Fortify Supply Chain, Contextualization at Runtime and Prioritization on Exploitability
In today’s interconnected world, securing your open source dependencies is paramount to safeguarding your applications. Cloudanix introduces a powerful solution that empowers you to identify and address vulnerabilities, gain contextual understanding of your security landscape, and prioritize risks based on their impact. With Cloudanix, you can confidently protect your applications and safeguard your organization.
Identify and Address Vulnerabilities in Your Open Source Dependencies to Improve Supply Chain Security
Cloudanix SCA helps identify vulnerabilities and compliance issues (License, Maintenance, Security Practices, etc.). Automatically scan your code repositories for Software Bill Of Materials (SBOM) and find out vulnerabilities and compliance issues associated with the SBOM for supply chain security. Cloudanix highlights fixes and provides recommendations for updates to open source vulnerabilities.
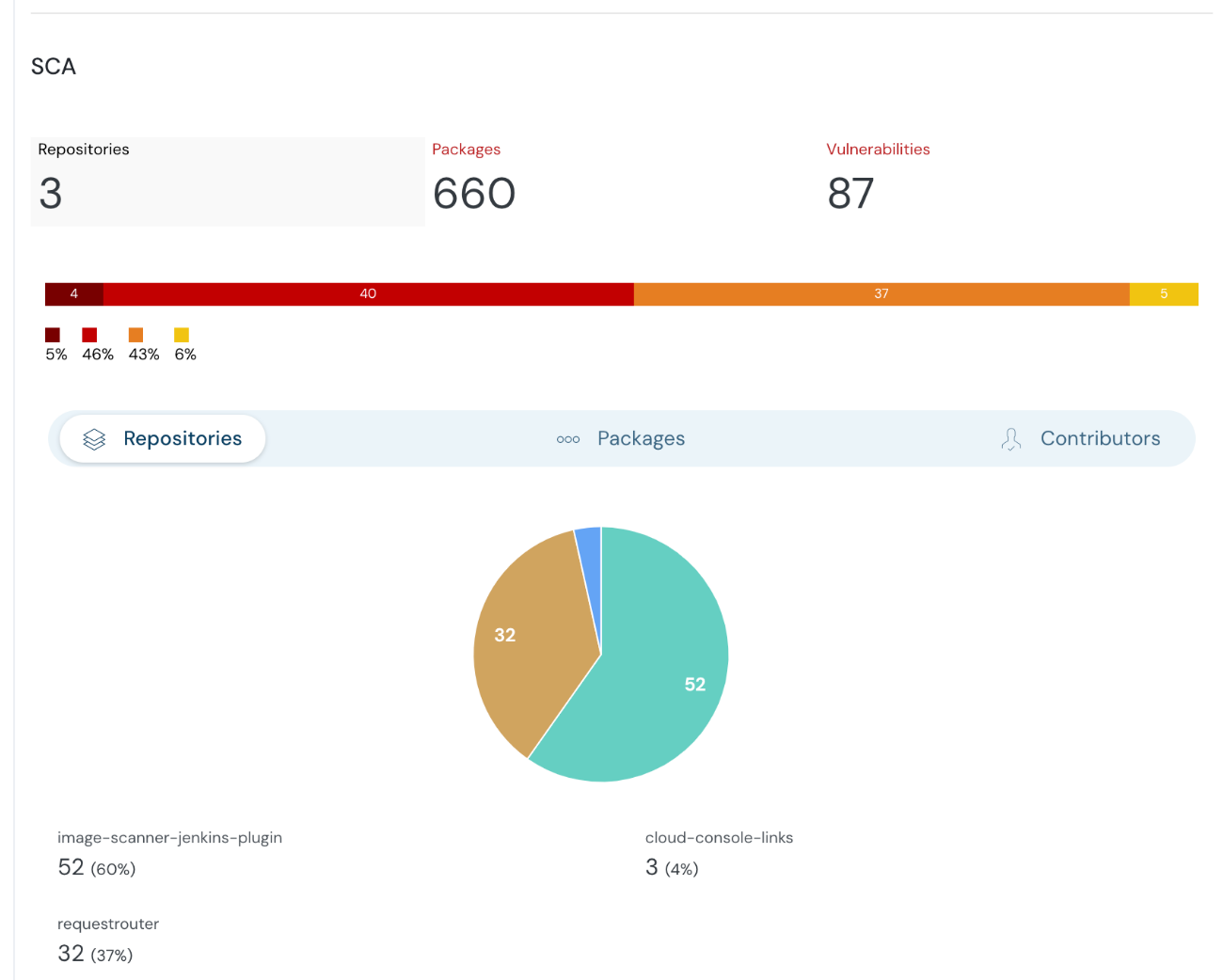 Summary of SCA in Cloudanix dashboard
Summary of SCA in Cloudanix dashboard
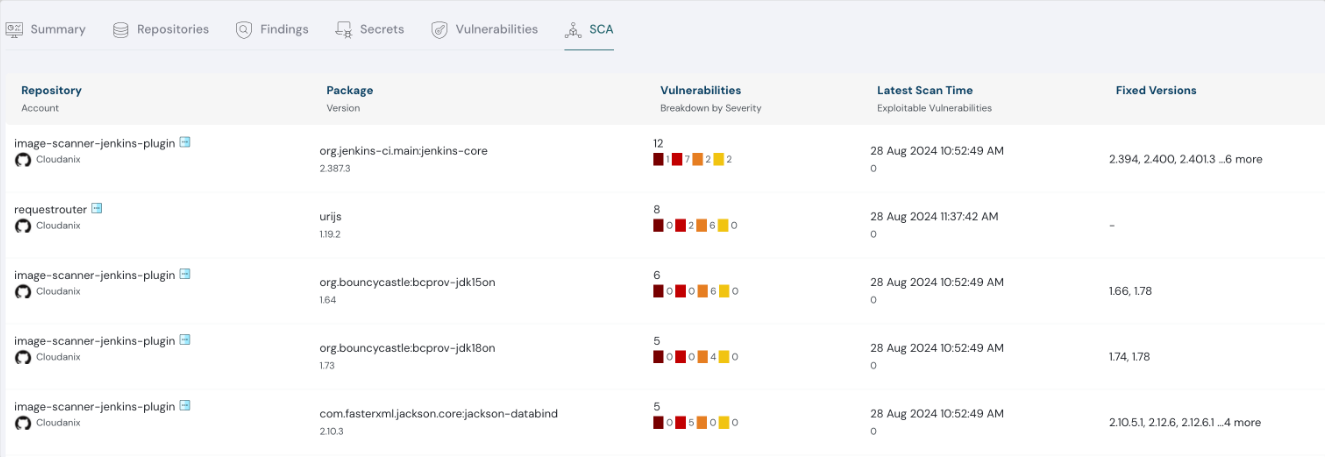
Cloudanix showing details of SCA in dashboard
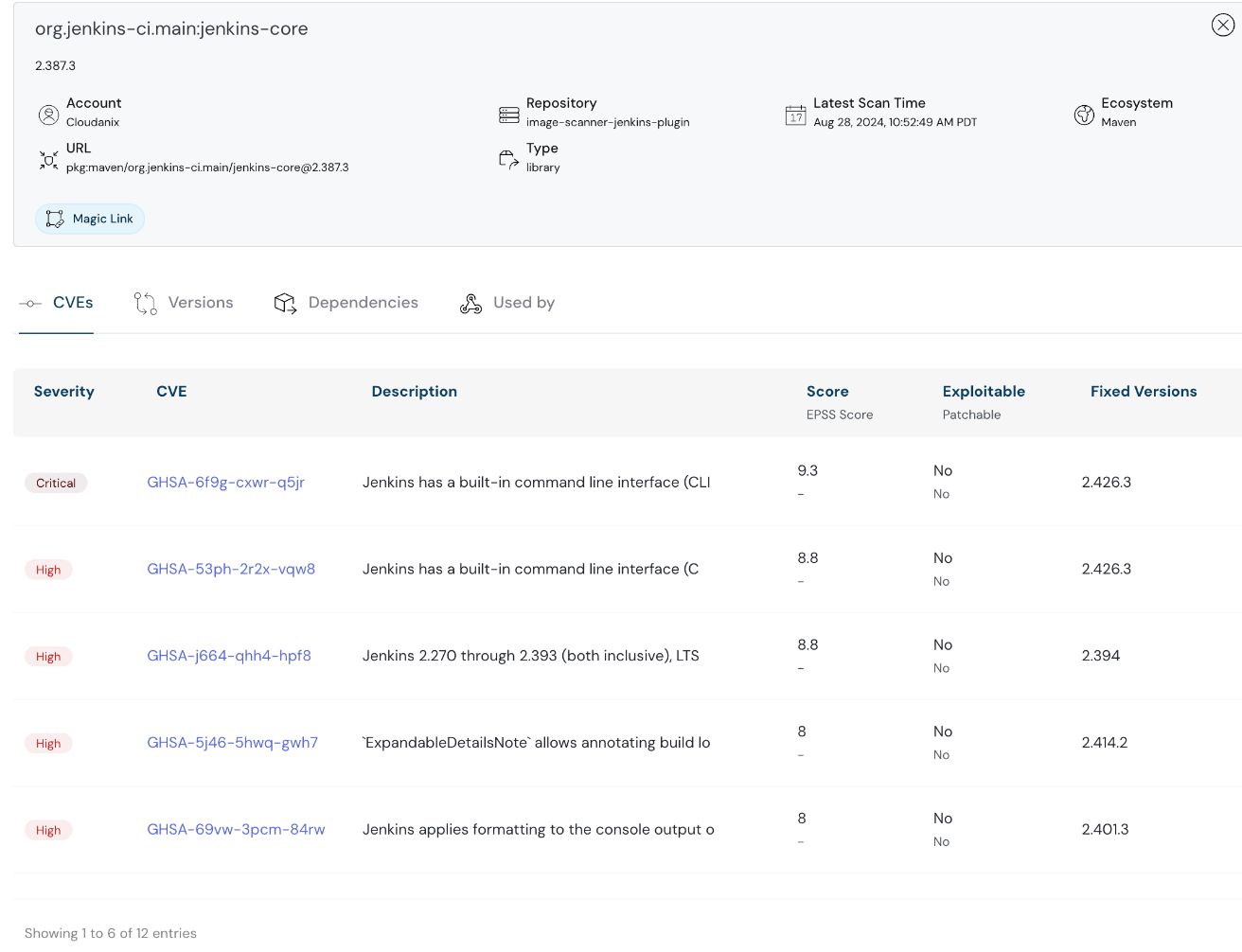 Cloudanix showcasing third party scans
Cloudanix showcasing third party scans
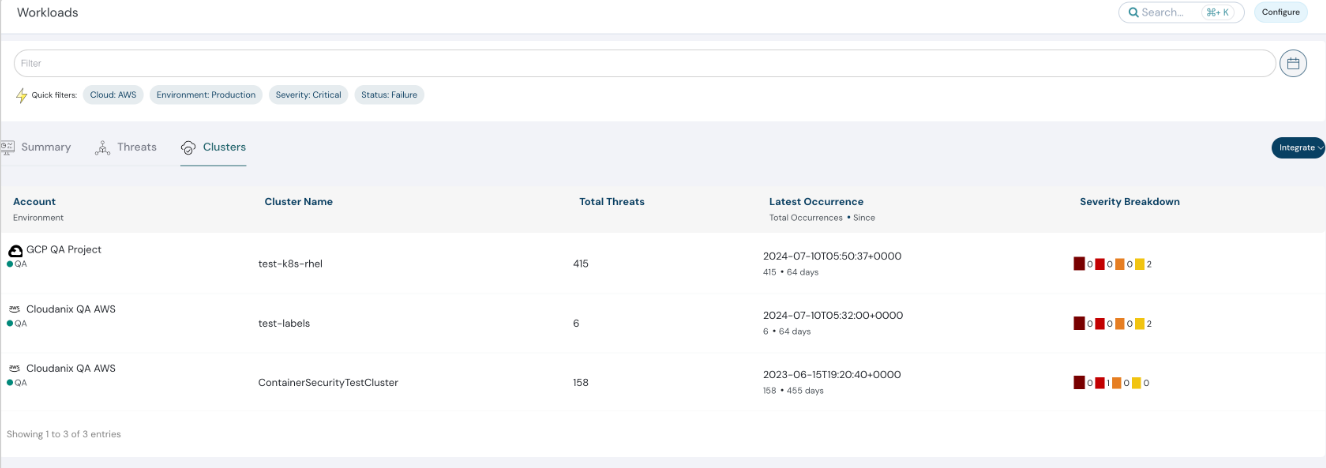
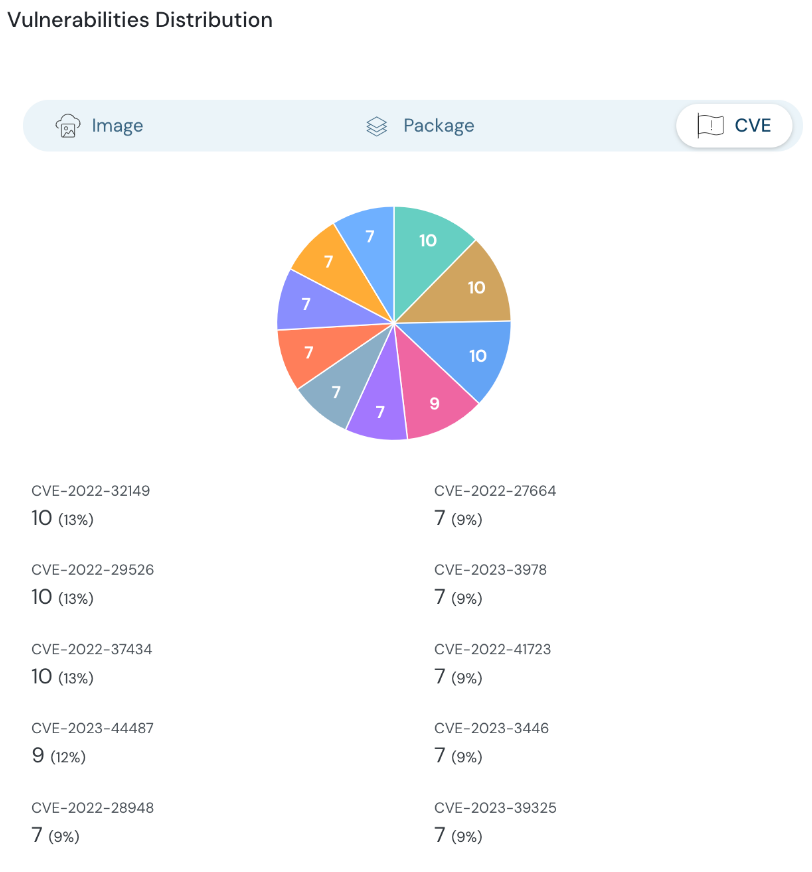
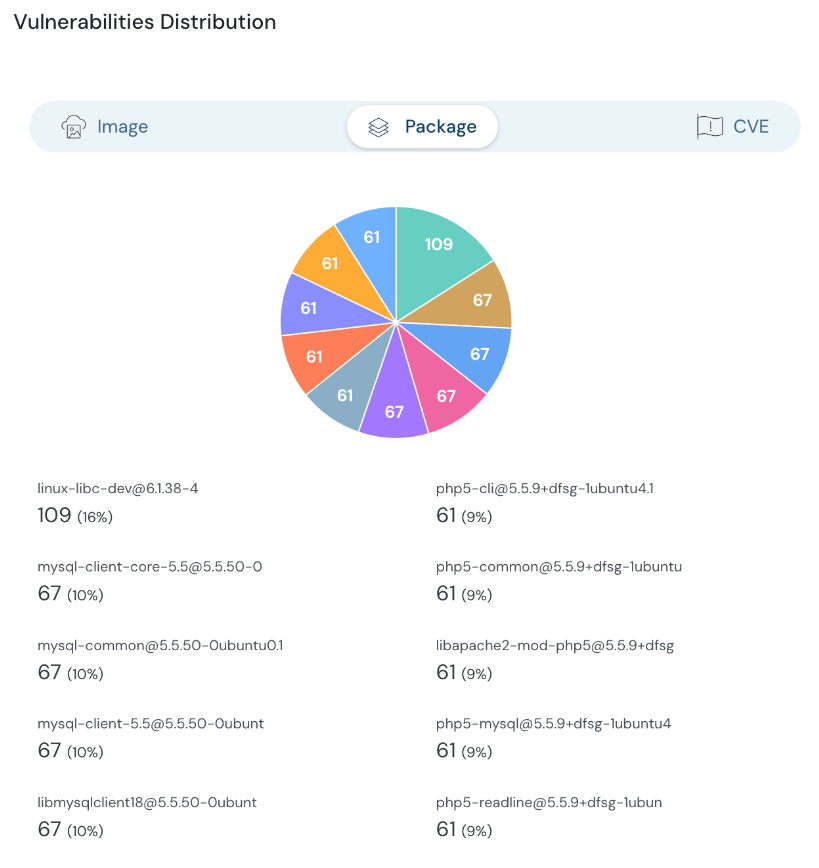
Contextualize Runtime Threats and Image Vulnerabilities
With the latest release, Cloudanix helps improve visibility into containers with both runtime threats and vulnerabilities from images running on those containers. This correlation helps you prioritize and find the most impactful containers to address first.
 Gain granular control over user permissions across AWS and GCP, preventing over-privileged access.
Gain granular control over user permissions across AWS and GCP, preventing over-privileged access.
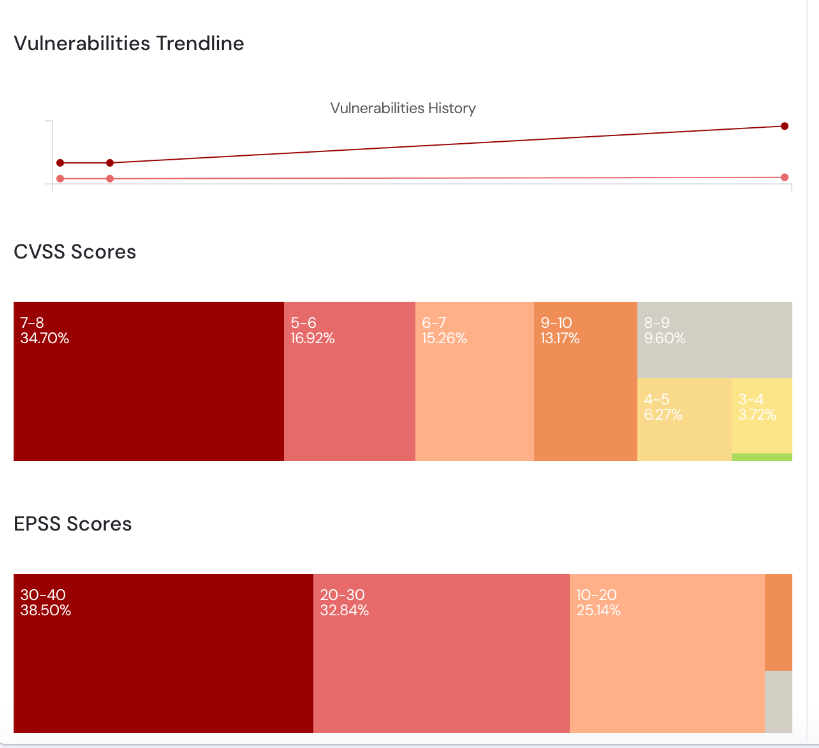
Prioritization Based on Exploitability
Cloudanix not only highlights CVSS scores, but also EPSS scores to understand exploitable vulnerabilities. It helps our users to understand and prioritize image vulnerabilities which need addressing.
 Elevate and revoke privileges for cloud users using Cloudanix console
Elevate and revoke privileges for cloud users using Cloudanix console
 Elevate and revoke privileges for cloud users using Cloudanix console
Elevate and revoke privileges for cloud users using Cloudanix console
 Elevate and revoke privileges for cloud users using Cloudanix console
Elevate and revoke privileges for cloud users using Cloudanix console
Cloudanix Blogs
- Top 10 revised code security best practices for developers
- Why IAM in the Cloud needs attention?
- What is Shift Left Security?
- What is Shared Responsibility Model?
Other Resources
- Cybersecurity Technology Adoption Cycle
- Secure By Default Comparison
- Detection Engineering and Threat Detection
- Building a Security Platform Engineering Team
- GitLab Patches Critical Flaw
TODO:// is not an option for Cloud Security
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedBlog
Read More Posts
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Wednesday, Nov 05, 2025
From Static to Strategic: Modernizing Privileged Access for Cloud Infrastructure
The promise of the cloud – agility, scalability, and innovation – has revolutionized how enterprises operate. Cloud infr
Read MoreTuesday, Sep 30, 2025
Eliminate Standing Access: Introducing JIT Kubernetes for Azure AKS Security
The Security Mandate: Why Permanent Access Fails Mission-Critical AKS Kubernetes has become the operating system of
Read MoreFriday, Aug 08, 2025
User Access Review in Cloud Security: A Foundational Guide to Securing Your Cloud Environment
Introduction: The Unseen Gatekeepers of Cloud Security In the rapidly expanding landscape of cloud computing, organi
Read More