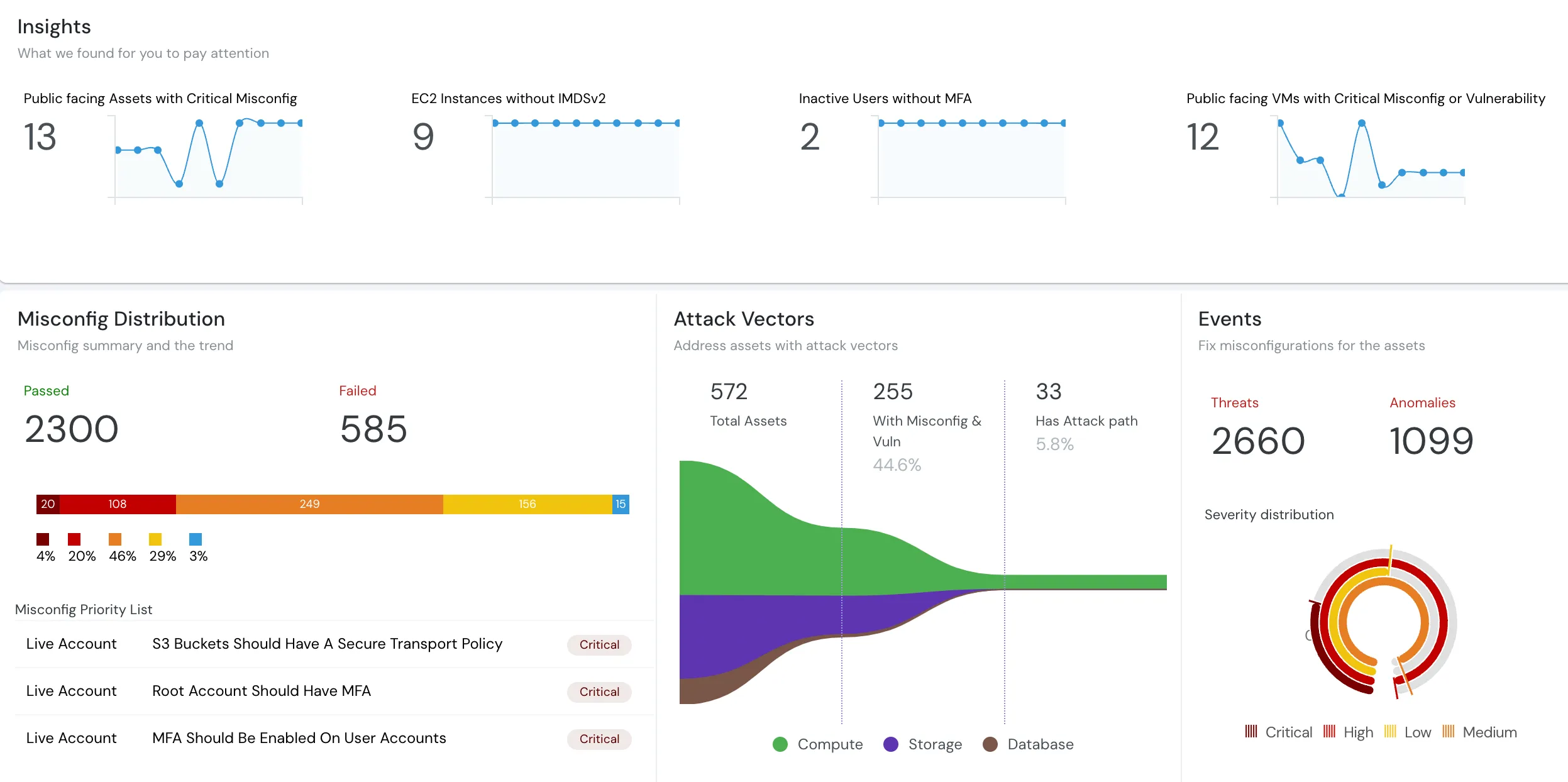
Stop Data Breaches Before They Happen
Organizations face unprecedented challenges in securing their data assets. 84% of enterprises experienced a database breach in the past 24 months, with an average cost of $4.88 million per incident. 67% struggle with privileged access management, while compliance requirements continue to expand globally (GDPR, CCPA, HIPAA, PCI-DSS). Cloudanix DAM mitigates these risks with preventive security controls that stop malicious queries before execution, dynamic data masking that protects sensitive information based on user roles, and comprehensive monitoring that provides complete audit trails—all while keeping your data within your own infrastructure.

Trusted by over 100+ customers worldwide
Complete Protection
Comprehensive Database Security Features
Cloudanix DAM delivers enterprise-grade database security with a privacy-first approach. Every feature is designed to protect your sensitive data while maintaining complete sovereignty and control.
Universal Database Coverage
Support for MySQL, PostgreSQL, Oracle, SQL Server, MongoDB, Snowflake, and all major databases across VMs and managed services.
Query Prevention
Block malicious or policy-violating queries before execution. Stop data exfiltration and unauthorized access in real-time.
Dynamic Data Masking
Automatically redact sensitive data based on user roles and context. Protect PII, PHI, and financial data without disrupting workflows.
Data Discovery
Automatically identify and classify sensitive data across all your databases. Understand where your critical data resides.
Policy-Based Controls
Define granular access policies with attribute-based controls. Enforce compliance requirements through automated policy enforcement.
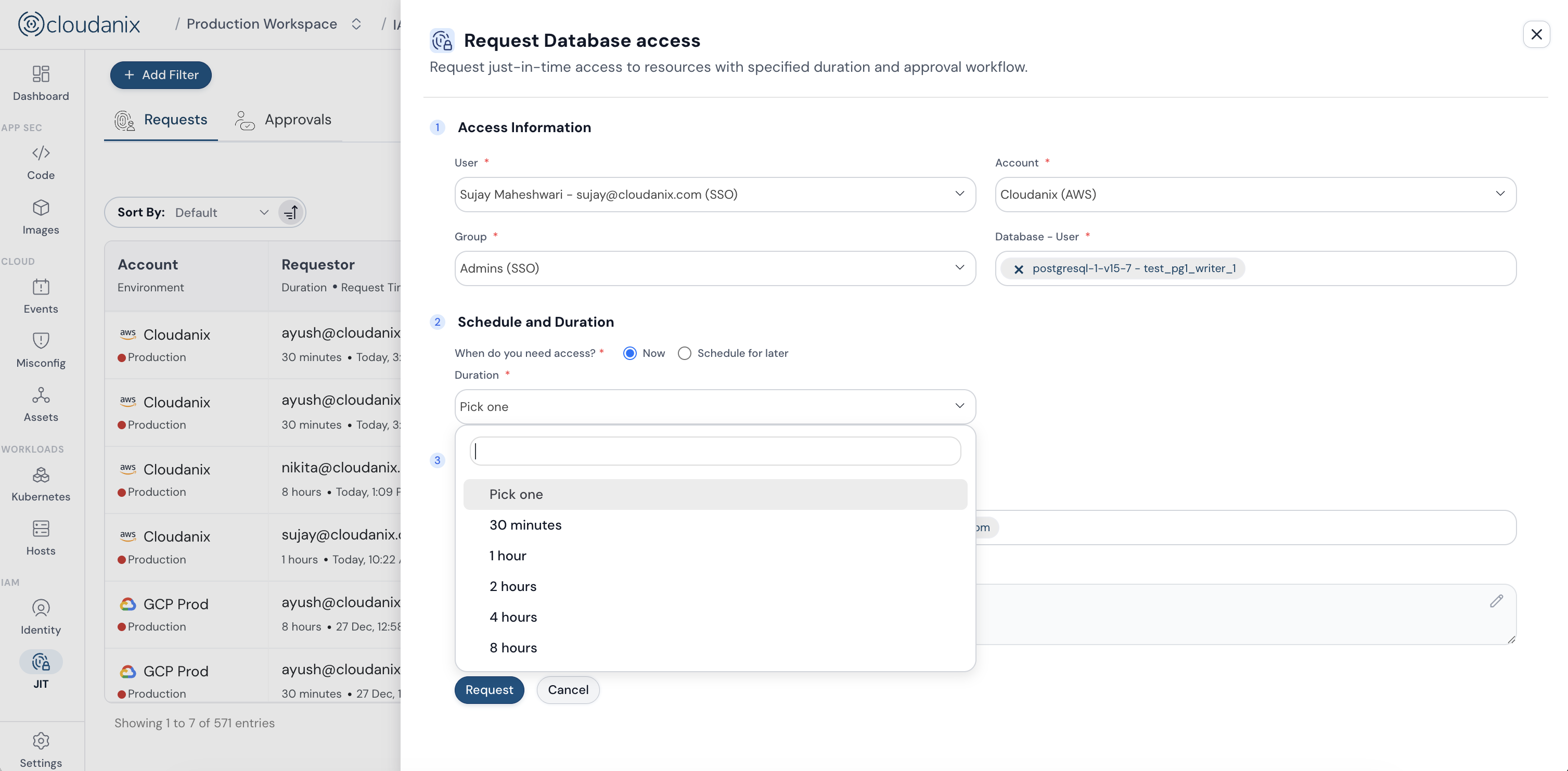
Just-In-Time Access
Time-bound access with automated expiration and revocation. Integrated approval workflows with Slack and MS Teams.
Real-Time Monitoring
Live query tracking and analysis with behavioral analytics. ML-powered anomaly detection identifies suspicious patterns.
Complete Audit Trails
Every database activity logged to your cloud storage. Comprehensive audit trails for compliance and forensic analysis.
100% Data Sovereignty
Your data never leaves your infrastructure. Maintain complete control and compliance with data residency requirements.
How Cloudanix DAM Works
Complete Database Security in Three Simple Steps
Deploy enterprise-grade database security in minutes, not months. Cloudanix DAM's unique architecture eliminates the complexity of traditional DAM solutions while providing superior protection and complete data sovereignty.
30-Minute Onboarding
Deploy containerized components directly in your cloud account. Configure the secure browser-based IDE access and connect to your target databases with built-in Just-In-Time access management. No complex infrastructure changes required.
Policy Configuration
Define granular access policies and data classification rules tailored to your organization. Set up intelligent masking patterns for sensitive data (PII, PHI, financial data) and configure JIT access workflows with approval chains integrated into Slack and MS Teams.
Real-Time Protection
Users access databases through the secure IDE where policies enforce in real-time before query execution. All database activity is logged to your cloud storage, with optional metadata streaming to the control plane for AI-powered anomaly detection and automated threat response.
Continuous Monitoring & Audit
Maintain complete audit trails with automatic logging of all database activities. Optional AI-powered anomaly detection identifies suspicious patterns and unauthorized behaviors, with automated alerts and incident response workflows to stop threats before damage occurs.
A Revolutionary Approach to Database Security
Cloudanix DAM vs Traditional Solutions
Unlike traditional DAM solutions that force you to choose between comprehensive monitoring and data sovereignty, Cloudanix DAM delivers both. See how our privacy-first architecture compares to conventional approaches.
Why Organizations Choose Cloudanix DAM
Here's how we compare to traditional DAM solutions:
- 100% Data Sovereignty: Your data never leaves your infrastructure vs. traditional DAM that requires data egress to third-party systems
- 30-Minute Setup: Deploy in minutes vs. complex 3-6 month traditional implementations
- Prevention Before Detection: Stop malicious queries before execution vs. detect-after-damage approach
- Integrated CNAPP: Optional code-to-cloud visibility in a single dashboard vs. siloed point solutions
- Zero Data Egress Costs: All processing in your environment vs. expensive data transfer fees
- Built-in JIT Access: Native integration with Just-In-Time access management vs. separate IAM/PAM systems
- 60% Lower TCO: Reduced infrastructure and no data egress costs vs. high licensing and operational expenses
- Data Residency Compliant: Runs in your sovereign region vs. potential compliance violations
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedYour questions answered.
Frequently Asked Questions
Everything you need to know about Database Activity Monitoring (DAM) — its role, value, and why modern data-driven organizations can't afford to operate without it.
Why Choose Cloudanix DAM
Key Features and Capabilities
Cloudanix DAM delivers comprehensive database security with features designed for modern cloud-native environments. From universal database support to preventive controls and seamless JIT integration, every feature is built with privacy and control at its core.
Universal Database Support
Any Database, One Solution: MySQL, PostgreSQL, Oracle, SQL Server, MongoDB, Cassandra, Snowflake, Redshift, and more. Cloud-Native Integration: Seamless support for RDS, Aurora, Azure SQL, Cloud SQL, and other managed services. Legacy Protection: Secure on-premises and hybrid deployments without infrastructure changes.
Just-In-Time Access Integration
Time-Bound Access: Automated expiration and revocation with complete audit trails for every access request. Multi-Resource Support: Unified JIT for databases, cloud console, Kubernetes, and VMs. Approval Workflows: Native integration with Slack, MS Teams, and other collaboration tools for seamless access management.
Learn MorePreventive Security Controls
Query Blocking: Stop malicious or policy-violating queries before execution to prevent data exfiltration. Dynamic Data Masking: Automatic sensitive data redaction based on user roles and context. Policy-Based Access Control: Granular rules engine with attribute-based controls for fine-grained permissions.
100% Data Sovereignty
Privacy First: Your data never leaves your infrastructure—maintain complete control and compliance. Customer-Controlled: Complete deployment within your cloud account with all audit trails stored in your cloud storage. Intelligent Control Plane: Optional metadata analysis for anomaly detection with zero customer data transmission.
90% Reduction in Data Breach Risk
Preventive Controls: Stop threats before damage occurs with real-time query blocking and data masking. Behavioral Analytics: ML-powered anomaly detection identifies suspicious patterns and unauthorized access. Zero Trust Architecture: Default-deny access model with continuous verification ensures only authorized users access sensitive data.
75% Faster Compliance Audits
Automated Reporting: Generate compliance reports for GDPR, HIPAA, PCI-DSS, SOC 2 with one click. Complete Audit Trails: Every database query, access request, and policy change is logged and timestamped. Compliance-Ready: Built-in support for major regulatory frameworks reduces audit preparation time dramatically.
CLOUDANIX
Insights from Cloudanix
Explore guides, checklists, and blogs that simplify cloud security and help you secure your infrastructure.
Case Studies
Real-world success stories where Cloudanix helped organizations secure their cloud infrastructure. Watch how we made a d...

What is CSPM?
Understand what Cloud Security Posture Management (CSPM) is and how it automates security and compliance across cloud en...
CASB, CSPM, SIEM: Cloud Security Essentials
Understand how CASB, CSPM, and SIEM work together to enhance your cloud security posture and ensure better governance.
What is Cloud Audit?
In-depth assessment of cloud environment for security, compliance, and optimization. Identify vulnerabilities, ensure da...
Top 10 Challenges of CSPM
Cloud environments are getting more complex and dynamic day by day, making it difficult to gain complete visibility into...
Cloudanix docs
Cloudanix offers you a single dashboard to secure your workloads. Learn how to set up Cloudanix for your cloud platform ...
Changelog
A complete history of changes, improvements, and fixes for Cloudanix. Subscribe to get notified about the latest updates...
