PagerDuty Addon, JIT for GCP & Subdomain Takeover Remediations
Overview
Gearing up for the festivities? We’ve got your back.
This update makes sure your cloud security is handled even when you’re away — with real-time alerts, expanded IAM coverage, and step-by-step remediation guides.
New Features
PagerDuty Addon
Integrate Cloudanix alerts directly into PagerDuty for streamlined incident management.
Enable it from the Alerts Settings page.
View PagerDuty Add-On →
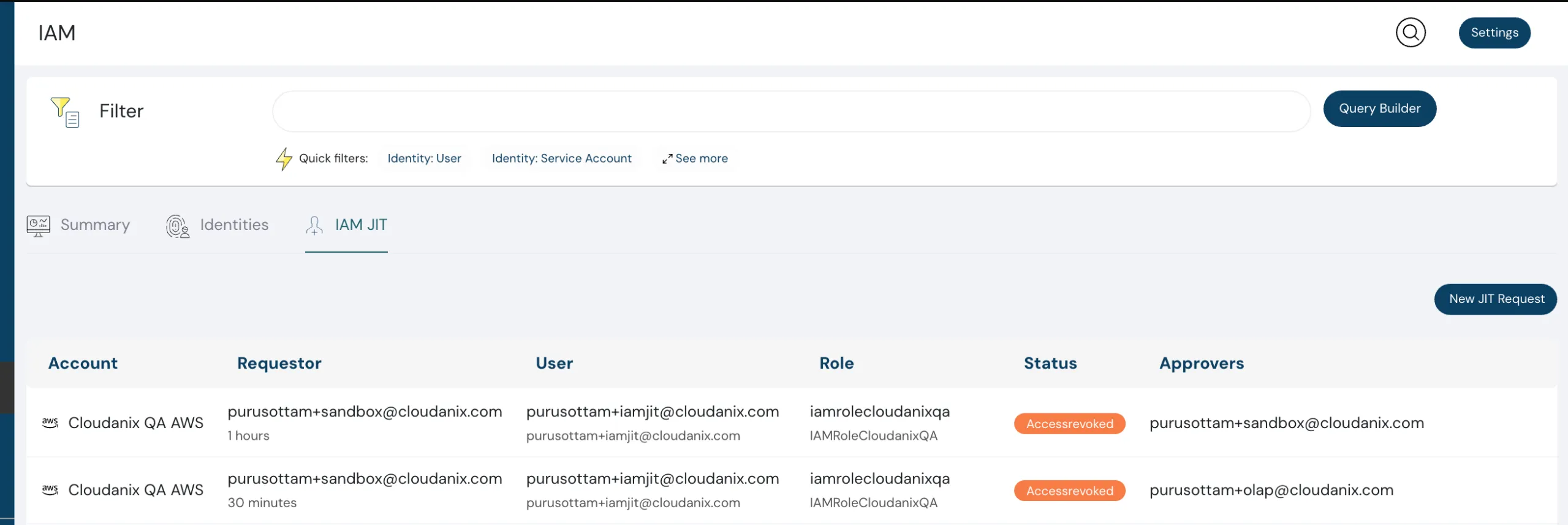
Just In Time (JIT) Access for GCP
Our IAM Just In Time access capability now supports Google Cloud Platform.
This helps you minimize standing privileges and follow best practices for least-privilege access.
Contact: support@cloudanix.com
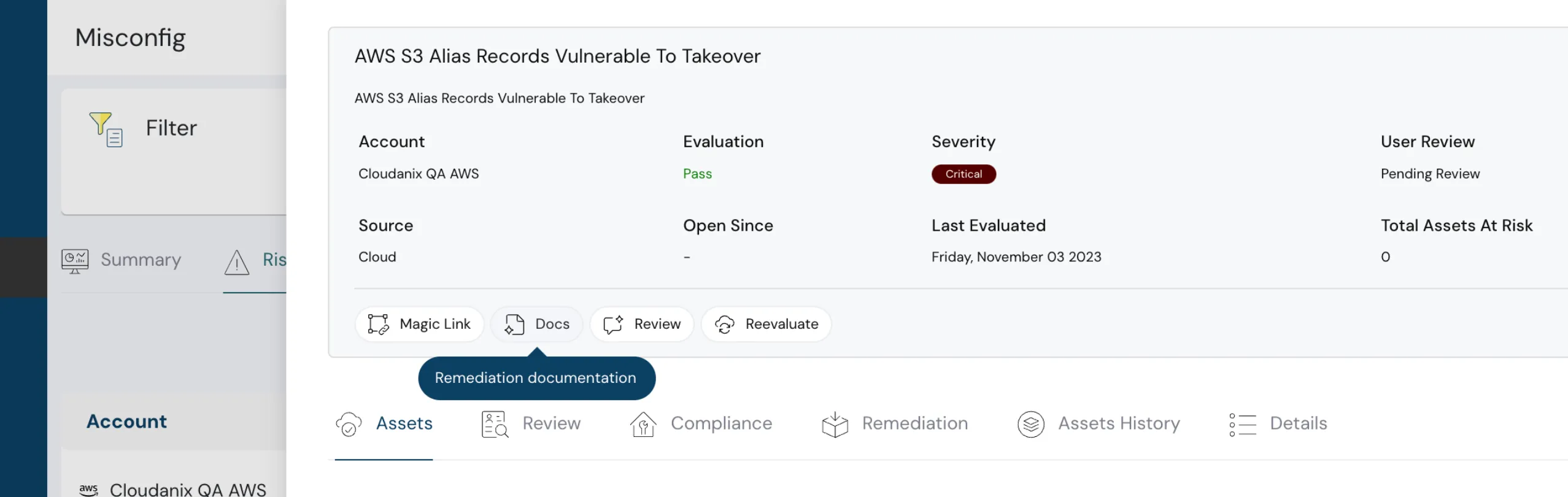
Remediation for Subdomain Takeover
You can now not only detect subdomain takeover risks but also access step-by-step remediation guides inside Cloudanix.
This makes fixing misconfigurations easier and faster.
Resources & Reading
- Announcing Cloudanix Code Security — Elevate your code’s defense.
- Security Best Practices for GitHub Actions
- GCP Security Command Center Attack Path Simulation and Exposure Scoring
- Lambda Function to Contain AWS Account Compromise
TODO:// is not an option for Cloud Security — Why security hygiene can’t wait.
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedBlog
Read More Posts
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Tuesday, Feb 10, 2026
The 2026 CNAPP Compliance Framework: Turning Audit from Crisis to Continuity
Introduction: The Death of the Point-in-Time Audit In the high-velocity cloud landscape of 2026, the traditional app
Read MoreThursday, Feb 05, 2026
CSPM vs. CNAPP: Navigating Cloud Security Evolution for Modern Enterprises
The shift to cloud-native architectures represents a fundamental change in how applications are designed, built, and dep
Read MoreThursday, Jan 22, 2026
Top 10 Identity and Access Management Solutions
Identity and Access Management (IAM) has traditionally been considered one of the boring parts of security. But with the
Read More