BYOQ (Bring Your Own Queries), HITRUST and Much More
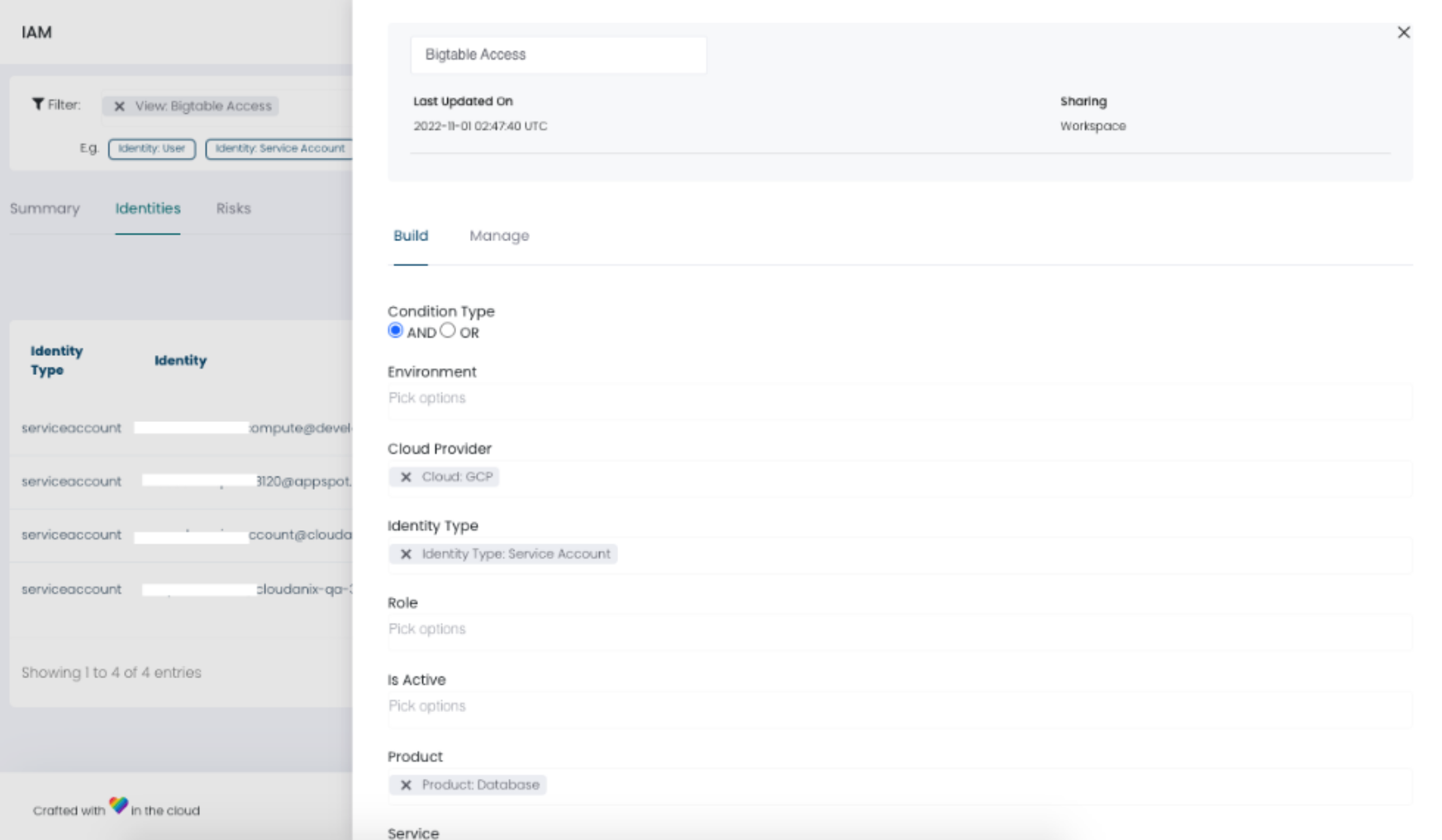
Build Your Own View
Earlier we had rolled out Inbuilt Views where we created custom views for you. But now you have the ability to Build Your Own Views.
A simple graphical interface helps you:
- Pick attributes
- Execute the query and save it
- Edit already executed queries
- Share it with your team members
Productivity and empowerment go to the next level!
Enriched IAM Screen
Your identities and their details are now presented in a tabular format. We now show you:
- Custom roles
- Granular permissions
- Various events these IAM principals have executed in your cloud accounts
Now the Principal view tells you:
- Their permissions
- Actions they have carried out
- Their review status
Announcing HITRUST and AWS Well Architected Framework Support
We have been showing your completeness against several compliance standards like HIPAA, SOC2, and many more.
Today we are rolling out two important additions:
- HITRUST
- AWS Well Architected Framework support
Setting Environments for Your Cloud Accounts
Cloudanix gives you a single dashboard for all your cloud accounts. Many customers have multiple accounts, even if they are using a single cloud provider.
Our users can now attach an environment to their cloud accounts, which can further be used in the Filter control on the page to query the information.
Security for your Code, Cloud and Data
Cloudanix replaces your 5-6 disjointed security tools within 30 minutes.
Get StartedBlog
Read More Posts
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Wednesday, Nov 05, 2025
From Static to Strategic: Modernizing Privileged Access for Cloud Infrastructure
The promise of the cloud – agility, scalability, and innovation – has revolutionized how enterprises operate. Cloud infr
Read MoreTuesday, Sep 30, 2025
Eliminate Standing Access: Introducing JIT Kubernetes for Azure AKS Security
The Security Mandate: Why Permanent Access Fails Mission-Critical AKS Kubernetes has become the operating system of
Read MoreFriday, Aug 08, 2025
User Access Review in Cloud Security: A Foundational Guide to Securing Your Cloud Environment
Introduction: The Unseen Gatekeepers of Cloud Security In the rapidly expanding landscape of cloud computing, organi
Read More