Cloudanix
Google Cloud Compute Audit
Comprehensive Google Cloud security auditing services to protect your compute instances from misconfigurations and security vulnerabilities.
OS Login Configuration
Enable OS login to ensure that SSH keys used to connect to instances are mapped with IAM users for enhanced security and access control.
IP Forwarding Security
IP forwarding should be disabled on all instances to ensure proper packet routing and prevent unauthorized network traffic.
Multi-AZ High Availability
Ensure instances are configured across multiple availability zones to eliminate single points of failure and ensure proper failover capabilities.
VM Instance Threshold
Monitor and control the total number of VM instances to prevent unauthorized resource consumption and ensure only approved applications are running.
SSH Key Management
Implement instance-specific SSH keys instead of project-wide keys to enforce the principle of least privilege and prevent privilege escalation.
Service Account Security
Prevent instances from using default service accounts with full API access and ensure proper service account configuration with least privilege principles.
Customer Encryption Keys
Enable Customer Supplied Encryption Keys for disks to ensure only authorized team members can access disk data, including protection from Google access.
Serial Port Security
Disable serial port connections for VM instances to prevent unrestricted IP access and enhance instance security.
Shielded VM Protection
Ensure Compute instances are launched with Shielded VM enabled for advanced security protections against rootkits and boot-level attacks.
Public IP Management
Prevent compute instances from being configured with external IP addresses to reduce attack surface and enhance network security.
Default Service Account Prevention
Configure instances to avoid using default Compute Engine service accounts with excessive Editor role permissions on projects.
Resource Limit Monitoring
Monitor resource usage against Google Cloud account limits to prevent service disruptions and ensure resource availability.
Confidential Computing
Enable Confidential Computing to protect sensitive code and data encrypted in memory during processing, preventing Google access to encryption keys.
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedCLOUDANIX
Insights from Cloudanix
Explore guides, checklists, and blogs that simplify cloud security and help you secure your infrastructure.
Case Studies
Real-world success stories where Cloudanix helped organizations secure their cloud infrastructure. Watch how we made a d...
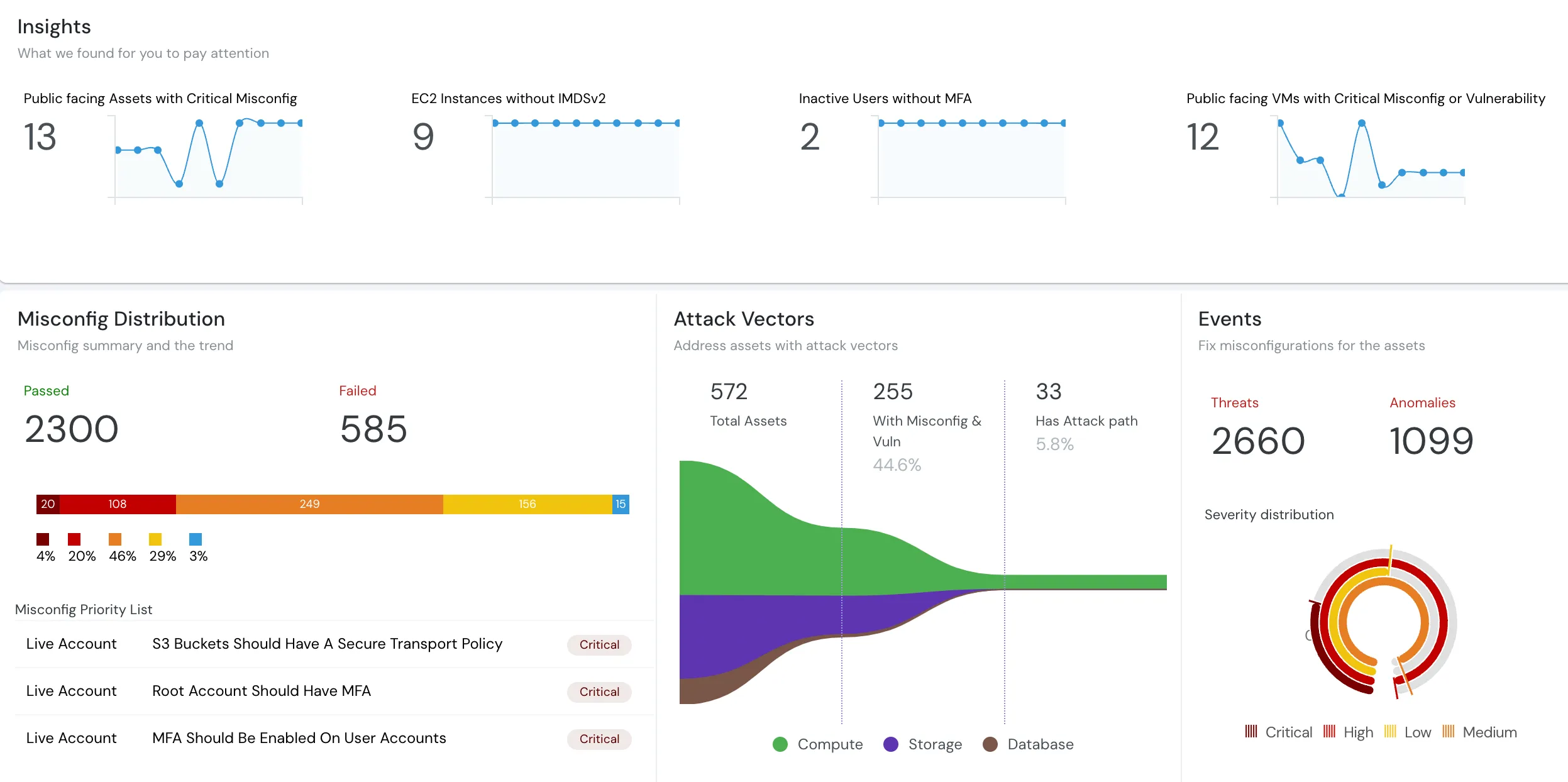
What is CSPM?
Understand what Cloud Security Posture Management (CSPM) is and how it automates security and compliance across cloud en...
CASB, CSPM, SIEM: Cloud Security Essentials
Understand how CASB, CSPM, and SIEM work together to enhance your cloud security posture and ensure better governance.
What is Cloud Audit?
In-depth assessment of cloud environment for security, compliance, and optimization. Identify vulnerabilities, ensure da...
Top 10 Challenges of CSPM
Cloud environments are getting more complex and dynamic day by day, making it difficult to gain complete visibility into...
Cloudanix docs
Cloudanix offers you a single dashboard to secure your workloads. Learn how to set up Cloudanix for your cloud platform ...
Changelog
A complete history of changes, improvements, and fixes for Cloudanix. Subscribe to get notified about the latest updates...
