JIT for Database, Security Health Monitoring, and Code Security Filters
Tighten your seatbelts, Cloudanix has made available the much-awaited JIT for Database. Our customers from the FSI, E-commerce, and HCLS segments being highly regulated, will benefit from this. There’s more for our customers across segments around VM security health monitoring status. Code security with additional filters for public/private repositories and code languages.
Request for Just In Time Access from Slack - No more app switching or context-switching
Our Identity Security Platform has already been securing cloud environments by enabling temporary, least-privilege IAM access, eliminating the risks of permanent cloud access. Now, we’re taking it a step further—extending JIT Access to databases to ensure sensitive data remains protected while allowing seamless, on-demand access when needed. By enforcing least privilege principles, JIT access ensures that sensitive databases remain secure while enabling seamless workflow access for developers and administrators.
With this enhancement, organizations can now eliminate permanent database credentials, need for a jumpbox, enforce strict access controls, minimize attack surfaces and reduce insider threats. Access is granted dynamically using time-bound tokens, ensuring that users only get the exact level of access required—when they need it, for as long as they need it. Whether it’s for cloud databases, critical applications, or infrastructure access, our dynamic, time-bound access controls provide granular security, auditability, and compliance enforcement in real time. Say goodbye to standing privileges and hello to secure, on-demand access.
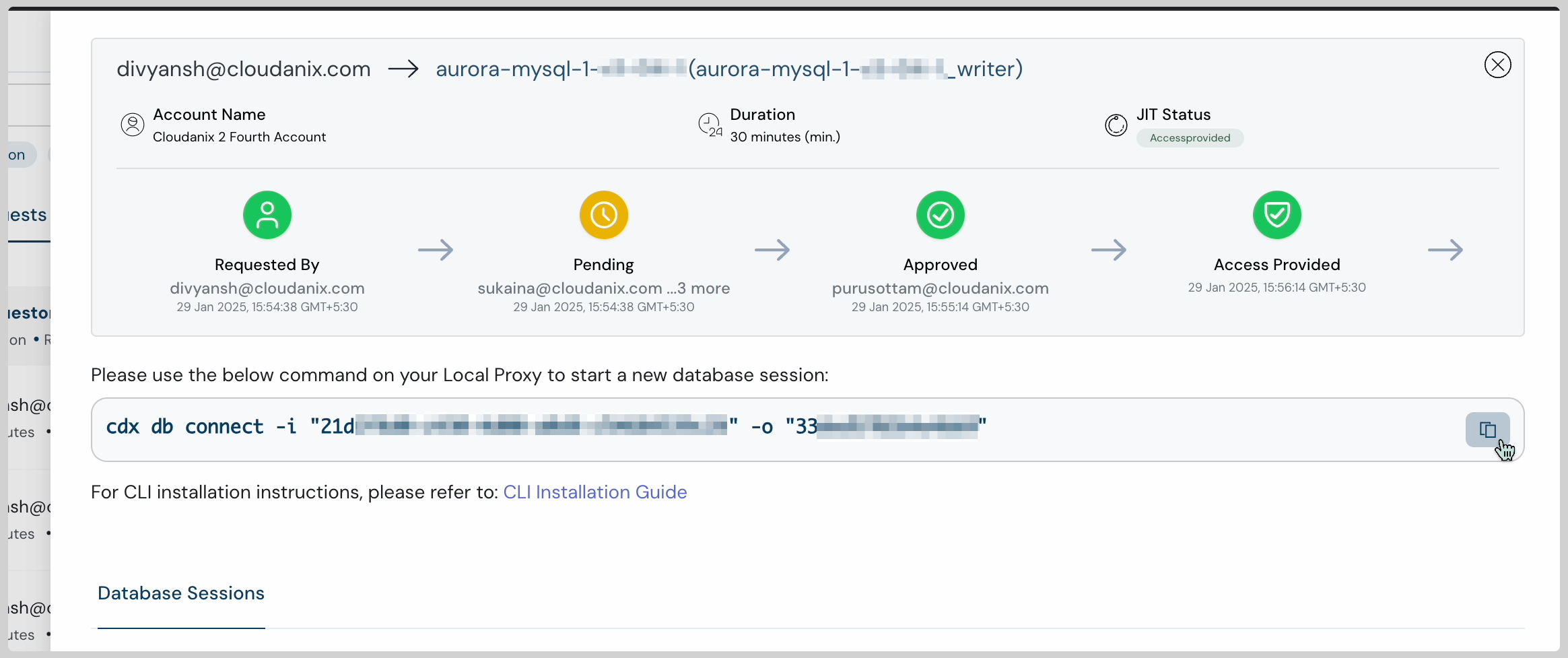
Request for Just In Time Access from Slack
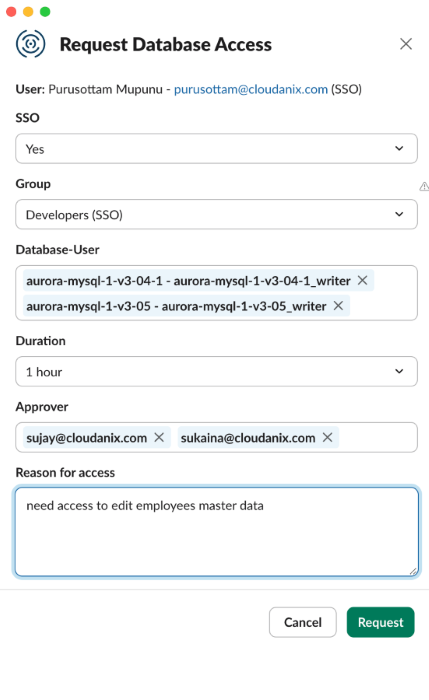
New session permissions
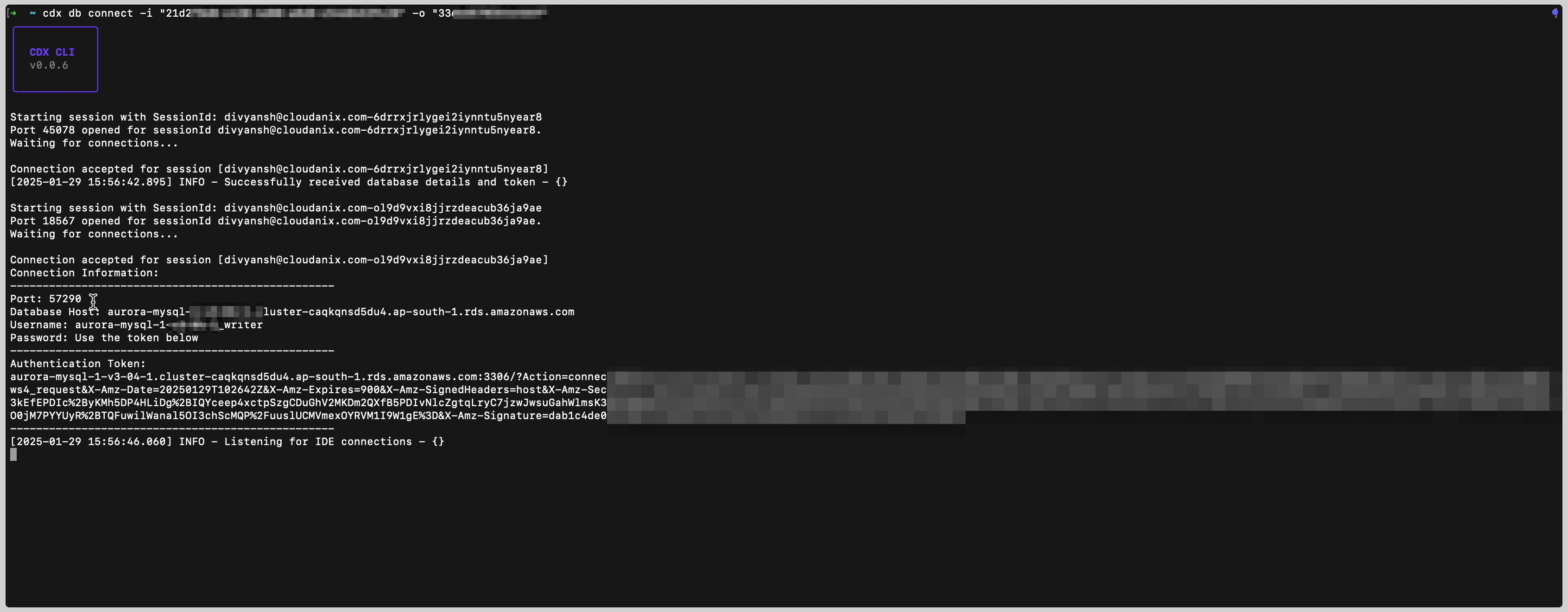
CLX for permission accepted screenshot
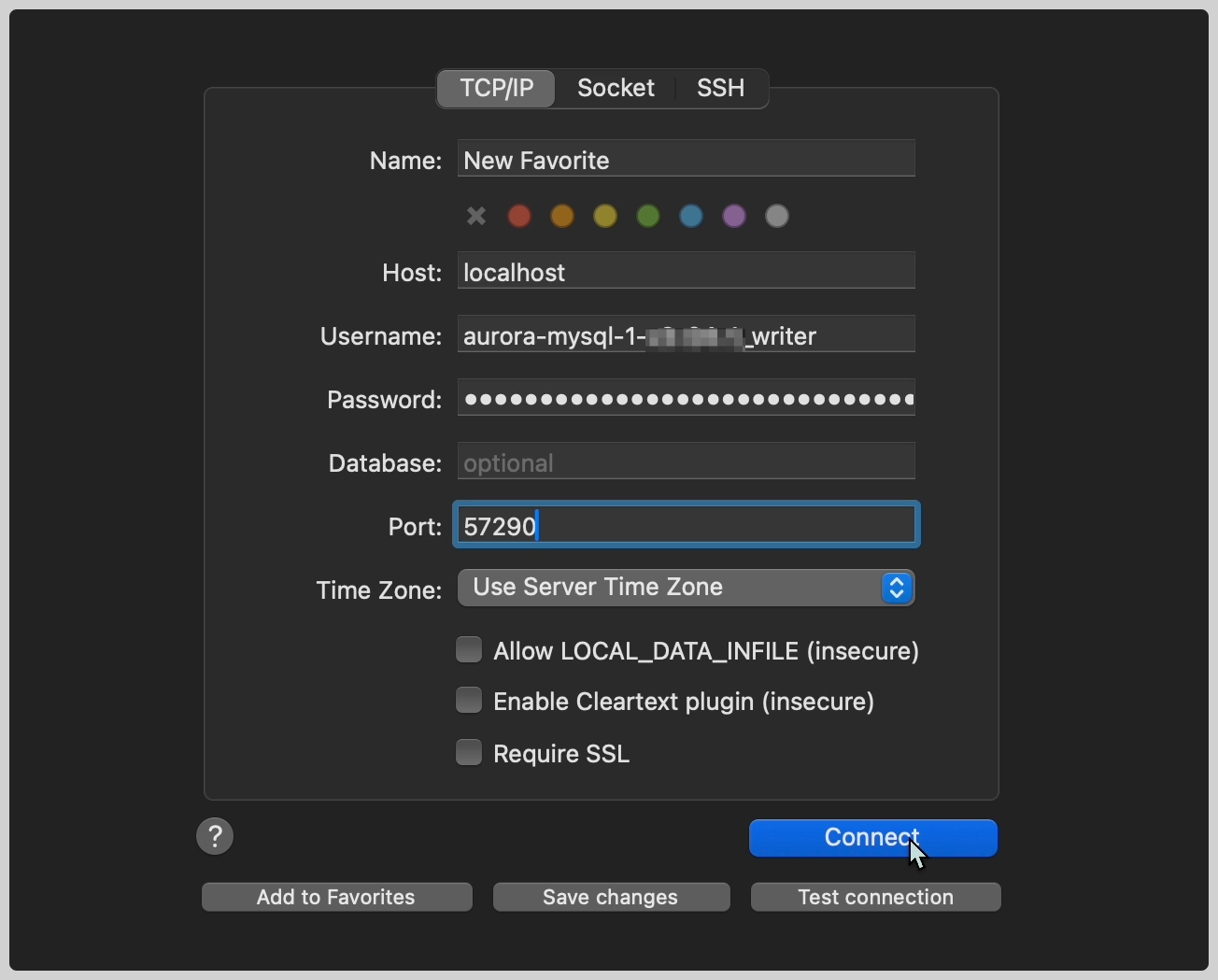 TCP/IP popup window for connection
TCP/IP popup window for connection
Stay up to date with Security Health Monitoring
With Security Health Monitoring, stay up to date with the monitoring status. Take swift action to remediate monitoring gaps directly from the Cloudanix Console.
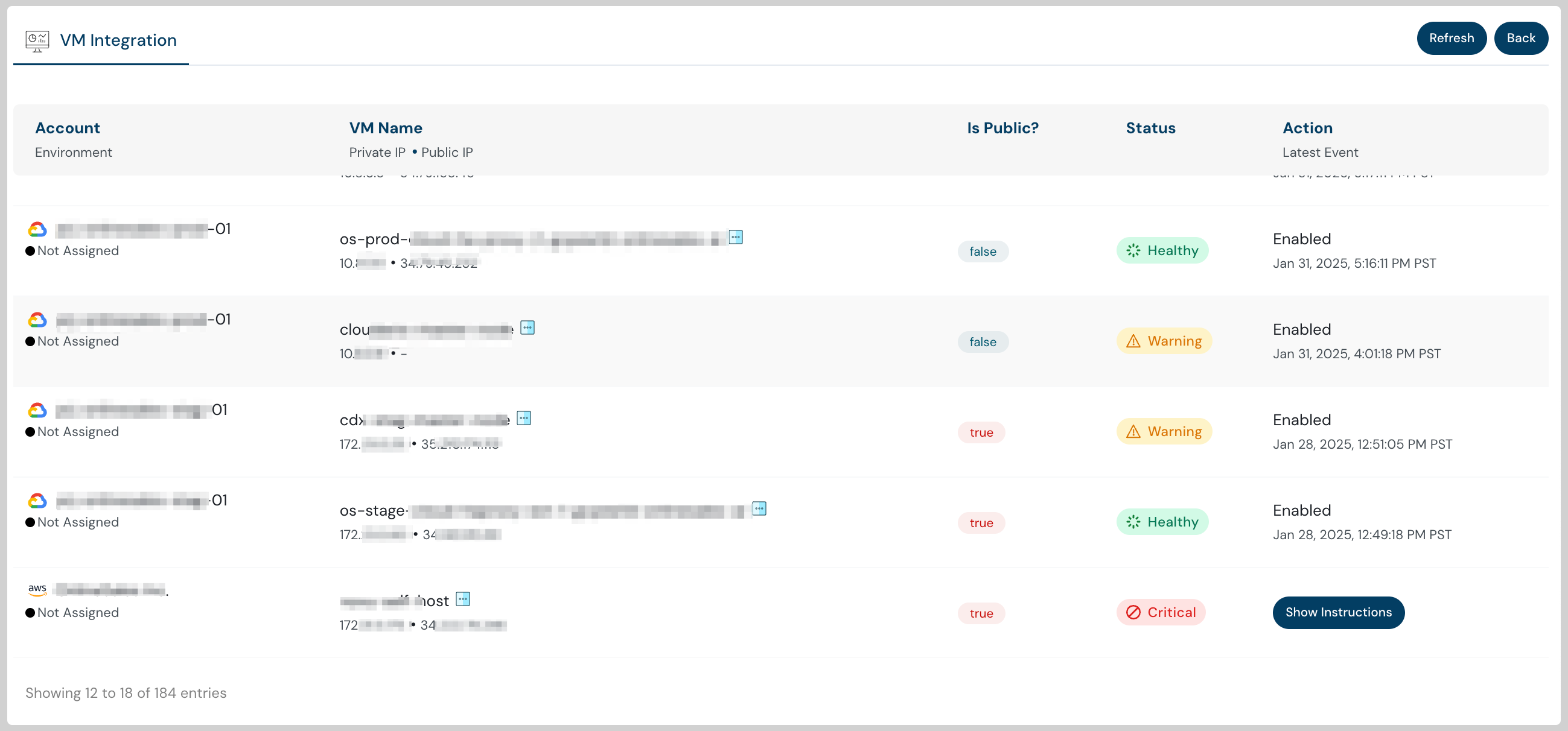 Cloudanix VM integration dashboard
Cloudanix VM integration dashboard
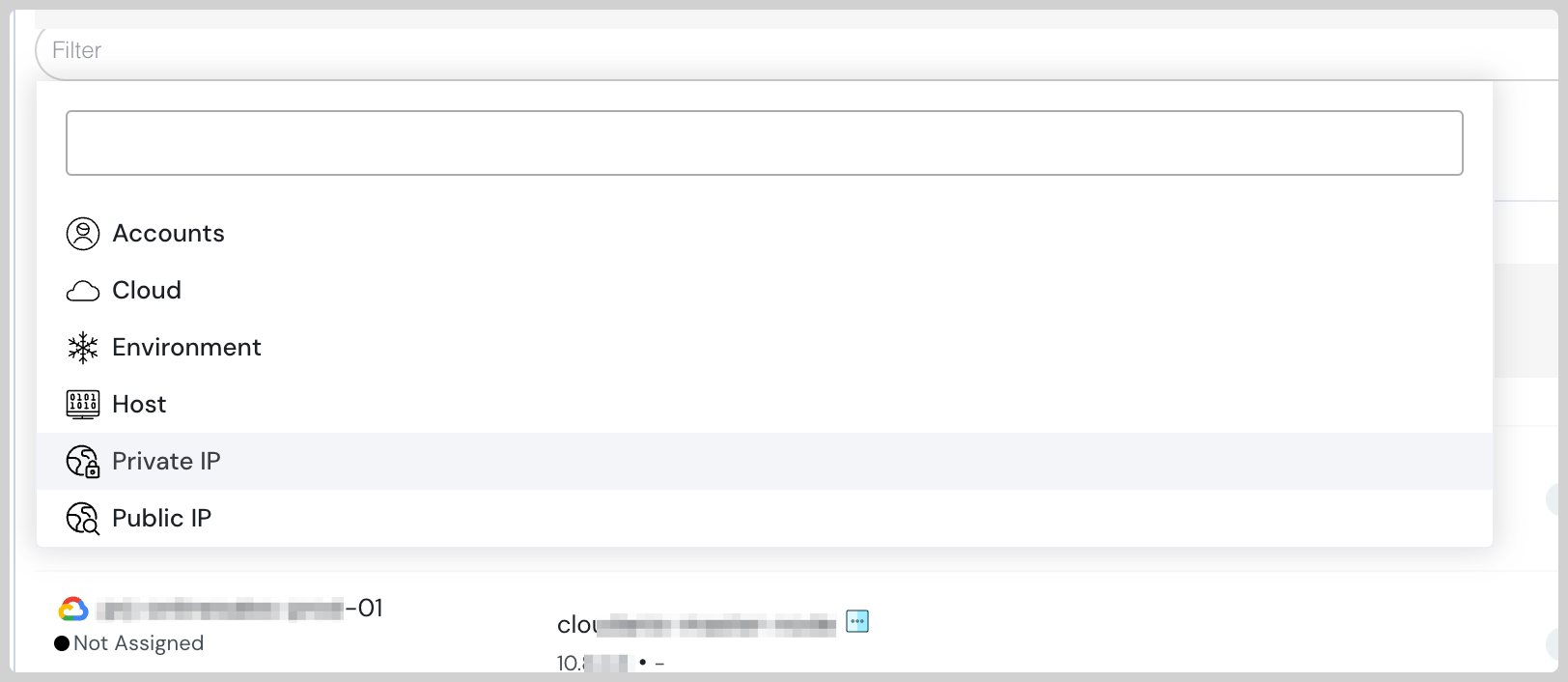 Cloudanix filter dashboard
Cloudanix filter dashboard
Monitor Public / Private Repositories across all code languages
With new filters, monitor both your Public and Private repositories. Also, use the Language filters to understand Code Security posture for all the environments used in the organization.
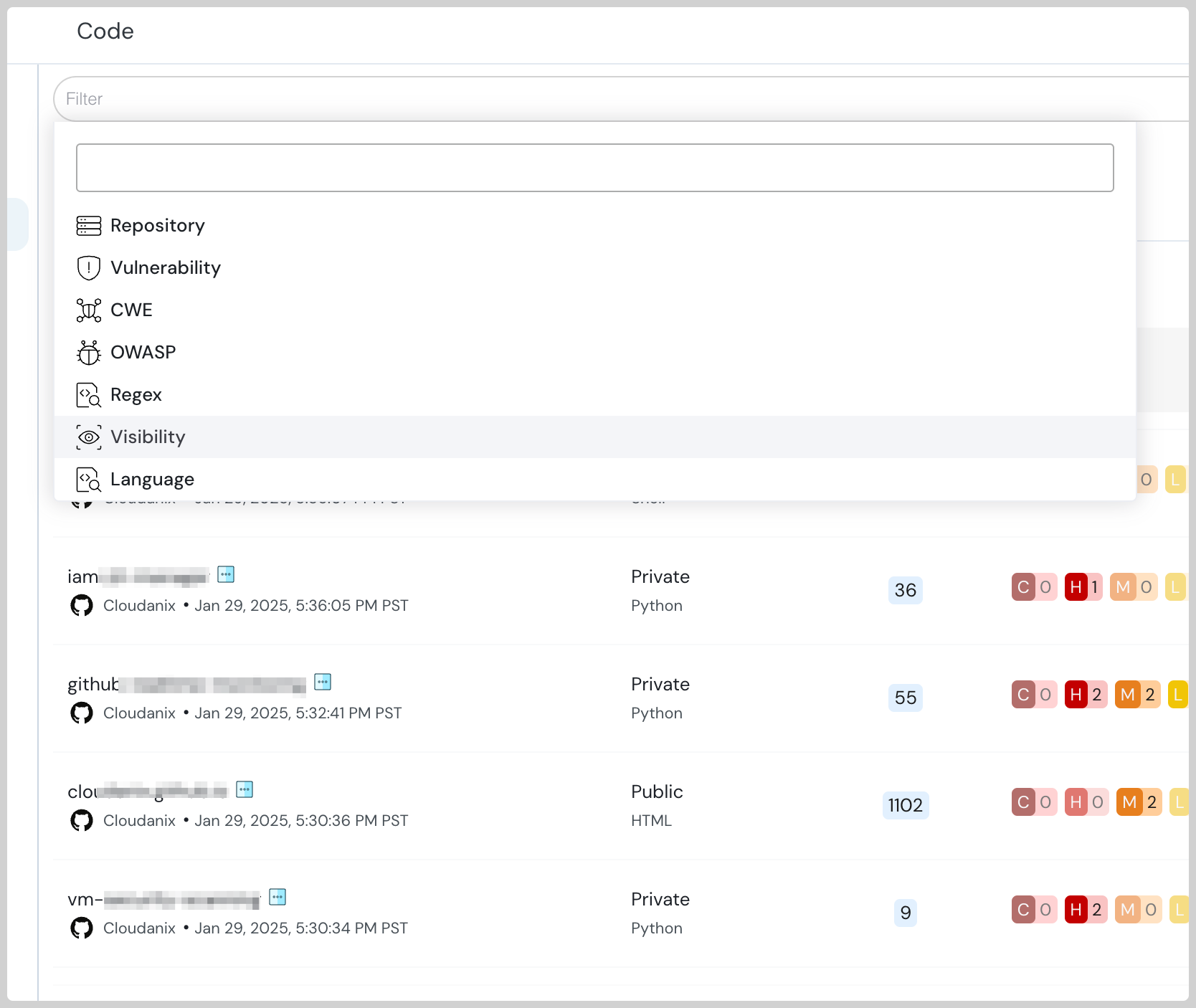 Cloudanix code security posture dashboard
Cloudanix code security posture dashboard
Cloudanix Resources
- Building Security Using Generative AI
- What is Incident Response? - Detailed Explanation
- Free Vendor Risk Assessment Template including Questionnaire
Resources over Internet
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedBlog
Read More Posts
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Wednesday, Nov 05, 2025
From Static to Strategic: Modernizing Privileged Access for Cloud Infrastructure
The promise of the cloud – agility, scalability, and innovation – has revolutionized how enterprises operate. Cloud infr
Read MoreTuesday, Sep 30, 2025
Eliminate Standing Access: Introducing JIT Kubernetes for Azure AKS Security
The Security Mandate: Why Permanent Access Fails Mission-Critical AKS Kubernetes has become the operating system of
Read MoreFriday, Aug 08, 2025
User Access Review in Cloud Security: A Foundational Guide to Securing Your Cloud Environment
Introduction: The Unseen Gatekeepers of Cloud Security In the rapidly expanding landscape of cloud computing, organi
Read More