“Code to Cloud Security” is a holistic approach that integrates security throughout the software lifecycle, from initial code development to cloud deployment and runtime. It emphasizes embedding security practices like secure coding, SAST/DAST, IaC security, and cloud configuration management. This strategy aims to proactively mitigate vulnerabilities, enhance resilience, and ensure compliance in modern cloud-native environments, shifting security left and fostering collaboration between development, security, and operations teams.
A “Code to Cloud” approach fundamentally shifts security left, embedding it early in development. This proactive stance catches vulnerabilities before deployment, reducing risks and costs associated with later remediation in the cloud. It fosters a shared responsibility model, integrating security into every stage, leading to more resilient, compliant, and ultimately, more secure cloud-native applications and infrastructure.
What are the different methods used in the Code to Cloud Security approach?
A robust ‘Code to Cloud Security’ strategy hinges on the consistent and comprehensive application of proven methodologies throughout the software development and deployment lifecycle. For senior security leaders and mid-level professionals, understanding and implementing these methods is paramount to building secure and resilient cloud-native environments.
The following outlines key techniques that, when integrated effectively, proactively mitigate risks and establish a strong security posture from the very first line of code to the operational cloud.
- Secure Coding Practices: This foundational method focuses on writing code that inherently minimizes security vulnerabilities. It involves educating developers on common pitfalls (e.g., OWASP Top 10) and establishing coding standards that emphasize security.
- Static Application Security Testing (SAST): SAST tools analyze source code, bytecode, or binary code without executing the application. They identify potential vulnerabilities by examining code patterns against a predefined set of rules.
- Dynamic Application Security Testing (DAST): DAST tools test a running application by simulating attacks from an external perspective. They interact with the application’s interfaces (e.g., web pages, APIs) to identify vulnerabilities.
- Infrastructure as Code (IaC) Security: IaC involves managing and provisioning infrastructure using code (e.g., Terraform, CloudFormation). IaC security focuses on ensuring that these code definitions are secure and don’t introduce misconfigurations.
- Container and Kubernetes Security: With the rise of containerization, securing containers and orchestration platforms like Kubernetes is crucial. This involves securing container images, the container runtime, and the orchestration layer.
- Cloud Configuration Security: Cloud environments offer numerous configurable services. Cloud configuration security focuses on properly configuring these services (e.g., IAM, storage, networking) to prevent misconfigurations that attackers can exploit.
- DevSecOps: DevSecOps is not a specific tool but a philosophy and set of practices that integrate security throughout the entire software development lifecycle (SDLC), fostering collaboration between development, security, and operations teams.
- Software Supply Chain Security: Modern software relies on numerous third-party libraries, dependencies, and tools. Supply chain security focuses on ensuring the integrity and security of these external components.
- Container Runtime Security: Runtime security focuses on protecting applications and infrastructure while they are actively running in the cloud. This involves monitoring for threats, detecting anomalies, and responding to security incidents in real-time.
By implementing a combination of these proven methods, organizations can build a robust “Code to Cloud Security” strategy that significantly reduces their risk posture in modern cloud-native environments. The specific methods and their implementation will vary based on the organization’s specific needs, technologies, and risk tolerance.
What is the need for code to cloud security?
In today’s rapidly evolving digital landscape, the adoption of cloud-native architectures necessitates a fundamental shift in how we approach security. The traditional, perimeter-centric model is no longer sufficient. A comprehensive ‘Code to Cloud Security’ strategy is not merely advisable; it’s a critical imperative driven by a confluence of factors that demand a holistic and integrated approach to protecting our applications and infrastructure.
Expanding attack surface
Modern applications are increasingly complex, distributed across cloud environments, and built using numerous microservices, containers, and third-party dependencies. This expanded attack surface presents more opportunities for vulnerabilities to be introduced and exploited.
Traditional perimeter-based security is insufficient to protect these dynamic and distributed environments. A “Code to Cloud” approach addresses security at each layer and stage, reducing the overall attack surface.
Shift left imperative
Identifying and fixing security vulnerabilities earlier in the development lifecycle (shifting security “left”) is significantly more cost-effective and less disruptive than addressing them in production.
Discovering a critical vulnerability in a live cloud environment can lead to significant downtime, data breaches, and reputational damage, all of which are far more expensive to remediate than fixing a coding flaw early on.
Cloud-native complexity
Cloud environments introduce their own set of complexities, including intricate configurations, diverse services, and the ephemeral nature of resources. Misconfigurations are a leading cause of cloud security incidents.
A “Code to Cloud” approach extends security considerations to infrastructure as code and cloud service configurations, ensuring that the underlying environment is as secure as the application itself.
Velocity of development
Modern development practices emphasize speed and agility (DevOps). Security needs to be integrated seamlessly into these fast-paced workflows without becoming a bottleneck.
Traditional security gates can slow down development cycles. “Code to Cloud” promotes automation of security testing and integration into CI/CD pipelines, enabling security to keep pace with development velocity.
Shared responsibility model
Cloud providers operate under a shared responsibility model, where they secure the underlying infrastructure, but the customer is responsible for securing what they put in the cloud (applications, data, configurations).
Organizations need a comprehensive strategy that covers their responsibilities within the shared model. “Code to Cloud” ensures that security is addressed throughout the application and infrastructure they deploy and manage in the cloud.
Compliance and regulatory requirements
Many industries are subject to strict compliance regulations (e.g., GDPR, HIPAA, PCI DSS) that mandate specific security controls for applications and data, regardless of where they are hosted.
A “Code to Cloud” approach helps organizations build and deploy applications and infrastructure in a way that aligns with these regulatory requirements, ensuring continuous compliance.
Software supply chain risks
Modern applications rely heavily on open-source libraries and third-party dependencies, which can introduce vulnerabilities if not properly managed and secured.
“Code to Cloud” extends security considerations to the software supply chain, ensuring the integrity and security of all components used in the application and its deployment.
Real-time threat detection
The threat landscape is constantly evolving, with new attack techniques and vulnerabilities emerging regularly. Organizations need to be able to detect and respond to threats in real-time in their cloud environments.
“Code to Cloud” includes runtime security measures that monitor and protect applications and infrastructure in the cloud, enabling timely detection and response to potential security incidents.
In essence, a “Code to Cloud Security” approach is not just a best practice; it’s a necessity for organizations operating in today’s complex and dynamic cloud-native landscape. It provides a holistic framework for building and maintaining secure applications and infrastructure from the ground up, reducing risk, ensuring compliance, and fostering a more resilient security posture.
What are the 4 key components of code to cloud security?
Let’s break down the “Code to Cloud Security” approach into its four most crucial key components that senior security leaders and mid-level professionals should prioritize:
Secure Development Lifecycle (SDL) Integration
This foundational component emphasizes embedding security practices and considerations into every phase of the software development lifecycle (SDLC), from planning and design to coding, testing, and deployment. It’s about “shifting left” and making security an integral part of how software is built, not an afterthought.
By integrating security early, organizations can identify and remediate vulnerabilities when they are cheapest and easiest to fix. This proactive approach reduces the likelihood of security flaws making their way into production cloud environments, minimizing risk and potential for costly breaches or rework. It fosters a security-conscious culture within development teams.
Infrastructure as Code (IaC) Security & Cloud Configuration Management
This component focuses on securing the underlying infrastructure that supports cloud applications. With the prevalence of IaC tools, security must be built into the infrastructure provisioning and management processes. Similarly, continuous monitoring and enforcement of secure cloud configurations are vital to prevent misconfigurations that can expose critical resources.
In cloud environments, insecure infrastructure configurations are a leading cause of security incidents. By treating infrastructure as code and applying security principles to its definition and deployment, organizations can prevent common pitfalls like overly permissive access controls or exposed services. Consistent cloud configuration management ensures ongoing adherence to security baselines.
Automated security testing and continuous monitoring
This component leverages automation to integrate security testing throughout the development and deployment pipelines (CI/CD). This includes SAST, DAST, container scanning, and dependency checking. Furthermore, continuous monitoring of running applications and infrastructure in the cloud is essential for detecting and responding to threats in real-time.
The speed and scale of modern cloud deployments necessitate automation. Manual security checks cannot keep pace. Automated testing ensures frequent and consistent vulnerability assessments, while continuous monitoring provides visibility into the runtime environment, enabling rapid detection of and response to anomalies or attacks.
Identity and Access Management across the entire spectrum
Robust IAM is critical at every stage, from developers accessing code repositories and CI/CD pipelines to applications interacting with cloud services and end-users accessing the deployed application. This includes principles like least privilege, multi-factor authentication (MFA), and consistent identity governance across development, deployment, and runtime environments.
Weak or misconfigured IAM is a primary attack vector in cloud environments. By implementing strong identity controls and consistently enforcing the principle of least privilege across the entire “code to cloud” journey, organizations can significantly limit the potential impact of compromised accounts or insider threats. This ensures that only authorized entities have the necessary access at each stage.
These four components – Secure Development Lifecycle Integration, IaC Security & Cloud Configuration Management, Automated Security Testing & Continuous Monitoring, and comprehensive IAM – form the bedrock of an effective “Code to Cloud Security” strategy. Prioritizing these areas will provide the most significant impact in building and maintaining secure cloud-native applications and infrastructure.
What are the key features to look for in cloud security tools for code protection?
When selecting a cloud security tool with a strong focus on “code security,” senior security leaders and mid-level professionals should look for the following key features:
- Broad Language and Framework Support: The tool should support a wide range of programming languages, frameworks, and infrastructure-as-code (IaC) languages commonly used in your development environment (e.g., Java, Python, JavaScript, Go, C#, as well as Terraform, CloudFormation, ARM templates, Kubernetes YAML). Comprehensive coverage ensures that vulnerabilities across your entire application stack and infrastructure definitions are identified. Limited support can create blind spots and leave significant portions of your codebase unprotected.
- Accurate and Actionable Vulnerability Detection: The Static Application Security Testing (SAST) capabilities should go beyond simple pattern matching. Look for tools that offer high accuracy with low false positive rates, provide detailed explanations of identified vulnerabilities, and offer clear remediation guidance with code examples. High false positive rates can overwhelm developers and security teams, leading to alert fatigue and missed critical issues. Actionable insights and remediation advice empower developers to fix vulnerabilities quickly and effectively.
- Integration with the Software Development Lifecycle (SDLC): Seamless integration with your existing development tools and workflows is crucial. This includes IDE plugins for real-time feedback, integration with source code management (SCM) systems (e.g., Git), and integration with CI/CD pipelines for automated security checks. Tight integration ensures that security checks are performed early and often without disrupting the development process. Automated checks in the CI/CD pipeline prevent vulnerable code from being deployed to cloud environments.
- Infrasrtucture as code scanning: The tool should be capable of scanning IaC templates for misconfigurations and security vulnerabilities before infrastructure is provisioned in the cloud. This includes checks for overly permissive security groups, exposed storage buckets, and insecure resource configurations. Securing IaC prevents insecure cloud deployments, reducing the risk of misconfigurations that can lead to breaches. Early detection in IaC is far more efficient than remediating issues in live cloud environments.
- SCA (Software Composition Analysis): SCA capabilities identify open-source components and third-party libraries used in your code and flag known vulnerabilities and license risks associated with them. It should provide information on vulnerable dependencies and suggest updated, secure versions. Modern applications rely heavily on external dependencies. SCA helps manage the risks associated with these components, ensuring that known vulnerabilities in your supply chain are addressed.
- Container security scanning: For cloud-native applications using containers, the tool should be able to scan container images for vulnerabilities at various stages of the lifecycle – from build to registry to runtime. This includes identifying OS package vulnerabilities and application-level flaws within the container. Containers introduce a new layer of complexity. Scanning container images ensures that vulnerable software doesn’t make its way into your cloud deployments.
- Policy Enforcement and Compliance Checks: The tool should allow you to define and enforce security policies and compliance rules relevant to your organization and industry regulations. It should provide reports and alerts when code or configurations violate these policies. Policy enforcement ensures that development adheres to your security standards and helps maintain compliance with relevant regulations.
- Reporting, Dashboards, and Analytics: Comprehensive reporting and intuitive dashboards provide visibility into the security posture of your code and cloud configurations. Look for features that allow you to track trends, prioritize risks, and measure the effectiveness of your security efforts. Visibility is key to understanding and managing risk. Effective reporting helps security teams communicate findings to developers and leadership, driving informed decision-making.
- Integration with Other Security Tools: The tool should ideally integrate with other security tools in your ecosystem, such as vulnerability management platforms, SIEM systems, and ticketing systems, to provide a holistic view of your security landscape and streamline workflows. Integration improves collaboration between security and development teams and enables a more coordinated and efficient security response.
By carefully evaluating cloud security tools based on these key features, organizations can select a solution that effectively addresses code security risks throughout their “code to cloud” journey, leading to more secure and resilient cloud-native applications.
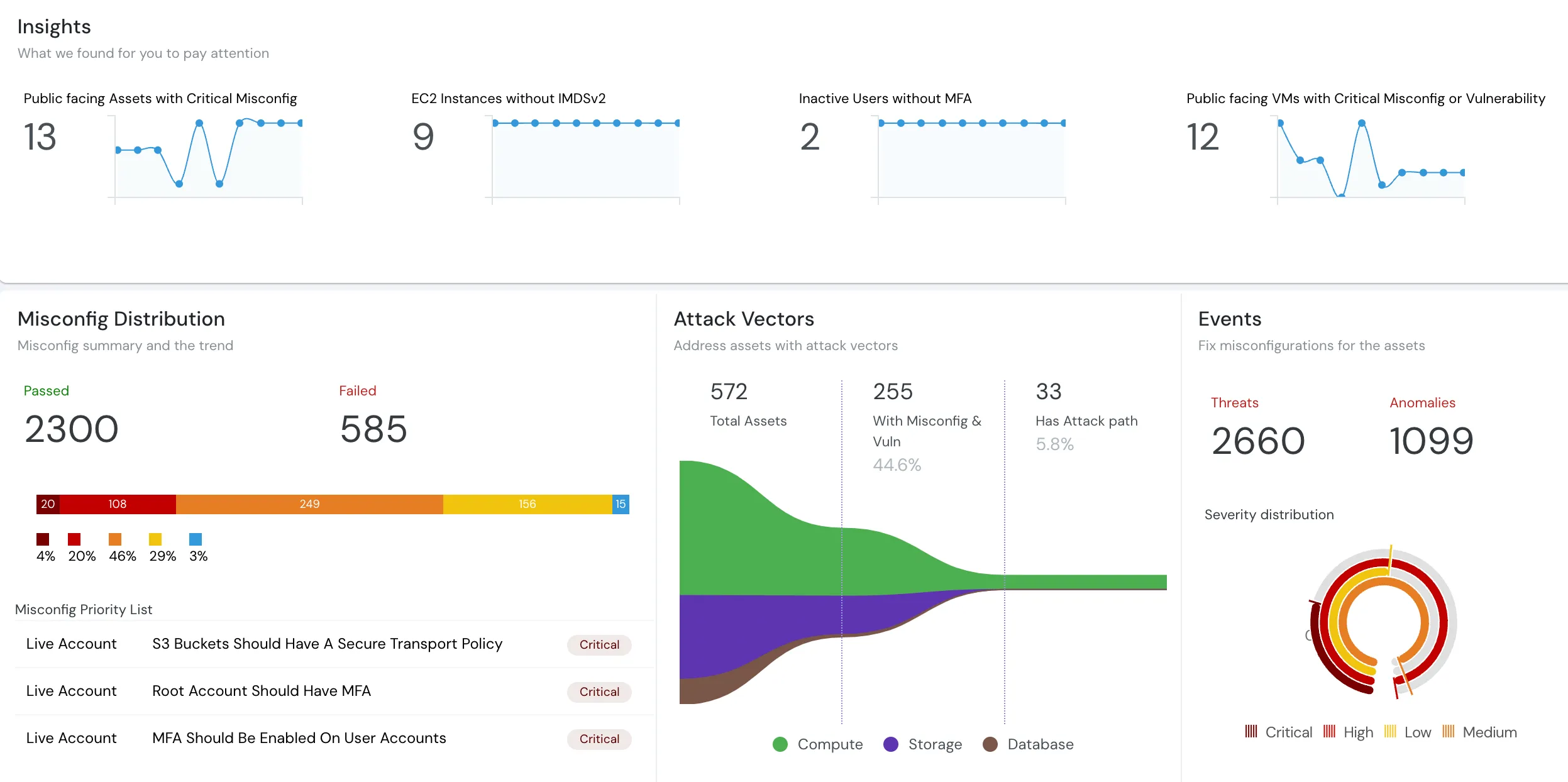
How can Cloudanix help you with Code to Cloud Security?
Cloudanix is a multi-surface attack management platform across Code, CI/ CD, Cloud, Workload and Identity. Get single dashboard with co-related security findings instead of using 5-6 disjointed and point security tools. In a world where threats can emerge from anywhere, Cloudanix stands as your ultimate defense, seamlessly integrating security across Code, Cloud, Identity, and Workloads to anticipate and block multi-surface attacks. Discover unparalleled protection that evolves with your digital landscape.
