Kubernetes Metadata Enhancements, RBI & SEBI Compliance Packs, Host Security Improvements, and More
As the regulatory landscape tightens, security becomes paramount. We’ve launched pre-built compliance packs for RBI and SEBI, simplifying compliance across cloud environments. Enhanced visualizations for host security and connected assets provide deeper insights for analyzing findings. Improved Kubernetes metadata management, on-demand scans, advanced anomaly detection, and more await you. Dive deeper and explore how Cloudanix’s CNAPP secures your cloud journey.
Revised Connected Assets View
This release revises the Connected Assets view to enhance the usability and consume-ability of assets, their related assets, metadata, and attack path all in one place. This enriched context assists customers in prioritizing more effectively.
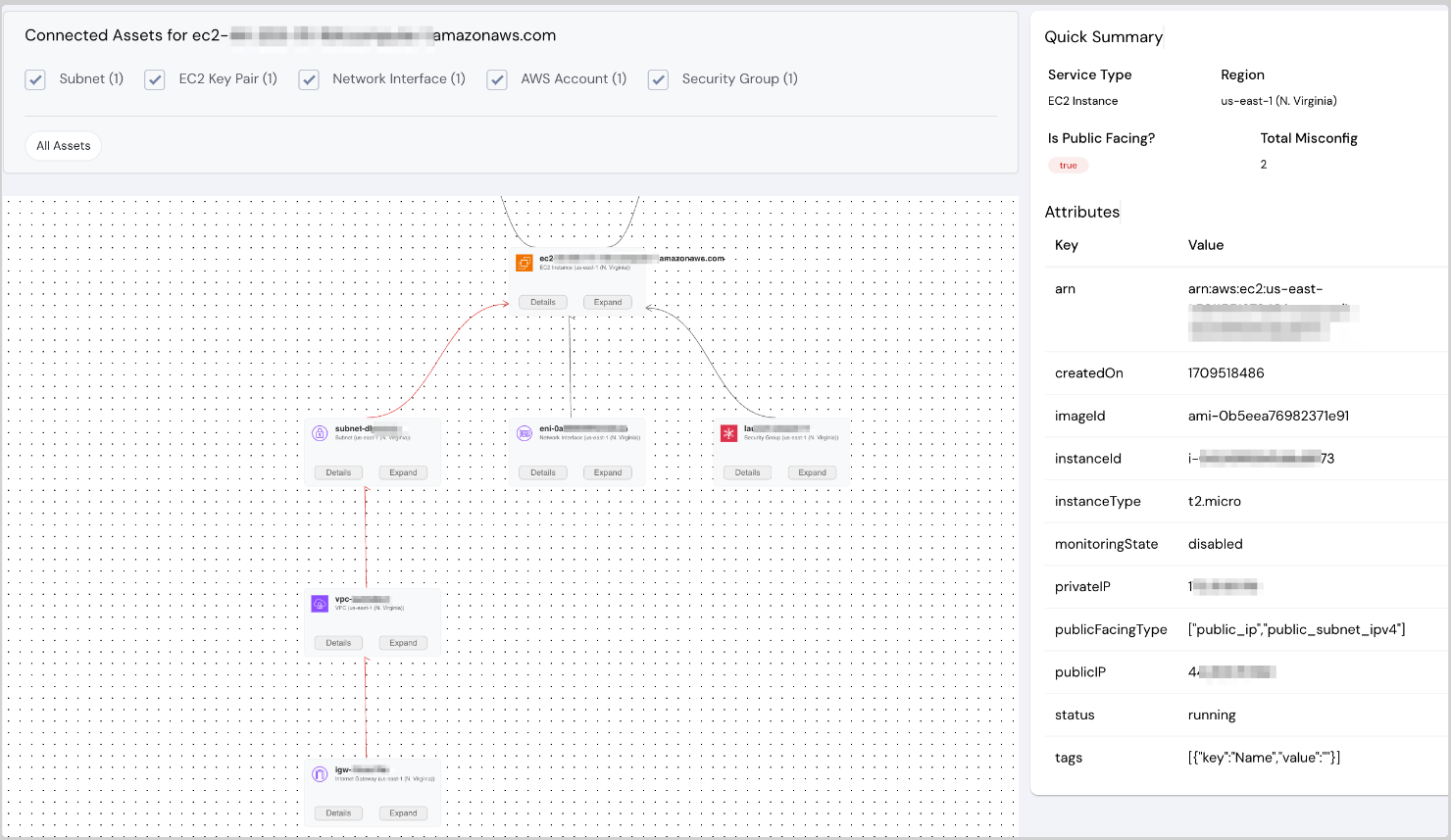 Dashboard showing connected assets
Dashboard showing connected assets
Host Security Improvements
The enhancements in visualizations and the introduction of Top 10 lists for Host Security Events & Vulnerabilities allow customers to analyze findings more effectively. This facilitates better prioritization among findings.
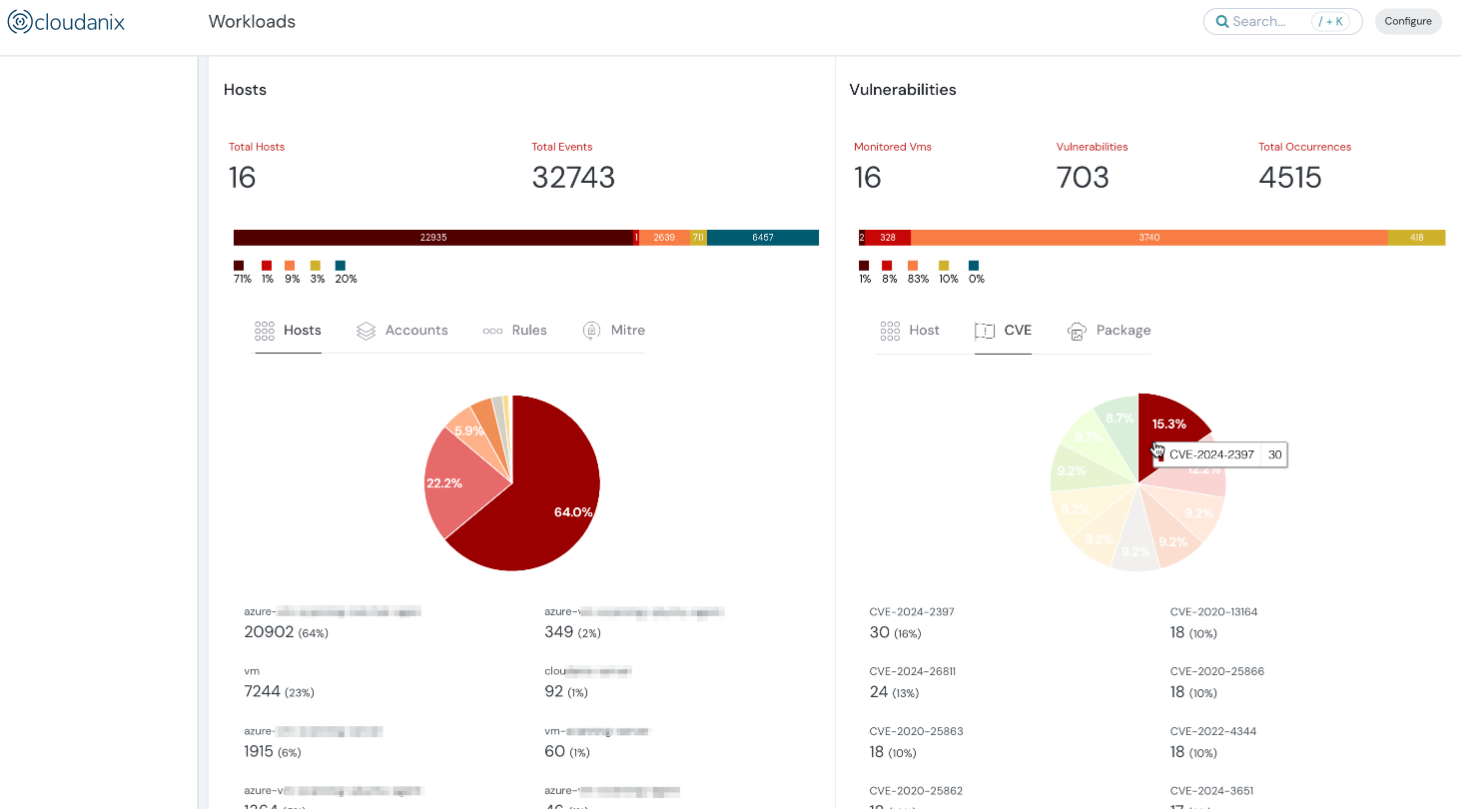 Host and vulnerability summary dashboard of Cloudanix
Host and vulnerability summary dashboard of Cloudanix
RBI & SEBI Compliance Packs
RBI and SEBI have introduced new compliance requirements for our Indian customers. In response, we’ve launched Compliance Packs. These not only allow customers to monitor compliance but also enhance security posture in accordance with RBI & SEBI guidelines.
 Cloudanix now supports RBI and SEBI compliance packs
Cloudanix now supports RBI and SEBI compliance packs
Kubernetes Metadata Enhancements
We have improved Kubernetes Policy Metadata to better map findings with MITRE Tactics and Attack Workloads, and to enhance tagging. Additionally, we’ve introduced impact analysis to help understand the severity of Kubernetes Realtime Runtime Threats.
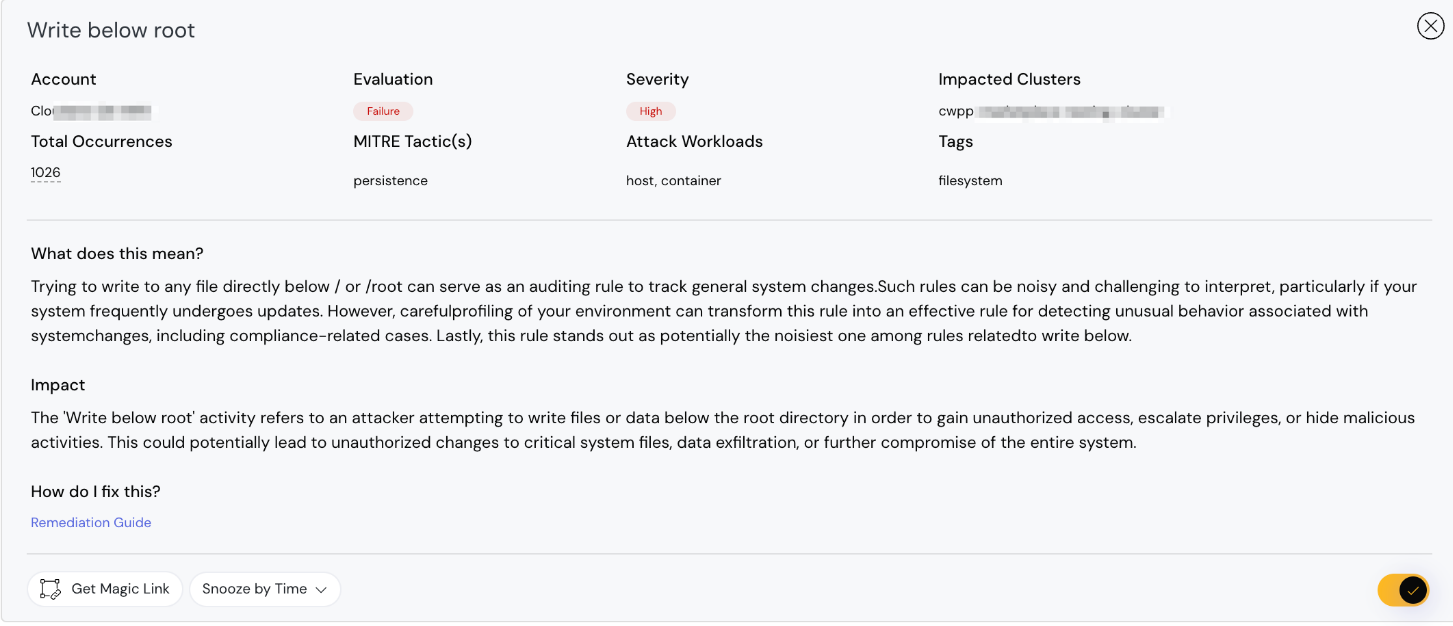 Kubernetes Policy Metadata to better map findings with MITRE Tactics and Attack Workloads
Kubernetes Policy Metadata to better map findings with MITRE Tactics and Attack Workloads
Manual Scan
If you need to scan a build package archive for secrets or vulnerabilities, our Manual Scan feature allows customers to upload and scan any packages for code security issues.
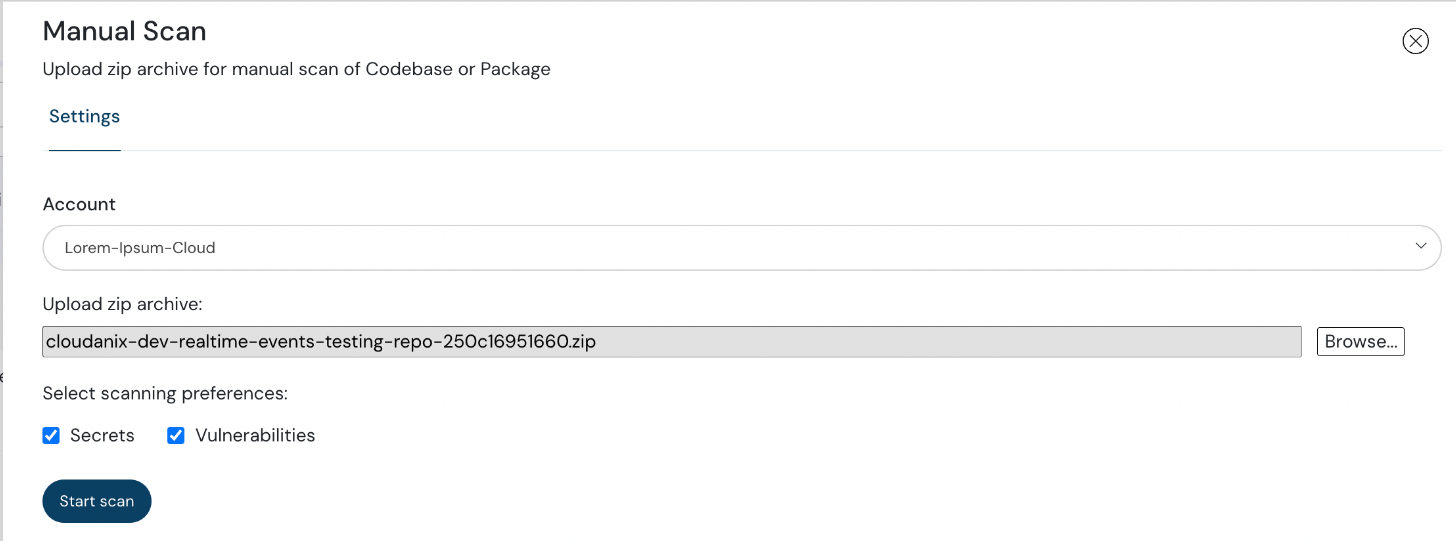 Manual Scan feature to upload and scan any packages for code security
Manual Scan feature to upload and scan any packages for code security
Volume-Based Anomaly Detection
We’re enhancing our anomaly detection capability to monitor and tag activities as anomalies based on volume trends. This will improve the signal-to-noise ratio using volume as an indicator for anomalies. For example, an unusual number of S3 policy changes.
A concern raised by AWS customers: LinkedIn Post
Cloudanix Blogs
Additional Resources
Industry News
- Cloud-Squatting Attacks & Mitigation
- Secrets in AWS Lambda
- AWS Organizations Design
- Incident Response Simulations
- Security Principles
TODO:// is not an option for Cloud Security
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedBlog
Read More Posts
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Wednesday, Nov 05, 2025
From Static to Strategic: Modernizing Privileged Access for Cloud Infrastructure
The promise of the cloud – agility, scalability, and innovation – has revolutionized how enterprises operate. Cloud infr
Read MoreTuesday, Sep 30, 2025
Eliminate Standing Access: Introducing JIT Kubernetes for Azure AKS Security
The Security Mandate: Why Permanent Access Fails Mission-Critical AKS Kubernetes has become the operating system of
Read MoreFriday, Aug 08, 2025
User Access Review in Cloud Security: A Foundational Guide to Securing Your Cloud Environment
Introduction: The Unseen Gatekeepers of Cloud Security In the rapidly expanding landscape of cloud computing, organi
Read More