Database Activity Monitoring - Yeah, It's here!
Probably our last product update for Year 2025. Or may be not! This one is a special edition though where we want to speaking about GA of Cloudanix DAM (Database Activity Monitoring)
Launching, Cloudanix DAM
Our customers have been using Cloudanix Database JIT. This enabled them to get time bound access to a database running in a private subnet.
The users could use Database IDE of their choice and interact with database. Pretty neat and powerful security measure to put in place.
Why Cloudanix DAM?
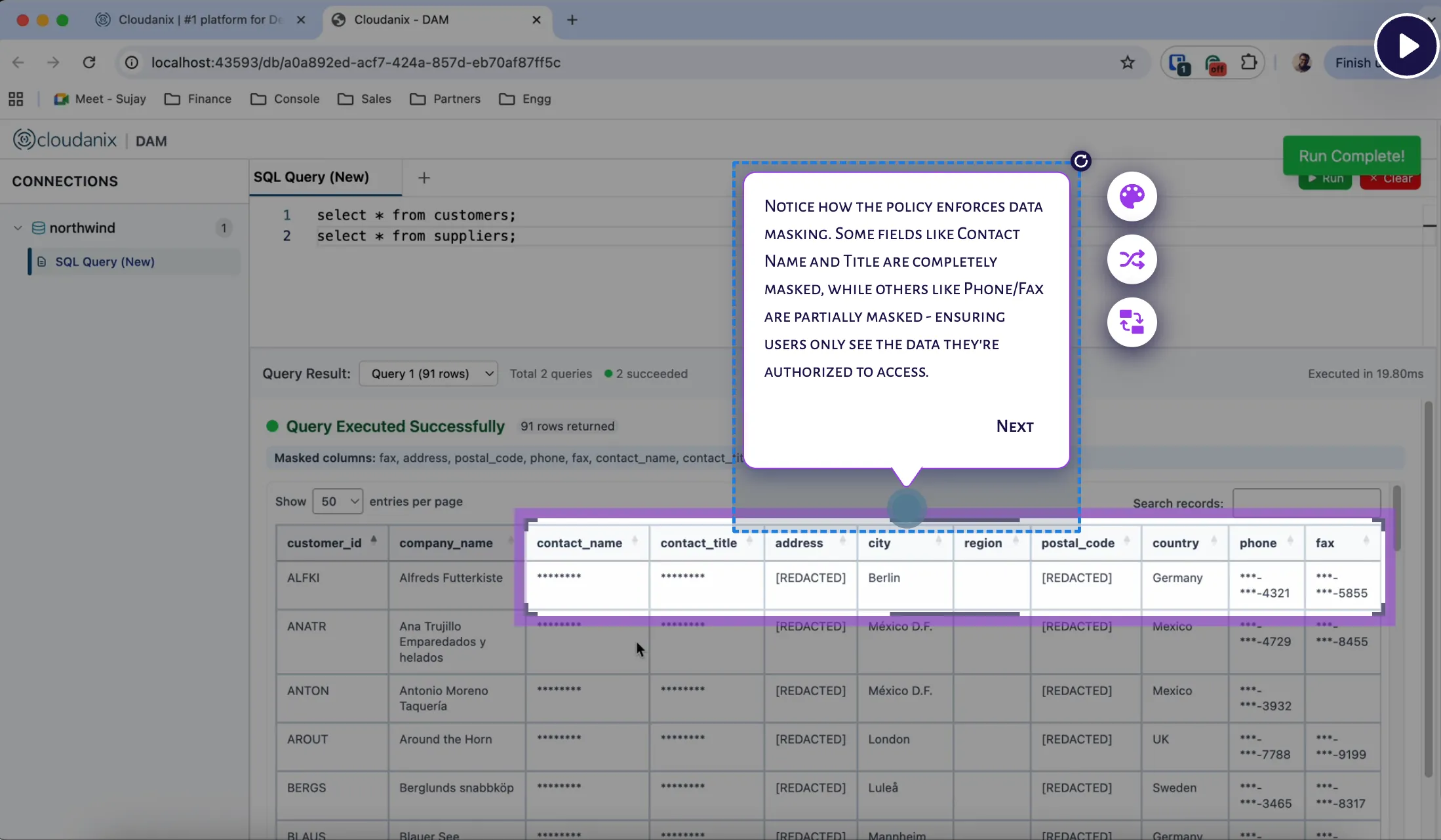
There are many scenario where not every team member can do any operation on database or get access to every piece of data stored in your tables.
For e.g. Your customer success team should not see customer’s SSN. Or your customer support team should only see last 4 digits of customer bank account number. Or under no circumstance, any query can be executed which will truncate the table.
Without Cloudanix DAM, this wasn’t easy as the user got access to database via IDE of their choice with no policy or data masking enforcements.
Welcome, Cloudanix DAM
Cloudanix DAM gives you a complete control on what your team members can execute and access. If you want to mask data, restrict access, prevent execution of queries - all of this can be done without any change to your database.
Takes 30 minutes to onboard. Access to your data can now have governance & access logs which your regulatory requirements and a good security practice always wanted.
The best part - Not a byte of information leaves your Cloud account. And yes, it works with any underlying database.
Launch Partner at AWS India Marketplace
We love AWS Marketplace. And now customers from India can transact and pay via local currency (Indian Rupee - INR), makes it very convenient and attractive for the customers. No more WHT issues.
We had the opportunity and privilege to be part of this journey as a Launch Partner. See announcement from AWS here.
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedBlog
Read More Posts
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Tuesday, Feb 10, 2026
The 2026 CNAPP Compliance Framework: Turning Audit from Crisis to Continuity
Introduction: The Death of the Point-in-Time Audit In the high-velocity cloud landscape of 2026, the traditional app
Read MoreThursday, Feb 05, 2026
CSPM vs. CNAPP: Navigating Cloud Security Evolution for Modern Enterprises
The shift to cloud-native architectures represents a fundamental change in how applications are designed, built, and dep
Read MoreThursday, Jan 22, 2026
Top 10 Identity and Access Management Solutions
Identity and Access Management (IAM) has traditionally been considered one of the boring parts of security. But with the
Read More