IAM JIT Integration with AWS Identity Center, Right Sizing Recommendations, Signals and Review
Cloudanix has spent February diligently tackling critical identity and access management (IAM) challenges that plague even seasoned industry leaders. Issues like ensuring proper access controls, managing granular permissions, avoiding orphaned access, and implementing Just-in-Time (JIT) access in hybrid environments with Active Directory from Microsoft, Google, etc., are now easier to address with Cloudanix.
IAM JIT Integration with AWS Identity Center
Cloudanix now offers fine-grained IAM Just-in-Time (JIT) access control with AWS Identity Center, enabling customers using SSO to elevate and revoke privileges for cloud users.
Control features include:
- Manage JIT eligibility for roles/permission sets
- Auto-approve requests for limited-permission roles
- Define maximum JIT access duration
- Tailor privileges with additional control levers
AWS account overview | Cloudanix
Managing the Identity source | Cloudanix
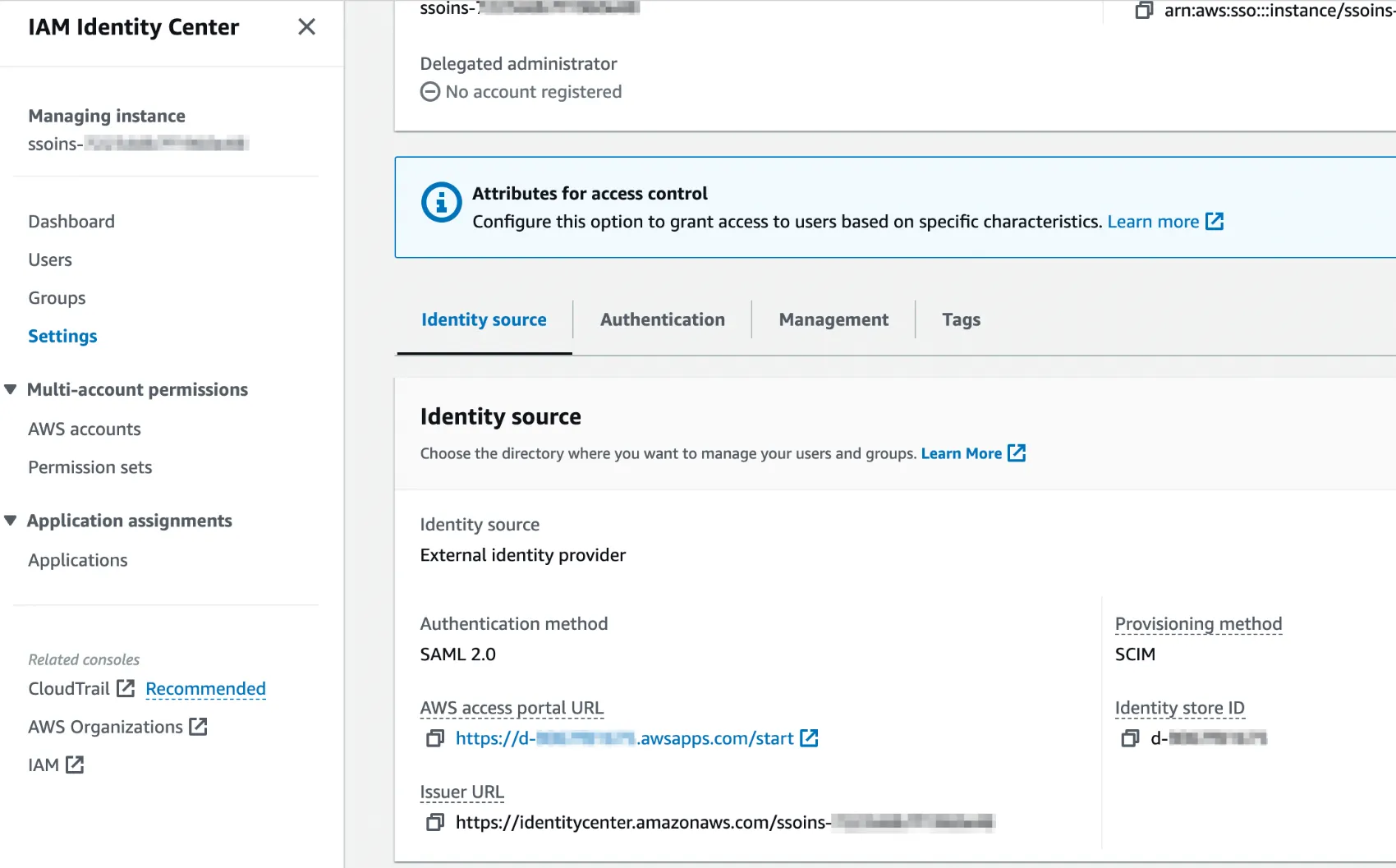
Manage your IAM JIT configuration | Cloudanix
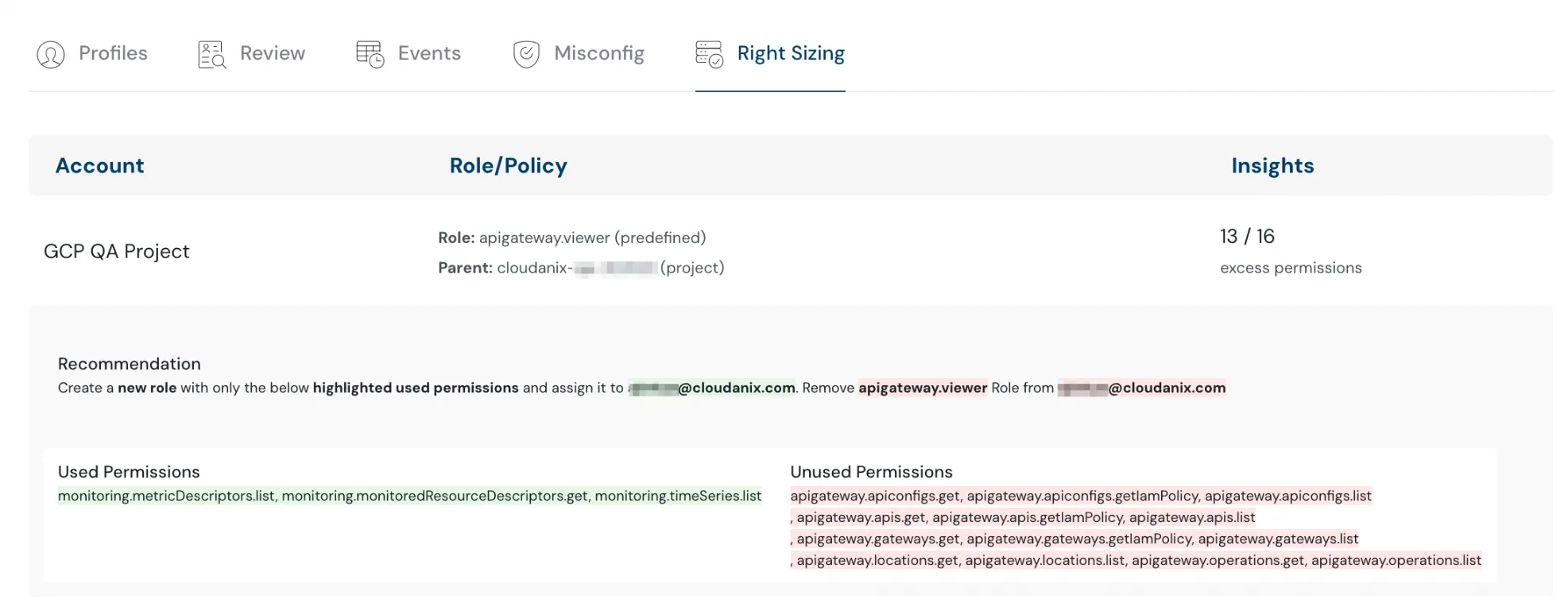
IAM Right Sizing Recommendations
Implement principle of least privilege with new recommendations based on actual user activity and permission usage patterns. Depending on usage:
- Define new, smaller policies
- Remove unused permissions entirely
IAM Rightsizing recommendations | Cloudanix
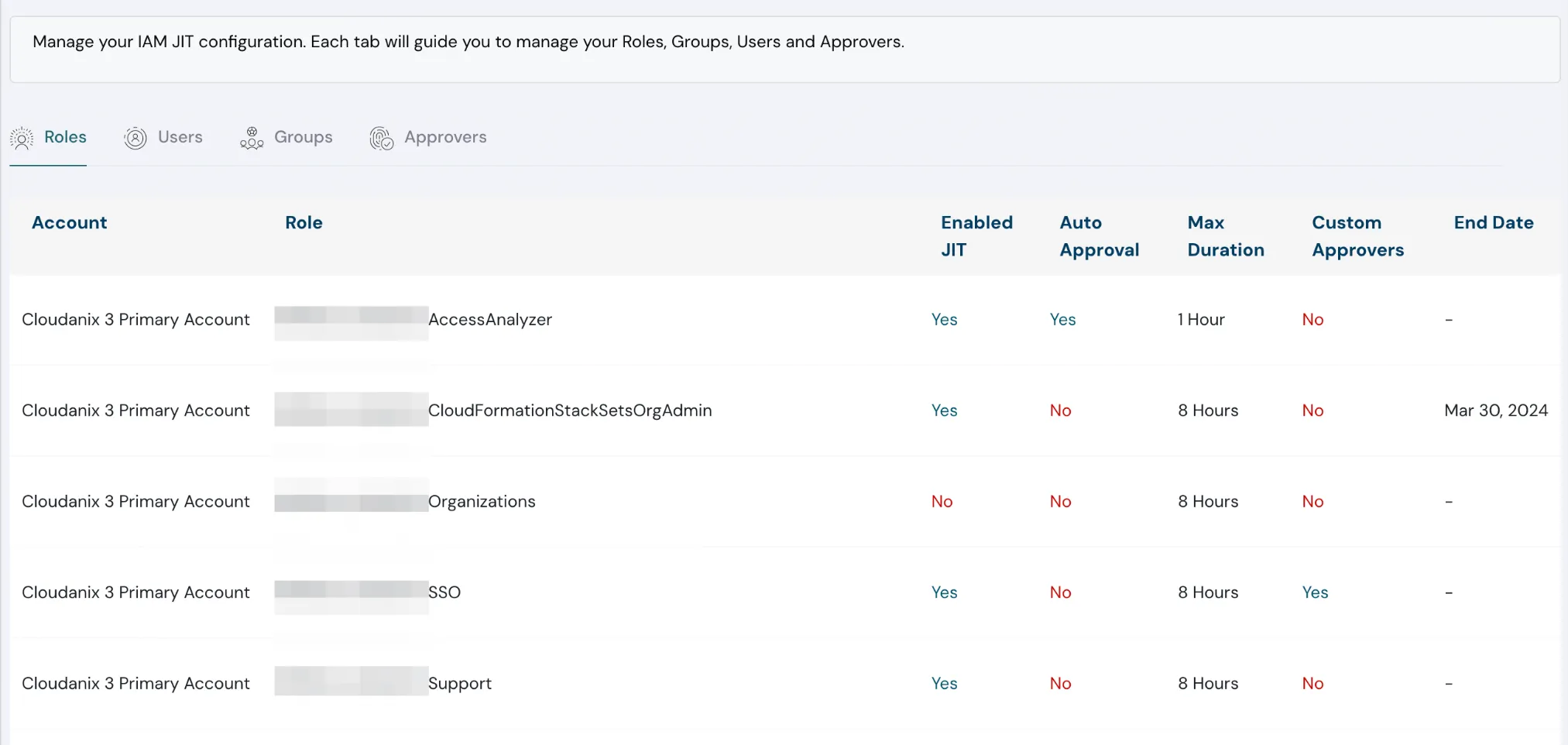
Streamline Reviews with “Not A Risk” Status
The new “Not A Risk” status allows reviewers to skip findings irrelevant to their business, speeding up the review process.
Risk review status section allowing to mark notes | Cloudanix
Extended IAM Signals
Gain deeper insight into IAM users and accounts:
- Distinguish between human and non-human accounts (service, third-party)
- Highlight the owner of IAM principals (internal vs. external vendors)
Cloudanix Blogs
- Top 10 Challenges with CSPM
- Real-Time Threat and Anomaly Detection for Workloads on AWS (co-authored with AWS)
- How Cloudanix Secures Containerized Applications Running on Amazon EKS (co-authored with AWS)
Additional Resources
Industry News
- An Infrastructure Engineer’s Opinionated Recommendations on Infra Tooling
- Rami McCarthy’s Review of State of ABAC in 2024
- Prevent Lateral Movement on GCP
- Privilege Management for Developers
- Audit EKS Permissions Used by Pods
TODO:// is not an option for Cloud Security
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedBlog
Read More Posts
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Tuesday, Feb 10, 2026
The 2026 CNAPP Compliance Framework: Turning Audit from Crisis to Continuity
Introduction: The Death of the Point-in-Time Audit In the high-velocity cloud landscape of 2026, the traditional app
Read MoreThursday, Feb 05, 2026
CSPM vs. CNAPP: Navigating Cloud Security Evolution for Modern Enterprises
The shift to cloud-native architectures represents a fundamental change in how applications are designed, built, and dep
Read MoreThursday, Jan 22, 2026
Top 10 Identity and Access Management Solutions
Identity and Access Management (IAM) has traditionally been considered one of the boring parts of security. But with the
Read More