Secure Access with JIT, Dependency Graphs, Rightsizing, Tracking Non-Human Identities and More
We know security teams are busy and are always looking for faster ways to manage security while planning for scale. Cloudanix focused on making it easier to elevate your security posture with visualization graphs for open source and transitive dependencies, maintaining compliance for human and non human identities and their accesses, advanced insights for achieving principles of least privilege, JIT for Azure and more.
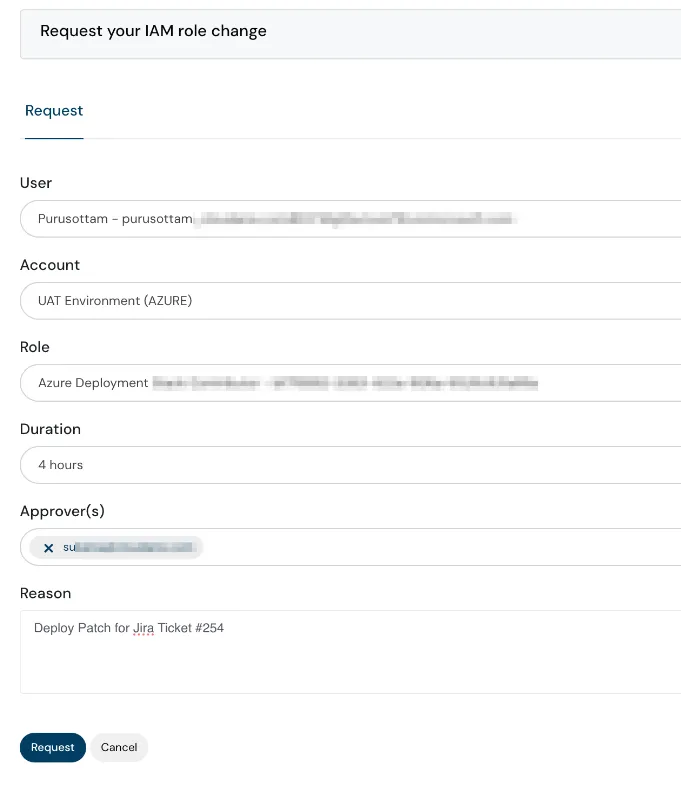
Secure Your Azure Access Effortlessly with Cloudanix IAM Just In Time
Why should Azure users be left out. With this release, Cloudanix IAM Just In Time (JIT) is available for all the major cloud providers AWS, GCP and Azure. Integrate IAM JIT with your Entra ID for a streamlined experience to elevate and revoke privileges for cloud users. With many levers to control the privileges being requested like:
- Manage JIT eligibility for roles
- Auto approve if roles are limited in permissions
- Define maximum duration of JIT access and more
Azure Access security effortlessly with IAM Just In Time
Dependency Graphs
Stay on top of your open-source dependencies and transitive dependencies with Cloudanix. Gain a comprehensive understanding of your open-source software ecosystem with our enhanced Dependency Graphs. With a clear, graphical representation of packages and their nested dependencies, identifying vulnerabilities, and outdated libraries has become easier and more intuitive. Also, visualize vulnerabilities at a repository level in detail.
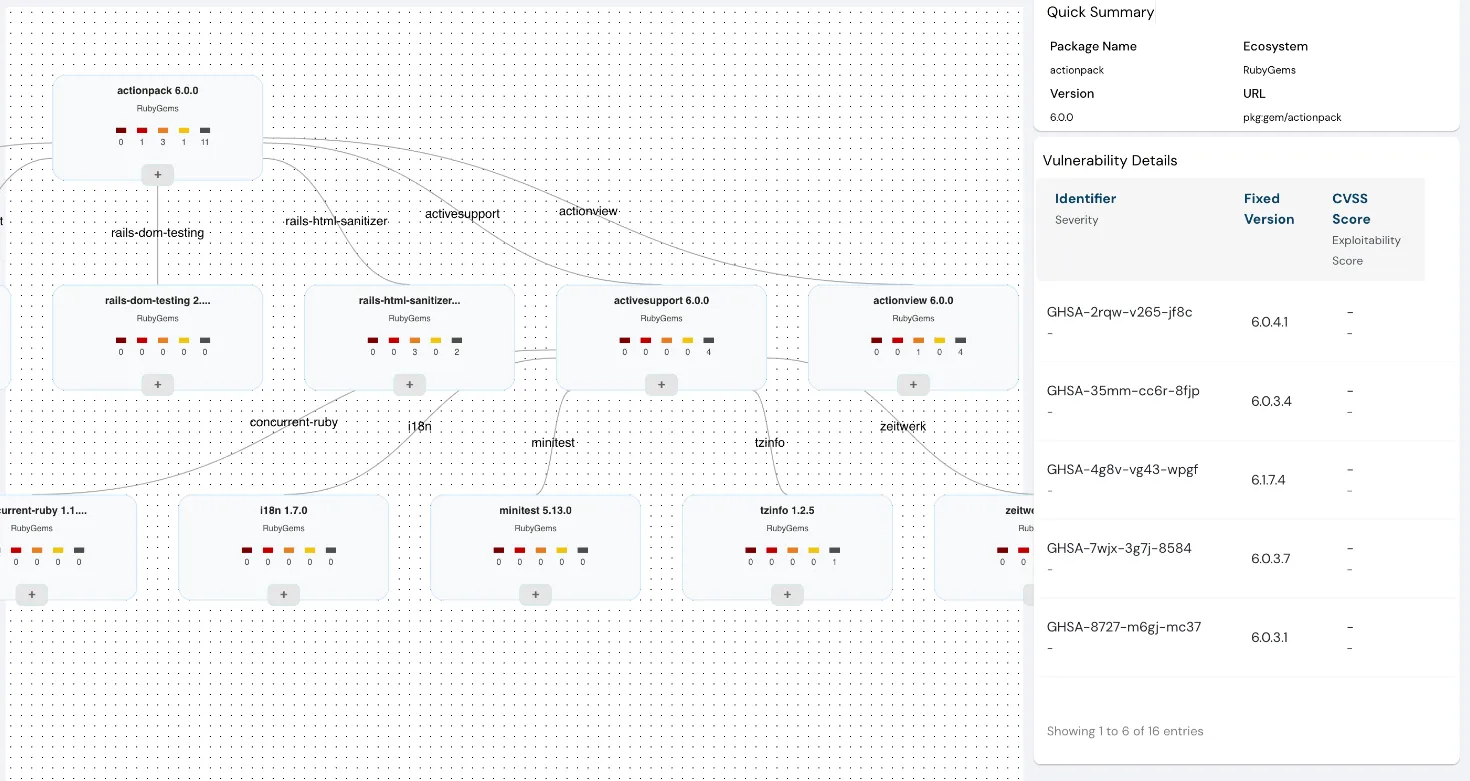
understanding of open-source software ecosystem with enhanced Dependency Graphs
understanding of open-source software ecosystem with enhanced Dependency Graphs
Track Non-Human Identities and Their Access in Detail
This new feature allows you to identify and monitor Non-Human & Human Access along with Third Party, Cross-Account and Internal Access to your cloud resources. With these insights, get a complete picture of all types of accesses and every access point, making it easier to secure your cloud environments and maintain compliance.
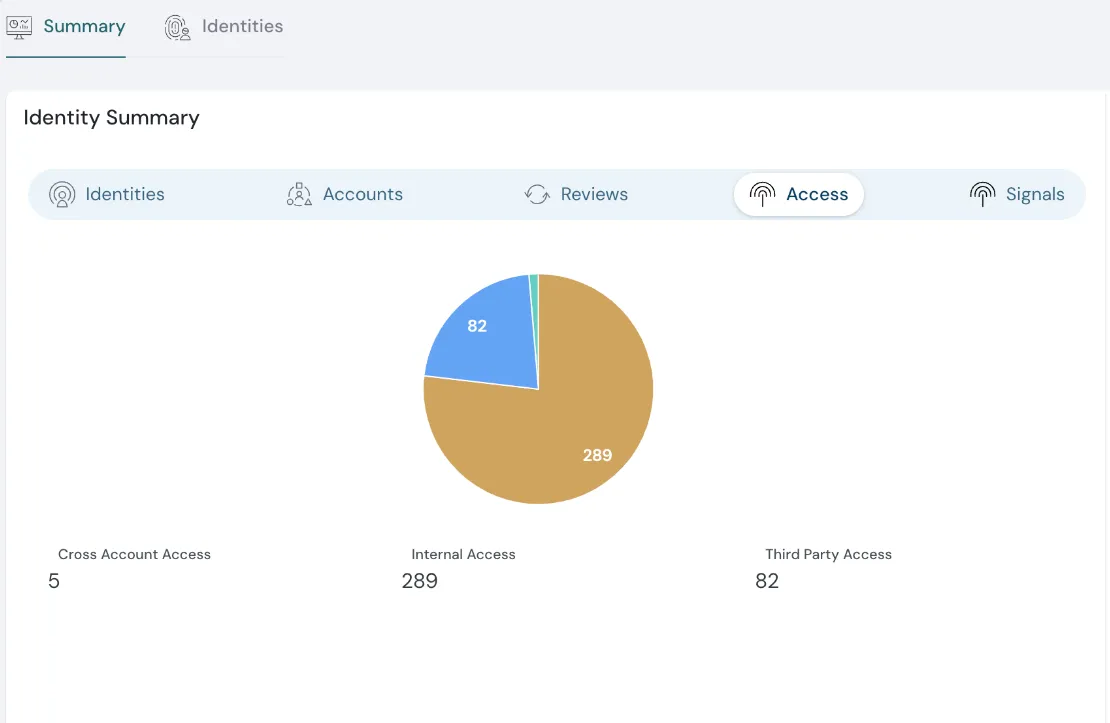
Non-Human Identities and their access in detail
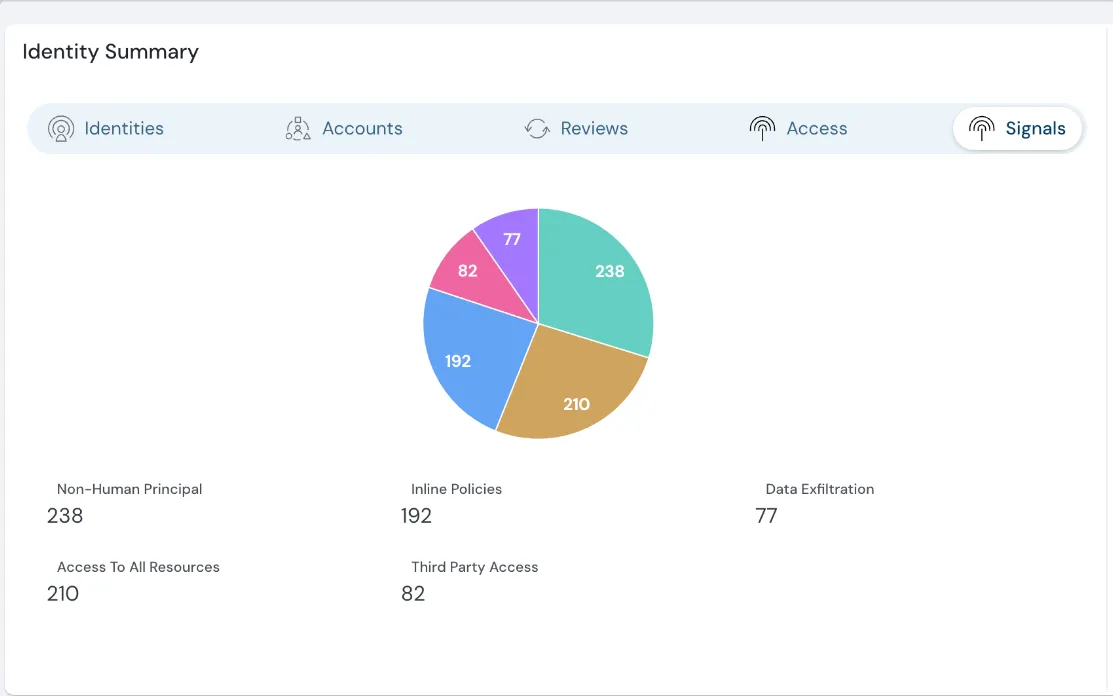
Non-Human Identities and their access in detail
Achieve Principles of Least Privilege with Advanced IAM Insights
Leverage our advanced IAM Insights, powered by Non-Human Intelligence and Right Sizing capabilities, to identify and eliminate unnecessary permissions. Gain actionable recommendations to enforce the principle of least privilege and strengthen your security posture.
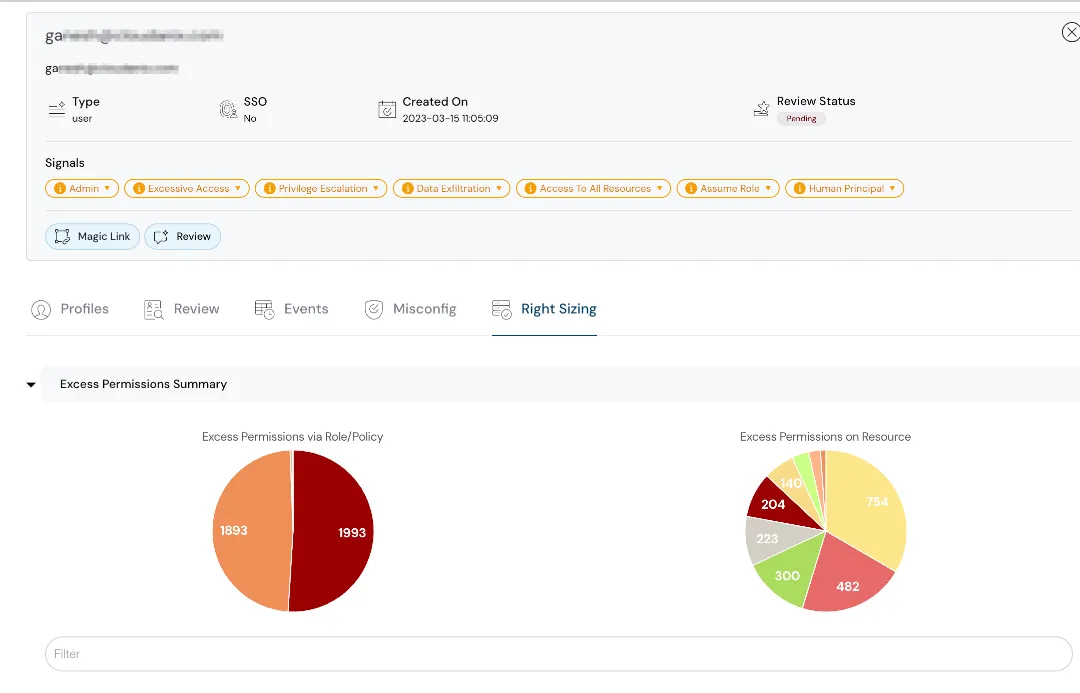
Non-Human Identities and their access in detail
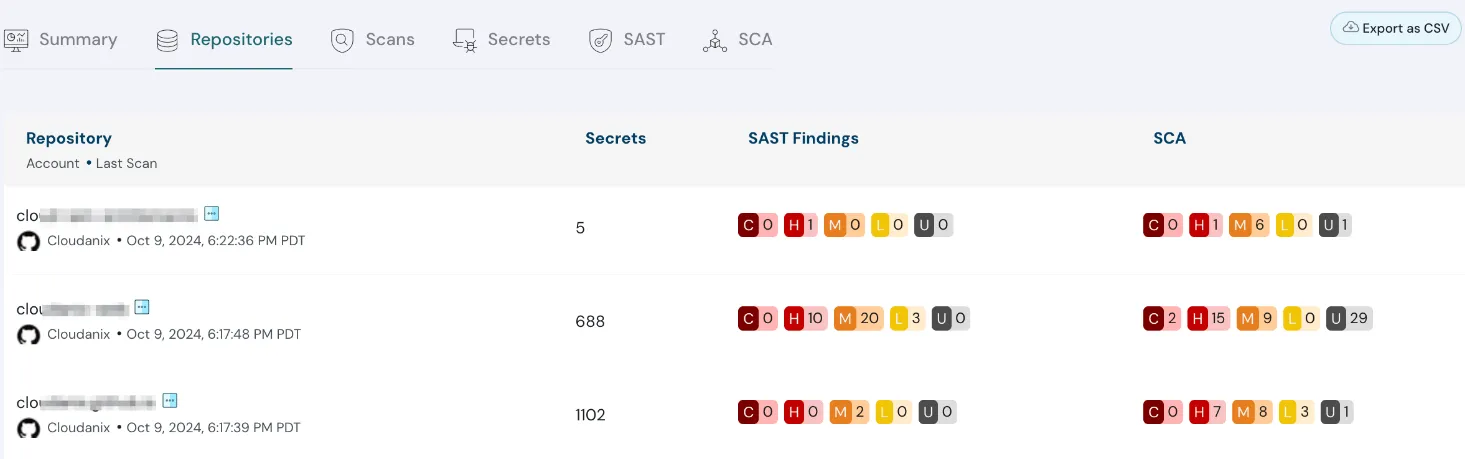
Prioritize Critical Findings with Impactful Resource Identification
Save time and focus on what matters most with our enhanced misconfiguration findings. Easily identify the most impactful resources, streamlining your remediation efforts and ensuring optimal security.

enhanced misconfiguration findings
Cloudanix Resources
- What is Shared Responsibility Model?
- What is Zero Trust Security?
- Hiring Cybersecurity Professionals
- Understanding What Is Non-Human Identities?
Resources over Internet
- Different ways to Delete an AWS resource by Rami McCarthy and Daniel Grzelak
- CNAPP & Success Criteria by Naman Sogani
- Complete Guide to exploiting CSRF
- YubiKeys are Vulnerable by Dan Goodin
TODO:// is not an option for Cloud Security
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedBlog
Read More Posts
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Tuesday, Feb 10, 2026
The 2026 CNAPP Compliance Framework: Turning Audit from Crisis to Continuity
Introduction: The Death of the Point-in-Time Audit In the high-velocity cloud landscape of 2026, the traditional app
Read MoreThursday, Feb 05, 2026
CSPM vs. CNAPP: Navigating Cloud Security Evolution for Modern Enterprises
The shift to cloud-native architectures represents a fundamental change in how applications are designed, built, and dep
Read MoreThursday, Jan 22, 2026
Top 10 Identity and Access Management Solutions
Identity and Access Management (IAM) has traditionally been considered one of the boring parts of security. But with the
Read More