Workload Protection & Platform Enhancements
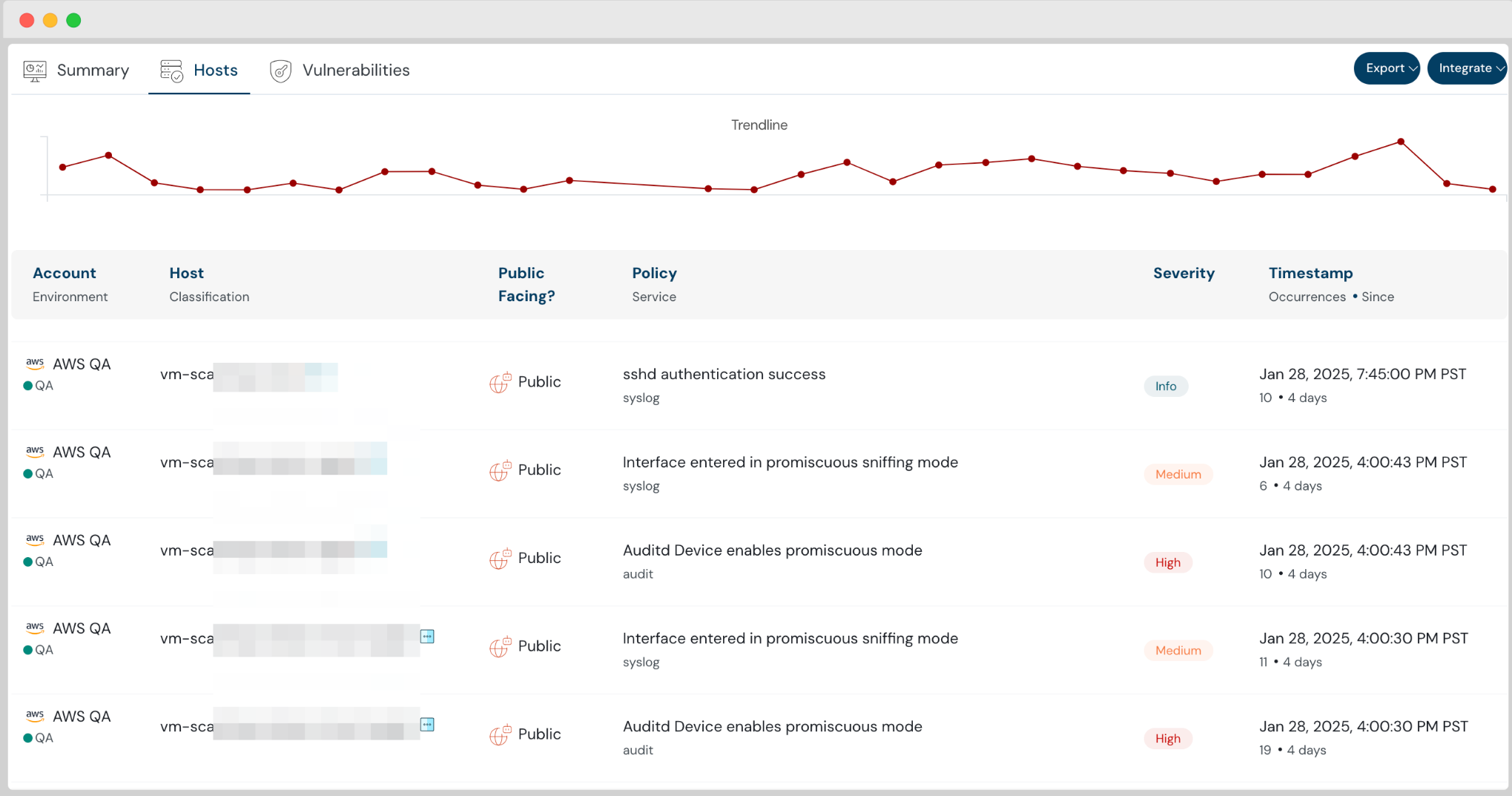
Protect Virtual Machines from Intrusion using Cloudanix IDS
The launch of Intrusion Detection System (IDS) for Virtual Machines further strengthens our Host Security Platform. As organizations scale their cloud infrastructure, attackers are constantly looking for vulnerabilities to exploit. Our IDS for Virtual Machines provides real-time threat detection, ensuring that malicious activities, unauthorized access attempts, and suspicious behaviors are instantly identified and addressed.
We continuously monitor VM traffic, logs, and system activities, leveraging behavioral analytics and signature-based detection to spot potential security threats. Whether it’s detecting zero-day attacks, insider threats, or anomalous access patterns, our IDS ensures that your virtual machines remain protected with continuous monitoring and automated alerts.
Request for Just In Time Access from Slack
Easily request and approve Just In Time access directly from Slack for faster workflows.
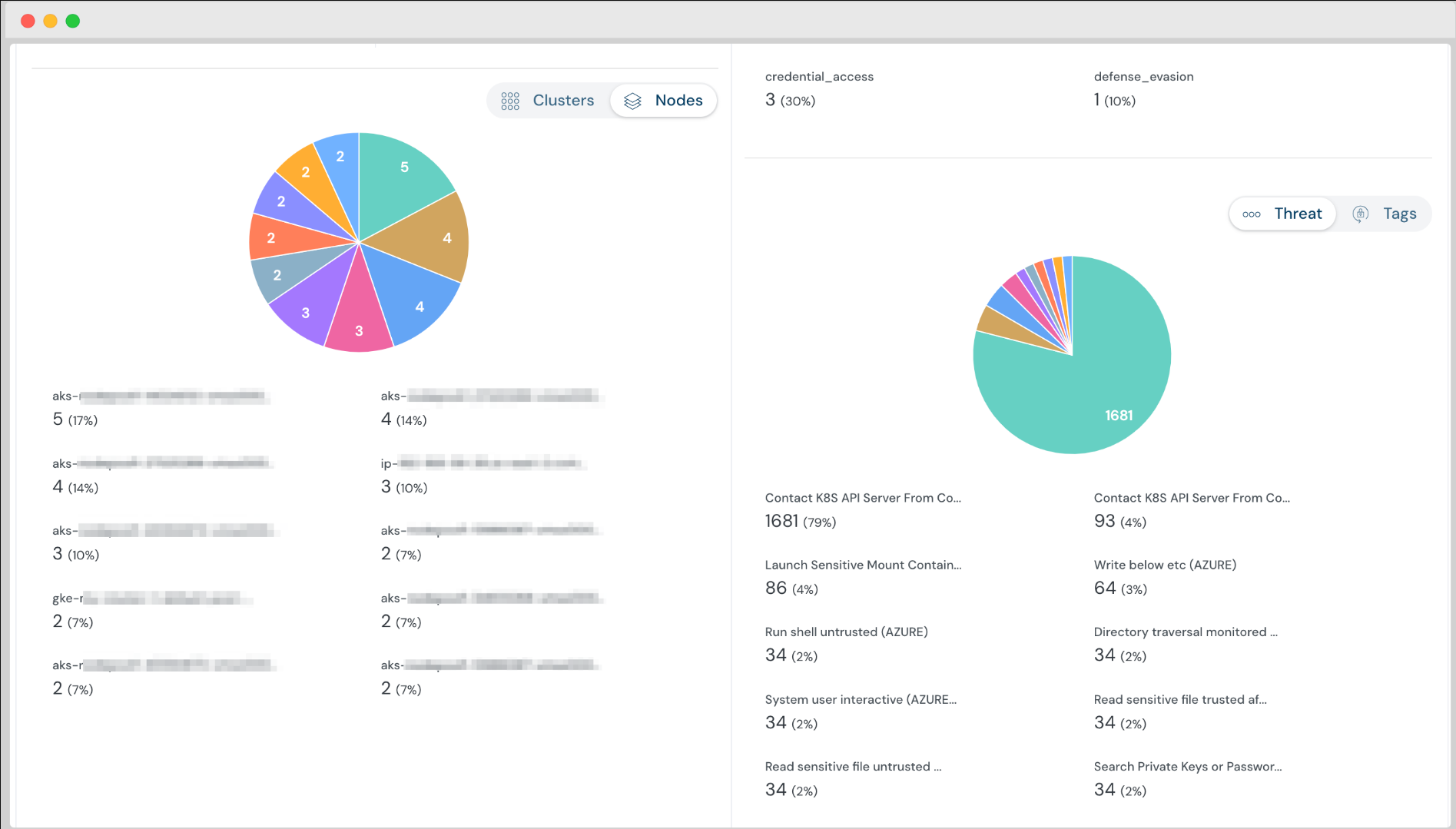
Kubernetes Runtime Security Monitoring at Node Level
Now, slice and dice runtime security threats at a node level — enabling you to analyze and prioritize node pools needing attention.
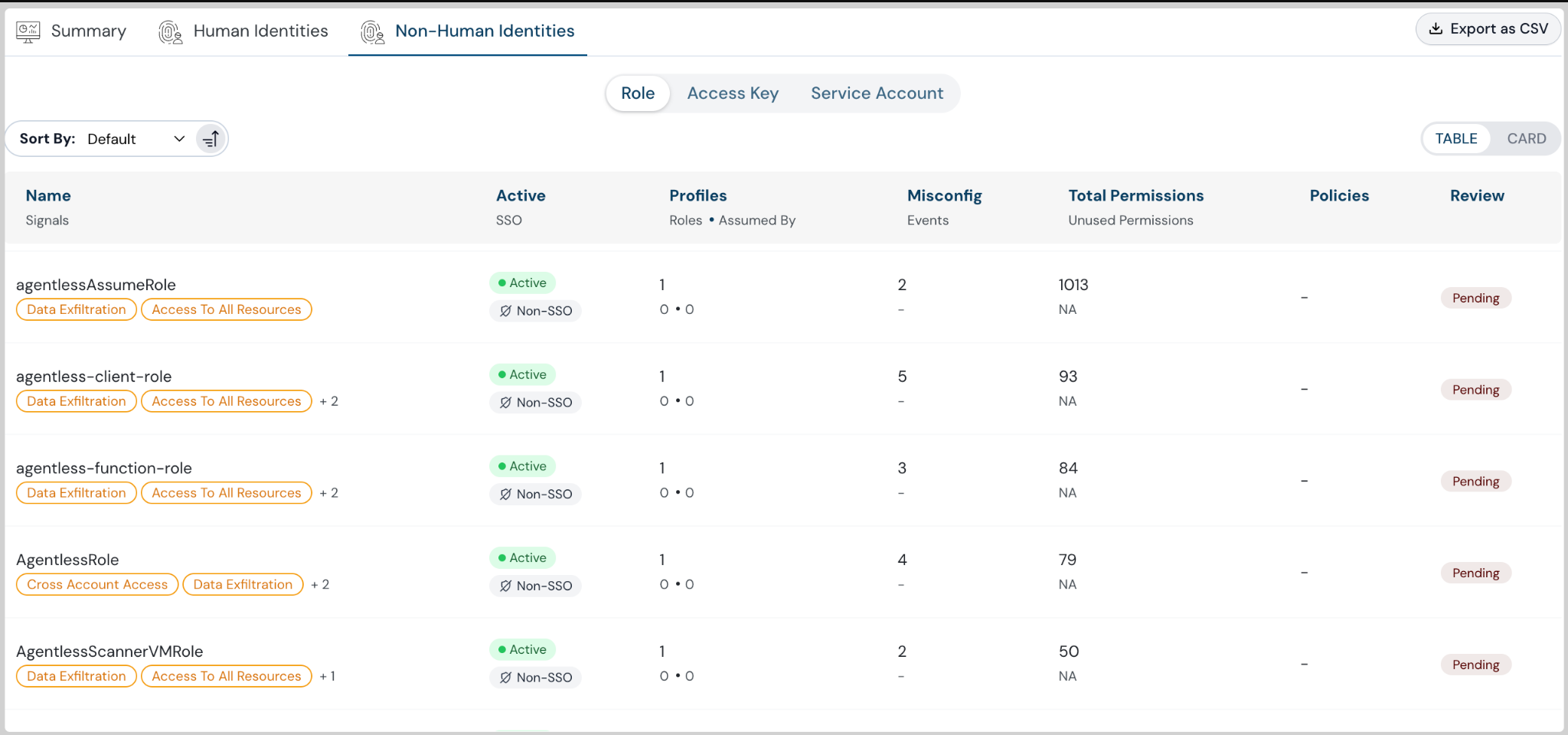
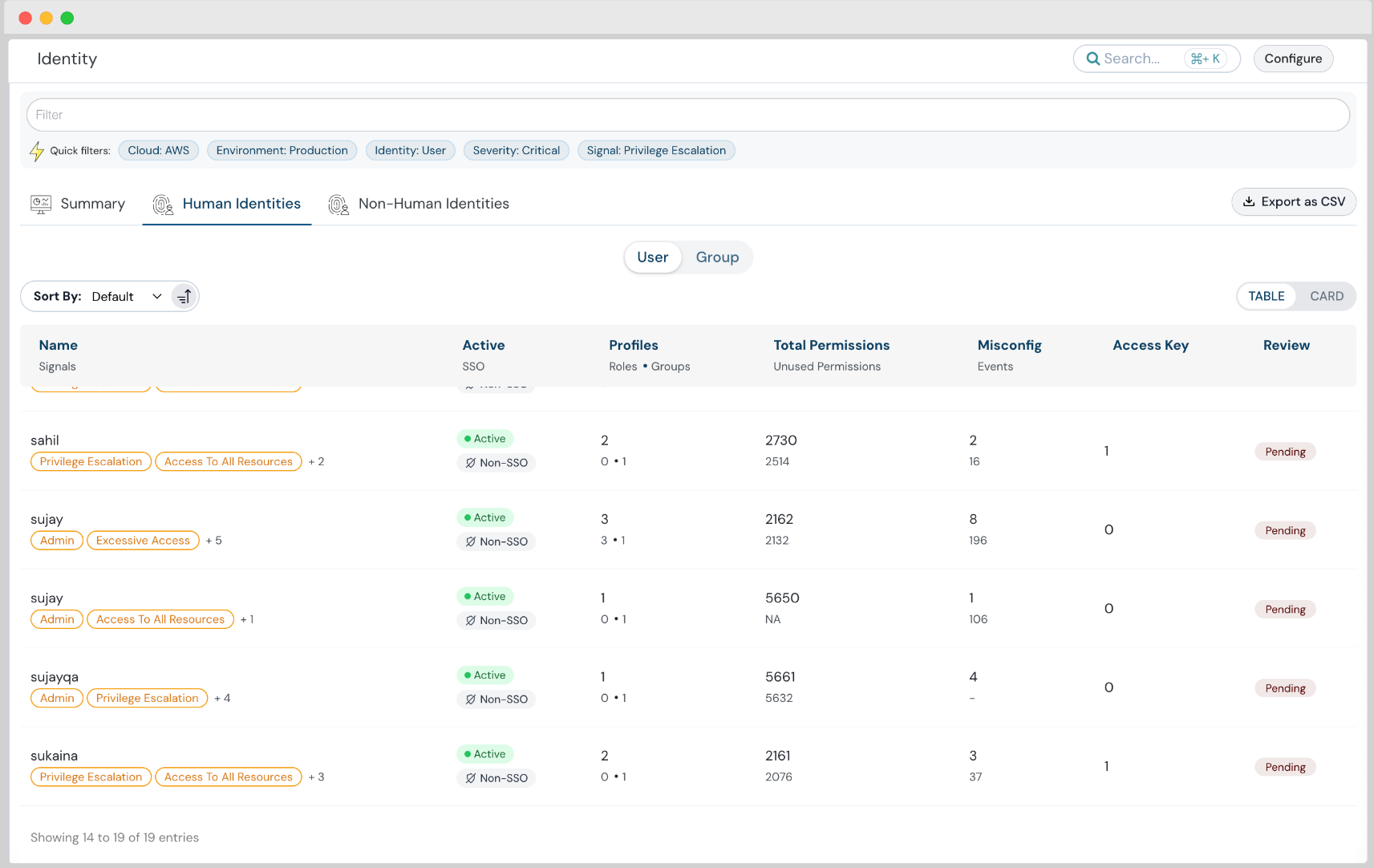
Identities Permission Analysis with Human and Non-Human Identity Segregation
With the latest release, gain deep visibility into identity risks. We now segregate human and non-human identities, making it easier to identify unused permissions, overly permissive identities, and cross-account access.
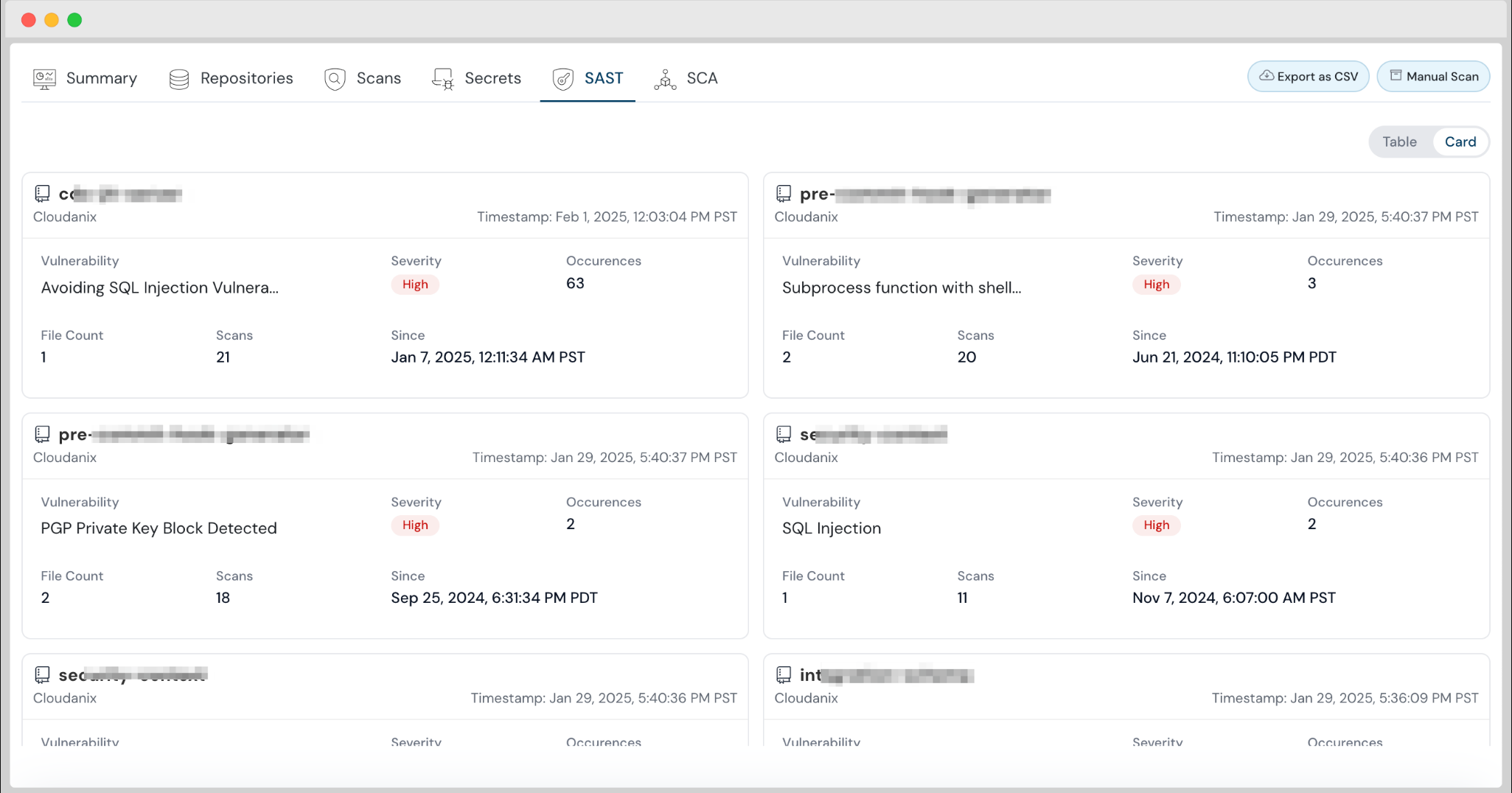
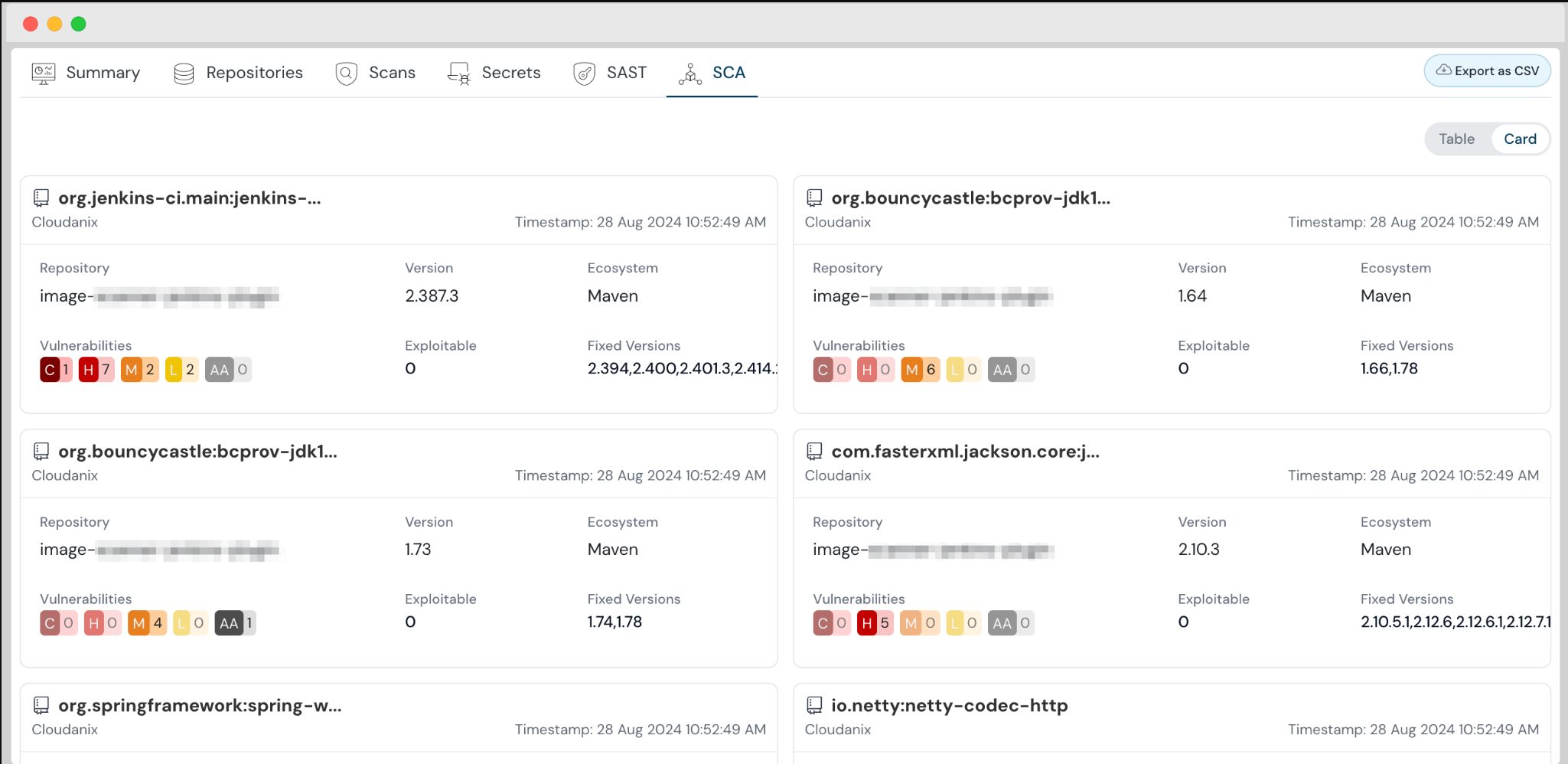
Enhanced Card Views for Code Security
Code Security is enhanced to present findings in a new Card view, helping you visualize issues in a more detailed and structured manner.
Cloudanix Blogs & Resources
- Source Code Security Best Practices
- What is Code Security?
- Top 10 Revised Code Security Best Practices for Developers
Industry News & External Reads
- OWASP Non-Human Identity (NHI) Top 10 - 2025
- AI Agent Identity: It’s Just OAuth — by Maya Kaczorowski
- Why Running as Root in Kubernetes Containers is Dangerous — by Marcin Wasiucionek
TODO:// is not an option for Cloud Security
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedBlog
Read More Posts
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Wednesday, Nov 05, 2025
From Static to Strategic: Modernizing Privileged Access for Cloud Infrastructure
The promise of the cloud – agility, scalability, and innovation – has revolutionized how enterprises operate. Cloud infr
Read MoreTuesday, Sep 30, 2025
Eliminate Standing Access: Introducing JIT Kubernetes for Azure AKS Security
The Security Mandate: Why Permanent Access Fails Mission-Critical AKS Kubernetes has become the operating system of
Read MoreFriday, Aug 08, 2025
User Access Review in Cloud Security: A Foundational Guide to Securing Your Cloud Environment
Introduction: The Unseen Gatekeepers of Cloud Security In the rapidly expanding landscape of cloud computing, organi
Read More