Identity and Access Management - The New Edge of Security
The network is not the perimeter. Identity is the perimeter.
Identity and Access Management (IAM) has traditionally been considered one of the boring parts of security. But with the rise in the field of cloud computing, IAM has become increasingly important and is now referred to as “the new edge of security.”
Earlier, network security controls such as firewalls and IP restrictions were the primary means of protecting systems and data. However, cloud environments limit visibility and control over the networking layer, making traditional perimeter defenses less effective.
Cloud-based models allow for broader and more distributed access, increasing the attack surface and complicating access control.
This is where IAM plays a critical role. IAM provides a centralized way to manage access to resources, whether those resources are on-premises or in the cloud. By implementing IAM, organizations can define and enforce who gets access to what, and under what conditions.
Why IAM is Crucial in the Cloud
Highlights from a ScaleToZero podcast episode featuring Chad:
- It is necessary to maintain control as applications and data migrate to the cloud.
- Cloud platforms offer limited built-in security controls, making IAM essential.
- IAM simplifies compliance by offering centralized access management.
- IAM reduces the risk of breaches by ensuring only authorized access to sensitive data.
If you are moving to the cloud or already operate in the cloud, a strong IAM strategy is essential.
Tips for Implementing a Strong IAM Program
- Implement IAM JIT (Just-In-Time): Team members should not have standing access. Access should be granted only when required.
- Define a Clear IAM Policy: Create strict access policies that are role-based and well-documented.
- Use Strong Authentication: Enforce MFA, hardware tokens like Yubikey, or access tokens.
- Monitor User Activity: Set up logging and alerts to detect suspicious behavior.
- Review IAM Policies Regularly: Ensure policies evolve with the organization’s needs.
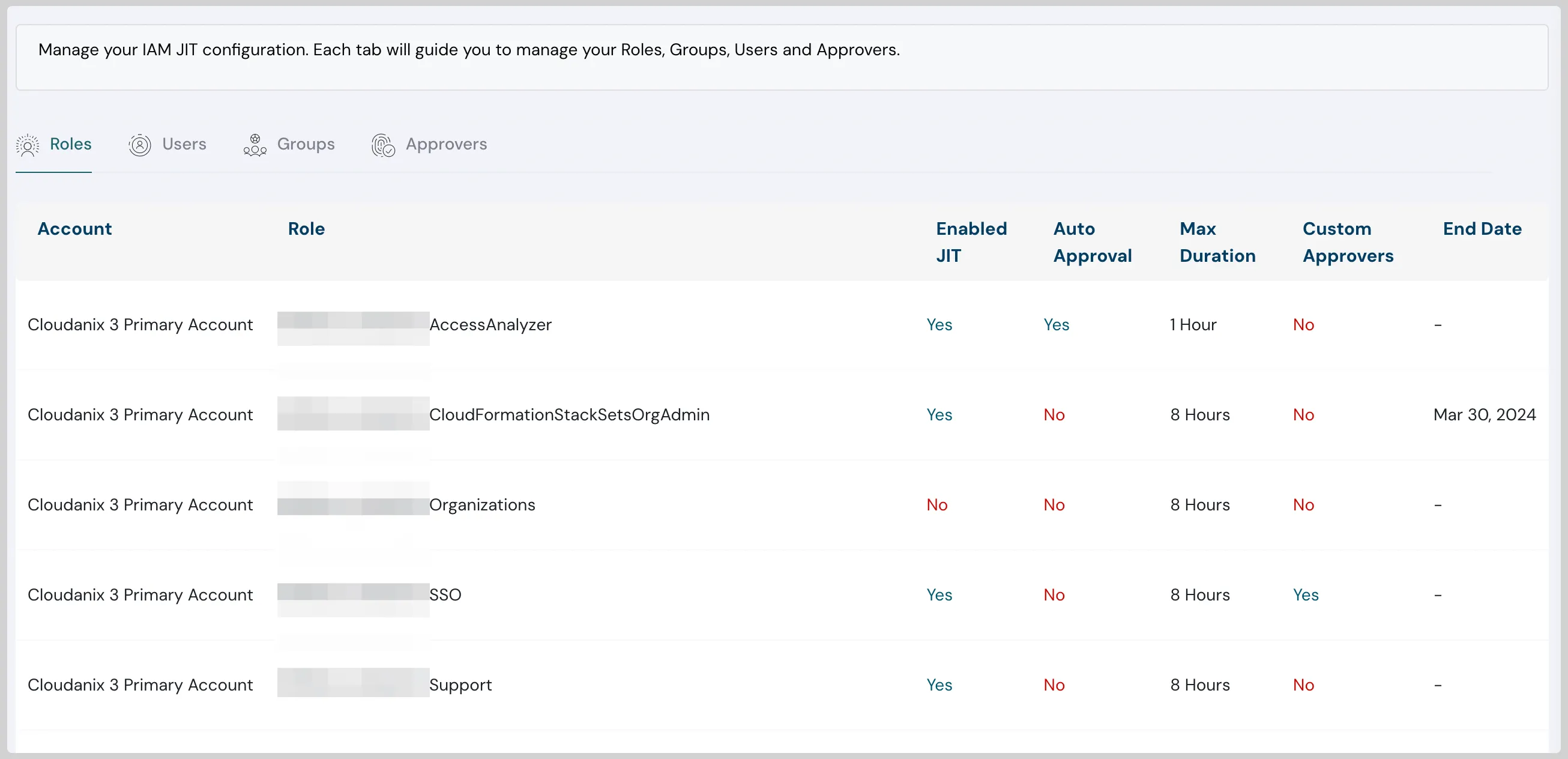
Cloudanix IAM JIT lets your team request limited-time access to permissions in just a few clicks, with full traceability and control.
How Has IAM Evolved in the Last Five Years?
IAM is no longer just about assigning permissions. Here’s how it’s changing:
- Proactive Security: Instead of reacting to incidents, organizations now anticipate and prevent IAM risks.
- IAM Automation: Tasks like provisioning and de-provisioning users are increasingly automated.
- IAM Security Tools: More tools are being used to detect and respond to IAM threats.
- Cloud IAM Adoption: Organizations need fine-grained control over access to cloud resources.
- Complex IAM Environments: As businesses scale, IAM must balance security with usability.
- Auditor Visibility with IAM JIT: IAM JIT helps auditors verify access logs, durations, and actions.
Communicating IAM’s Business Value to Stakeholders
Security teams must align IAM efforts with business outcomes to gain stakeholder support:
- Align with Business Goals: Show how IAM supports compliance, reduces fraud, and boosts innovation.
- Quantify the Impact: Highlight reductions in security incidents or operational costs.
- Use Simple Language: Avoid jargon when explaining IAM to non-technical audiences.
- Tailor Messages: A CFO, CTO, and CIO each care about different aspects of IAM.
Practical Ways to Communicate IAM Value:
- Build a business case that outlines cost, benefit, and risk reduction.
- Use dashboards that show IAM metrics: unauthorized access attempts, provisioning speed, etc.
- Share success stories of IAM helping achieve compliance or preventing incidents.
- Integrate IAM with the broader security strategy.
- Involve all departments in IAM policy development and training.
- Continually assess and optimize IAM performance.
IAM JIT and Cloudanix
Cloudanix IAM Just-In-Time (JIT) ensures temporary, auditable, and secure access across your cloud platforms. Teams gain the right permissions at the right time with clear expiration and audit trails.
Additional Resources
- IAM JIT Integration with AWS IAM Identity Center
- Right-Sizing IAM Permissions & Reviews with Cloudanix
- Why Understanding IAM is Important
Remember: In the cloud, the network is not the perimeter. Identity is.
