The inability of traditional perimeter defenses (such as firewalls) to protect data from insider threats and privileged users led to the introduction of DAM. Before DAM, organizations relied solely on slow, post-incident native database logs, which were easily circumvented or incomplete. This made real-time alerting and granular auditing nearly impossible, leaving a critical security gap in data protection and compliance.
What is Database Activity Monitoring?
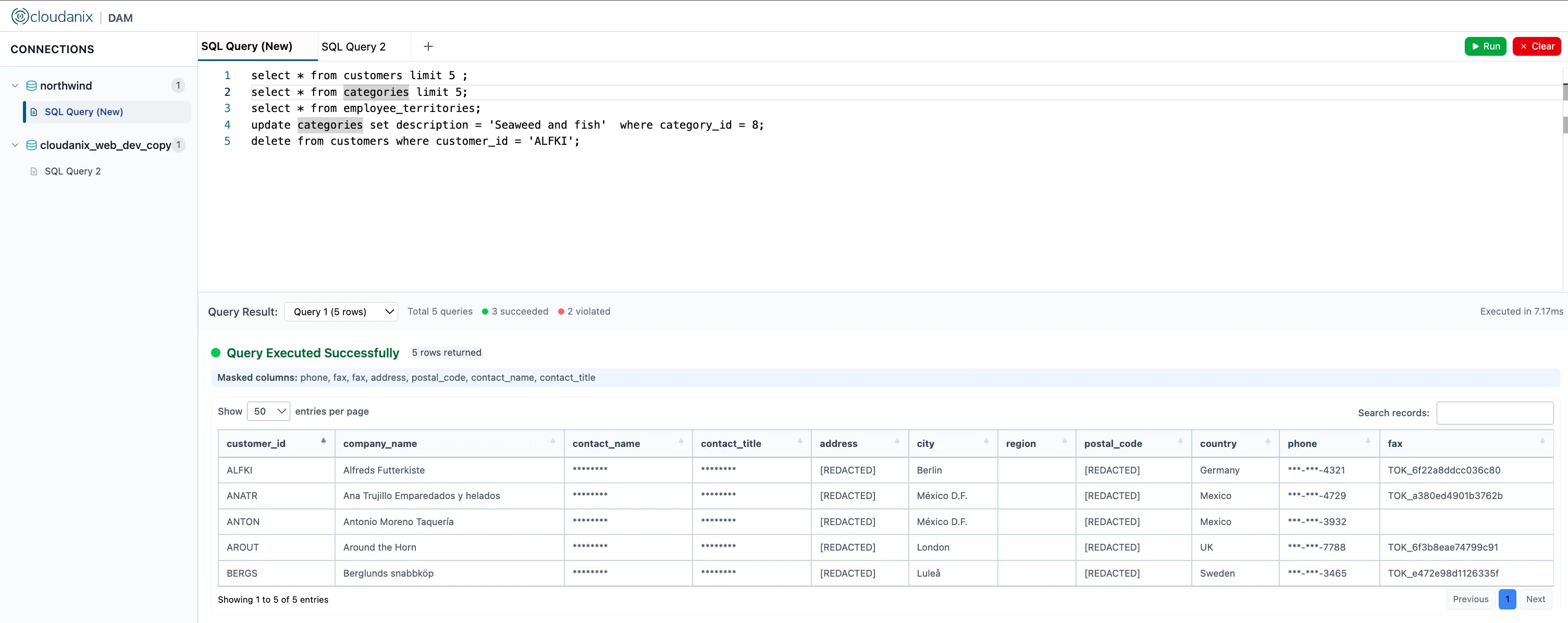
Database Activity Monitoring (DAM) is a security technology that captures, analyzes, and records all events and transactions occurring in real-time between database users/applications and the database itself.
In essence, DAM provides an independent layer of visibility into the “data plane” by:
- Auditing and Logging: Monitoring and recording details like the specific SQL queries executed, the results returned, the identity of the user, and the time of the transaction.
- Real-Time Protection: Identifying and alerting on policy violations or suspicious activities, such as unauthorized access to sensitive tables, changes to the database schema, or signs of a SQL injection attack.
- Enforcing Security Policies: Serving as a primary control point to enforce the principle of least privilege and provide an unalterable audit trail necessary for regulatory compliance (e.g., GDPR, HIPAA, PCI DSS).
What is the difference between Database Access Management and Database Activity Monitoring?
Often, there is confusion between Database Access Management (DAM) and Database Activity Monitoring (DAM) because they both use the same acronym and are closely related security disciplines.
While one is about prevention and control, the other is about visibility and detection. They are best viewed as complementary pillars of an overall data security strategy.
Database Access Management (DAM) - The Gatekeeper
Database Access Management refers to the policies, processes, and technologies focused on governing and securing who can access what data, when, and under what conditions. It is a proactive, pre-access control mechanism.
- Primary Goal: Control and Prevention. To block unauthorized users and actions before they can occur.
- Core Functions:
- Authentication: Verifying the user’s identity (e.g., MFA, SSO).
- Authorization: Defining and enforcing permissions (e.g., RBAC or ABAC).
- Privilege Management: Implementing Just-in-Time (JIT) Access to remove static, standing privileges.
- Focus: Identity and Permissions. Who you are and what you are allowed to do.
- Key Output: A secure connection where the user has the minimum necessary privileges.
Database Activity Monitoring (DAM) - The Security Camera
Database Activity Monitoring (the industry-standard definition of DAM) refers to a security technology that observes, records, and analyzes every action performed inside the database system. It is a reactive and real-time visibility control, operating during and after access.
- Primary Goal: Detection and Auditing. To identify suspicious or unauthorized behavior and maintain an unalterable log for compliance and forensics.
- Core Functions: Real-time Logging: Capturing every SQL query (SELECT, DML, DDL), results, and privileged command, independently of native database logs. Anomaly Detection: Identifying activities that deviate from the normal baseline (e.g., a DBA querying a sensitive table they never normally touch). Alerting: Generating immediate alerts for policy violations or signs of threat.
- Focus: Behavior and Transactions. What the user actually did, when, and how.
- Key Output: A persistent, forensic-quality audit trail and real-time threat alerts.
How does Database Activity Monitoring (DAM) work?
The working process of Database Activity Monitoring (DAM) in the cloud context fundamentally follows the same four steps as Database Access Management, but the implementation methods (Step 1) are adapted due to the constraints of Database-as-a-Service (DBaaS) platforms like Azure SQL Database, AWS RDS, or Google Cloud SQL. In these managed environments, traditional host-based agents often cannot be installed.
Here is the step-by-step process of how a DAM solution operates:
Step 1: Activity Capture
Because you typically can’t install an agent on the underlying database server (the “host”) in a DBaaS model, cloud DAM solutions rely on two primary, non-intrusive methods:
- API/Log-Based Collection: This is the most common method. The DAM solution connects to the cloud provider’s native auditing features to collect the activity logs and events. For example, it might integrate with Azure Auditing or AWS CloudTrail/RDS Audit Logs to pull all recorded SQL statements and session details.
- Gateway or Proxy Deployment (Network-Based): The solution deploys an independent, proxy-based gateway (often a container or VM) that sits between the users/applications and the cloud database endpoint. All traffic passes through this gateway, allowing the DAM solution to sniff, intercept, and record the SQL wire protocol transparently, achieving network-based monitoring.
- Virtual Appliance/Sidecar: For Kubernetes (K8s) or Infrastructure-as-a-Service (IaaS) database deployments (e.g., SQL Server on an Azure VM), a lightweight DAM agent might still be deployed as a sidecar container or a virtual appliance on the same virtual network.
Step 2: Interpretation and Normalization
This step remains largely unchanged, but the normalization process is crucial in multi-cloud or hybrid environments:
- Reconstruction and Translation: Raw log data or intercepted packets are reconstructed into complete SQL statements (DML, DDL, DCL).
- Normalization Across Services: The DAM system normalizes the audit records, whether they came from an Azure SQL audit log, an AWS RDS log, or a containerized database, into a single, unified format. This is vital for centralized reporting and applying consistent policies across a heterogeneous cloud database fleet.
Step 3: Analysis and Enforcement (Centralized Cloud Policy)
The analysis phase is often enhanced by the scalability of the cloud environment and its integrated identity services:
- Policy Correlation: Normalized activities are checked against security policies. Crucially, in the cloud, these policies often integrate directly with Identity and Access Management (IAM) systems like Microsoft Entra ID or AWS IAM to resolve the identity of the user who executed the query.
- Behavioral Anomaly Detection: Cloud DAM platforms leverage scalable cloud infrastructure to run machine learning algorithms against large volumes of historical data to establish baselines of normal behavior and flag anomalies in real-time.
- Real-time Alerting and SIEM Integration: Upon detecting a threat (e.g., unauthorized data deletion), the system generates immediate alerts that are typically streamed directly to a centralized Security Information and Event Management (SIEM) tool (like Azure Sentinel or Splunk) for correlation with non-database events.
Step 4: Centralized Auditing and Compliance (Tamper-Proof Cloud Storage)
The cloud provides secure, cost-effective storage for the forensic trail:
- Secure Log Storage: The independent, comprehensive audit trail is securely stored in a scalable, tamper-proof cloud storage solution (e.g., an encrypted Azure Blob Storage account or S3 bucket). This storage is completely segregated from the original database to ensure a true separation of duties.
- Compliance Reporting: This centralized repository enables the generation of unified reports for auditors, proving that access and activity were monitored and controlled across the entire multi-cloud data estate.
In essence, DAM works by decoupling monitoring from access. Whether deployed via agents (on-prem/IaaS) or cloud-native integration/proxies (DBaaS), the system creates an independent, immutable, and normalized audit trail of every database event.
What are the benefits of DAM?
Implementing Database Activity Monitoring (DAM) in a cloud context provides a robust defense layer that satisfies both deep technical security requirements and broad non-technical governance and compliance needs.
Cloud DAM significantly shrinks the attack surface and provides unparalleled security visibility, regardless of the underlying database service (DBaaS or IaaS).
- Detection of Insider and Privileged User Threats: DAM monitors all activities of database administrators (DBAs) and privileged users, who often bypass perimeter security. Since this monitoring is independent of native database logs, privileged users cannot erase the audit trail of their actions, enabling true separation of duties.
- Real-Time Threat Detection and Alerting: It captures and analyzes database traffic and events in real-time, allowing security teams to immediately detect and receive alerts on suspicious behaviors, such as unauthorized data access, schema changes, or signs of a SQL injection attack.
- Comprehensive Auditing and Forensic Trail: DAM creates a persistent, immutable, and forensic-quality audit trail of every SQL query, user identity, and result set. This capability is essential for post-incident analysis and understanding the full scope of a breach.
- Anomaly and Behavioral Analysis: Modern DAM solutions use machine learning to establish a baseline of normal user activity. They automatically detect deviations from this baseline—such as a developer accessing production data they normally don’t touch—which helps flag sophisticated threats that policy checks might miss.
The visibility provided by DAM directly translates into better governance, reduced financial risk, and streamlined operations.
- Simplified Regulatory Compliance: DAM provides the necessary, detailed evidence (the “who, what, and when”) required to satisfy stringent audit requirements for standards like GDPR, HIPAA, PCI DSS, and SOX. It turns compliance from a manual burden into an automated reporting function.
- Reduction of Data Breach Risk and Cost: By providing real-time detection and preventing unauthorized data access or exfiltration, DAM significantly lowers the probability of a costly data breach.
- Support for Zero Trust Architecture: DAM is a critical technology for enforcing the “Verify Explicitly” and “Least Privilege Access” principles of Zero Trust. It continuously monitors that users, even trusted ones, are only accessing the resources they explicitly need, when they need them.
- Operational Efficiency and DBA Accountability: By centralizing audit logs and normalizing data across different database platforms (heterogeneous environments), DAM reduces the manual effort and performance overhead typically associated with enabling resource-intensive native database auditing features.
Cloud DAM provides independent, real-time visibility and control over all database activities, effectively closing the security gap left by perimeter defenses and fulfilling the stringent auditing requirements of cloud-native governance and compliance.
What are the challenges of implementing the Database Access Management tool, and how to overcome?
Implementing a Database Activity Monitoring (DAM) tool, especially in dynamic cloud environments, presents several technical and operational challenges.
Performance and Resource Overhead
Agent Overhead (Host-Based): Solutions that rely on installing an agent directly on the database server can consume CPU and disk resources with every query, potentially degrading database speed and responsiveness, especially under high transaction volumes.
Decryption Load: Monitoring encrypted traffic (common via SSL/TLS in cloud databases) requires the DAM solution to decrypt and re-encrypt the data stream to inspect the SQL payload. This process adds latency to the query execution and increases the system load.
Encrypted Traffic and Blind Spots
The method of deployment dictates the visibility of the DAM solution.
Network-based DAM (using taps or sniffing) will often miss encrypted traffic unless a man-in-the-middle or SSL decryption capability is implemented, which adds complexity. It can also fail to capture local database activity (e.g., stored procedures, scheduled jobs, or privileged users logging in directly on the host).
In Database-as-a-Service (DBaaS) environments, you cannot install host agents. This forces reliance on native cloud audit logs, which, while convenient, can sometimes lack the deep, granular, and independent context provided by agent-based monitoring.
Operational Complexity and Scalability
Managing a DAM solution across a large, hybrid environment is operationally demanding.
In hybrid or IaaS environments, managing, updating, and ensuring compatibility of agents across hundreds of databases running various OS versions and database versions (e.g., Oracle, PostgreSQL, SQL Server) creates a significant and costly operational burden.
Databases generate a massive amount of data, and logging every single query creates huge volumes of audit data. The DAM system must efficiently handle this data growth, or it risks leading to delays, data loss, or overwhelming security teams with unprioritized alerts (“alert fatigue”).
Contextualizing Activity and Alert Fidelity
A primary challenge is transitioning from raw activity logs to actionable security intelligence.
DAM captures the activity, but without sensitive data classification (knowing which data is highly sensitive, like PII or credit card numbers), security teams struggle to prioritize the immense volume of alerts and focus on genuine threats versus routine activity.
In complex, multi-tiered application environments, identifying the true end-user or the specific application code that initiated a transaction can be difficult. Without accurate correlation, the resulting audit log lacks the necessary accountability for compliance and forensics.
To address the challenges of implementing Database Activity Monitoring (DAM) in the cloud, a shift from traditional agent-based thinking to a cloud-native, hybrid model is required.
How quickly and accurately can DAM detect and alert to an active data exfiltration attempt?
Database Activity Monitoring (DAM) can detect and alert on active data exfiltration attempts in near real-time to real-time, achieving a significant reduction in the Mean Time to Detect (MTTD) a breach. The accuracy is generally high, especially when machine learning is employed, but it is fundamentally dependent on how the tool is deployed and configured.
Detection Speed: Near Real-Time
The goal of DAM is to shrink the detection window from days or months (which is the industry average for many breaches) to seconds or minutes.
For attacks involving compromised credentials or privilege misuse, the average time for organizations to identify a breach is alarmingly long—often over 200 days.
DAM operates by intercepting and analyzing SQL queries as they are executed. This continuous, stream-based analysis means detection is synchronous with the attacker’s activity. For instance, an alert is triggered the moment a privileged user runs a suspiciously large SELECT * query on a sensitive table. This ability to spot anomalies at the moment of access is what enables the massive reduction in MTTD.
Detection Accuracy: High, Context-Dependent
DAM’s accuracy is considered high, particularly when it relies on behavioral context, but it must be carefully managed to prevent alert fatigue.
Modern DAM systems use machine learning (ML) and behavioral analytics to establish a baseline of normal activity for every user, application, and database. This allows the system to achieve high accuracy (e.g., in testing for covert data channels, models can achieve over 95% accuracy) in detecting deviations that signify exfiltration, such as:
- Unusual queries (e.g., accessing credit card numbers late at night).
- High volume of data returned (e.g., a developer suddenly extracting millions of rows).
- Connection from an unexpected source IP address.
A major challenge is tuning the detection sensitivity to minimize False Positive Rates (FPR). If a DAM solution generates too many irrelevant alerts, security analysts will suffer from alert fatigue and may miss a genuine exfiltration attempt. Best practices involve:
- Integrating sensitive data classification to prioritize alerts only on high-value data.
- Implementing feedback loops where security analysts tag false positives, allowing the ML models to continuously improve and suppress recurring benign activity.
Conclusion
Database Activity Monitoring (DAM) is an indispensable layer of the modern cloud security stack, essential for achieving Zero Trust for data.
It directly addresses the most critical security gap by operating as an independent, tamper-proof security camera that watches the data plane. DAM’s ability to transition from passive logging to real-time behavioral analysis provides immediate alerts on potential data exfiltration attempts, drastically reducing the Mean Time to Detect (MTTD) a breach. Ultimately, DAM transforms compliance reporting from a burden into an automated, verifiable process.
