Cutting Down Notification Noise with Container Updates
And now you can further cut down the noise with this new feature!
Recently, several nations and businesses have been affected by data breaches, and according to statistics, human error accounts for 95% of cybersecurity breaches. This highlights how important it is for employees to be aware of the possible consequences that can protect their infrastructure from outside attacks.
In the past month, we have made significant progress on several new features and enhancements.
Highlights
1. Container Notifications
You can now mute notifications for your container workloads based on pods, containers, and nodes. This means you can receive more targeted alerts and cut down the noise.
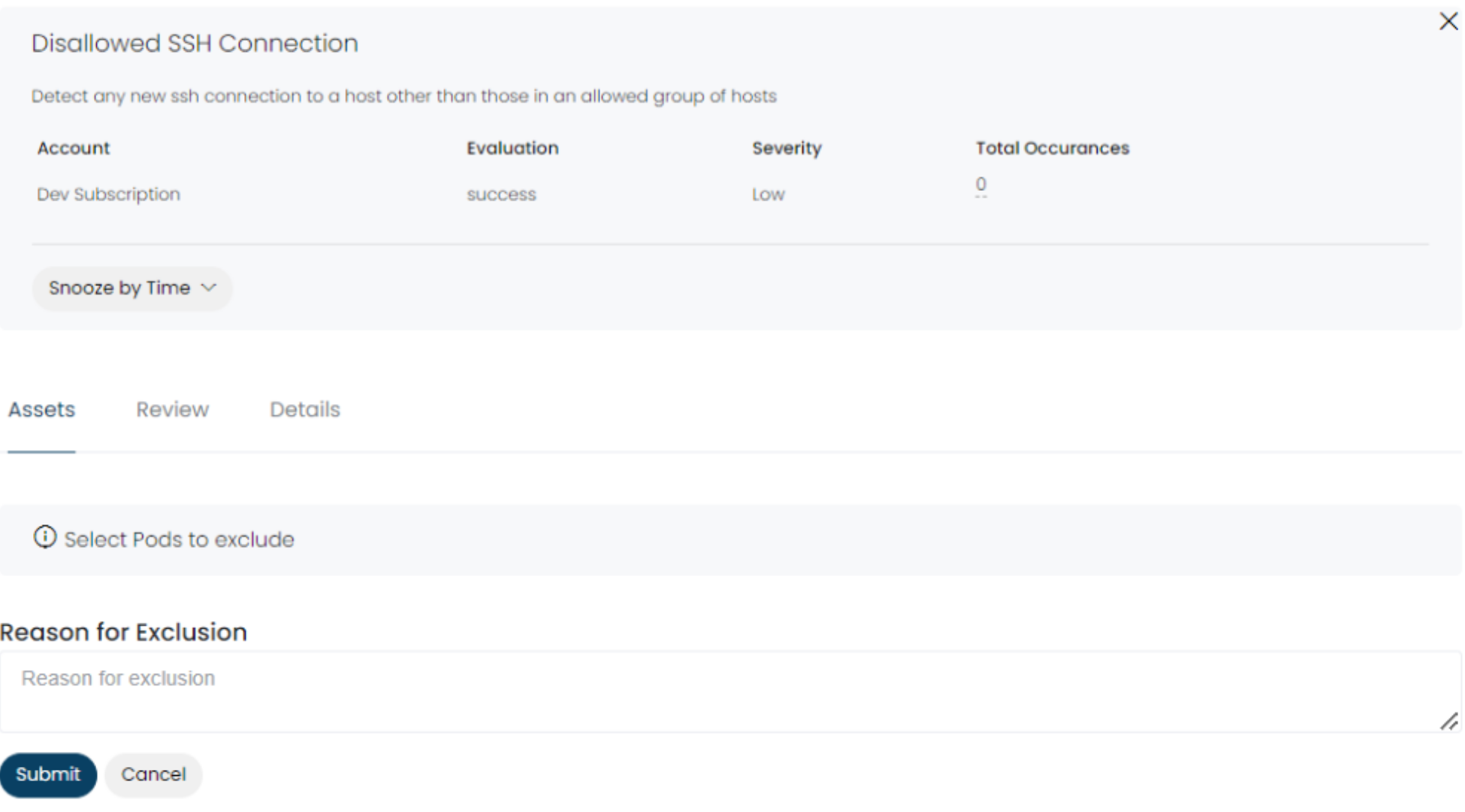
2. Review Container Risks
We now support the same workflow for containers as we do for your Risk screens. You can:
- Acknowledge (and open a Jira ticket)
- Pause the risks
- Accept the risk
3. Better Events UX & Notifications
Events UX and notifications have been revamped to show additional information directly in Slack/Email, so you don’t have to come to the Dashboard. You can consume the information on the go.
4. Historical Data
On the Risk slide-out, you can now see historical assets that may have failed in the past. This helps track how risks have been affecting assets and how they have been remediated over time.
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedBlog
Read More Posts
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Wednesday, Nov 05, 2025
From Static to Strategic: Modernizing Privileged Access for Cloud Infrastructure
The promise of the cloud – agility, scalability, and innovation – has revolutionized how enterprises operate. Cloud infr
Read MoreTuesday, Sep 30, 2025
Eliminate Standing Access: Introducing JIT Kubernetes for Azure AKS Security
The Security Mandate: Why Permanent Access Fails Mission-Critical AKS Kubernetes has become the operating system of
Read MoreFriday, Aug 08, 2025
User Access Review in Cloud Security: A Foundational Guide to Securing Your Cloud Environment
Introduction: The Unseen Gatekeepers of Cloud Security In the rapidly expanding landscape of cloud computing, organi
Read More