Code Security Enhancements, Full Scan Support, Image Vulnerability Triaging, and More
Code Security Enhancements
With this release, there are major enhancements to Code Security:
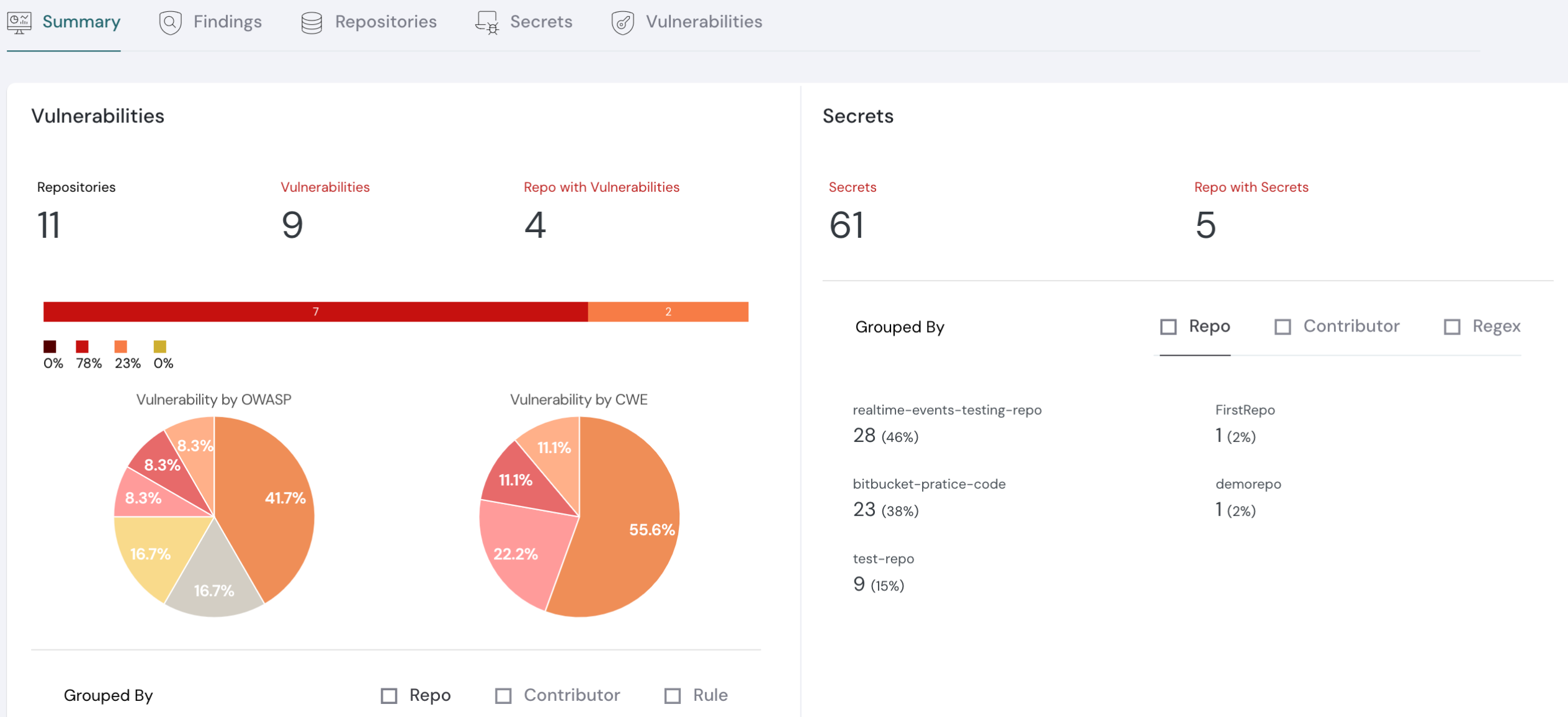
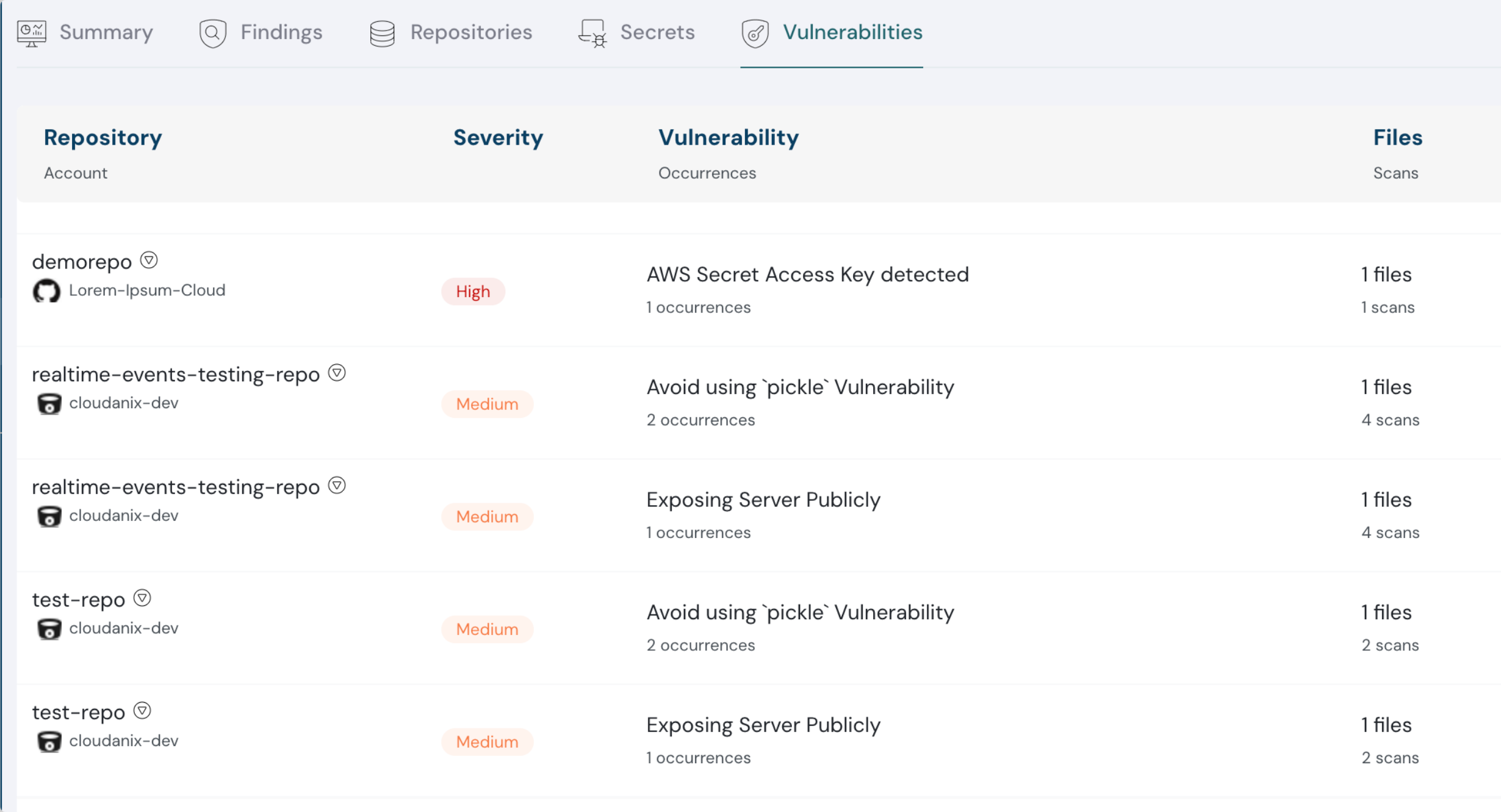
- Dedicated sections for Secrets and Vulnerabilities to dig deeper into occurrences, mapping them to files and scans.
- Improved triaging of detected secrets and vulnerabilities.
The secrets scan dashboard
List of vulnerabilities in code
Full Scan Support
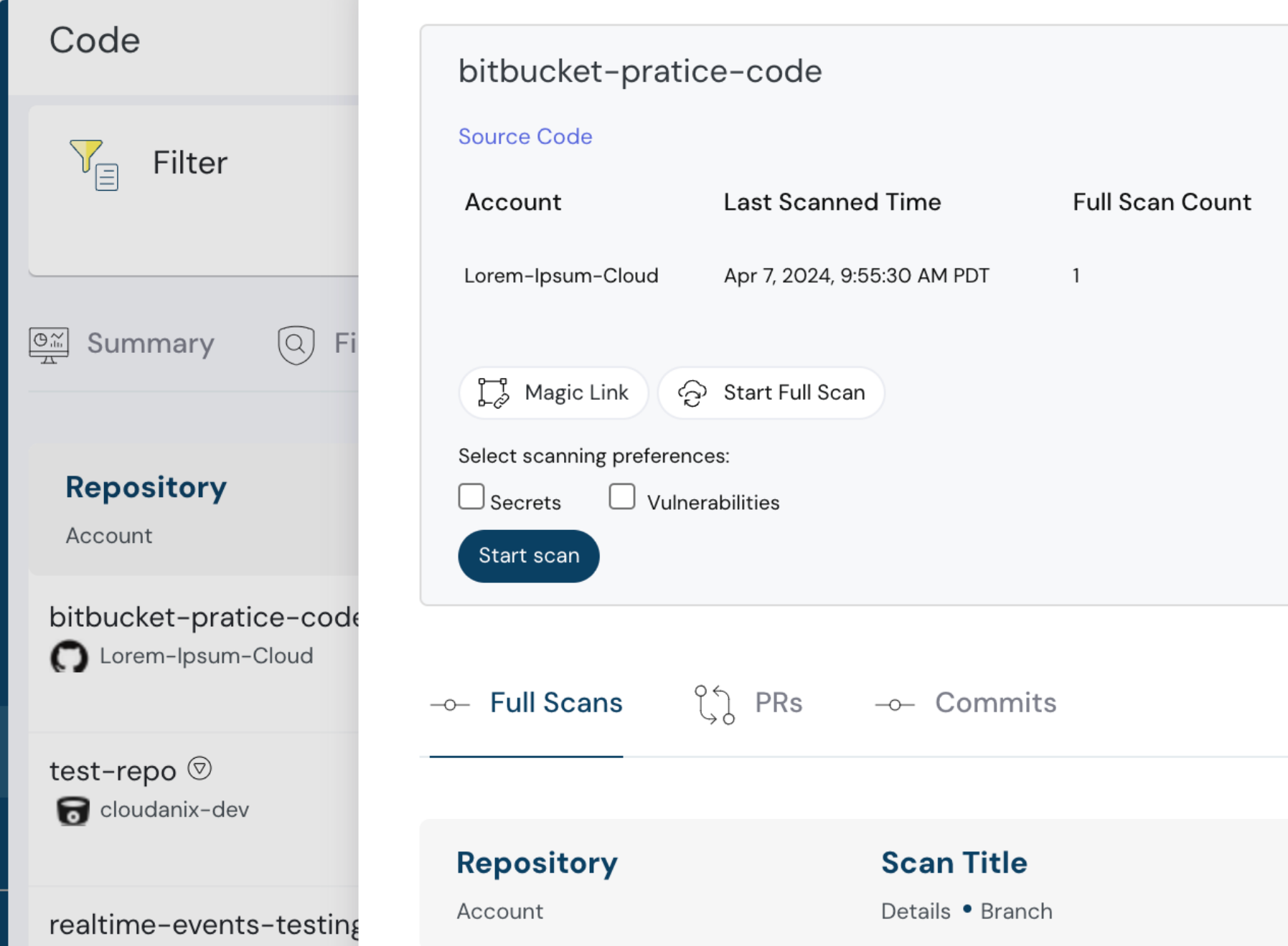
Initiate a Full Scan for GitHub or Bitbucket repositories directly from the Cloudanix Console.
This provides flexibility to start scans at will, in addition to the Weekly Automated Full Scans.
Full Scan Report for GitHub or Bitbucket
PR Check, Status, and Comments
With the latest release, customers can:
- Enforce PR Checks to fail builds based on acceptable conditions
- Add automated comments in PRs based on findings
- Insert findings status in the PRs
This reduces friction between Engineering and Security by limiting security gaps in code from reaching production.
Enforce PR Checks to fail builds based on an acceptable condition
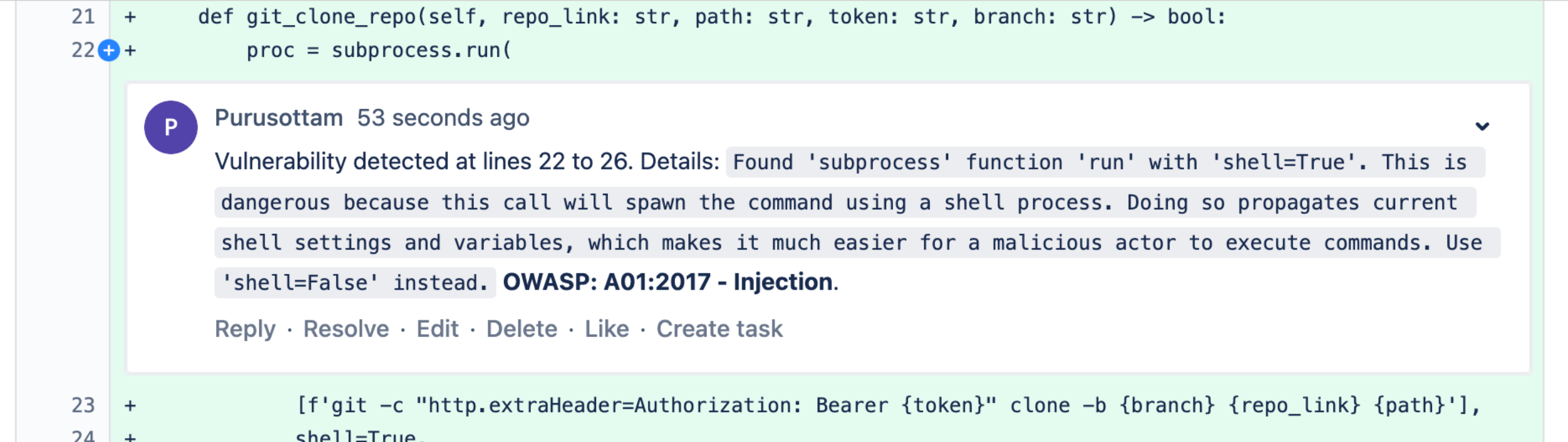
Image Vulnerability Triage
Slice and dice image vulnerability data even further using CVE or package-based filters.
Misconfiguration Policy Enhancements
We’ve expanded our AWS Misconfiguration Policy Set by another 150 policies, bringing the total to over 610. These additions provide parity with AWS Config and cover security rules across most AWS services.
Cloudanix Blogs
- Integrate IAM JIT for AWS Identity Center
- CSPM & Challenges of CSPM
- Real-Time Threat and Anomaly Detection for Workloads on AWS (co-authored with AWS)
- Announcing Cloudanix Code Security: Elevate Your Code’s Defense
Additional Resources
- Benefits of Using the Right CIEM Solution and How To Choose
- What is Code Security?
- What is Platform Engineering?
Industry News
- A Deep Dive of AWS Ransomware Attack
- Rippling’s Unique Take on Building SIEM In-House
- Declarative Images Using Code at ChainGuard
- Least Privilege and the False Sense of Security
- GitHub’s Approach to Security, Availability, and Accessibility
TODO:// is not an option for Cloud Security
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedBlog
Read More Posts
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Wednesday, Nov 05, 2025
From Static to Strategic: Modernizing Privileged Access for Cloud Infrastructure
The promise of the cloud – agility, scalability, and innovation – has revolutionized how enterprises operate. Cloud infr
Read MoreTuesday, Sep 30, 2025
Eliminate Standing Access: Introducing JIT Kubernetes for Azure AKS Security
The Security Mandate: Why Permanent Access Fails Mission-Critical AKS Kubernetes has become the operating system of
Read MoreFriday, Aug 08, 2025
User Access Review in Cloud Security: A Foundational Guide to Securing Your Cloud Environment
Introduction: The Unseen Gatekeepers of Cloud Security In the rapidly expanding landscape of cloud computing, organi
Read More