VM Vulnerabilities Prioritization, GitLab Cloud Support, and More
We’re excited to unveil a range of powerful updates designed to streamline your security workflow and empower you to focus on what matters most. This month we deliver to you enhanced VM vulnerability management, a revamped dashboard with an optimized layout, streamlined Google Cloud Builder integration, expanded GitLab security, and more.
Enhanced VM Vulnerability Management
Gain deeper insights into exploitability, patch-ability, fixability, and other critical factors to prioritize the most impactful vulnerabilities in your virtual machines.
Dashboard showing summary for number of vulnerabilities
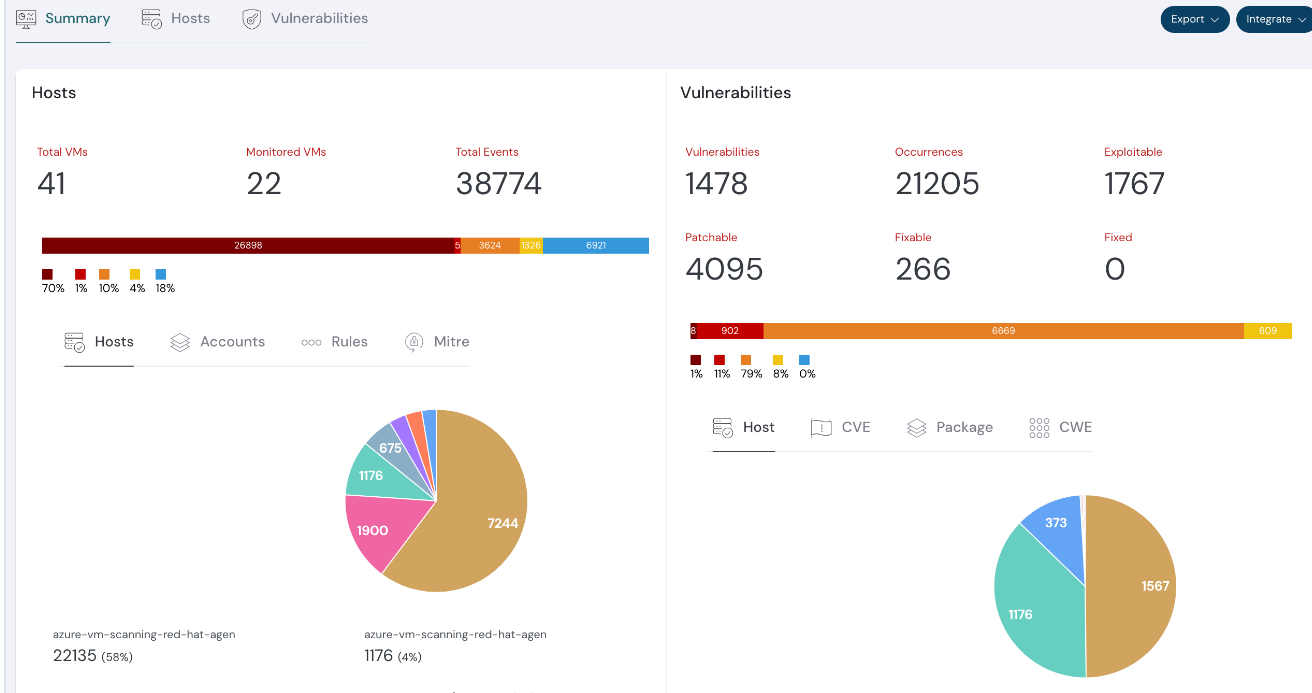
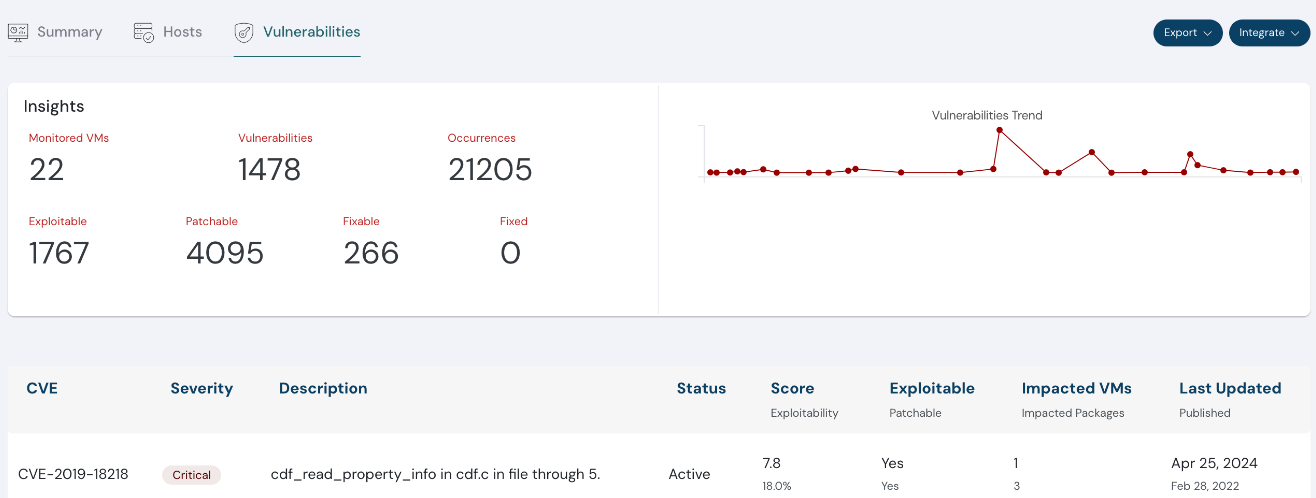
Overview of the number of vulnerabilities present and related details
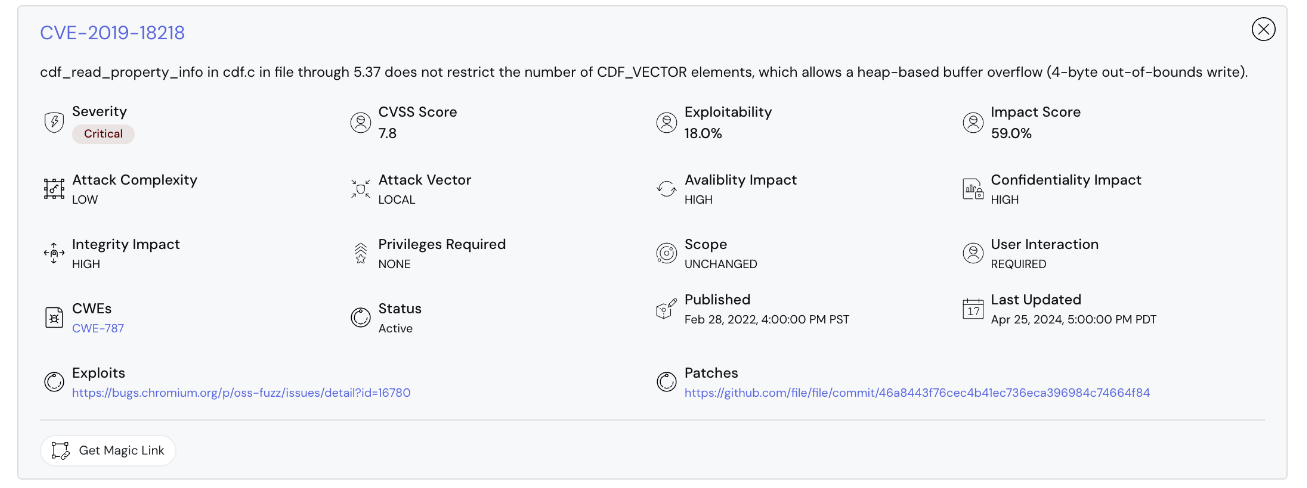
 Details of vulnerability including exploits and patches
Details of vulnerability including exploits and patches
Revamped Dashboard & Views
Navigate effortlessly through a redesigned dashboard, events, assets, and more. We’ve optimized the layout to highlight the most critical security findings, allowing you to make informed decisions at a glance.
 Updated dashboard for cloud misconfigurations
Updated dashboard for cloud misconfigurations
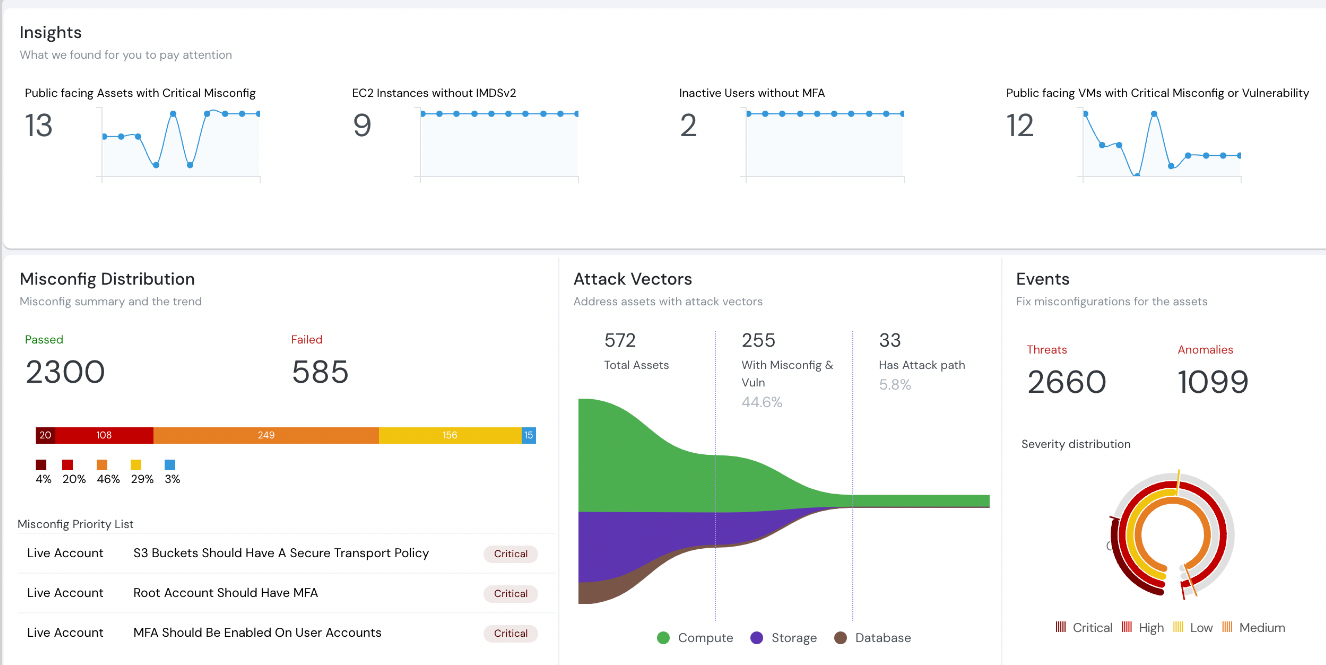 Dashboard: Events monitoring | CSPM tool
Dashboard: Events monitoring | CSPM tool
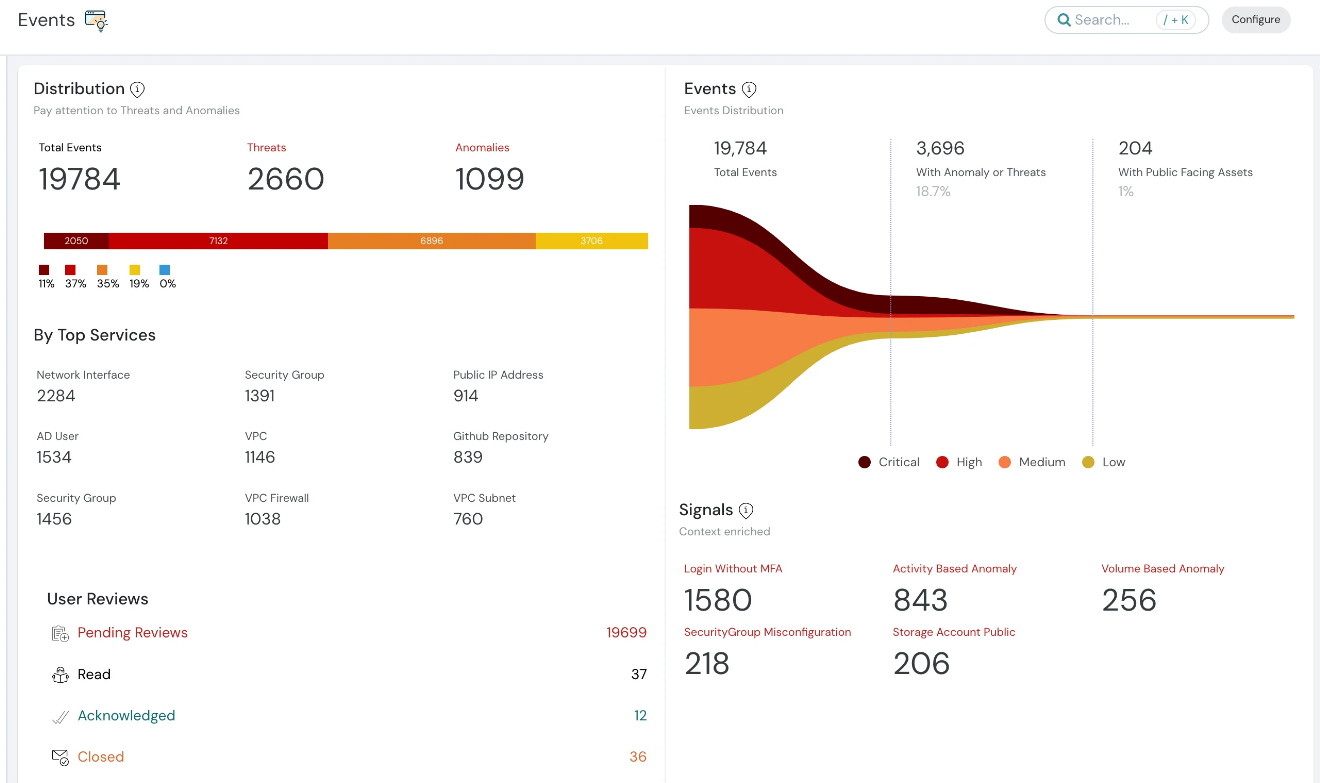 Dashboard: available assets and details
Dashboard: available assets and details
Streamlined Google Cloud Builder Integration
Integrate our Docker Image Vulnerability Scanning seamlessly into your Google Cloud Build pipeline. Findings are now displayed directly within the pipeline and the Cloudanix Console, ensuring a clear view of your container security posture.
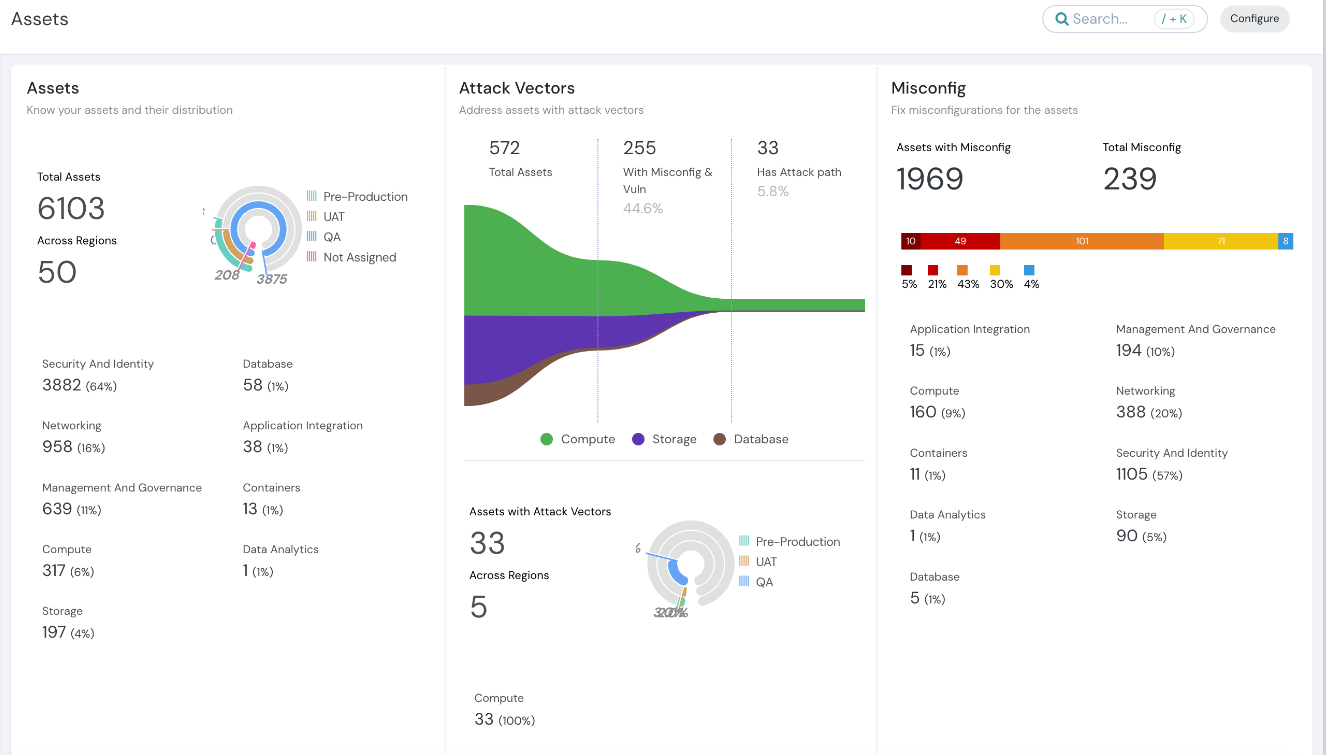 Findings displayed directly within the pipeline and Cloudanix Console
Findings displayed directly within the pipeline and Cloudanix Console
Expanded GitLab Security
For GitLab Cloud users, we’re introducing comprehensive Code Security support. Integrate your GitLab projects and repositories to leverage advanced Secrets and Static Analysis (SAST) scanning, fortifying your code from the ground up.
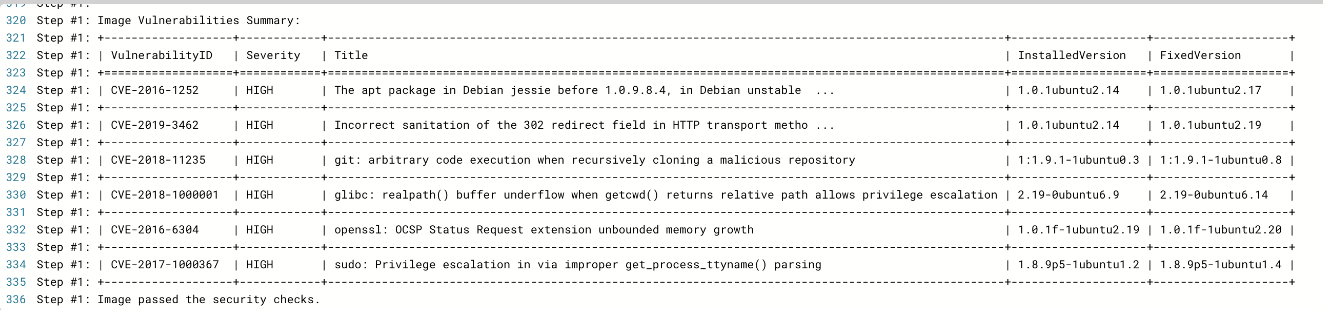 Introducing Code Security support for GitLab Cloud users
Introducing Code Security support for GitLab Cloud users
Cloudanix Blogs
- Unveiling Cloud Console Link Project
- Vulnerability Management & its Significance
- CI/CD Pipelines & Best Practices
- Platform Engineering and the Buzz Around It
Industry News
- Vulnerability Management and Prioritization
- Threat Modeling Encryption At Rest
- AWS Supports Pass Keys for MFA
- Phishing 2.0 & Evolution
- Subdomain Takeover Prevention
TODO:// is not an option for Cloud Security
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedBlog
Read More Posts
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Wednesday, Nov 05, 2025
From Static to Strategic: Modernizing Privileged Access for Cloud Infrastructure
The promise of the cloud – agility, scalability, and innovation – has revolutionized how enterprises operate. Cloud infr
Read MoreTuesday, Sep 30, 2025
Eliminate Standing Access: Introducing JIT Kubernetes for Azure AKS Security
The Security Mandate: Why Permanent Access Fails Mission-Critical AKS Kubernetes has become the operating system of
Read MoreFriday, Aug 08, 2025
User Access Review in Cloud Security: A Foundational Guide to Securing Your Cloud Environment
Introduction: The Unseen Gatekeepers of Cloud Security In the rapidly expanding landscape of cloud computing, organi
Read More