Slack App for JIT Access, Smarter Image Vulnerability Scanning and More
You asked, we delivered! We’re thrilled to announce the launch of our new Slack application for JIT (Just In Time) access. This highly requested feature streamlines access management, enabling users to request, accept, and revoke access—all without leaving Slack. But that’s not all! We’ve also enhanced our image vulnerability scanning with smarter tracking and improved visibility, helping you stay ahead of emerging threats and maintain a secure environment.
Request for Just In Time Access from Slack - No more app switching or context-switching
JIT Access is now integrated with Slack. Request on-demand cloud access right where you collaborate without leaving your favorite communication tool. Enhancing productivity and seamless & secure cloud access, all without leaving Slack.
Approval workflow is also integrated with Slack. Simplify cloud IAM permissions, enhance control – all with a quick Slack message, right from the platform your team uses every day.
 Request for Just In Time Access from Slack
Request for Just In Time Access from Slack
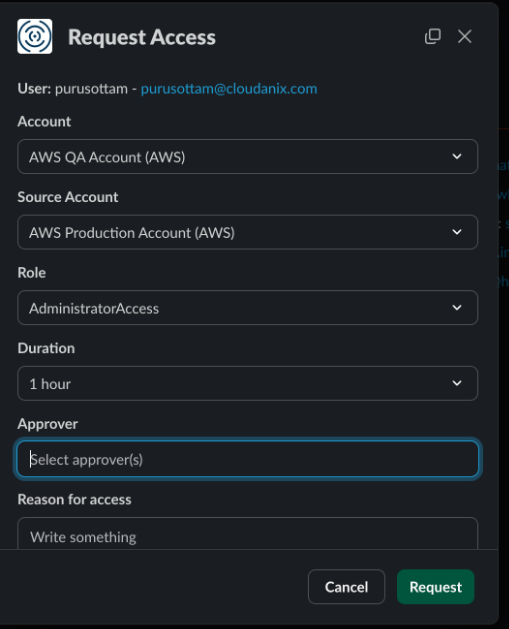 Requesting access from the Slack app
Requesting access from the Slack app
Smarter Image Vulnerability Scanning
Image Vulnerability Scanning has been upgraded to track drift between scan results of different image versions.
Improvements include highlighting newly introduced, resolved and unchanged vulnerabilities.
Understand your image’s security trajectory at a glance. Gain deeper insights into your security posture and stay ahead of threats with this enhanced visibility.
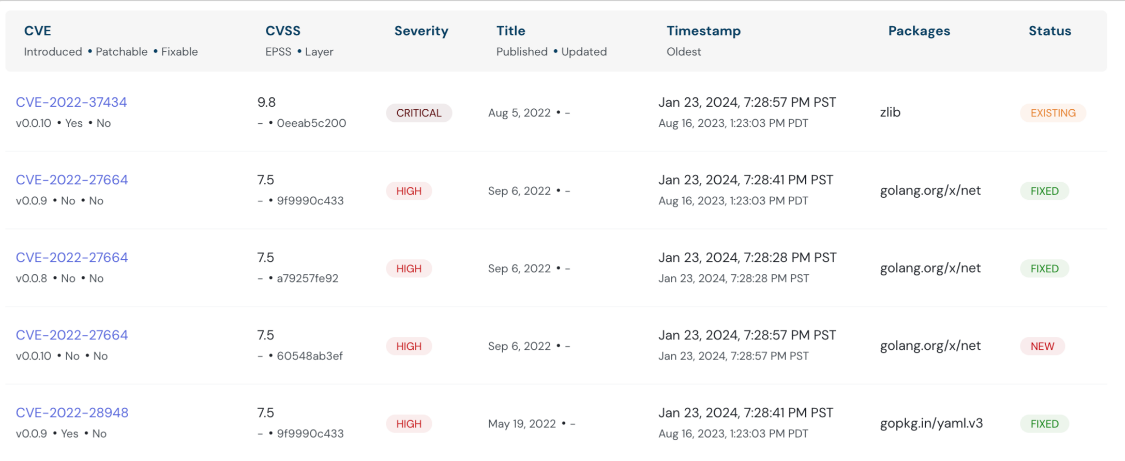 Understand your image’s security trajectory
Understand your image’s security trajectory
Cloudanix Resources
- Vulnerability Management - Deep dive
- Shared Responsibility Model - Securing every aspect of cloud
- Cloud Audit - Comprehensive assessment of cloud environment
Resources over Internet
- All Important updates prior to AWS re:Invent by Chris Farris
- Entrepreneurs Need to Stay Aware: Cybersecurity Threats May Directly Impact the Bottom Line
- eBPF Threat Modeling Guide for Security Usage
TODO:// is not an option for Cloud Security
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedBlog
Read More Posts
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Wednesday, Nov 05, 2025
From Static to Strategic: Modernizing Privileged Access for Cloud Infrastructure
The promise of the cloud – agility, scalability, and innovation – has revolutionized how enterprises operate. Cloud infr
Read MoreTuesday, Sep 30, 2025
Eliminate Standing Access: Introducing JIT Kubernetes for Azure AKS Security
The Security Mandate: Why Permanent Access Fails Mission-Critical AKS Kubernetes has become the operating system of
Read MoreFriday, Aug 08, 2025
User Access Review in Cloud Security: A Foundational Guide to Securing Your Cloud Environment
Introduction: The Unseen Gatekeepers of Cloud Security In the rapidly expanding landscape of cloud computing, organi
Read More