Cloudanix
How to secure AWS IAM?
Root account has full permissions across the entire account. Root account should not have access keys. Also, it certainly shouldn't access any service. Instead, create IAM users with predefined roles.
Root Account Should Not Have Access Keys
Root account has full permissions across the entire account. Root account should not have access keys. Also, it certainly shouldn't access any service. Instead, create IAM users with predefined roles.
Root Account Access Keys Should Be Rotated
Root account should not have access keys. If at all you have that, then the keys should be rotated periodically.
Certificates Should Not Be Tied With Root Account
Certificates should not be tied with root accounts.
Root Account Certificates Should Be Rotated
Certificates tied with root accounts needs rotation.
Root account Should Have MFA
Multifactor Authentication is strongly recommended to be enabled for every account with no exceptions in order to secure your AWS environment and adhere to IAM security best practices.
Root Account Should Have Password Rotation
Ensure that your root account password is rotated every few days.
AWS Account Should Have A Minimum Number of Admins
Your AWS account should have minimum number of admins
AWS Account Should Not Have Too Many Admins
Your AWS account has too many admins.
User Account Without Any Usage Should Be Removed
Any unused IAM user without console access and API access should be removed as an extra security measure for protecting your AWS resources against unapproved access.
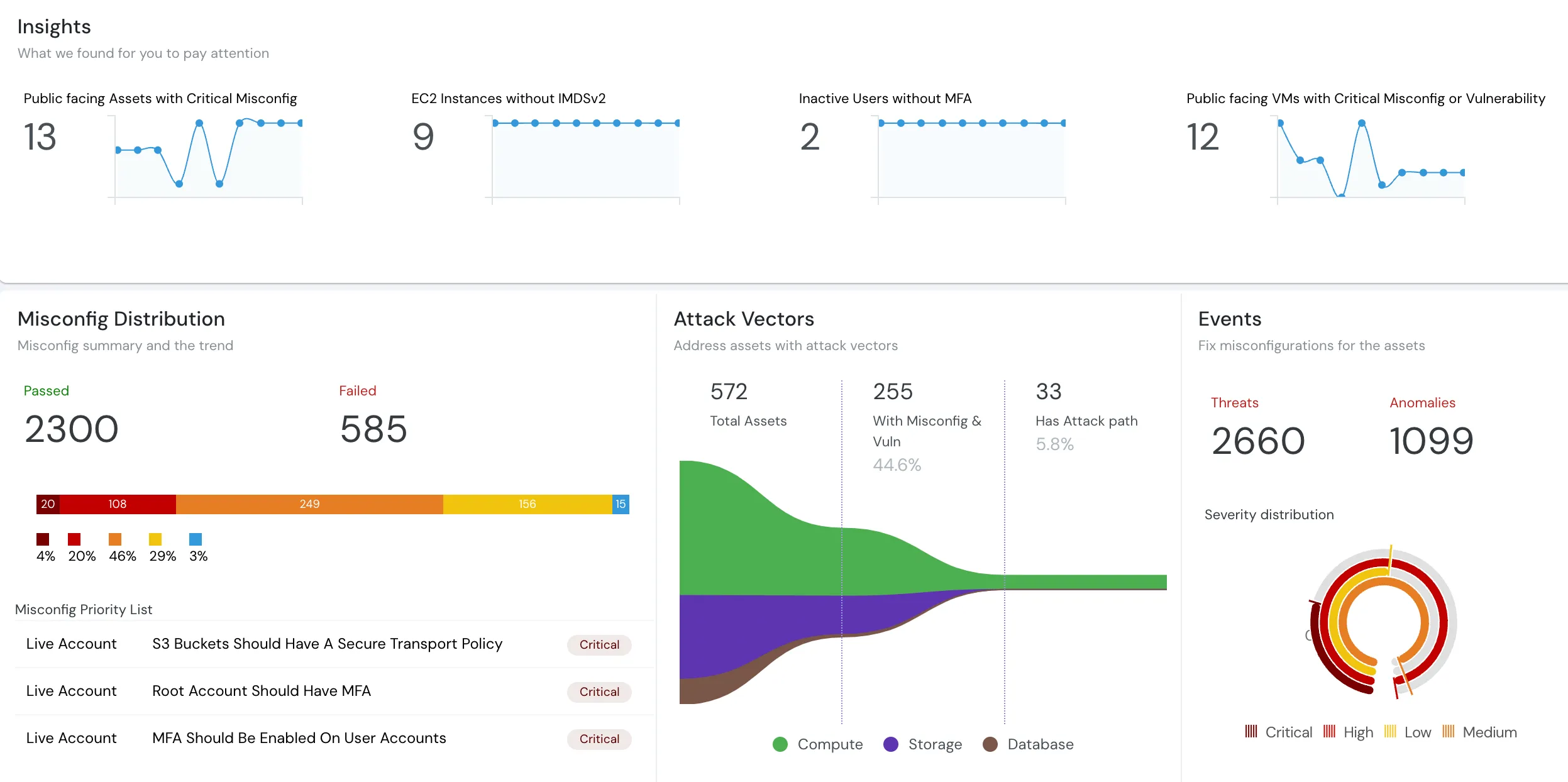
MFA Should Be Enabled On User Accounts
MFA must be enabled on user accounts. AWS recommends that you configure multi-factor authentication (MFA) to help protect your AWS resources.
User Account Access keys Should Be Rotated
The access keys should rotated periodically.
User Account Certificates Should Be Rotated
The certificates should be rotated periodically.
Inactive User Account Access keys Should Be Dropped
Inactive access keys should be dropped.
User Console Access Inactive
Users who are infrequent or do not need access to console, their account access should be cleared off.
User Account Service Inactivity
Checks inactivity of any user on a service. Those priviledges should be removed for better security posture.
Users Should Not Have Inline Policies
IAM users should not have Inline policies. It is recommended that IAM policies be applied directly to groups and roles but not users.
User Account Should Not Have Multiple Access Keys
Multiple access keys for the same user should be avoided. There should be just 1 access key per user account.
Inactive Roles Should Be Removed
Inactive roles should be cleaned up.
Role Service Inactivity
Roles which have access to services but have not used in past several days should be looked into and cleaned up.
Roles Should Not Have Inline Policies
Role should not have inline policies attached to them.
Groups Without Users Should Be Removed
Empty groups should be cleaned up and should not linger around.
ELB Certificates Should Be Rotated
Ensures that you rotate your certificate before the set configurable days.
Complex Password Policy Should Be Present
Password policy should be complex enough so that users can set passwords which are not easy to guess and crack.
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedCLOUDANIX
Insights from Cloudanix
Explore guides, checklists, and blogs that simplify cloud security and help you secure your infrastructure.
Case Studies
Real-world success stories where Cloudanix helped organizations secure their cloud infrastructure. Watch how we made a d...
What is CSPM?
Understand what Cloud Security Posture Management (CSPM) is and how it automates security and compliance across cloud en...
CASB, CSPM, SIEM: Cloud Security Essentials
Understand how CASB, CSPM, and SIEM work together to enhance your cloud security posture and ensure better governance.
What is Cloud Audit?
In-depth assessment of cloud environment for security, compliance, and optimization. Identify vulnerabilities, ensure da...
Top 10 Challenges of CSPM
Cloud environments are getting more complex and dynamic day by day, making it difficult to gain complete visibility into...
Cloudanix docs
Cloudanix offers you a single dashboard to secure your workloads. Learn how to set up Cloudanix for your cloud platform ...
Changelog
A complete history of changes, improvements, and fixes for Cloudanix. Subscribe to get notified about the latest updates...
