Enhanced Vulnerability Management, Fine-Tune Code Security Settings & More
Fueled by your invaluable feedback, Cloudanix continues to evolve! This update prioritizes empowering you with better data consumption. Experience granular filtering controls, tailor your code security with advanced settings, and leverage enhanced reporting capabilities. We are committed to providing you with the tools you need to make informed decisions and achieve optimal security outcomes.
Read to see what we have cooked up for you.
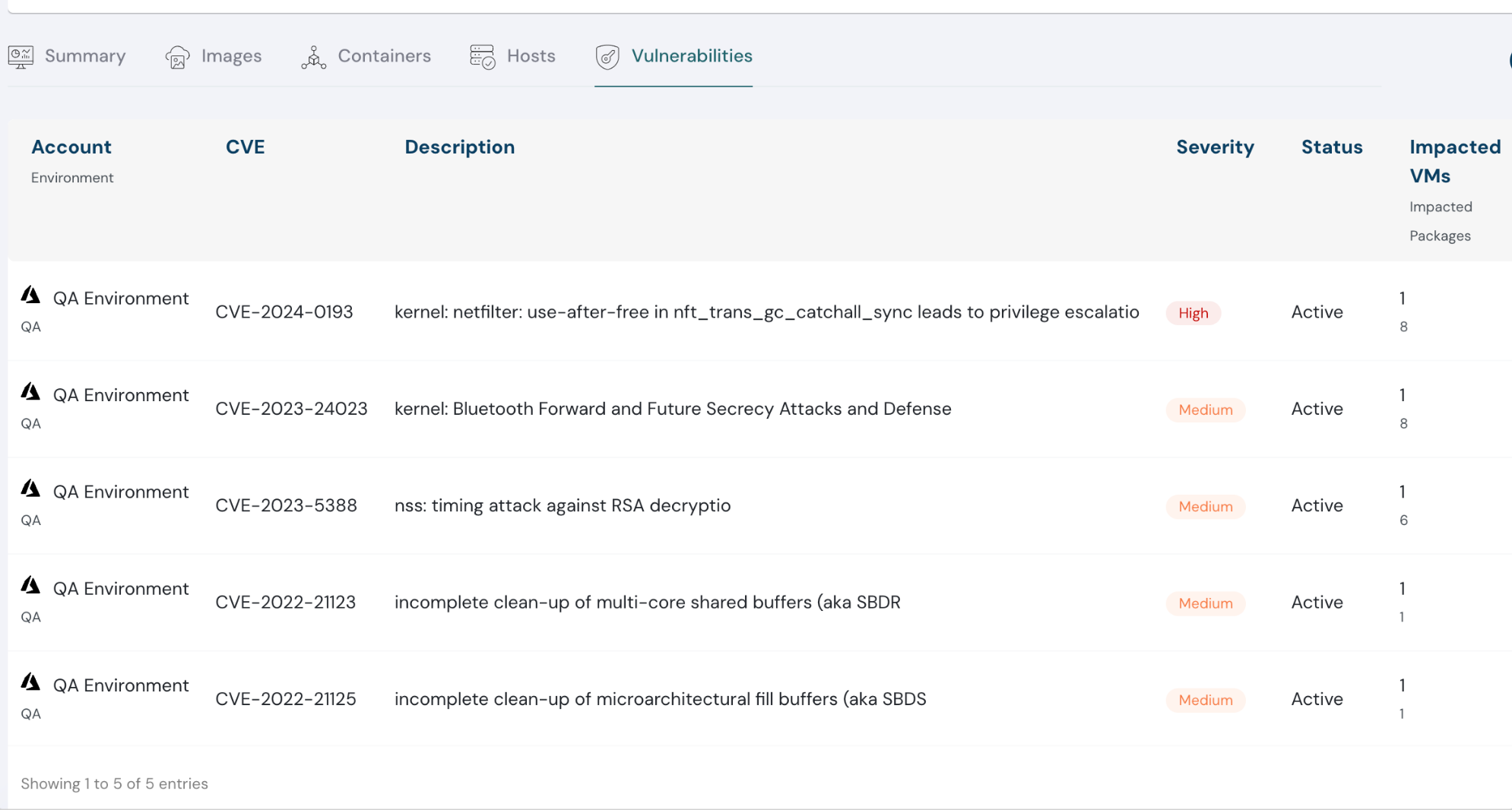
Vulnerability Management for Hosts
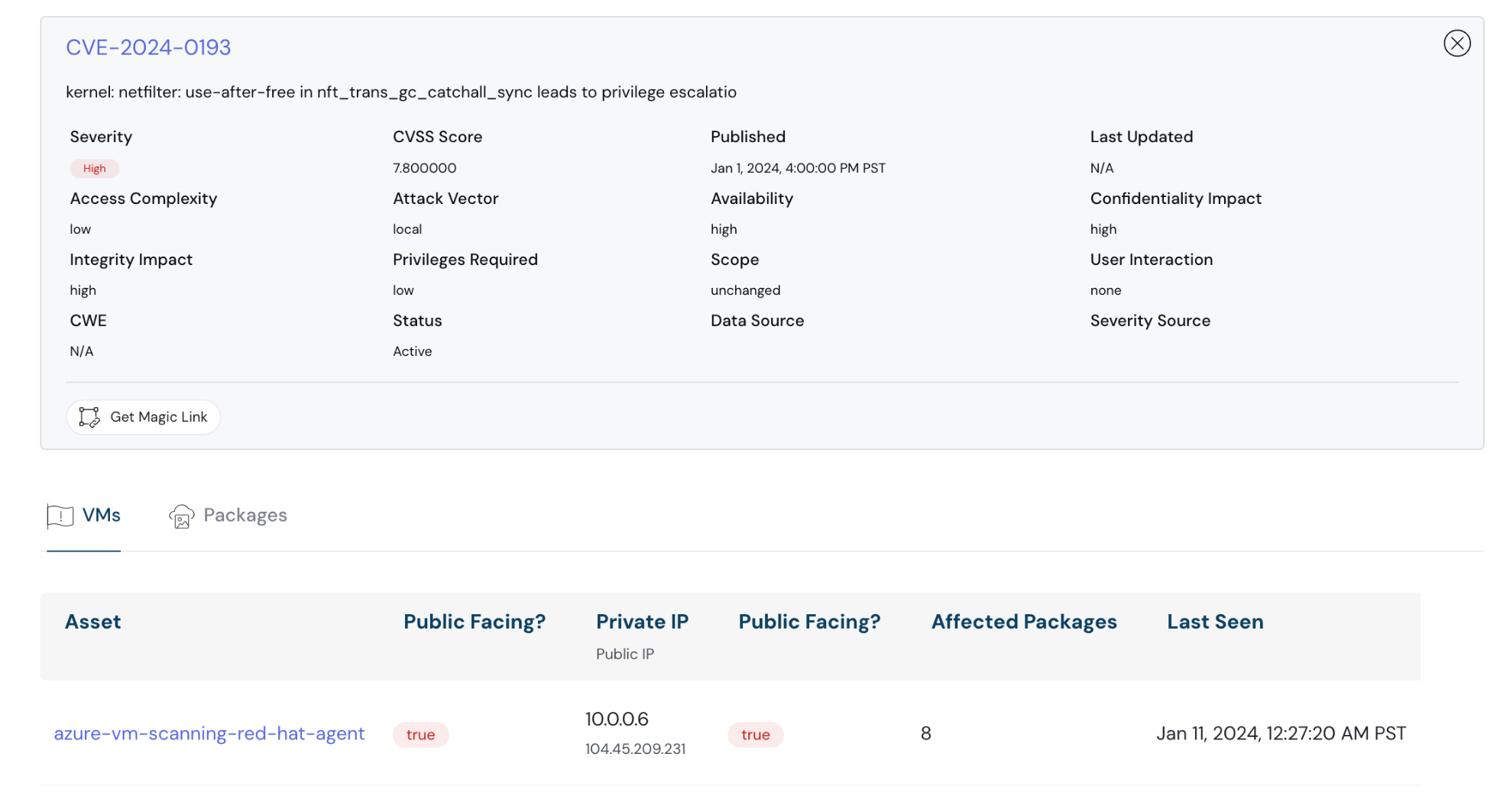
Now, gain complete control over your virtual machine security. See all open vulnerabilities at a glance, with detailed information on severity, exploit complexity, attack vectors, and other crucial factors. This enhanced visibility empowers you to prioritize threats effectively, streamlining your vulnerability triaging and remediation process.
Paired with existing File Integrity Monitoring and Malware Analysis, VM Vulnerabilities Management forms a powerful shield, keeping you one step ahead of attackers.
List of vulnerabilities in cloud environment — Cloudanix dashboard
Detailed information about the severity — Cloudanix dashboard
Improved Filter Control
Our all-new Filter Control empowers you to dissect your findings with better granularity. Simply choose your desired “Area of Filter,” then drill down and select the specific values you need.
This interface puts you in complete control, allowing you to effortlessly pinpoint the exact information you are searching for.
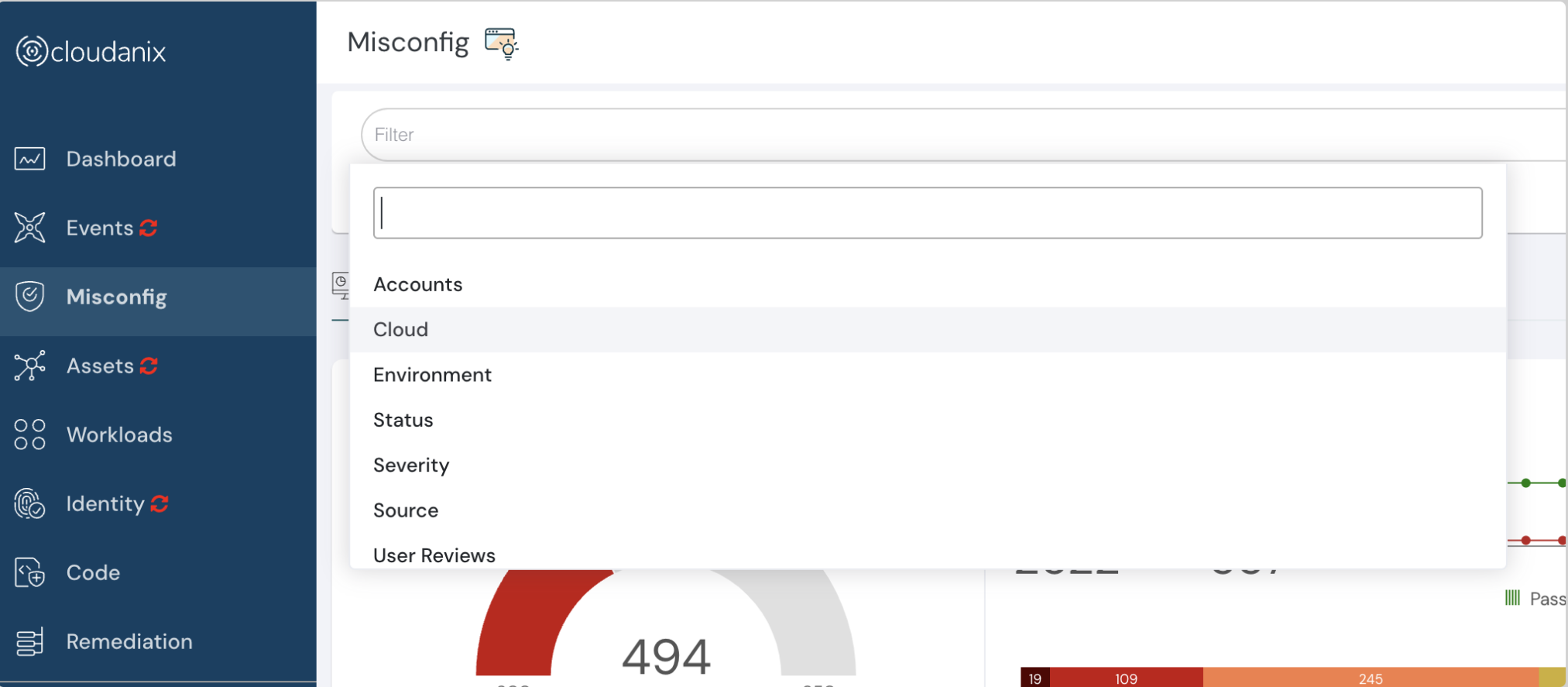 All new filter control feature
All new filter control feature
<img src=“/images/changelog/enhanced-vulnerability-management/enhanced-vulnerability-managementSS4.png” alt=“Software Screen-Shot” class=“rounded-2xl border-10 border-gray-50”
/> Controls based on severity
Code Security Settings
Each practitioner looks at Code Security in a slightly different way. To empower this diversity, we are introducing advanced Code Security Settings.
This allows you to define:
- Capabilities to use
- Scan Triggers
- Full Scan Schedule (Daily, Weekly, Monthly, etc.)
- PR Failure conditions (Critical Count, High Count, Allowed CVEs, etc.)
- Jira Integration parameters
This flexibility ensures Code Security that adapts to your development process, optimizing efficiency and maximizing security.
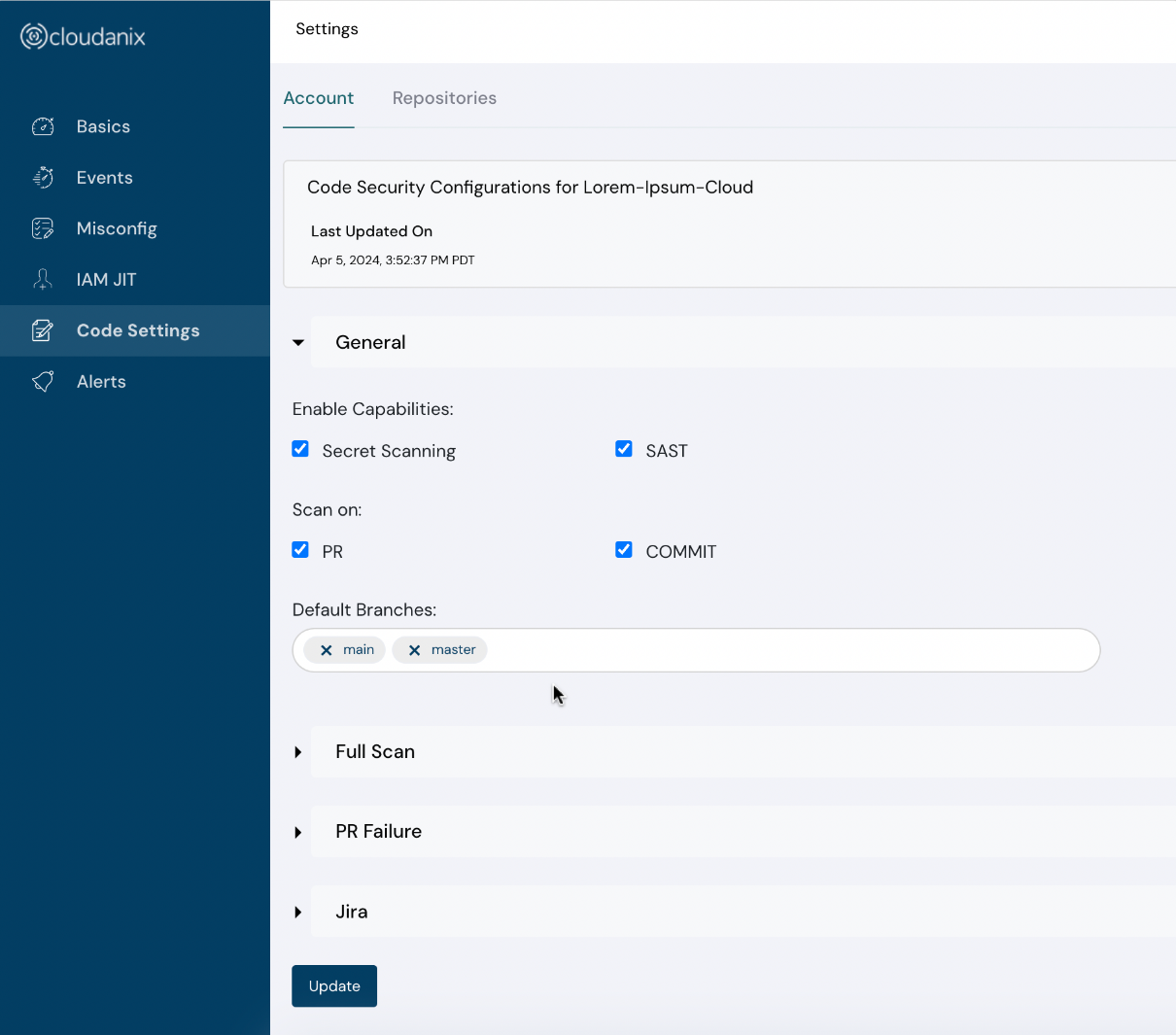
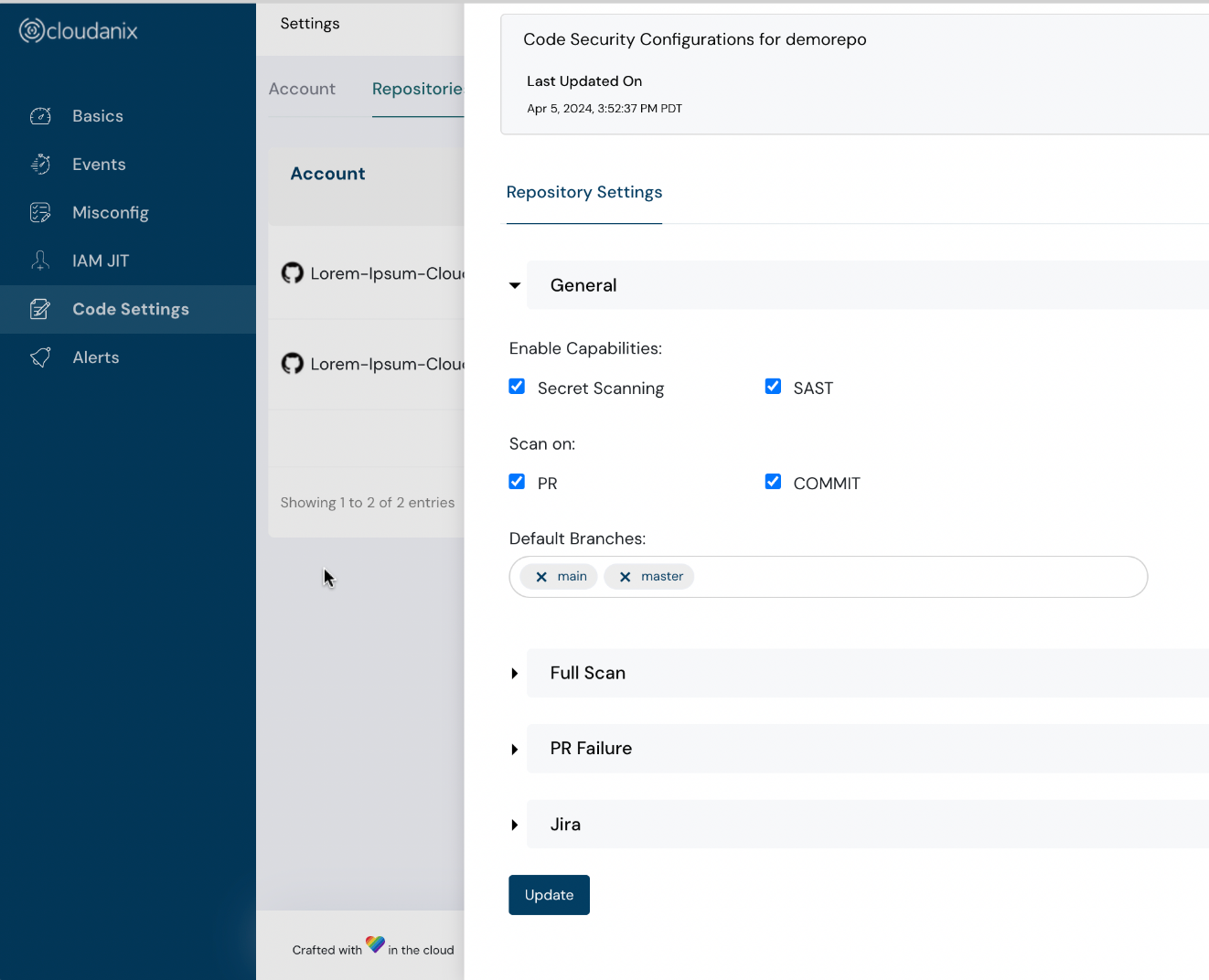
Code security settings screenshots
PDF Reports for Code & Host Security
Now you can generate detailed Security Posture Reports for Code Security and Host Security, and share them with other stakeholders inside and outside of the organization.
Blogs
- Top 12 Container Security Best Practices
- Unveiling Cloud Console Link Project - Your Shortcut to Cloud Resources
Additional Resources
Industry News
- Recipe for Scaling Security - David Dworken
- K8s Secure Design - Doyensec
- Logging at the scale of Cloudflare
- Supply Chain Attacks to rule them all - Adnan Khan
- AWS Security Mind Map - Artem Marusov
TODO:// is not an option for Cloud Security
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedBlog
Read More Posts
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Wednesday, Nov 05, 2025
From Static to Strategic: Modernizing Privileged Access for Cloud Infrastructure
The promise of the cloud – agility, scalability, and innovation – has revolutionized how enterprises operate. Cloud infr
Read MoreTuesday, Sep 30, 2025
Eliminate Standing Access: Introducing JIT Kubernetes for Azure AKS Security
The Security Mandate: Why Permanent Access Fails Mission-Critical AKS Kubernetes has become the operating system of
Read MoreFriday, Aug 08, 2025
User Access Review in Cloud Security: A Foundational Guide to Securing Your Cloud Environment
Introduction: The Unseen Gatekeepers of Cloud Security In the rapidly expanding landscape of cloud computing, organi
Read More