NIST CSF Core Functions and Cloud Security
NIST CSF 2.0 organizes cybersecurity activities into six core functions: Govern (organizational context and risk management), Identify (asset and risk understanding), Protect (safeguards implementation), Detect (threat and anomaly detection), Respond (incident response), and Recover (resilience and recovery planning).
Cloud environments using AWS, Azure, GCP, and OCI introduce unique cybersecurity challenges including shared responsibility, rapid configuration changes, ephemeral resources, and complex identity management. Cloudanix helps organizations implement NIST CSF functions across multi-cloud infrastructure through automated security monitoring, risk assessment, and continuous compliance.
Govern and Identify: Asset Discovery and Risk Management
NIST CSF's Govern function establishes cybersecurity governance, risk management strategy, and organizational context. The Identify function requires understanding organizational assets, risks, and vulnerabilities.
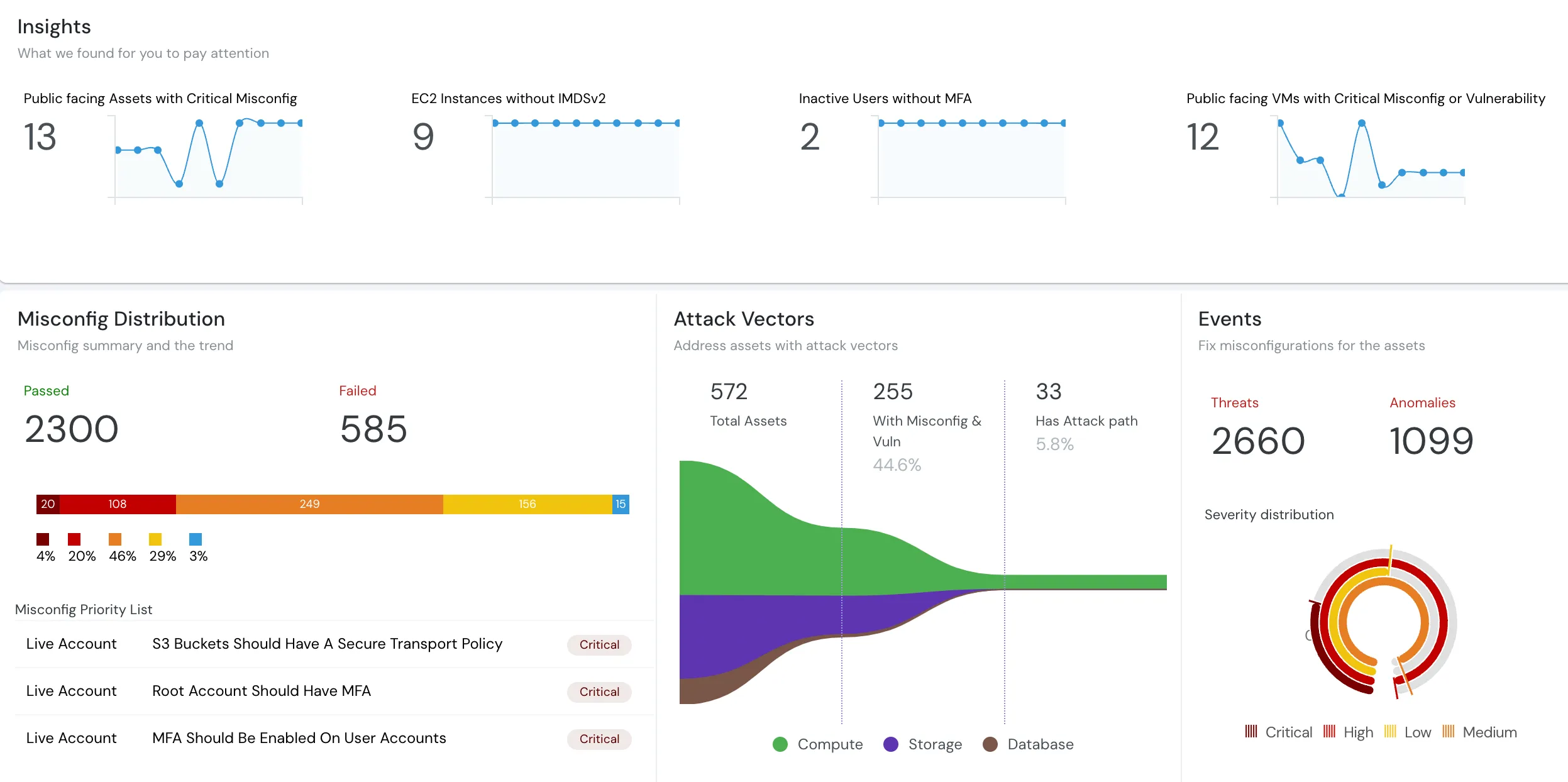
Cloudanix provides comprehensive asset discovery across AWS, Azure, GCP, and OCI environments, identifying all cloud resources including compute instances, databases, storage, network components, and identities. Continuous risk assessment evaluates security posture, identifies misconfigurations and vulnerabilities, prioritizes risks based on business impact, and supports CSF implementation tiers assessment.
Protect: Access Control and Identity Management
NIST CSF's Protect function includes access control (PR.AC) and identity management categories. The framework requires limiting access to authorized users, processes, and devices while managing identities and credentials.
Cloudanix's Just-In-Time (JIT) access implements time-bound privileged access across multi-cloud environments, supporting CSF PR.AC-4 (access permissions management) and PR.AC-6 (credential management). Comprehensive identity governance monitors both human and non-human identities including service accounts, API keys, and workload identities across AWS IAM, Azure AD, GCP IAM, and OCI IAM.
Detect: Continuous Monitoring and Anomaly Detection
NIST CSF's Detect function (DE.AE, DE.CM) requires continuous monitoring to identify cybersecurity events and anomalies. Organizations must implement security monitoring processes to detect unauthorized access, anomalous activities, and potential security incidents.
Cloudanix provides real-time security monitoring across cloud environments including Database Activity Monitoring (DAM) for AWS RDS, Azure SQL, Google Cloud SQL, and Oracle Cloud databases. Continuous monitoring detects misconfigurations, unusual access patterns, policy violations, and potential security incidents, providing the visibility required by CSF's Detect function.
Protect: Secure Configuration and Vulnerability Management
NIST CSF Protect function includes data security (PR.DS), protective technology (PR.PT), and maintenance (PR.MA) categories. Organizations must implement security controls including secure configurations, vulnerability management, and protection mechanisms.
Cloudanix continuously scans AWS, Azure, GCP, and OCI for security misconfigurations and vulnerabilities, maintains secure configuration baselines, detects deviations from approved settings, and provides workload security through vulnerability scanning and runtime protection. This supports CSF PR.IP-1 (baseline configurations) and PR.DS-6 (integrity checking mechanisms).
Respond and Recover: Incident Response and Resilience
NIST CSF's Respond function addresses incident response planning, communications, analysis, mitigation, and improvements. The Recover function focuses on resilience planning and recovery activities.
Cloudanix supports incident response through comprehensive audit logging, automated alerting on critical security events, evidence collection for incident analysis, and tracking of security findings and remediation. These capabilities help organizations implement CSF RS.AN (incident analysis), RS.MI (incident mitigation), and RC.RP (recovery planning) categories.
Software Supply Chain Security (CSF Supply Chain Risk Management)
NIST CSF 2.0 emphasizes supply chain risk management under the Govern function (GV.SC) and Identify function (ID.SC). Organizations must identify, assess, and manage cybersecurity risks within their supply chains including third-party software dependencies.
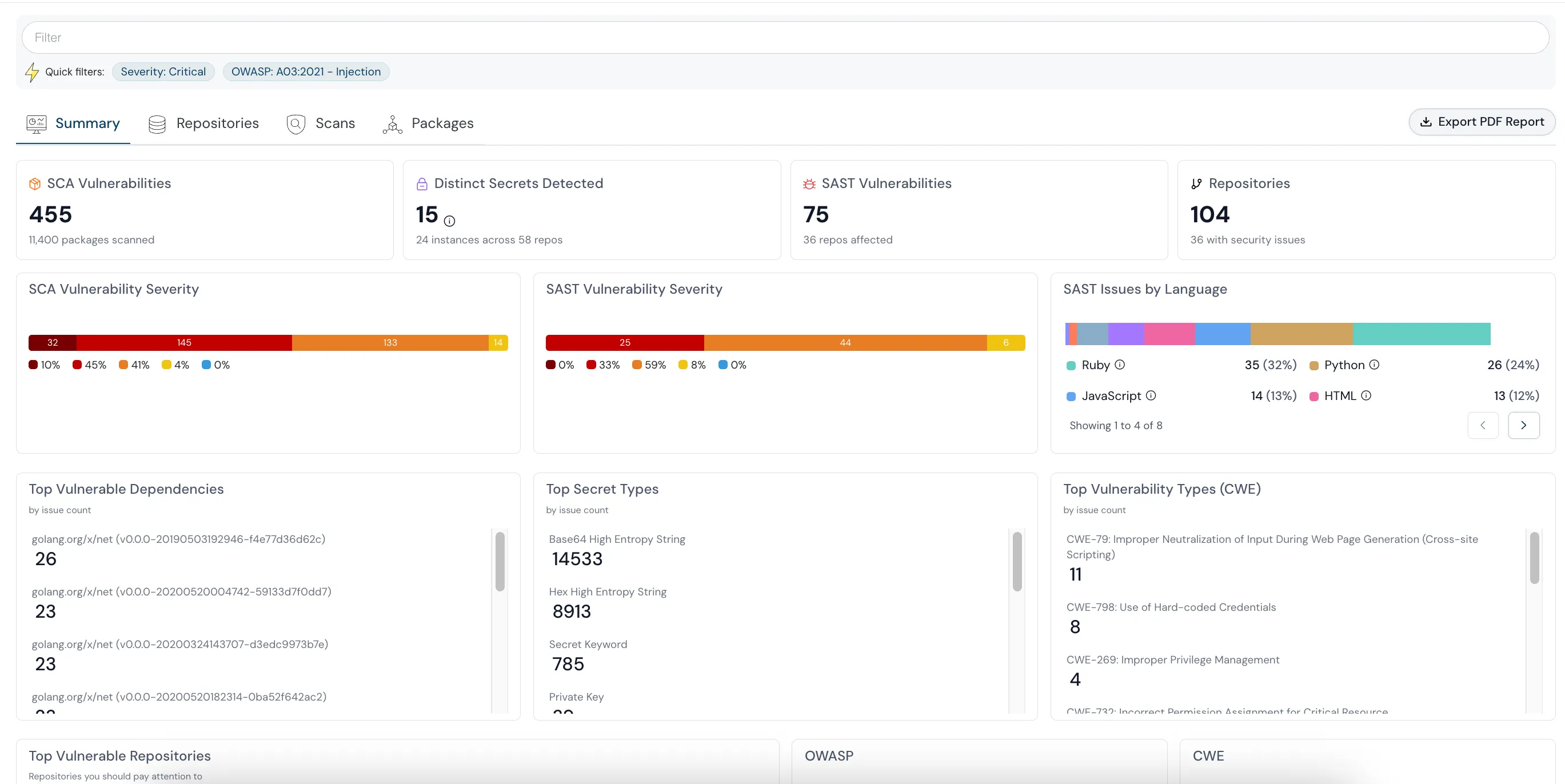
Cloudanix generates comprehensive Software Bill of Materials (SBOMs) for cloud workloads and containerized applications across AWS, Azure, GCP, and OCI. SBOM capabilities provide visibility into software components and dependencies, identify known vulnerabilities in third-party code, support supply chain risk assessment, and enable rapid response to supply chain security incidents — all critical for implementing CSF's supply chain risk management categories.