Code Quality Gate Thresholds, Infrastructure Classifications and More
Code security took center stage in our sprints last month. Enhancing and building deeper checks and capabilities that ensure the code checked in is safe from exploits. Some of the things we’ve worked on are enforcing thresholds for PRs using Cloudanix Quality Gate, consolidated report with Code Insights, use tagging for classification of your application and data, and more.
Enforce Thresholds for Your PRs Using Cloudanix Quality Gate
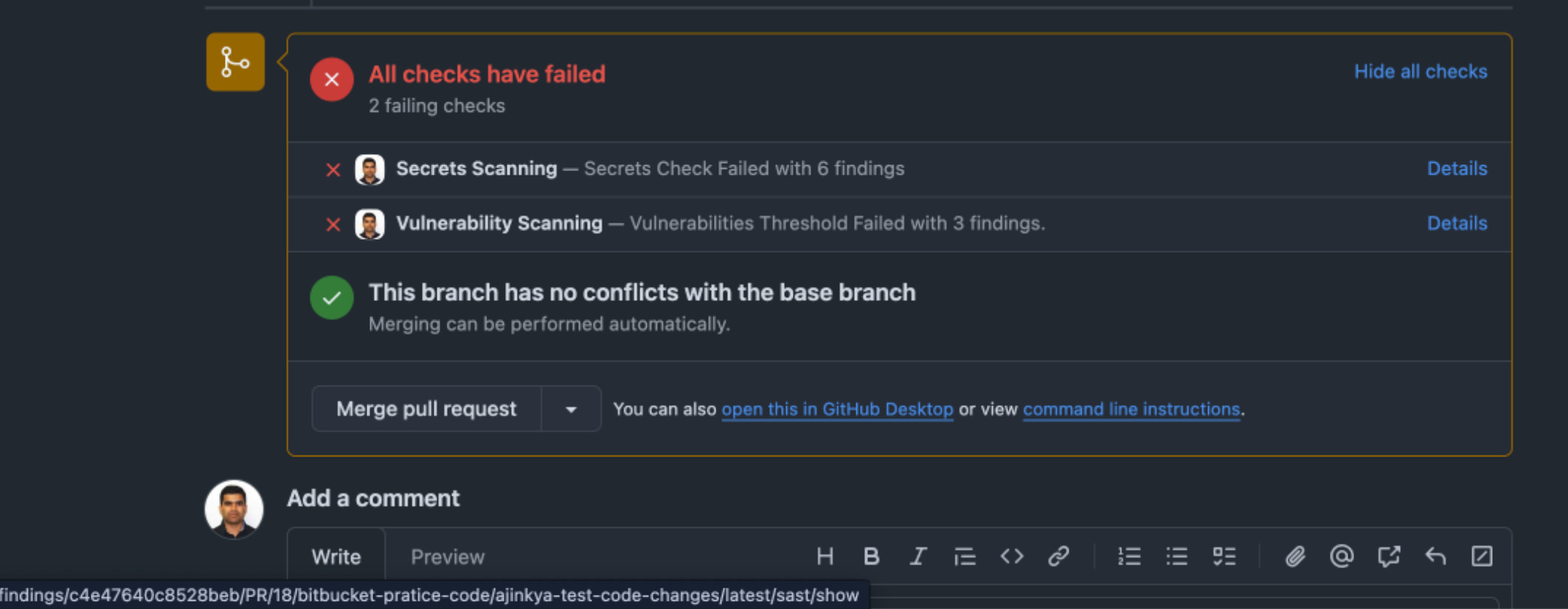
With Cloudanix Quality Gate capability, Security Teams and Engineering Managers can enforce thresholds for PRs. This enables Developers to focus on the most important security gaps in the world of noise.
Thresholds include Vulnerability Counts by Severity, Allowed & Denied CVEs, Allowed CWEs, etc.
Enforce thresholds for your PRs using Cloudanix Quality Gate
One Consolidated Report with Code Insights
In Bitbucket, integrate Cloudanix to generate Annotations. Improve code quality in the Pull Requests via the Code Review process in the Reports.
Annotations include capabilities like Secrets Detection, Vulnerability Scanning (SAST) and Supply Chain Security (SCA).
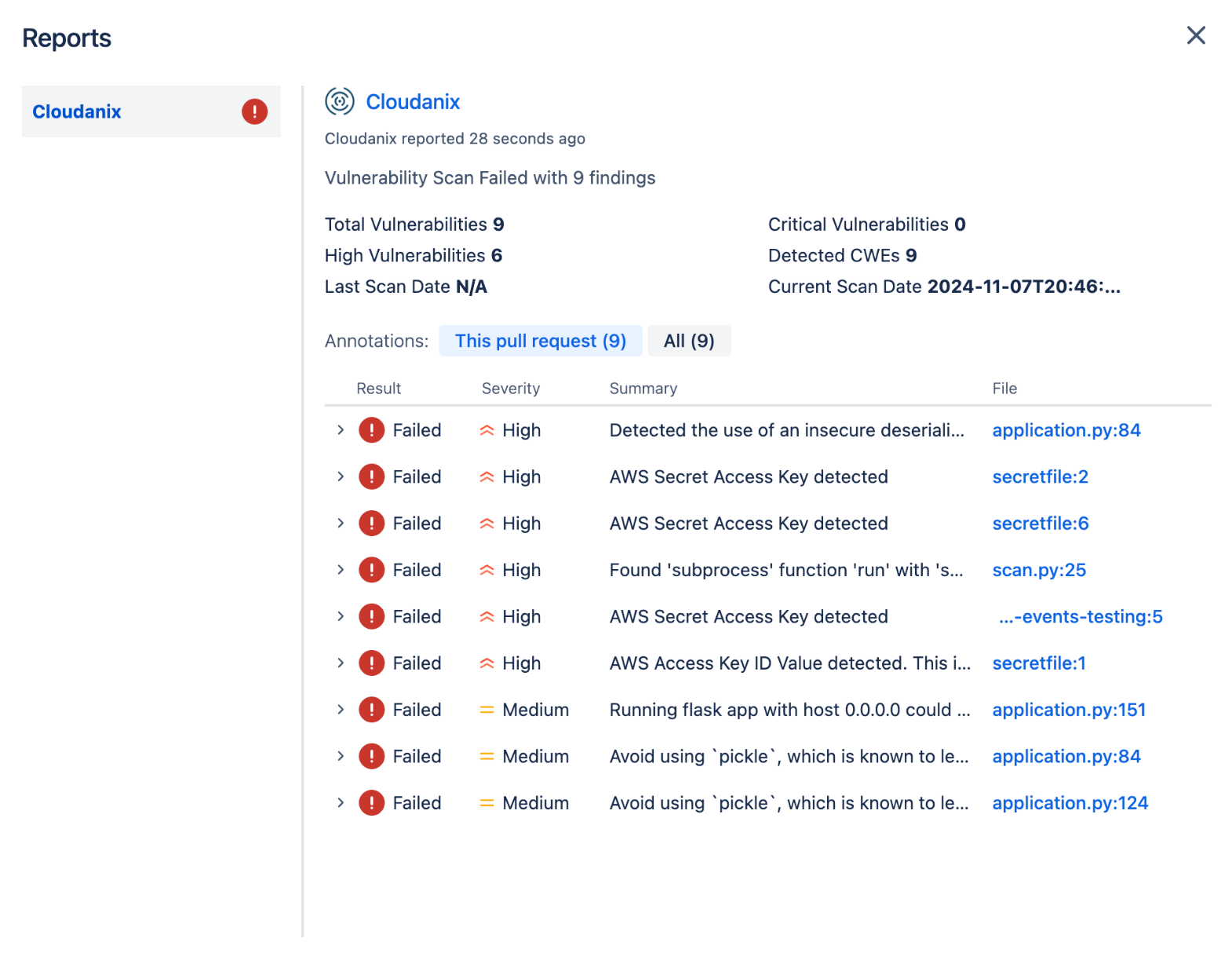 One consolidated report with Code Insights
One consolidated report with Code Insights
 One consolidated report with Code Insights
One consolidated report with Code Insights
Understand Sensitivity of Your Infrastructure Using Classifications
Not all infrastructure is created equal. With the latest release, tag your applications and data with different classifications.
This helps Cloudanix understand the sensitivity of the infrastructure and data.
Use the classifications to slice and dice better in the Platform.
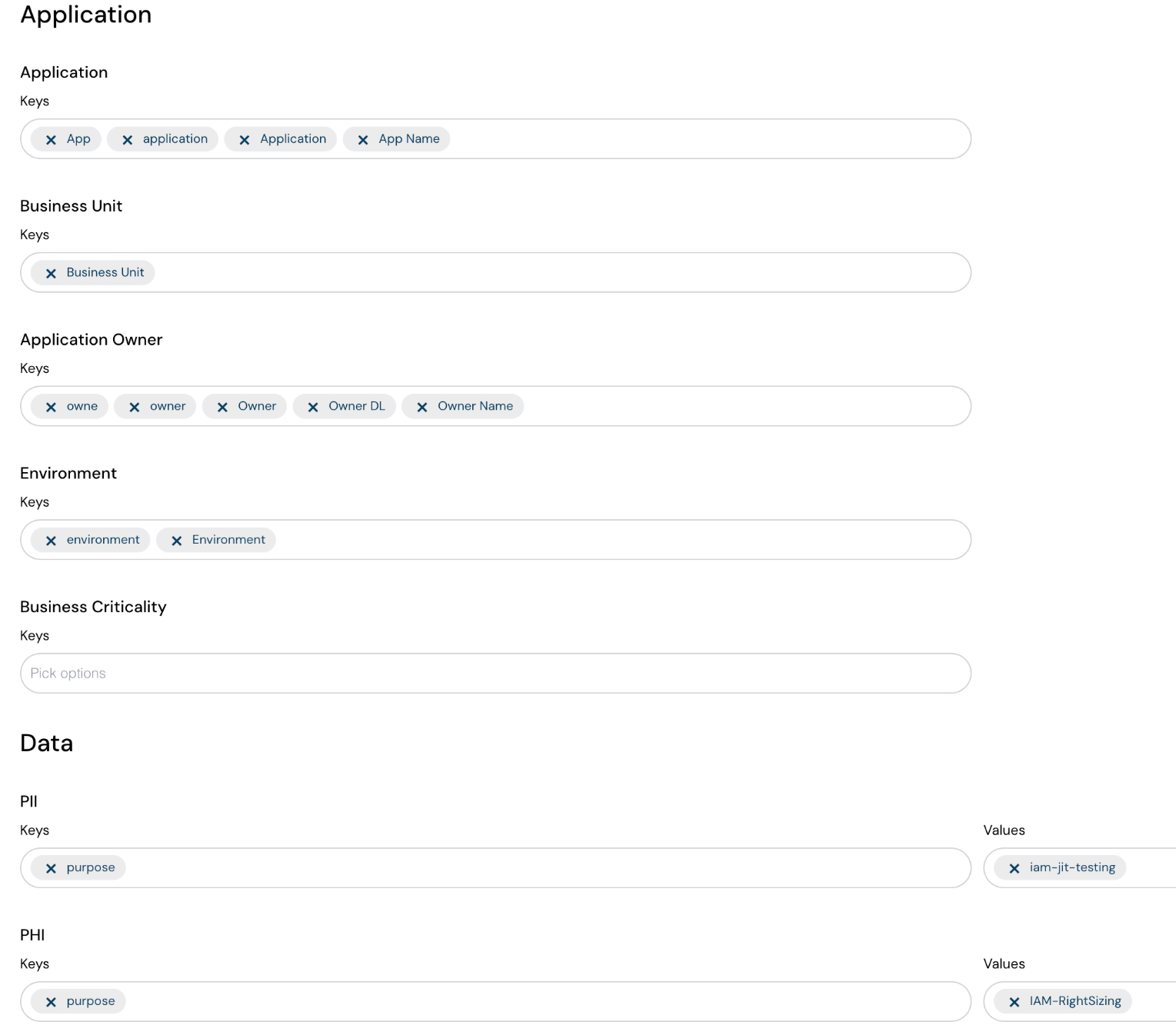 Tag your Applications and Data with different classifications
Tag your Applications and Data with different classifications
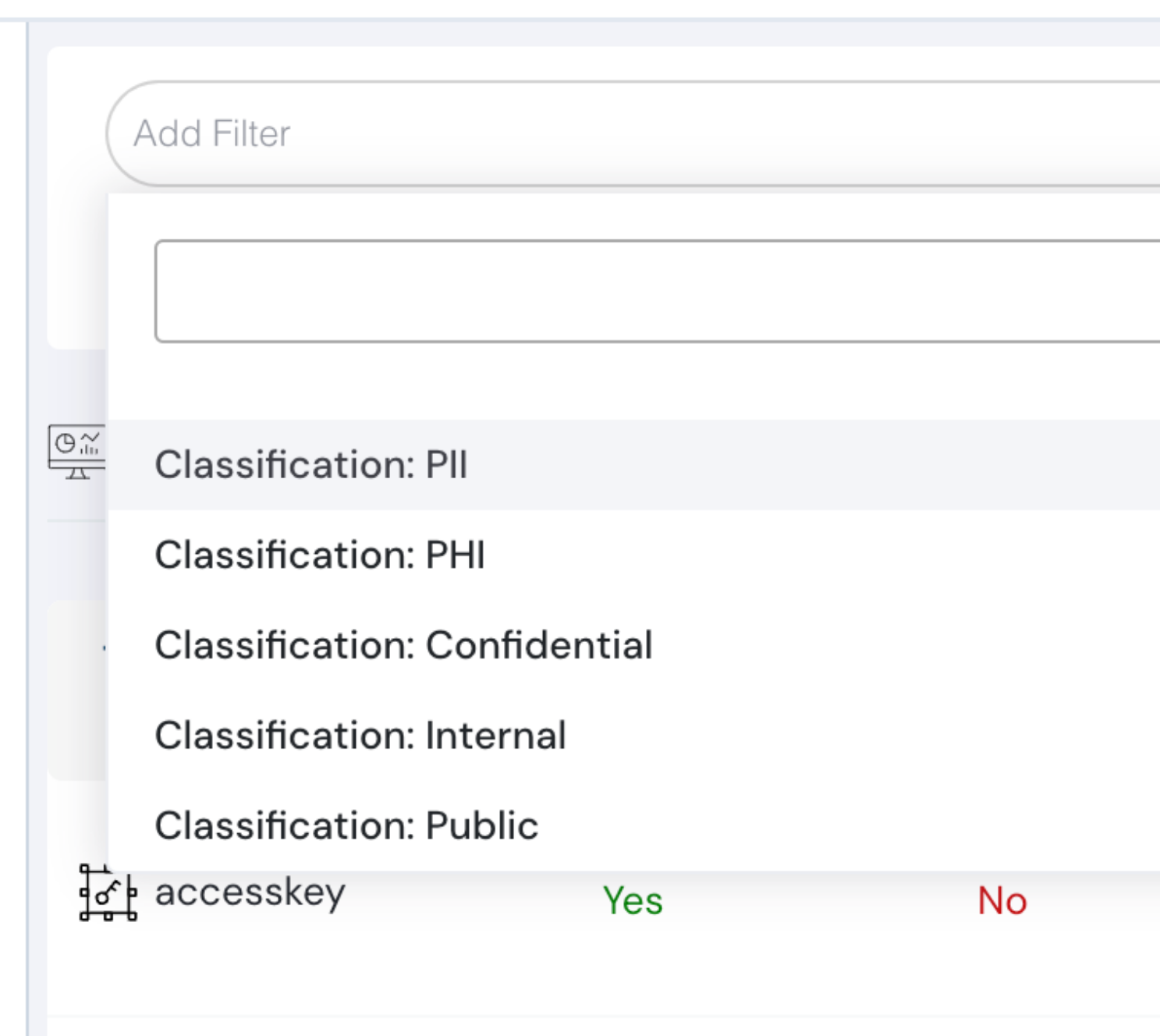 Tag your Applications and Data with different classifications
Tag your Applications and Data with different classifications
Cloudanix Resources
- The Science of Hiring Cybersecurity Professionals
- Platform Engineering - A deep dive
- Comprehensive Guide to Threat Modeling
- Security that goes beyond your traditional security practices - Zero Trust Security
- Restorative Justice Framework in Cloud Security
Resources over Internet
- Simplifying XSS Detection with Nuclei
- Cloud Access Management Maturity Model - Part 1 by Rowan Udell
- Zero Trust Maturity Model by CISA
- Research - CyberGreen
- Threat Modeling: Designing for Security (Book) by Adam Shostack
TODO:// is not an option for Cloud Security
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedBlog
Read More Posts
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Wednesday, Nov 05, 2025
From Static to Strategic: Modernizing Privileged Access for Cloud Infrastructure
The promise of the cloud – agility, scalability, and innovation – has revolutionized how enterprises operate. Cloud infr
Read MoreTuesday, Sep 30, 2025
Eliminate Standing Access: Introducing JIT Kubernetes for Azure AKS Security
The Security Mandate: Why Permanent Access Fails Mission-Critical AKS Kubernetes has become the operating system of
Read MoreFriday, Aug 08, 2025
User Access Review in Cloud Security: A Foundational Guide to Securing Your Cloud Environment
Introduction: The Unseen Gatekeepers of Cloud Security In the rapidly expanding landscape of cloud computing, organi
Read More