Identity Security & Just In Time Access
In The Cloud, Network Is Not The Perimeter. IAM Is.
Zero Trust security starts with Just In Time access. Cloudanix offers JIT for Cloud, Database and Workloads. Just In Time onboarding and adoption is easy with no disruption to any of your existing tooling and setup. Your identity perimeter becomes your strongest security boundary.
Zero Trust Access Management
Comprehensive Just In Time Access Across Your Infrastructure
Cloudanix provides Just In Time access for every layer of your cloud infrastructure. Eliminate standing privileges and achieve true Zero Trust security with time-bound, workflow-approved access.
Just In Time Cloud
Temporary access to cloud accounts without permanent IAM permissions. Integrates with IAM or Identity Center in 30 minutes.
- Compliance: Complete audit trail of who got access, who approved, and what they did
- Zero permanent access for individuals and third-party vendors
- Works with any IdP of your choice
- Used by DevOps, SRE, Engineering, IT, Third Party Vendors
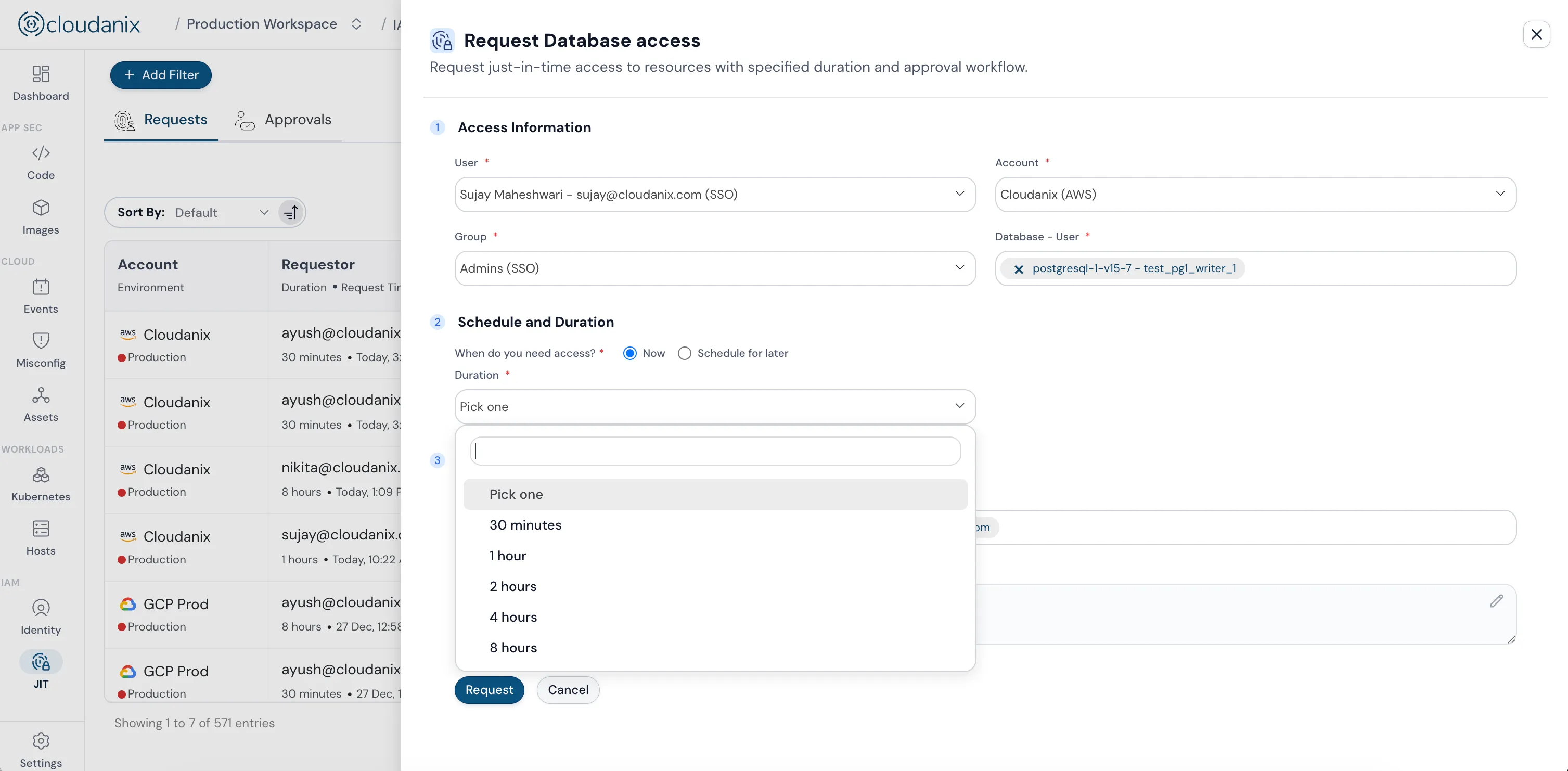
Just In Time Database
Session-based temporary database access with no static passwords. Every database operation is logged for compliance.
- Eliminates jump boxes and public IPs
- Generates time-bound temporary passwords
- Complete audit trail of database operations
- Used by Data Science, Engineering, IT, Customer Success, GenAI teams
Just In Time VM
On-demand SSH and SSM access to virtual machines with no key management overhead. Role-based access control with complete approval workflows.
- No SSH key management required
- Time-bound access credentials on demand
- Users access via their current tools (SSH/SSM)
- Complete compliance audit trail
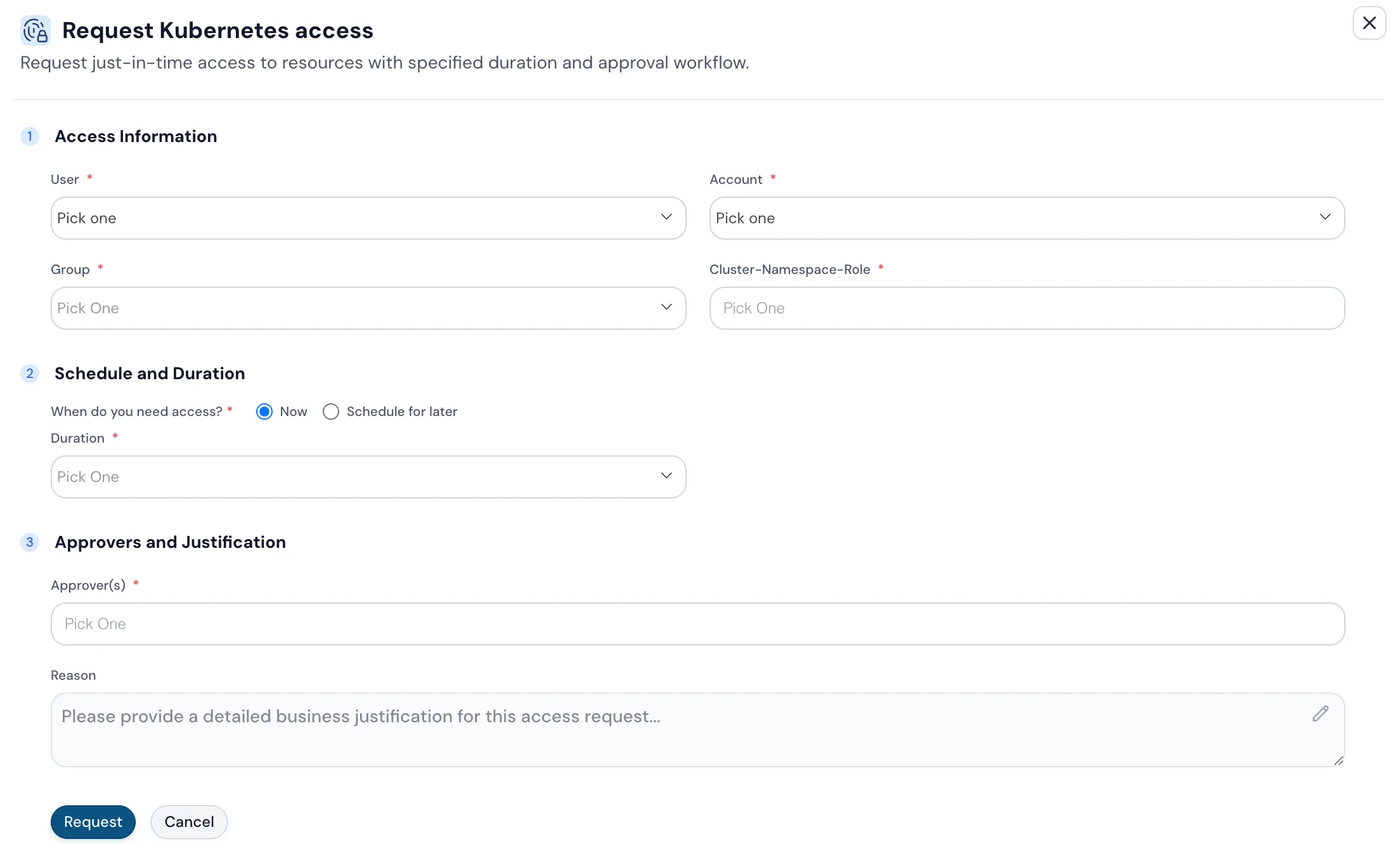
Just In Time Kubernetes
Temporary kubectl access to Kubernetes clusters with approval workflows. Eliminate long-term cluster access.
- No long-term kubeconfig management
- Time-bound cluster access
- Role-based permissions with approvals
- Used by Engineering, DevOps, SRE, Platform teams
Just In Time SaaS
Temporary access to SaaS applications with approval workflows. Eliminate standing administrative privileges.
- Time-bound SaaS access
- Approval workflows for elevated privileges
- Complete audit logging
- Integration with popular SaaS platforms
Complete Entitlement Management
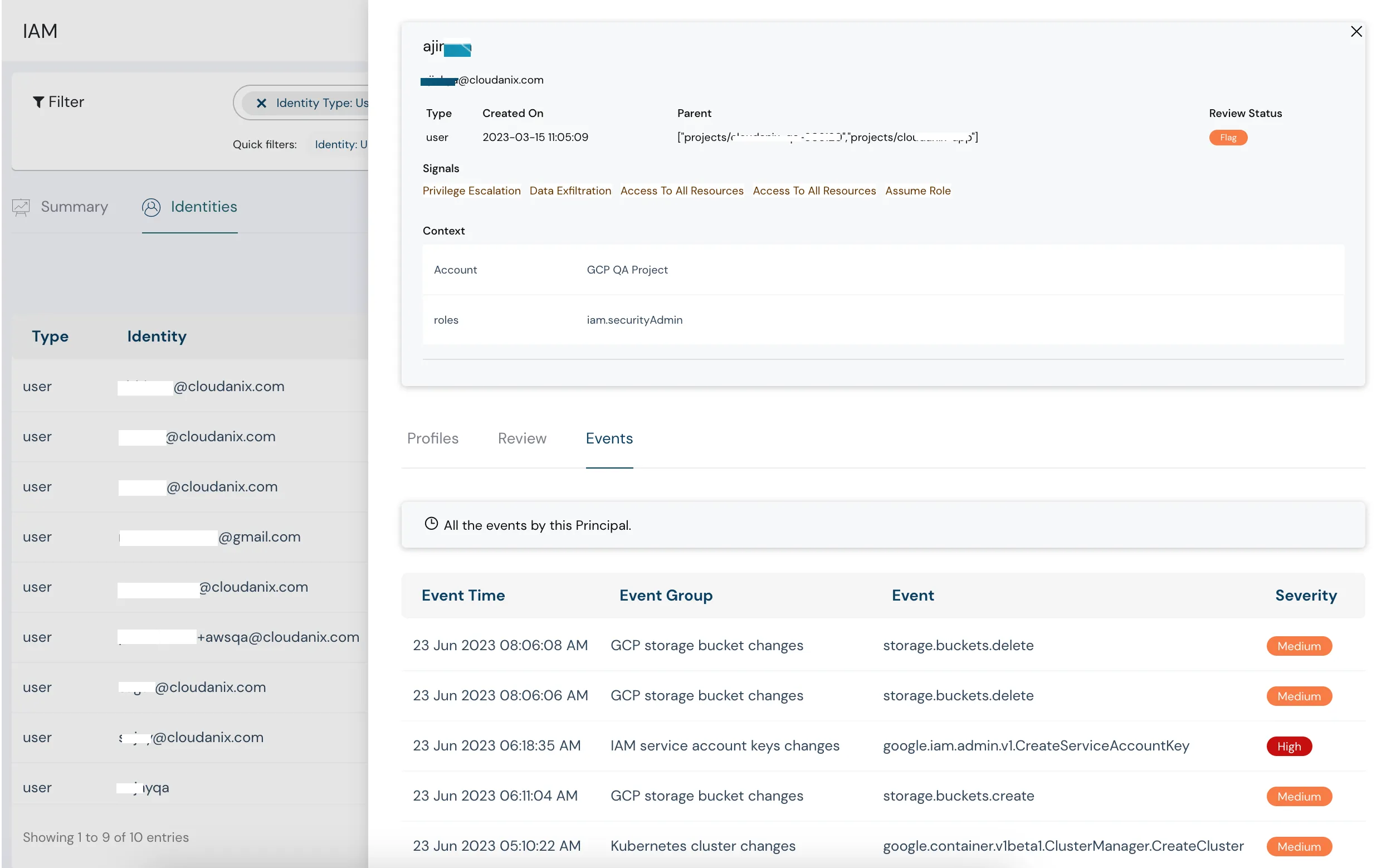
Monitor permissions, detect excessive entitlements, and maintain least privilege with Cloud Infrastructure Entitlement Management.
- Identify over-permissioned identities
- Access pattern analysis
- Compliance reporting
- Real-time threat detection
Zero Standing Privileges
Eliminate permanent access across your entire infrastructure. Every access request is temporary, approved, and audited.
Complete Compliance Coverage
Meet regulatory requirements with comprehensive audit trails and access governance across all your infrastructure.
- SOC 2 compliance ready
- HIPAA audit trails
- PCI DSS requirements
- GDPR data access logging
Modern Cloud Security Requires Modern Access Controls
Why Identity Is the New Perimeter
Traditional network perimeters have dissolved in cloud environments. Your applications, databases, and workloads are distributed across multiple clouds, regions, and services. In this new reality, identity becomes your security perimeter. Every access decision must be authenticated, authorized, and audited. Just In Time access ensures that even trusted identities only receive the minimum permissions needed, only when needed, and only for as long as needed. This is the foundation of Zero Trust security—never trust, always verify, and grant access just in time.
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedHow Cloudanix JIT Works
Simple, Secure, Seamless Access Management
Cloudanix Just In Time access transforms how your teams access cloud resources. No more permanent privileges, no more security risks from standing access.
Request Access
Team members request temporary access through Slack, the Cloudanix console, or CLI. Specify the resource, permission level, and duration needed—all in seconds.
Workflow Approval
Requests flow through customizable approval workflows. Approvers receive instant notifications in Slack or email and can approve or deny with a single click. Every decision is logged.
Time-Bound Access
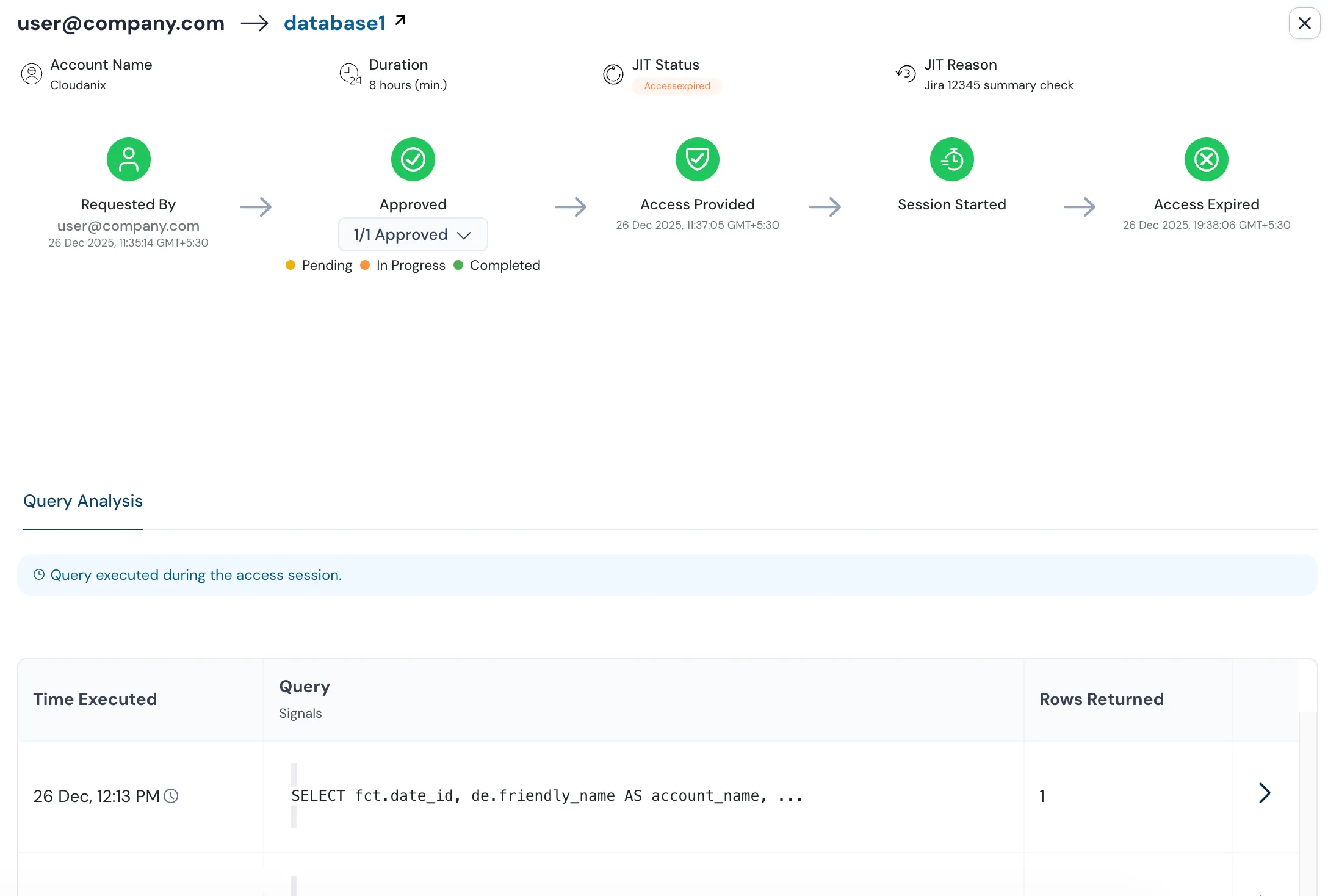
Upon approval, users receive temporary credentials or access that automatically expires. For databases, temporary passwords are generated. For cloud resources, temporary IAM credentials are issued.
Complete Audit Trail
Every action is logged: who requested access, who approved it, what they did with the access, and when it expired. Full compliance coverage for SOC 2, HIPAA, PCI DSS, and more.
Quick Integration
Cloudanix integrates with your existing IAM, Identity Center, or cloud provider setup in 30 minutes. No disruption to current workflows or tools—your teams continue using familiar interfaces.
Universal Access
Works seamlessly for internal teams, contractors, and third-party vendors. Perfect for DevOps, SRE, Engineering, IT, Data Science, Customer Success, and GenAI teams.
Identity & JIT Access
Frequently Asked Questions
Common questions about Cloudanix Identity Security and Just In Time Access
CLOUDANIX
Insights from Cloudanix
Explore guides, blogs, and resources about Identity Security and Just In Time Access that simplify cloud security.
Zero Trust Identity Security
Learn how Just In Time access implements Zero Trust principles by eliminating standing privileges and enforcing time-bou...
Integrate JIT with AWS Identity Center
Step-by-step guide to integrating Cloudanix Just In Time access with AWS Identity Center for seamless, secure temporary ...

JIT Kubernetes for Azure AKS
Discover how to implement Just In Time access for Azure Kubernetes Service (AKS) to secure your container workloads with...
Cloudanix Documentation
Complete technical documentation for implementing and managing Just In Time access across cloud, database, VM, Kubernete...
