You’ve likely invested in Cloud Security Posture Management (CSPM) tools. These solutions promised to bring order to your cloud security, helping you identify misconfigurations and enforce compliance. But if you’re like many organizations actively migrating workloads and embracing cloud-native technologies, you might find yourself asking: “Is this truly enough for our dynamic, containerized environments?”
The landscape of cloud adoption has dramatically shifted. We’ve moved beyond simple virtual machines to highly complex, ephemeral containerized workloads running on orchestration platforms like Kubernetes, specifically EKS. This evolution introduces a new breed of security challenges that traditional, compliance-focused CSPM often struggles to address.
There’s a growing sentiment, what some might call “CSPM fatigue,” where organizations, having seen many CSPM products, are now simply “not amazed”. This often stems from these tools focusing predominantly on static, surface-level compliance checks rather than providing deep, real-time workload protection for the dynamic realities of modern cloud.
For today’s cloud environments, the real security imperative lies in robust container security and real-time event visibility. After speaking with hundreds of companies, we discovered that these are the capabilities that truly help you understand and mitigate risk in dynamic, rapidly changing infrastructures.
The Blind Spots of “Traditional” CSPM in Modern Clouds
While traditional CSPM has its place, it often operates with significant blind spots when confronted with the pace and complexity of modern, containerized cloud environments.
Traditional CSPM excels at scanning static configurations: S3 bucket policies, security group rules, IAM roles, and network ACLs. It’s great for foundational hygiene checks. However, modern cloud environments are inherently dynamic. Workloads consist of ephemeral containers that spin up and down in seconds, leveraging auto-scaling groups and continuous deployments. Traditional CSPM, often reliant on periodic scans or batch processing of logs, struggles to keep pace with these rapid changes, creating significant delays between a security event occurring and its detection.
The most critical limitation is often the container blind spot. Containers introduce new layers to the stack—the image, the registry, the runtime, and the orchestration layer—that traditional CSPM, primarily focused on the underlying cloud infrastructure, doesn’t adequately cover all of them.
While the infrastructure might be compliant, security flaws within the container image or threats occurring at runtime (e.g., privilege escalation, malware execution, unauthorized processes) can go entirely undetected by a traditional CSPM.
This leads to a pervasive lack of real-time context. In a fast-moving cloud environment, a 12-hour or even an hourly delay in detecting a security event can be catastrophic. You need to know what’s happening now to respond effectively. An “open RDS alert” that a team was “not previously aware of” highlights exactly how crucial misconfigurations can be missed when relying solely on traditional methods.
Comprehensive Container Security
For organizations predominantly running EKS (Kubernetes) workloads, container security isn’t just a best practice; it’s a non-negotiable requirement. Containers demand a specialized, multi-layered approach to security.
Security for containers must span their entire lifecycle, from development to runtime:
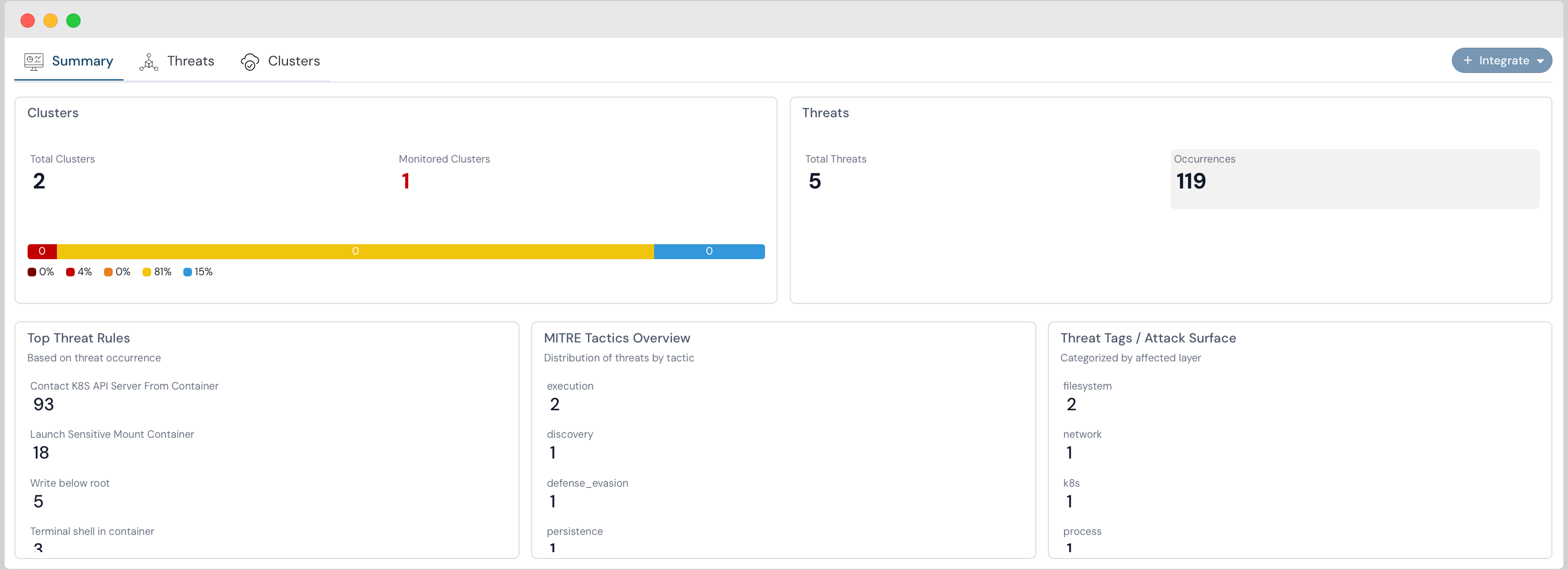
Image Scanning
The journey to secure containers begins long before deployment. Comprehensive vulnerability scanning of container images in registries and during CI/CD pipelines (like Jenkins) is crucial to identify and remediate known vulnerabilities before they even reach your production environment.
Runtime Protection
This is where many traditional security tools fall short. You need deep visibility and protection for what’s happening inside the running container. This includes detecting and preventing anomalous behavior, unauthorized process execution, privilege escalation attempts, and command injection attacks. It’s about protecting the active workload, not just its initial configuration.
Kubernetes-Native Security
Protecting containers necessitates understanding the Kubernetes orchestration layer itself. This involves securing the Kubernetes control plane, enforcing network policies to segment container traffic, and ensuring proper pod security standards. It’s about gaining visibility into cluster-wide events and potential misconfigurations specific to Kubernetes constructs.
Vulnerability Management & Remediation
Beyond merely finding vulnerabilities, a robust container security solution provides actionable insights for remediation. It allows for the customization of severity for misconfigurations, enabling teams to prioritize and fix the most critical issues first.
Network Visibility within Containers
Understanding traffic flow between containers and pods, as well as ingress/egress, is critical for detecting lateral movement, anomalous communication, and potential exploitation pathways.
For a security team, ensuring comprehensive container security means protecting the very core of their modern, cloud-native applications and preventing real-world exploitation.
The Power of Real-time Events and Deep Risk Visibility
In dynamic cloud environments, real-time event visibility is not just a feature; it’s a game-changer for effective security.
The critical insight from “real-time events” lies in enabling rapid detection and response. In the cloud, every second counts. Real-time monitoring means immediate alerts on critical misconfigurations, suspicious activities, or active threats, allowing for rapid incident response before small issues escalate. This moves organizations beyond reactive, delayed responses to proactive threat mitigation.
Beyond just simple alerts, a powerful platform provides contextual alerts. It’s not just about notifying you that “something is wrong,” but providing the precise details: “What’s wrong, where it is located, why it matters, and how to fix it.” This enables a “30k ft view of the risk with ability to dig deeper”, allowing security teams to quickly understand the true impact and prioritize their efforts effectively.
Real-time monitoring can even surface issues that periodic scans might entirely miss, or that teams were “not previously aware of”, such as an open RDS instance. This includes the ability to detect and flag anomalies by learning normal behavior and flagging deviations.
For security operations, this level of visibility translates to actionable findings. Alerts can be integrated into existing SIEM solutions via Webhooks, streamlining the response process. It provides clear guidance for triaging and remediation, allowing security teams to efficiently address critical and high misconfigurations first.
Furthermore, it offers a crucial “visibility of what is happening” to teams that have the “democracy” to create their own infrastructure, fostering shared responsibility while maintaining centralized oversight. This continuous audit trail also significantly aids in demonstrating compliance with stringent standards like FedRAMP, CIS, ISO27001, HIPAA, and GDPR.
Unlocking True Cloud Security: A Holistic Platform Approach
Moving “beyond traditional CSPM” requires a cloud security platform that seamlessly integrates these critical capabilities and provides you with a robust security solution.
Cloudanix provides comprehensive container security, offering end-to-end protection from scanning images in your registries (like those used in Jenkins CI ) to monitoring runtime behavior within your EKS clusters. This ensures your primary workloads are protected at every layer of the stack.
Our real-time event monitoring and deep risk visibility capabilities provide the immediate insights you need to stay ahead of threats. Cloudanix actively surfaces previously unknown risks—such as the “open RDS alert” that a customer was unaware of—and offers that crucial “30k ft view of the risk with ability to dig deeper”. This also extends to detecting exposed ports on VMs and network-based vulnerabilities.
Our findings are not just alerts; they provide the very context required for effective triaging and remediation, allowing your security team to prioritize and address critical and high misconfigurations efficiently. We support seamless integration via Webhooks to your existing SIEM for streamlined security operations.
Designed for flexibility, our platform connects at the subscription level (e.g., Azure subscriptions, AWS accounts) and can connect multiple subscriptions at a time via OIDC connection, offering broad coverage without being overly intrusive.
We also support specific use cases, like notifying of DNS entry changes in Cloudflare. Our commitment to continuous improvement means we are actively working on features like date-based event filtering and robust test cases for host and Kubernetes security, including feedback on Suricata.
The outcome is a truly secure, compliant, and agile cloud environment that gives you confidence in your modern workloads, even as they scale and evolve across platforms like DigitalOcean and Azure.
Gain True Visibility Over Your Cloud Workloads
Traditional CSPM serves as a foundational step, but for the dynamic realities of modern, containerized cloud workloads, specialized container security and real-time event visibility are paramount. This strategic shift moves you from merely checking compliance boxes to proactive, deep risk management.
A holistic cloud security platform is essential for uncovering hidden risks, securing your most dynamic assets, and providing the immediate insights necessary to protect your business. Are you ready to move beyond basic CSPM and gain true visibility and control over your containerized workloads? Discover how Cloudanix can deliver comprehensive container security and real-time event monitoring for your modern cloud environment.
